One of the biggest threats to both individuals and organizations in the digital age is the threat of ransomware. This kind of malware encrypts the data of its victims making it unreadable unless the attacker pays the ransom.
Protecting your databases requires understanding ransomware, how it works and how to recover in the event of an attack.
WHAT IS RANSOMWARE?
Ransomware is a type of malicious attack with the purpose of preventing access to data until a ransom is paid. From small businesses (even individuals) to large enterprises, ransomware attacks can affect anyone and cause serious operational, reputational and financial harm.
Impact of Ransomware
Ransomware attacks are on the rise, striking fear into individuals, companies, and even governments alike. A recent case involving the Axis Health System highlights the urgent issue: a cyber-attack discovered in August 2024 had gone unnoticed for nearly two months. The implications? Sensitive files have already been leaked to the dark web, and the criminal group behind the attack is demanding a staggering roughly $1.6 million ransom. Even if the ransom is paid, there’s no guarantee of complete data recovery; access restoration might only provide partial relief.
For healthcare providers, the stakes are incredibly high. A ransomware attack can cripple access to patient records, leading to delays in treatment that could jeopardize lives. The immediate aftermath often leaves organizations unable to access crucial information, resulting in significant downtime that can plummet productivity, wipe out revenues, and erode customer trust.
The consequences of such attacks extend beyond the financial realm. Companies that fail to safeguard sensitive information risk legal repercussions, including hefty fines and regulatory penalties. The reputational damage can be devastating, threatening the very survival of the business.
Moreover, paying a ransom rarely provides a full recovery of data. Once news of the breach becomes public, it often invites further attacks, creating a vicious cycle that’s hard to escape. In today’s digital landscape, protecting against ransomware isn’t just a matter of security; it’s a matter of survival.
Oracle Data Protection Solutions
Oracle databases are equipped with unique, integrated features to enhance security within your databases. This includes features such as Transparent Data Encryption that keeps data encrypted at-rest and when backed up and recovered, along with Oracle Key Vault for comprehensive key and secret store management.
Along with having the right security measures in place, it has become increasingly important to have a recovery plan in the event of a potential attack. Despite implementing various measures to encrypt, secure, and monitor access to databases, attacks can still make it through to compromise data and inflict system outages. Thus, it is imperative to have a resilient and reliable backup and recovery solution in place that can quickly restore databases to a transactionally consistent point in time with minimal data loss.
Oracle offers two strategic database recovery solutions: Zero Data Loss Recovery Appliance (ZDLRA) for on-premises database protection and the Zero Data Loss Autonomous Recovery Service (ZRCV) for cloud database protection. A summary of capabilities in both solutions is shown below, followed by a closer look into how these work to protect and recover your Oracle data.
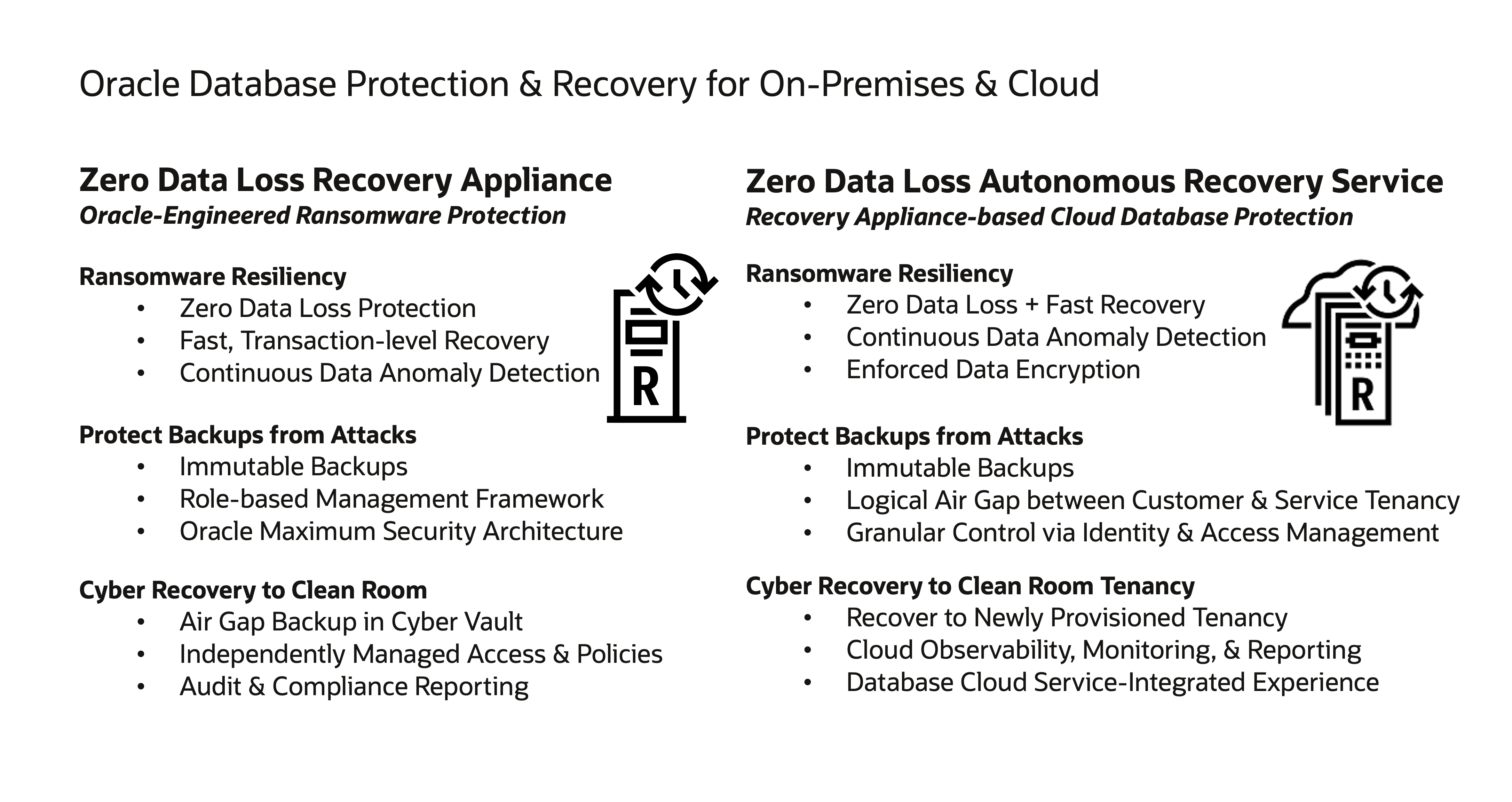
Zero Data Loss Protection
ZDLRA and ZRCV provide real time protection, dramatically shrinking potential data loss compared to general purpose backup solutions. A record of every transactional change that occurs on each database is captured on the appliance, allowing a business to be able to recover up to the last second before a possible ransomware attack with complete and transactionally consistent data.
Immutability
In both solutions, backups are configured for immutability, meaning that end users cannot modify retention settings or delete backups on their own.
The Recovery Appliance can be set with an immutable retention window so that backups are made impervious to modifications or deletions by the appliance administrator or backup operator (i.e. RMAN user). Only after the backup expires out of the window, will it be possible for modifications and deletions to occur.
In cloud, the Recovery Service operates in an Oracle-managed tenancy, separate from the customer’s databases tenancy with network connectivity via private endpoints, effectively rendering the service ‘invisible’ to database users. In addition, a backup retention lock can be enabled on specific databases via protection policy, disallows reduction of the retention period by any user or administrator in the tenancy and moving of the database to a different policy (which may have lower retention period setting).
Cyber Vault
On-premises database backups to a production ZDLRA can also be configured to replicate to a ZDLRA in a cyber vault stored in a separate location. In this deployment model, the production ZDLRA is connected to the vault via a separate network, controlled by a firewall or gateway to create an ‘air gap’. With this setup, no access is allowed into the vault. This network is only open at random, periodic times from within the vault, to allow new backups to replicate across so that the ZDLRA in the vault can stay as current as possible with production, as shown in the figure below.
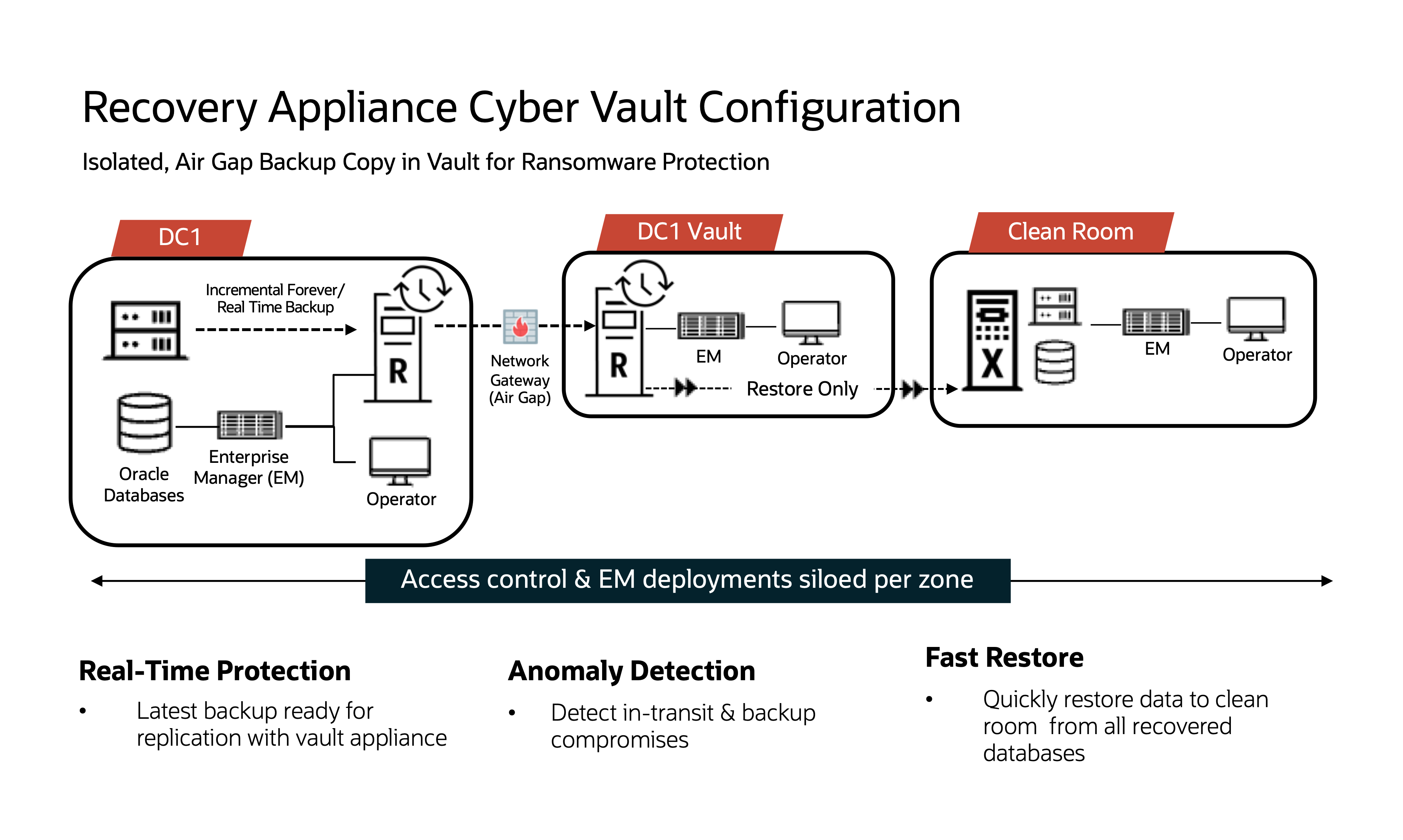
Key advantages of ZDLRA in the vault include reducing the vault network open window via incremental forever backup replication versus a much longer window to be open for replicating full backups. All backups are continuously validated for data anomalies as they are received and while stored on-disk, and built-in separate of duty framework allows vault administrators to have separate access/management, isolated from on-premises database and production administrators.
In the event of a production compromise, network connections into the vault can be shutoff and backups immediately restored to a clean room environment, where infrastructure is available to run minimum business viable databases and applications. This gives businesses the ability to take compromised systems offline for forensics analysis, while preserving business continuity until production operations can be re-established.
Database Integrated Data Anomaly Detection
Both solutions provide data anomaly detection and alerts for backup compromises due to possible ransomware. This data validation is done at all touch points in the backup lifecycle, from the moment the backup is created and sent, to when it is stored on disk using a block-level checksum-based method. Even while the backups are stored on the appliance, there is a periodic validation checked even if the backup was not touched. Additionally, backups of all data files and archived logs are verified to be present and complete for an actual restore.
Fastest Oracle Database Recovery
ZDLRA and ZRCV use daily incremental only backups to create daily ‘virtual full backups’ whereby a full backup is materialized when needed by a database restore operation. This means that a very recent full backup from today or any day within the retention period is readily available for restore. This eliminates the time-consuming traditional recovery approach of restoring and applying incremental backups, and speeds up overall database recovery.
Summary
The continued growth and increased sophistication of ransomware attacks has impacted all industries, and shown that enterprises are still challenged with meeting requirements for timely data restoration with minimal data loss. There are no better solutions to protect your Oracle enterprise databases than with the Oracle-integrated Zero Data Loss Recovery Appliance and Autonomous Recovery Service. If you’re ready to get started, refer to the resources section to discover how their innovative capabilities can be leveraged to uplevel your database protection and recovery posture against ransomware attacks.
ADDITIONAL RESOURCES
Recovery Appliance Product Page: https://www.oracle.com/engineered-systems/zero-data-loss-recovery-appliance/
Recovery Appliance Documentation: https://docs.oracle.com/en/engineered-systems/zero-data-loss-recovery-appliance/index.html
Oracle Backup & Recovery Blog: https://blogs.oracle.com/maa/category/maa-backup-and-recovery
Backup & Recovery Office Hours Sessions: https://asktom.oracle.com/ords/r/tech/catalog/series-landing-page?p5_series_id=1324315180218357785683422494484787420
