Introduction
The Security Technical Implementation Guide (STIG), which is published by the Defense Information Systems Agency (DISA), is a document that provides guidance on configuring a system to meet cybersecurity requirements for deployment within the Department of Defense (DoD) IT network systems.
The STIG guidelines have been included in the scap-security-guide package available under the ol8_appstream channel, which can be used with the openscap tool for evaluating the compliance of an Oracle Linux installation. The validation process can also suggest and in some cases automatically apply remediation in cases where compliance is not met. Individual rules and the remediation details are well documented in ssg-ol8-guide-standard. The scap-security-guide package available for Oracle Linux 8 machines provides the remediation playbooks for different profiles including STIG, which is located under /usr/share/scap-security-guide/ansible/ .
These playbooks can be used with Oracle Linux Automation Manager for applying the remediation on a group of machines.
Let’s now go through the steps on how to leverage Oracle Linux Automation Manager to apply remediation for a STIG profile.
Prerequisites:
- The scope of the playbook is for on-premises Oracle Linux 8 machines only
- The Oracle Linux Automation Manager machine should have ssh access to the target host(s)
- Hosts, Inventories, Machine credentials configured on the Oracle LinuxAutomation Manager
- Create a local project with the ol8-playbook-stig.yml added
# cp /usr/share/scap-security-gudie/ansible/ol8-playbook-stig.yml /var/lib/awx/projects/<project-directory>
OR
- Create a remote project with the playbook listed in the Oracle GitHub repository
- Job template to be created from ol8-playbook-stig.yml respectively
Installing openscap
Ensure that the latest version of the openscap package is installed on the target host.
# dnf install openscap -y
Execute the following command to check the compliance:
# oscap xccdf eval --profile stig --results /tmp/<path-to-result>.xml --report /tmp/<path-to-report>.html --cpe /usr/share/xml/scap/ssg/content/ssg-ol8-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-ol8-xccdf.xml
The report which will be generated as an HTML file that will list the compliance score and the details on each of the rules that was a success or a failure.
OR
If there are a large number of target machines, installing the OpenSCAP package and running the scan can be combined into a simple playbook.
Remediation Playbook
Each task from the playbook is in the below format:
- name: Ensure tmux is installed
package:
name: tmux
state: present
when: ansible_virtualization_type not in ["docker", "lxc", "openvz", "podman", "container"]
tags:
- DISA-STIG-OL08-00-020039
- NIST-800-171-3.1.10
- NIST-800-53-CM-6(a)
- enable_strategy
- low_complexity
- low_disruption
- medium_severity
- no_reboot_needed
- package_tmux_installed
Every task is associated with job tags, for example “no_reboot_needed” as seen above.
The “job tags” option from Oracle Linux Automation Manager can be leveraged to selectively execute only the required tasks.
Similarly, the tasks which are not required can be skipped using “skip tags” from Oracle Linux Automation Manager when launching the template.
As part of the remediation activity, one of the rules with tag DISA-STIG-OL08-00-010550 disables root login over SSH.
If the remediation for this task is applied, the consequent tasks will fail as the SSH root login would be disabled.
Hence, this task needs to be skipped for the consequent tasks to be played.
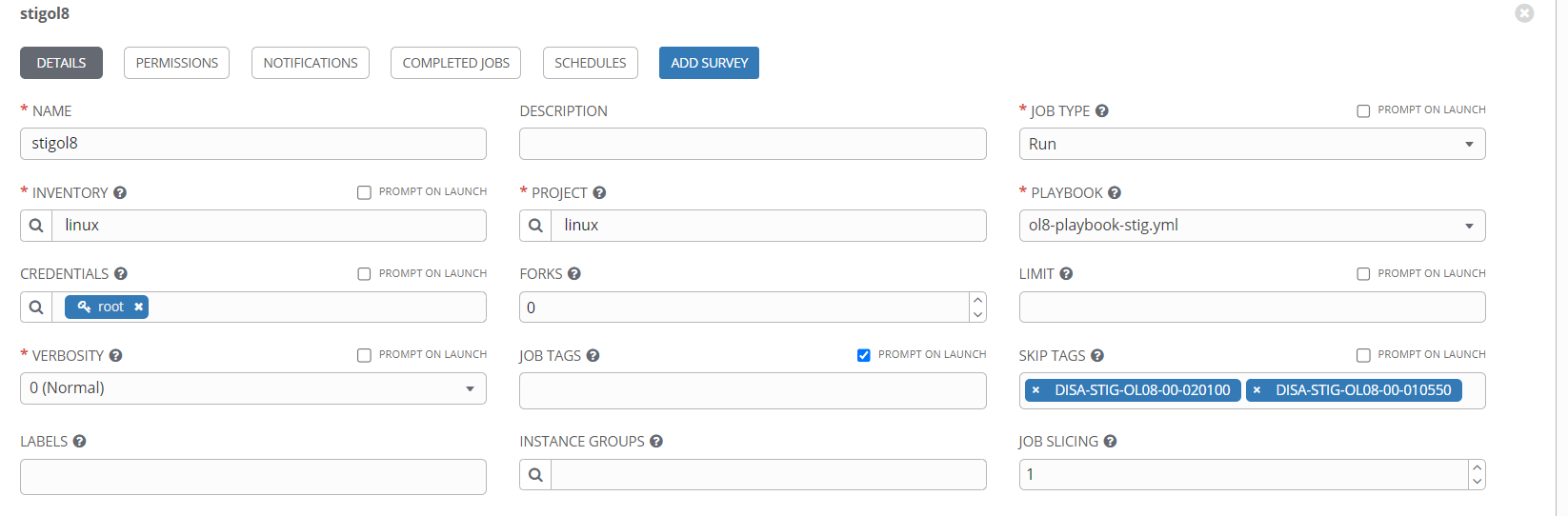
Ensure to enter “DISA-STIG-OL08-00-010550” tag under “skip tags” before launching the template.
If more logging is required, increase the verbosity to 2 (More Verbose) and Launch the template.
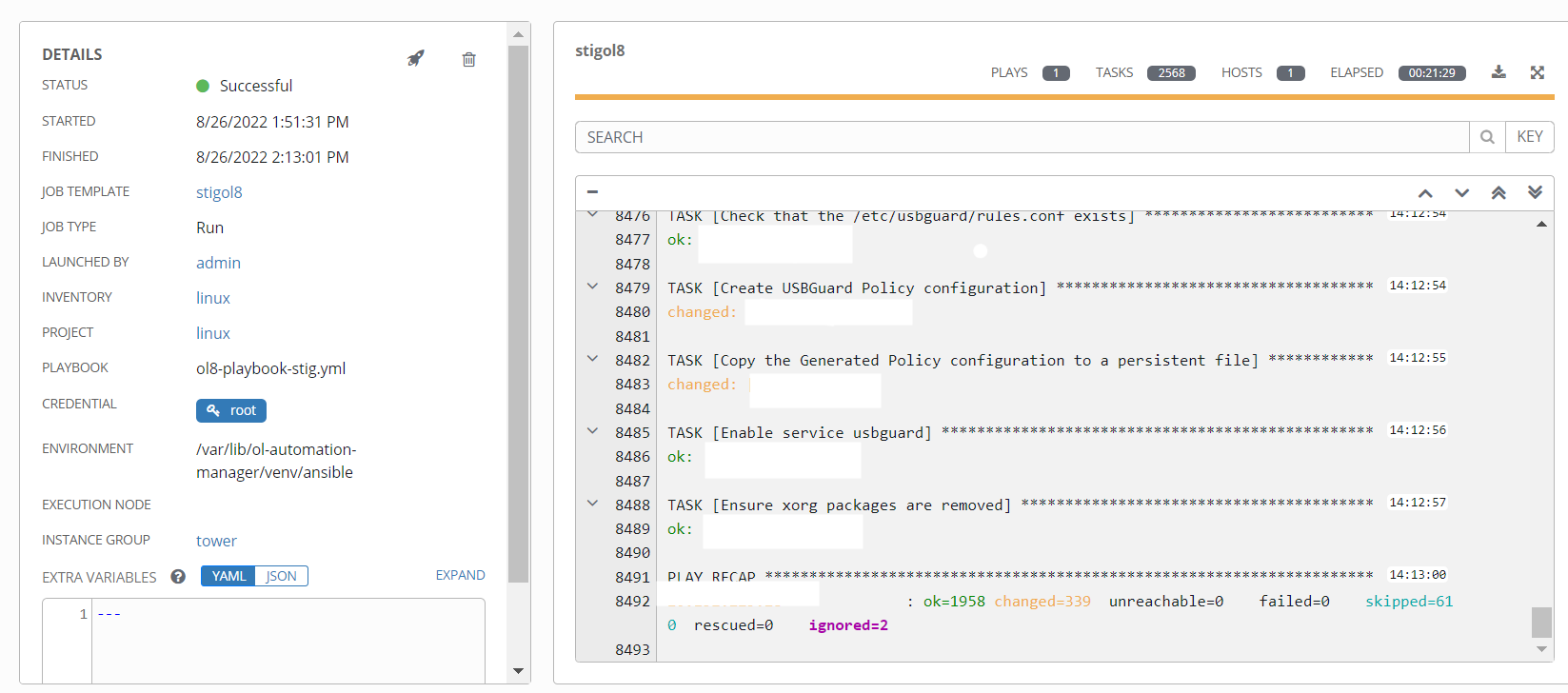
Rescanning the host for compliance
The template may require a minimum of 30 minutes to be completed. Post which, rerun the oscap command, specifying a new path for the report and results.
# oscap xccdf eval --profile stig --results /tmp/<new-path-to-result>.xml --report /tmp/<new-path-to-report>.html --cpe /usr/share/xml/scap/ssg/content/ssg-ol8-cpe-dictionary.xml /usr/share/xml/scap/ssg/content/ssg-ol8-xccdf.xml
Open the generated html file using a browser and notice the compliance score.
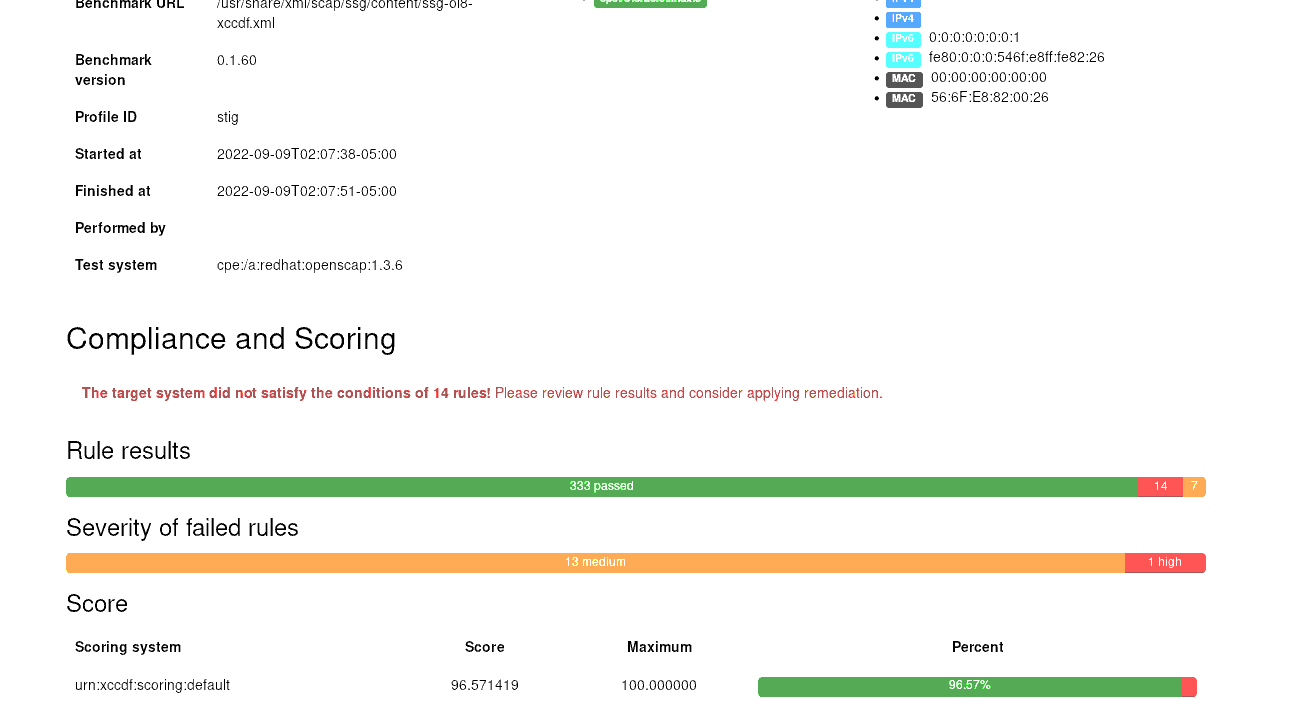
Note that the compliance score varies between different environments and may not be the same as seen above.
Considerations before applying the remediation
As part of applying remediation, there will be multiple modifications made, hence it is necessary to review each task. Here are few examples:
- DISA-STIG-OL08-00-010550 – Disables SSH root login. SSH session to the servers might give an “Access Denied” error.
- DISA-STIG-OL08-00-010020 – Enables FIPS. Ensure to reboot the host for the FIPS to be enabled. Though the remediation is applied, the rule will still be marked as failed.
- DISA-STIG-OL08-00-010670 – Disables kdump services.
To continue exploring more use cases of Oracle Linux Automation Manager, Please navigate to Ansible Collections Github page.
Resources
- Oracle Linux Automation Manager Getting Started Guide
- Oracle.com/linux
- Download Oracle Linux
- Oracle Linux product documentation
- Oracle Linux Premier Support Information
- Oracle Cloud Native Environment
