In September, Oracle EVP of OCI Security and Developer Platforms, Mahesh Thiagarajan, wrote an informative piece on how Oracle intends to become your most trusted cloud platform. In it, Mahesh shared the tenets that Oracle follows to build security and privacy into the cloud:
- Simple and effortless: Oracle is aware of the importance of providing simple and effortless security services and the fact that ease also means quicker adoption.
- Deeply integrated: Oracle strives to bring security to customers – not make customers change their security strategy to meet our cloud requirements.
- Complete control: Through an industry-wide initiative, Oracle and other leaders are helping to design a new open standard for network and data security. We recently announced the Oracle Zero Trust Packet Routing Platform, which can help you redefine how you access, move, and secure data.
This is augmented with ongoing innovations from the Oracle security team and technologies such as Oracle Linux. Though often viewed as behind-the-scenes, Oracle Linux plays a major role in Oracle’s trusted cloud strategy.
Oracle Linux is the Enterprise Linux distribution underpinning Oracle Cloud Infrastructure, and it can be used by customers in Oracle Cloud or for on-premises deployments. Freely available to all with high-quality, low-cost support for those who need it, Oracle Linux is a transparent and secure multicloud operating system that offers a smooth experience to organizations running workloads both on-premises and in the cloud.
Oracle Linux helps ensure administrators and developers have the features and tools they need to deploy their workloads securely using best-in-class technologies and established best practices. Let’s review the foundational elements that make Oracle Linux a trusted part of the cloud.
Oracle Linux images
Oracle Linux is the most popular Linux operating system deployed on Oracle Cloud Infrastructure (OCI). To address a wide range of customer needs, we provide different types and releases of Oracle Linux images for Oracle Cloud.
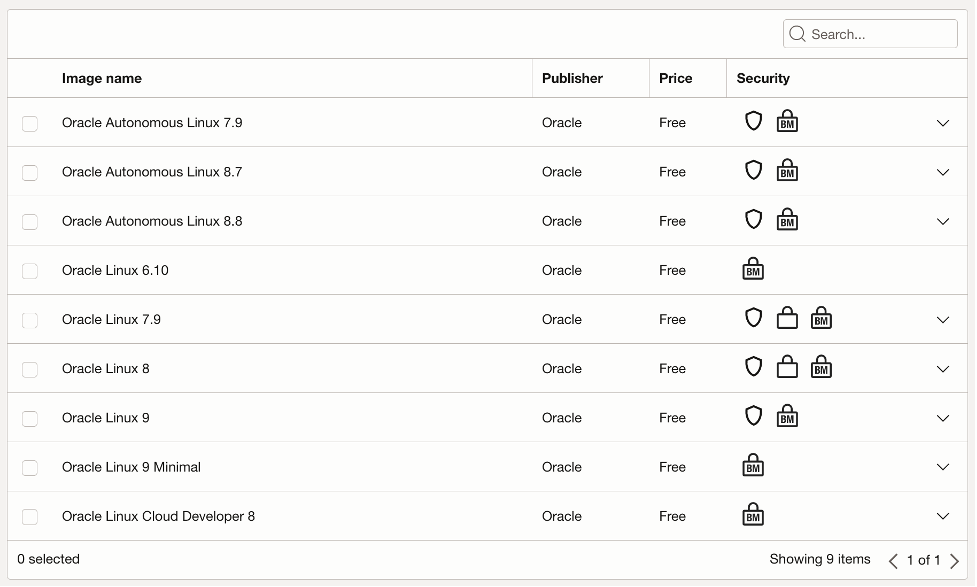
All of these images, from Oracle Autonomous Linux to the standard Oracle Linux image, along with a Developer image focused on development for the cloud, include the same high levels of security, and have Ksplice pre-installed. The following are unique and lesser-known security features of Oracle Linux enabled by default.
- Shielded instances use the combination of Secure Boot, Measured Boot, and the Trusted Platform Module to increase the firmware security of your instances. Oracle Linux images enable and support all of them, which harden the host’s firmware security to defend against malicious boot level software.
- Confidential computing encrypts and isolates, in real time, data and the applications processing that data, preventing unauthorized access or modification of either the data or the application. Oracle Linux supports “confidential computing” in the Unbreakable Enterprise Kernel (UEK). This capability is the result of collaboration with AMD on modern technologies like AMD Secure Encrypted Virtualization (SEV) and AMD Transparent Secure Memory Encryption (TSME).
Security Technical Implementation Guides (STIGs)
Oracle also offers an Oracle Linux STIG image. A STIG is a document written by the Defense Information Systems Agency (DISA) that provides guidance for configuring a system to meet cybersecurity requirements for deployment within the IT systems of the Department of Defense (DoD). Adhering to a STIG can help secure a network against cybersecurity threats by improving infrastructure and network security to mitigate vulnerabilities. Compliance with STIGs is a requirement for DoD agencies or any organization that is part of the DoD information networks (DoDIN).
Oracle regularly updates the Oracle Linux STIG images, available through the Oracle Cloud Marketplace, with the latest security errata and helps automate compliance by providing a hardened version of the standard Oracle Linux images.
The latest versions of the Oracle Linux STIG are available at the DoD Cyber Exchange website. Search for Oracle Linux and then download the appropriate zip file.
Slim container images for reduced attack surface
Oracle Cloud Infrastructure gives you the option to run Oracle Linux on a virtual machine (VM), on bare metal shapes, and containerized on top of Kubernetes.
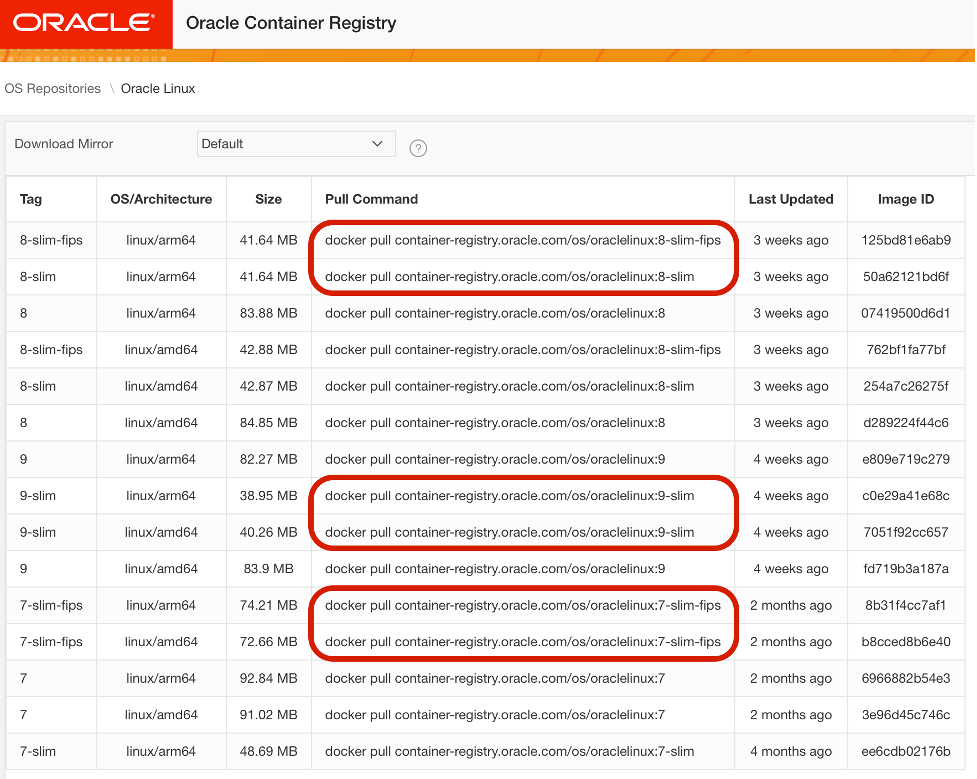
Kubernetes relies on Open Container Initiative container images to deploy an application and services. Oracle has built a dedicated portal for Oracle products’ container images, including Oracle Linux. All are available at https://container-registry.oracle.com.
An image is the base of your container. Thus, keeping images slim and light speeds up the build and deployment of containers. Image size matters for different reasons:
- Reduced deployment time and improved team productivity and application performance;
- Improved storage utilization;
- Reduced network bandwidth when transferring between hosts or different environments.
Removing unnecessary files and keeping images slim helps eliminate vulnerable components and reduces the attack surface exposed to security threats.
This is why the Oracle Container Registry offers you access to “slim” and “slim-fips” images for Oracle Linux.

Ksplice
Available to Oracle Linux customers with Oracle Linux Premier Support and free of charge for Oracle Cloud Infrastructure customers, Oracle Ksplice updates select critical components of your Oracle Linux installation with important security patches without needing to reboot your server or restart your service.
With more than 2.5 million servers protected each month and over 100 million patches applied, Oracle Ksplice can be trusted to keep customers’ systems up to date while reducing service interruption.
With this unique capability, Oracle Linux customers can significantly reduce the time allocated for planning and implementing critical OS security patches and align them with application patching schedules.
FIPS and Common Criteria certifications
Created by the National Institute of Standards and Technology’s (NIST’s) Computer Security Division, the Federal Information Processing Standard (FIPS) established a data security and computer system standard per the Federal Information Security Management Act.
FIPS Publication 140-2, Security Requirements for Cryptographic Modules, specifies the security requirements that must be satisfied by a cryptographic module that is used within a security system to protect sensitive, but unclassified information. Oracle Linux provides a set of cryptographic libraries, services, and user-level cryptographic applications that are validated at FIPS Publication 140-2, and we are also working to provide new FIPS Publication 140-3 validation.
Oracle Linux 8 has received several Federal Information Processing Standard-140 (FIPS-140) validations of its cryptographic modules as well as a Common Criteria (CC) Certification for Oracle Linux 7 and Oracle Linux 8.
Two options are available for Oracle Linux FIPS validated configurations:
- Step-by-step instructions on how to enable FIPS on an existing Oracle Linux deployment;
- Pre-configured Oracle Linux FIPS-enabled container images in the Oracle Container Registry.
Under the cover
The Oracle Linux team invests time and resources to improve the Linux Kernel security and functionality for enterprises. Among all the improvements applied to the operating system, two deserve a special mention:
- QEMU and KVM hypervisor security. As a cloud provider, Oracle relies on the KVM/QEMU hypervisor and participates in the community project to improve its performance and security. QEMU can be susceptible to security attack because it is a large monolithic program that provides many services to the VMs it controls. Oracle worked, implemented, and finalized the idea of a disaggregated QEMU hypervisor, where each service relies on a dedicated host process with the intent to reduce the hypervisor attack surface. Further details are available here.
- NFS in-transit encryption (RPC with TLS). Oracle actively contributed to the Linux upstream Kernel on the “in-transit encryption” for NFS storage solution to bring transparent, end-to-end encryption to NFS to help avoid theft of information while data is transmitted on the network. The Linux community recently included Oracle’s contribution starting from upstream Linux Kernel 6.4 release.
Conclusion
Cloud confidence comes with proper security and a trusted cloud platform, and Oracle Cloud Infrastructure and Oracle Linux are security-first in planning, design, and implementation.
The Oracle Linux team is constantly focused on preventing challenges arising from cybercrime. We supply the tools so customers can harden Linux deployments and protect their infrastructures, both on-premises and in the cloud, while following the highest-level standards coming from important entities like the NIST’s Computer Security Division or Common Criteria.
At Oracle, the security of our customers’ data is the top priority. We’ve come a long way, and we continue to work on these tenets to remain your trusted cloud platform and provider.
Resources
Get more information about Oracle Linux Security or contact an Oracle Linux representative to discuss Oracle Linux consulting services and see how Oracle Linux can help you protect your people, platforms, and data. To learn more, visit
