This technical article explains how to check if there are any patches available for your Linux system, such as Oracle Linux, Red Hat Enterprise Linux, CentOS Linux, or Ubuntu, that you can apply without a reboot using Oracle Ksplice. Users of these distributions should use Ksplice Inspector to check for updates, and if found, apply the patches using Ksplice without a reboot, and without changing distributions.
Ksplice Inspector is a free online tool that can show you a list of available updates that you can apply today with Ksplice without any downtime. Proactively identifying security vulnerabilities with Ksplice Inspector is an important step to help you assess the cybersecurity challenge you are facing today. Get Oracle Linux Premier Support or Oracle Cloud Infrastructure subscriptions to immediately enable the ability to apply those patches without reboot.
IT systems require regular patching for security, performance, and compliance reasons. Without Ksplice, users reported that on average, organizations take roughly 134 days to apply security patches to all relevant Linux servers (ESG Research Insights Paper Survey: Today’s Top 3 IT Challenges with Modern Application Environments, March 2021). Ksplice allows you to patch without downtime, making patching more easily planned and automated. Customers who patch with Ksplice report better ability to respond to urgent security updates, such as spending fewer hours during their patch window, requiring fewer staff members during patching, and patching more frequently.
Additional examples are provided to show certain Ksplice commands for managing patching and updates. For illustration purposes, the examples are provided using a command line interface.
Use Ksplice Inspector
Here I’m using a Linux system running Oracle Linux 8 with the Unbreakable Enterprise Kernel (UEK) Release 6 as an example.
[opc@honsu-ol8-vm1 ~]$ cat /etc/oracle-release Oracle Linux Server release 8.5 [opc@honsu-ol8-vm1 ~]$ uname -a Linux honsu-ol8-vm1 5.4.17-2136.304.4.4.el8uek.x86_64 #2 SMP Fri Mar 4 17:21:40 PST 2022 x86_64 x86_64 x86_64 GNU/Linux
Open a terminal on the Linux system you want to check and run the following command in your terminal.
[opc@honsu-ol8-vm1 ~]$ echo "`uname -s`//`uname -m`//`uname -r`//`uname -v`" Linux//x86_64//5.4.17-2136.304.4.4.el8uek.x86_64//#2 SMP Fri Mar 4 17:21:40 PST 2022
Copy the output of that command into this text box of Ksplice Inspector and click Find Updates.
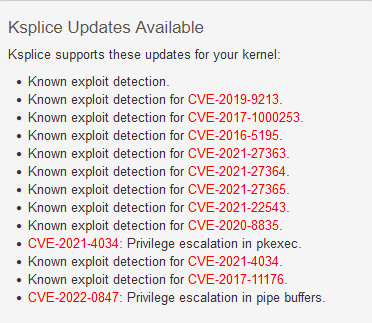
You can also find the same information by running the following from a command line terminal:
[opc@honsu-ol8-vm1 ~]$ (uname -s; uname -m; uname -r; uname -v) | \ > curl https://api-ksplice.oracle.com/api/1/update-list/ \ > -L -H "Accept: text/text" --data-binary @- Your kernel needs the following updates: Known exploit detection. Known exploit detection for CVE-2019-9213. Known exploit detection for CVE-2017-1000253. Known exploit detection for CVE-2016-5195. Known exploit detection for CVE-2021-27363. Known exploit detection for CVE-2021-27364. Known exploit detection for CVE-2021-27365. Known exploit detection for CVE-2021-22543. Known exploit detection for CVE-2020-8835. CVE-2021-4034: Privilege escalation in pkexec. Known exploit detection for CVE-2021-4034. Known exploit detection for CVE-2017-11176. CVE-2022-0847: Privilege escalation in pipe buffers.
Apply Ksplice updates
If your systems are under Oracle Linux Premier Support or Oracle Cloud Infrastructure subscriptions, and you’ve configured and enabled Ksplice for your Linux system, it is simple and easy to apply Ksplice updates with zero-downtime. The code below shows how to apply the Ksplice updates covered in the above example.
[opc@honsu-ol8-vm1 ~]$ sudo ksplice -y kernel upgrade The following steps will be taken: Install [gnazdq12] Known exploit detection. Install [5xvbepz2] Known exploit detection for CVE-2019-9213. Install [9uejl8j0] Known exploit detection for CVE-2017-1000253. Install [hu4ybx21] Known exploit detection for CVE-2016-5195. Install [j4j1a9ir] Known exploit detection for CVE-2021-27363. Install [en8bmrwg] Known exploit detection for CVE-2021-27364. Install [h1g12nxn] Known exploit detection for CVE-2021-27365. Install [dbo8mooo] Known exploit detection for CVE-2021-22543. Install [p98zatiu] Known exploit detection for CVE-2020-8835. Install [52nyjrrn] CVE-2021-4034: Privilege escalation in pkexec. Install [bkb6unty] Known exploit detection for CVE-2021-4034. Install [d5eam6ll] Known exploit detection for CVE-2017-11176. Install [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Installing [gnazdq12] Known exploit detection. Installing [5xvbepz2] Known exploit detection for CVE-2019-9213. Installing [9uejl8j0] Known exploit detection for CVE-2017-1000253. Installing [hu4ybx21] Known exploit detection for CVE-2016-5195. Installing [j4j1a9ir] Known exploit detection for CVE-2021-27363. Installing [en8bmrwg] Known exploit detection for CVE-2021-27364. Installing [h1g12nxn] Known exploit detection for CVE-2021-27365. Installing [dbo8mooo] Known exploit detection for CVE-2021-22543. Installing [p98zatiu] Known exploit detection for CVE-2020-8835. Installing [52nyjrrn] CVE-2021-4034: Privilege escalation in pkexec. Installing [bkb6unty] Known exploit detection for CVE-2021-4034. Installing [d5eam6ll] Known exploit detection for CVE-2017-11176. Installing [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Your kernel is fully up to date. Effective kernel version is 5.4.17-2136.304.4.5.el8uek
Remove Ksplice update
Removing Ksplice updates is also easy. You can uninstall all updates, bringing you back to your original stock kernel, or uninstall individual updates by specifying a Ksplice identifier (KID) while your system is running. The KID for an applied patch is displayed inside square brackets. This example is to roll back a single Ksplice update for the CVE-2022-0847.
[opc@honsu-ol8-vm1 ~]$ sudo ksplice -y kernel remove bpuyuneq The following steps will be taken: Remove [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Removing [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Effective kernel version is 5.4.17-2136.304.4.4.el8uek
Apply Ksplice update to fix the CVE-2022-0847
In the above example, Ksplice update for the CVE-2022-0847 was removed. Now I’m running ksplice upgrade command to apply the available Ksplice update to fix the CVE-2022-0847.
[opc@honsu-ol8-vm1 ~]$ sudo ksplice -y kernel upgrade The following steps will be taken: Install [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Installing [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Your kernel is fully up to date. Effective kernel version is 5.4.17-2136.304.4.5.el8uek
Show installed Ksplice updates
You can use ksplice show command to display the installed Ksplice updates.
[opc@honsu-ol8-vm1 ~]$ sudo ksplice kernel show Installed updates: [gnazdq12] Known exploit detection. [5xvbepz2] Known exploit detection for CVE-2019-9213. [9uejl8j0] Known exploit detection for CVE-2017-1000253. [hu4ybx21] Known exploit detection for CVE-2016-5195. [j4j1a9ir] Known exploit detection for CVE-2021-27363. [en8bmrwg] Known exploit detection for CVE-2021-27364. [h1g12nxn] Known exploit detection for CVE-2021-27365. [dbo8mooo] Known exploit detection for CVE-2021-22543. [p98zatiu] Known exploit detection for CVE-2020-8835. [52nyjrrn] CVE-2021-4034: Privilege escalation in pkexec. [bkb6unty] Known exploit detection for CVE-2021-4034. [d5eam6ll] Known exploit detection for CVE-2017-11176. [bpuyuneq] CVE-2022-0847: Privilege escalation in pipe buffers. Effective kernel version is 5.4.17-2136.304.4.5.el8uek
Conclusions
Whether you are running Oracle Linux, Red Hat Enterprise Linux, CentOS Linux, or Ubuntu, you can use the free Ksplice Inspector to find out a list of available Ksplice updates (check supported kernels).
With Oracle Linux Premier Support or Oracle Cloud Infrastructure subscriptions, customers can have access to award-winning Oracle support resources and Linux support specialists, around-the-clock, and best-in-class support for Linux issues and best-in-class mitigation for security vulnerabilities via our non-disruptive Ksplice updates. You can update your systems without a reboot. Your applications (on bare metal or virtual machine) continue to run and your container workloads are not disrupted with Oracle Ksplice.
Note that Ksplice updates can be applied to the above mentioned distributions, and do not require conversion to Oracle Linux. The Oracle Linux Premier Support subscriptions or Oracle Cloud Infrastructure subscriptions entitle the user to run Ksplice on the supported distributions.
Next steps
To explore and experience the benefits of Oracle Ksplice zero-downtime updates, try Oracle Ksplice free for 30 days, or read the tutorial Using Oracle Ksplice in Oracle Linux 8 and run it on an Oracle-provided free lab environment.
Ksplice patching can be integrated with your popular Linux management tools or services such as Oracle Linux Manager, Oracle Enterprise Manager, OS Management Service, or your preferred ones. Ksplice API is also available for many independent software vendors for interoperability and tight integration in order to meet your enterprise security and patching requirements.
Please contact your Oracle team to discuss how we work with you to help close security gaps and reduce the attack surface of your Oracle Linux and virtualization infrastructure.
Additional Resources
Oracle Linux is one of the most secure operating environments deployed on-premises and in the cloud, and you can rely on Oracle Linux to help accomplish your IT goals. Oracle Linux ships with secure defaults and provides top-notch security features like Ksplice for kernel, hypervisor and user space live patching, known exploit detection, and modern Linux kernel support to the enterprise, whether deployed in the cloud or on-premises. Oracle Ksplice can
- protect Linux systems (Oracle Linux, Red Hat Enterprise Linux, CentOS, Ubuntu, etc.) from vulnerabilities and help increase security compliance
- reduce human error by automating the patching process
- keep systems running, improving system availability with no reboots
- cut admin time and cost
- improve support diagnostic capabilities
To learn more about Oracle Linux and Oracle Ksplice, visit
- Oracle Ksplice
- Oracle Linux Documentation: Ksplice User’s Guide
- Free Tutorial and Lab: Using Oracle Ksplice in Oracle Linux 8
- Free 30-day trial of Ksplice zero-downtime updates
- Oracle Linux Errata Announcements: linux.oracle.com/errata
- oracle.com/linux
