When we began work to include Kata Containers with Oracle Linux Cloud Native Environment I was immediately impressed with the change they bring to the security boundary of containers but I had to wonder, how does it work?
This article attempts to briefly cover the What, When and How of Kata Containers.
Before we dive into Kata Containers you may want to read the brief history of Linux containers.
1. What are Kata Containers?
Kata Containers is an open source [project with a] community working to build a secure container runtime with lightweight virtual machines that feel and perform like containers, but provide stronger workload isolation using hardware virtualization technology as a second layer of defense.
Kata Containers stem from the Intel® Clear Containers and Hyper RunV projects. Kata Containers use existing CPU features like Intel VT-X and AMD-V™ to better isolate containers from each other when run on the same host. Each container can run in its own VM and have its own Linux Kernel. Due to the boundaries between VMs a container should not be able to access the memory of another container (Hypervisors+EPT/RVI).
runc is the runtime-spec reference implementation on Linux and when it spawns containers it uses standard Linux Kernel features like AppArmour, capabilities(7), Control Groups, seccomp, SELinux and namespaces(7) to control permissions and flow of data in and out of the container. Kata Containers extends this by wrapping the containers in VMs.
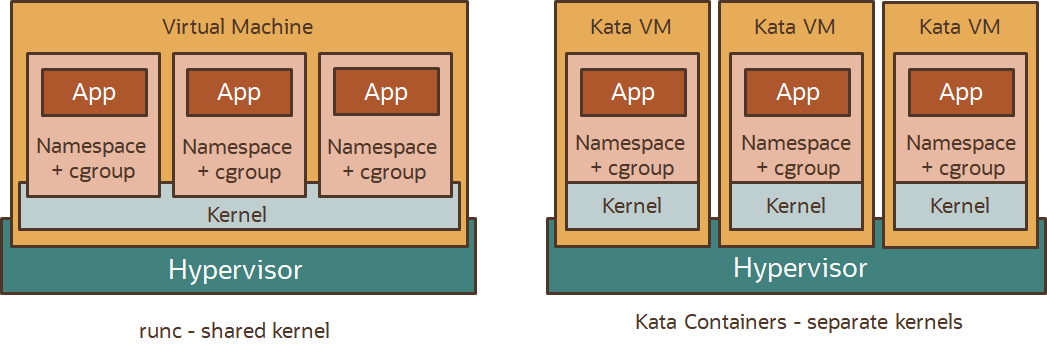
2. When should I use Kata Containers?
runc is the most common container runtime, the default for Docker™, CRI-O and in turn Kubernetes®. Kata Containers give you an alternative, one which provides higher isolation for mixed-use or multi-tenant environments. Kubernetes worker nodes are capable of using both runc and Kata Containers simultaneously so dedicated hardware is not required.
For intra-container communication efficiency and to reduce resource usage overhead, Kata Containers executes all containers of a Kubernetes pod in a single VM.
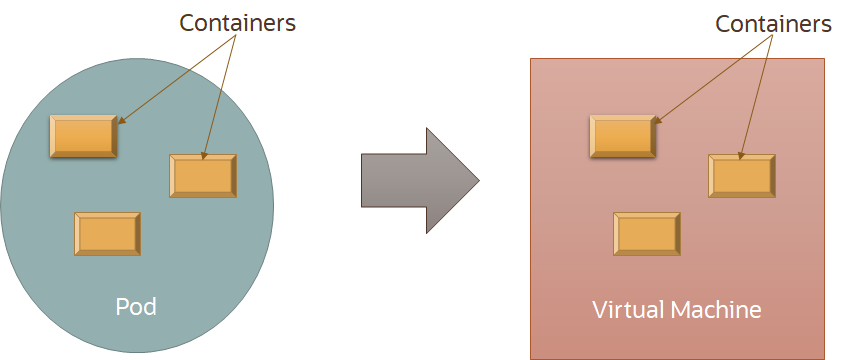
Deciding when to use runc and when to use Kata Containers is dependent on your own security policy and posture. Factors that may influence when higher levels of isolation are necessary include:
- The source of the image – trusted vs untrusted.
- Was the image built in-house or downloaded from a public registry?
- The contents of the container
- In-house software that brings a competitive advantage
- The dataset the container works on (public vs confidential)
Working in a virtual environment may impact performance so workload-specific testing is recommended to evaluate the extent, if any, of that impact in your environment.
3. How do Kata Containers work?
When installing the Kubernetes module of Oracle Linux Cloud Native Environment both runc and Kata Containers are deployed along with CRI-O, which provides the necessary support between Kubernetes and the container runtimes.
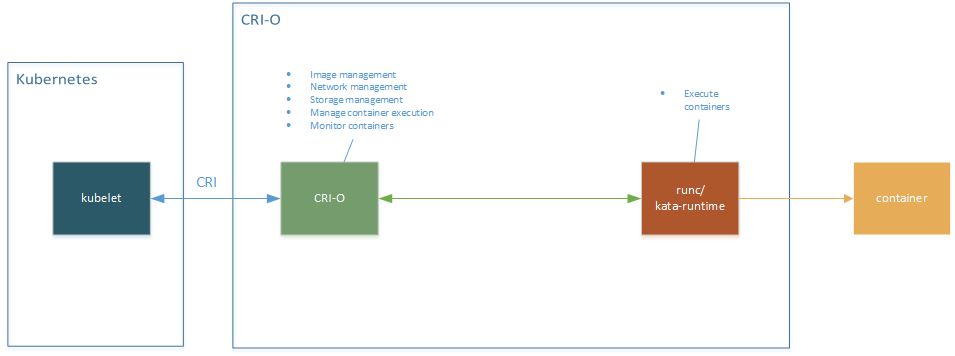
A heavily optimized and purpose-tuned Linux Kernel is used by Kata Containers to boot the VM. This is paired with a minimized user space to support container operations and together they provide fast initialization.
In order to create a Kata Container, a Kubernetes user must initially create a RuntimeClass object. After that Pods or Deployments can reference the RuntimeClass to indicate the runtime to use. Examples are available in the Using Container Runtimes documentation.
Kata Containers are designed to provide “lightweight virtual machines that feel and perform like containers“; your developers shouldn’t need to be aware that their code is executing in a VM and should not need to change their workflow to gain the benefits.
Trademarks Oracle and Java are registered trademarks of Oracle and/or its affiliates. Other names may be trademarks of their respective owners.