An important step in securing an organization’s IT infrastructure is to regularly scan production software for Common Vulnerabilities and Exposures (CVE).
The purpose of a CVE scan is to identify potential vulnerabilities in the organization’s systems and networks, and to provide a report that details the vulnerabilities found, their severity, and recommended remediation steps.
While there are numerous third party tools available to perform a CVE scan, the scan can be easily performed using Oracle’s Ksplice Inspector, a free online tool that can show a list of available updates that users can apply today with Ksplice without any downtime. Proactively identifying security vulnerabilities with Ksplice Inspector is an important step to help users assess the cybersecurity challenge. Get Oracle Linux Premier Support or Oracle Cloud Infrastructure subscriptions to immediately enable the ability to apply those patches without reboot.
The Ksplice Inspector tool requires the end user to provide the output of the command:
# "echo "`uname -s`//`uname -m`//`uname -r`//`uname -v`"
From the output, you will have the list of the CVEs affecting the system.
Gathering the output from multiple machines and examining the list could be a time consuming task.
Let’s review the steps to get whole process automated using Oracle Linux Automation Manager.
The workflow of the playbook uptrack-check.yml is as follows:
Firstly, the playbook prompts the user to check if the lists needs to be stored in a file on the remote server or displayed in Oracle Linux Automation Manager.
This is done using an extra variable which needs to be declared while launching the template.
Extra variables are key-value pairs that can be passed at runtime while executing the Job template.
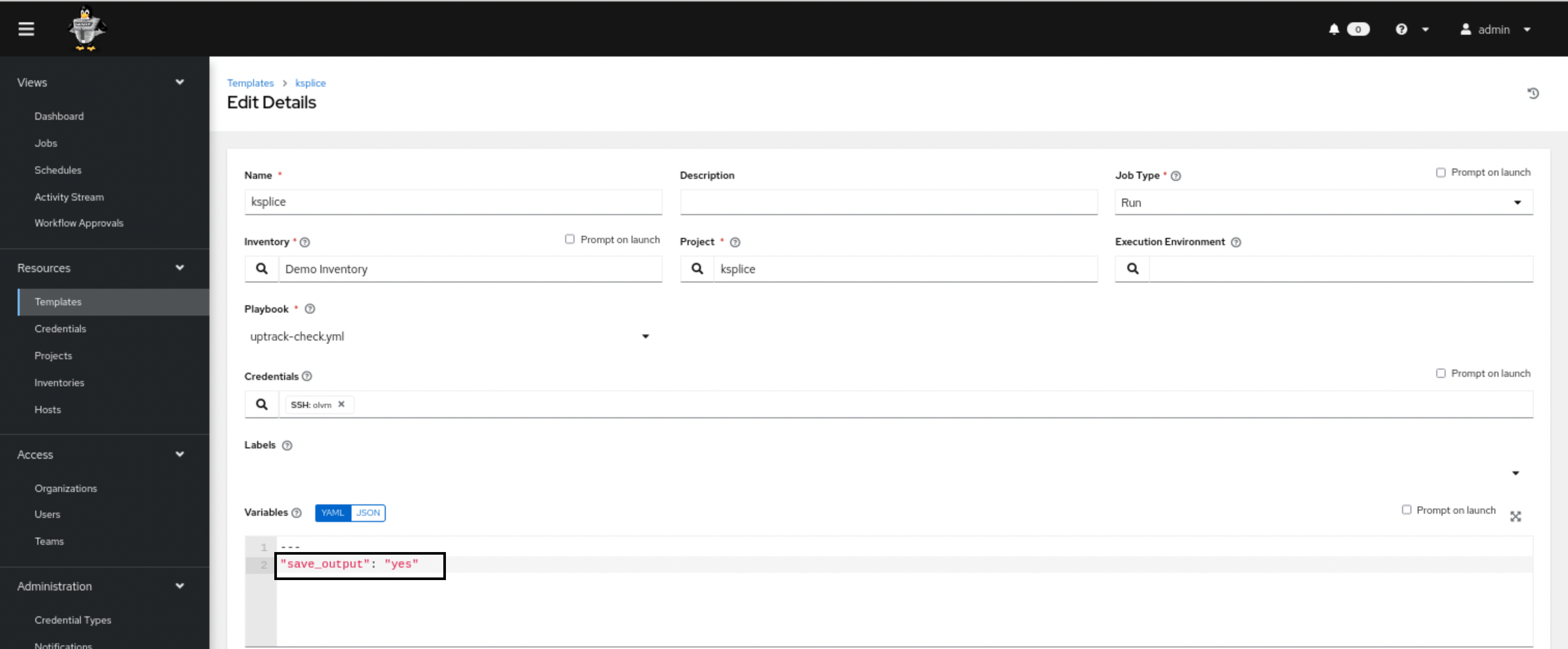
If we opt to save the output as seen above, the list of CVEs will be stored in an html file with the name uptrack-check.html under /tmp directory on the target system for which the scan is being executed.
You can open the html file with the browser of your choice and find the list of the CVEs.

Remember to click on each CVE number which redirects to https://linux.oracle.com for more information.
If the output needs to be listed in Oracle Linux Automation Manager, rather than being stored in the file, pass the extra variable “save_output”: “no” when the template is launched.
The output will look truncated, but you can click on the same to get the entire list in JSON format.
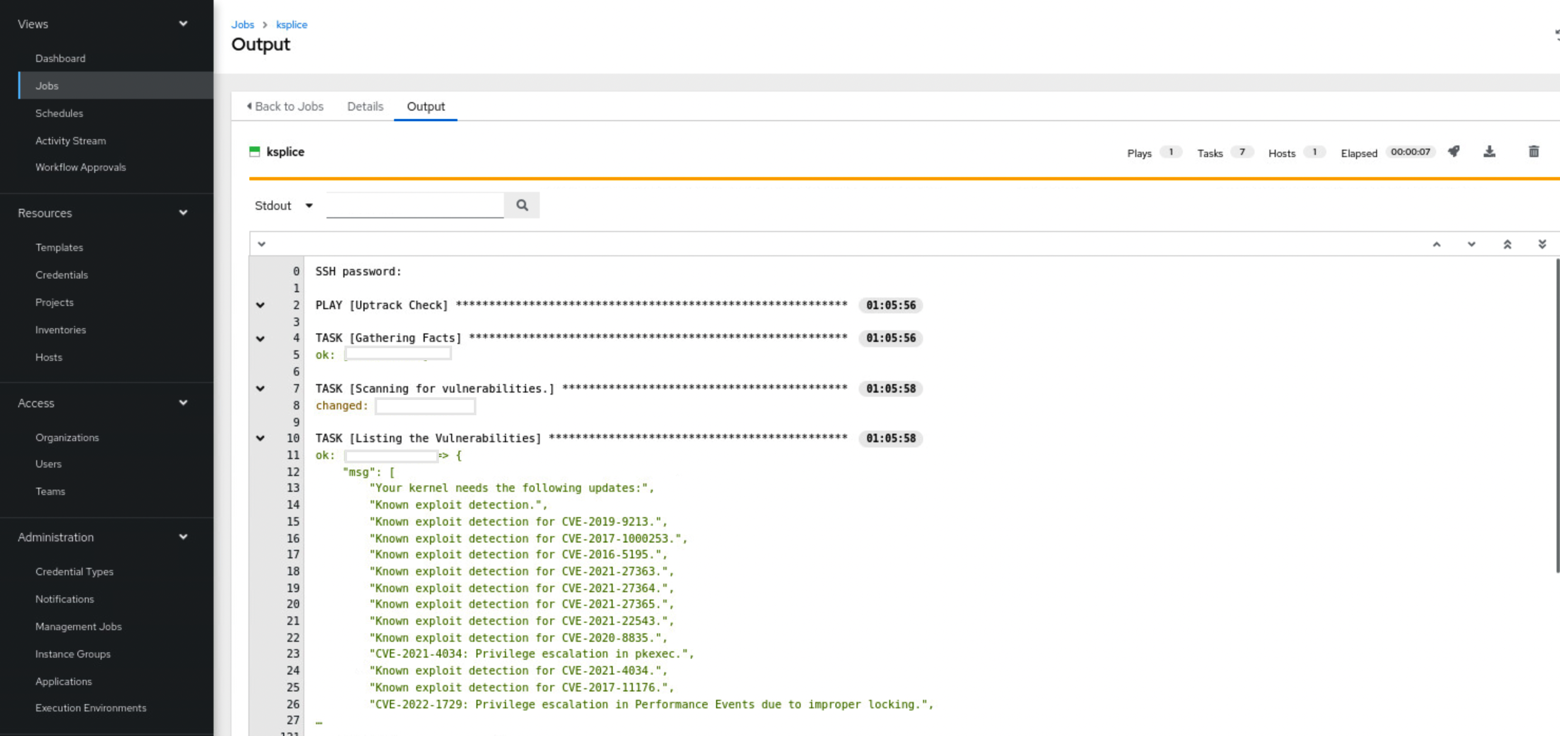
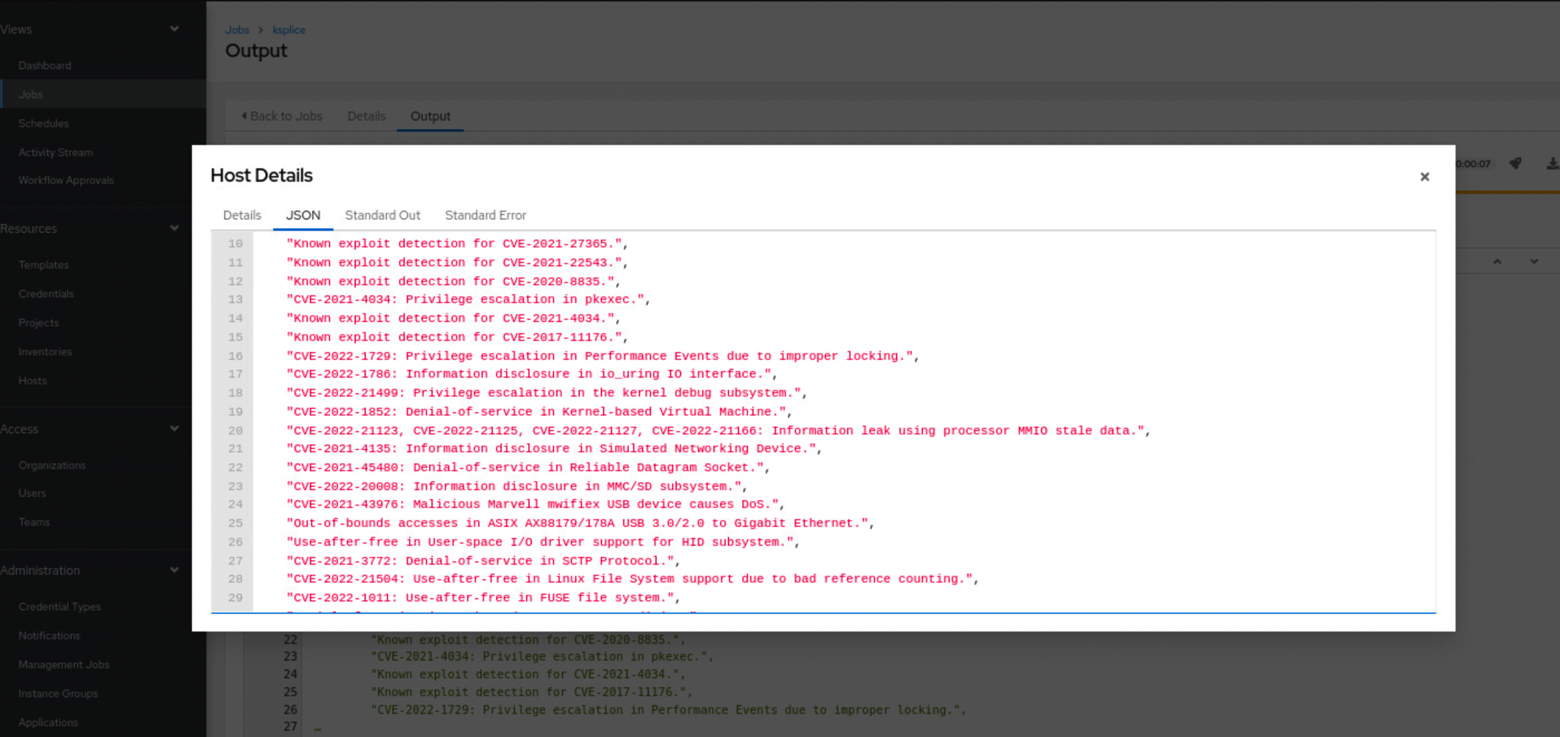
Now that we know the list of CVEs the machines are exposed to, the next step is to patch the machines.
By now, you may have inferred that with Oracle Linux Automation Manager capabilities, even the task of patching can be automated. If you did, you’re right.
Navigate to uptrack-online.yml and uptrack-offline.yml to learn how the patching can be performed.
Proceeding further, Oracle Linux Automation Manager also allows us to schedule the job at the required date and time.
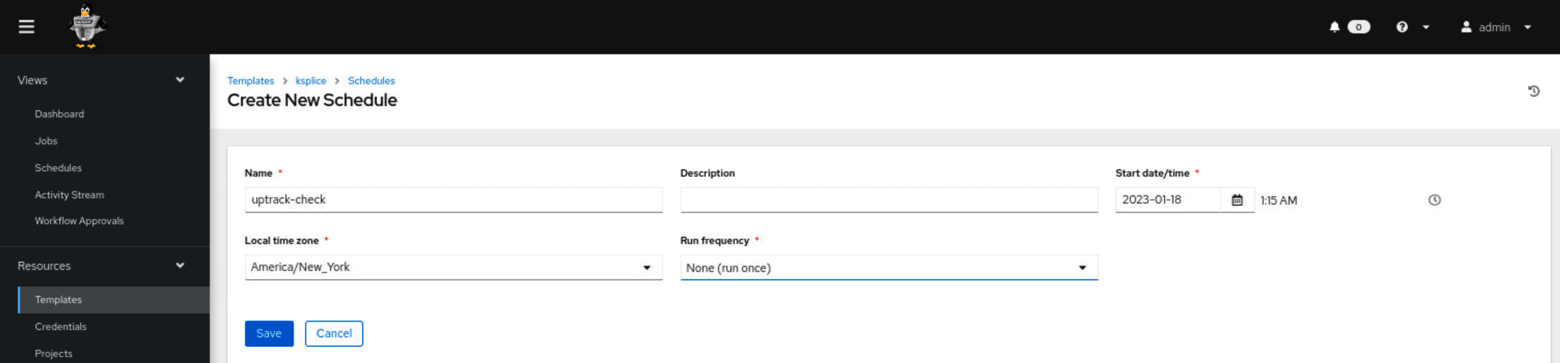
This is one of the numerous use cases where Oracle Linux Automation Manager can be leveraged to efficiently scan and patch systems, ensuring their security with ease.
Take a look at Oracle Ansible collections for more comprehensive examples.
