In a previous post, we showed you how to create an Object Storage bucket, and how to upload a simple HTML page to it. In this post, you learn how to control access to the Object Storage buckets by using Identity and Access Management (IAM) policies.
By default, a Tenant Admin Policy is created at the tenancy level. This policy allows anyone in the Administrator group to manage all the resources in the tenancy, including the Object Storage resources. This post shows you how to create a user group that controls access to specific services.
Create user groups
Before you create the policies, you need to create user groups first. In this post, you create 3 groups:
- ObjectStorageAdmins: Users with admin access to Object Storage resources
- ObjectStorageWriters: Users who can list and write objects to Object Storage buckets
- ObjectStorageReaders: Users who can download objects from Object Storage buckets
Let’s create these groups.
- Open the navigation menu, go to Identity, and then click Groups.
- Click Create Group.
- For the group name, enter ObjectStorageAdmins.
- For the description, enter Object Storage Administrators.
- Click Create Group. After the group is created, its details page is displayed.
- To add users to the group, click Add User to Group and select a user from the list.
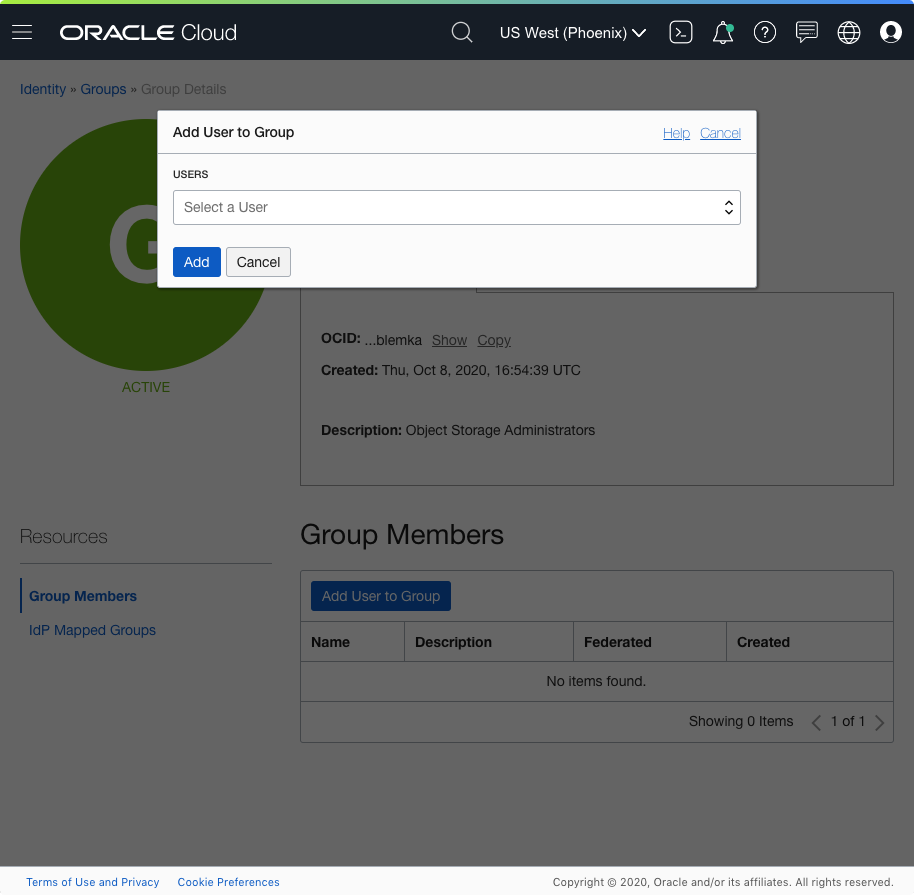

Figure 1: Add a User to a Group
- Repeat the preceding steps to create the remaining groups, using the unique names previously provided. When you’re done, you have three groups, as shown in the figure below.
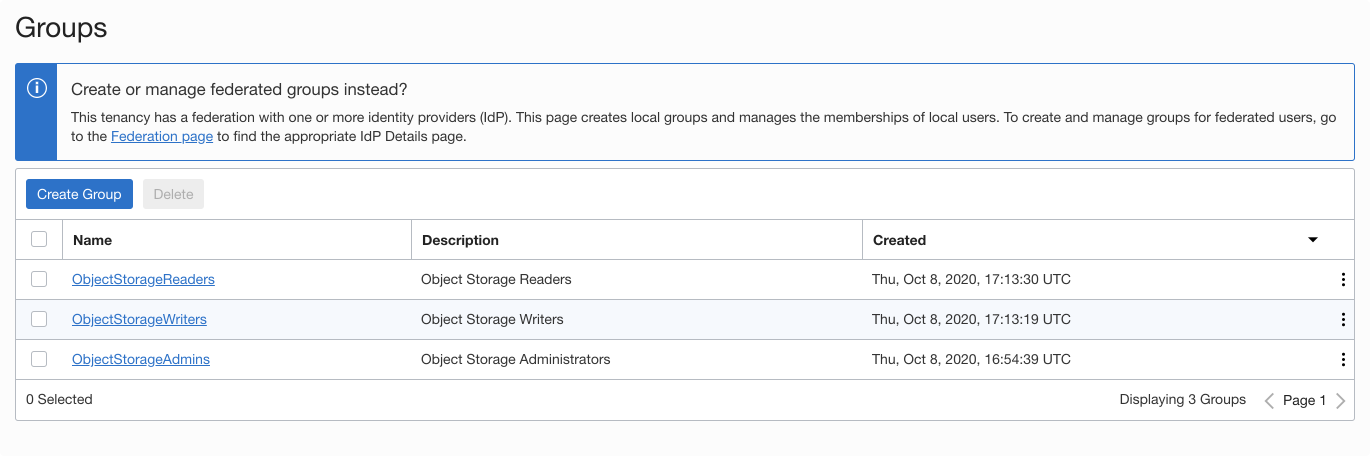

Create policies
With the user groups in place, you can now create policies. Create two policy statements for each group: one for buckets and one for objects.
Object Storage administrator policy
The first policy gives the ObjectStorageAdmins group the ability to perform all actions with Object Storage buckets and objects in all compartments.
You can create the policy at the tenancy level to grant access to all compartments through policy inheritance.
- Open the navigation menu, go to Identity, and then click Policies.
- Click Create Policy.
- For the policy name, enter ObjectStorageAdminsManagePolicy.
- For the policy description, enter Allow ObjectStorageAdmin group to manage object storage buckets.
- From the Compartment list, select your root compartment.
- Add the following policy statement, which allows ObjectStorageAdmins to manage buckets:
Allow group ObjectStorageAdmins to manage buckets in tenancy- Add a second policy statement that allows ObjectStorageAdmins to manage objects:
Allow group ObjectStorageAdmins to manage objects in tenancy- Click Create.
Object Storage writer policy
The next policy gives the ObjectStorageWriters group the ability to write objects to any Object Storage bucket in the tenancy. Alternatively, you could narrow the scope of the policy to a specific compartment.
The policy includes permissions to list the buckets, list the objects in a bucket, and create objects in a bucket. Although we use the manage verb, we narrow the scope by specifying the OBJECT_INSPECT and OBJECT_CREATE permissions.
Follow these steps to create the policy:
- Open the navigation menu, go to Identity, and then click Policies.
- Click Create Policy.
- For the policy name, enter ObjectStorageWritersPolicy.
- For the description, enter Allow ObjectStorageWriters group to write objects.
- From the Compartment list, select your root compartment.
- Add the following policy statement, which allows ObjectStorageWriters to read buckets:
Allow group ObjectStorageWriters to read buckets in tenancy- Add a second policy statement that allows ObjectStorageWriters to inspect and create objects:
Allow group ObjectStorageWriters to manage objects in tenancy where any {request.permission='OBJECT_CREATE', request.permission='OBJECT_INSPECT'}- Click Create.
Alternatively, you could use the where target.bucket.name statement to limit access to a specific bucket. For example, here’s how you could write a policy statement that allows the group to list and upload objects to MyBucket:
Allow group ObjectStorageWriters to manage objects in tenancy where all {target.bucket.name='MyBucket', any {request.permission='OBJECT_CREATE', request.permission='OBJECT_INSPECT'}}Object Storage reader policy
The last policy allows the users in the ObjectStorageReaders group to download objects from any Object Storage bucket in the tenancy. Just like before, you could narrow the scope to a specific compartment. The policy includes permissions to list the buckets, list objects in the buckets, and read existing objects in a bucket.
Follow these steps to create the policy:
- Open the navigation menu, go to Identity, and then click Policies.
- Click Create Policy.
- For the policy name, enter ObjectStorageReadersPolicy.
- For the description, enter Allow ObjectStorageReaders group to read objects and buckets.
- From the Compartment list, select your root compartment.
- Add the following policy statement, which allows ObjectStorageReaders to read buckets:
Allow group ObjectStorageReaders to read buckets in tenancy- Add a second policy statement that allows ObjectStorageReaders to read objects in a bucket:
Allow group ObjectStorageReaders to read objects in tenancy- Click Create.
You could also use the target.bucket.name and the compartment name to limit the access to a specific bucket in a compartment. For example, the following policy statements allow the users to list all the buckets in the Developers compartment, but to read the objects in and download only from MyBucket.
Allow group ObjectStorageReaders to read buckets in compartment Developers
Allow group ObjectStorageReaders to read objects in compartment Developers where target.bucket.name='MyBucket'Conclusion
In this post, you learned how to set up policies for object storage. You saw how to create groups and create separate policies for each group.
Resources
- Working with Oracle Cloud Infrastructure Object Storage
- Working with identity and access management (IAM) in Oracle Cloud Infrastructure.
- Common Policies
Every use case is different. The only way to know if Oracle Cloud Infrastructure is right for you is to try it. You can select either the Oracle Cloud Free Tier or a 30-day free trial, which includes US$300 in credit to get you started with a range of services, including compute, storage, and networking.
