Welcome back. A few days ago, we posted the first blog on the topic, Policies in Oracle Cloud Infrastructure (OCI) Data Integration, check it out! Today, we will explore Policies some more.
Based on the previous blog, we now understand the Policies required for Oracle Cloud Infrastructure Data Integration. In this blog, let us take some example use-cases and use Policy variables and resource-type combinations. Oracle Cloud Infrastructure Data Integration is an ETL service that can be used by administrators, architects, data engineers, ETL developers, test engineers, etc. Every team has a different role to work with Data Integration. For example, Test Engineers may want to test the jobs and check if the business scenarios have been validated. Let us consider an example where an organization wants to build a data mart in an Autonomous Data Warehouse (ADW). To build a data mart, Oracle Cloud Infrastructure Data Integration has been selected.
Now, for the given scenario let us understand the Policies.
- Consider the following groups that have been defined in OCI by the Administrators. These groups contain the respective users to perform defined tasks.
- DI_Admins – Oversee, manage, and monitor lifecycle management and security policies for the service
- DI_Developers – Develop and build data integration solutions
- DI_Execution – Execute, monitor and diagnose Data Integration solutions
- To enable Oracle Cloud Infrastructure Data Integration to perform the tasks in the user Tenancy, Oracle Cloud Infrastructure Administrators need to define the policy at the Tenant level or at the Compartment level. To create Policies, In the main menu —→ Under “Governance and Administration” —-→ Click on Identity and Select Policies.
It is recommended to define Policies at the Compartment level. The below Policies are defined at the Compartment level. For more information on the Policies, refer to the previous blog; Policies in Oracle Cloud Infrastructure Data Integration.
This Policy is to allow the service Data Integration to use User Virtual Cloud Network (VCN)
Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-8-14_17-1-8.png” data-mce-src=”https://confluence.oci.oraclecorp.com/download/attachments/274569972/image2020-8-14_17-1-8.png?version=1&modificationDate=1597404668602&api=v2″ data-unresolved-comment-count=”0″ src=”/wp-content/uploads/sites/121/2025/11/image3-10.png” style=”width: 600px; height: 120px; border-width: 1px; border-style: solid;” title=”Data Integration Service > Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-8-14_17-1-8.png”>
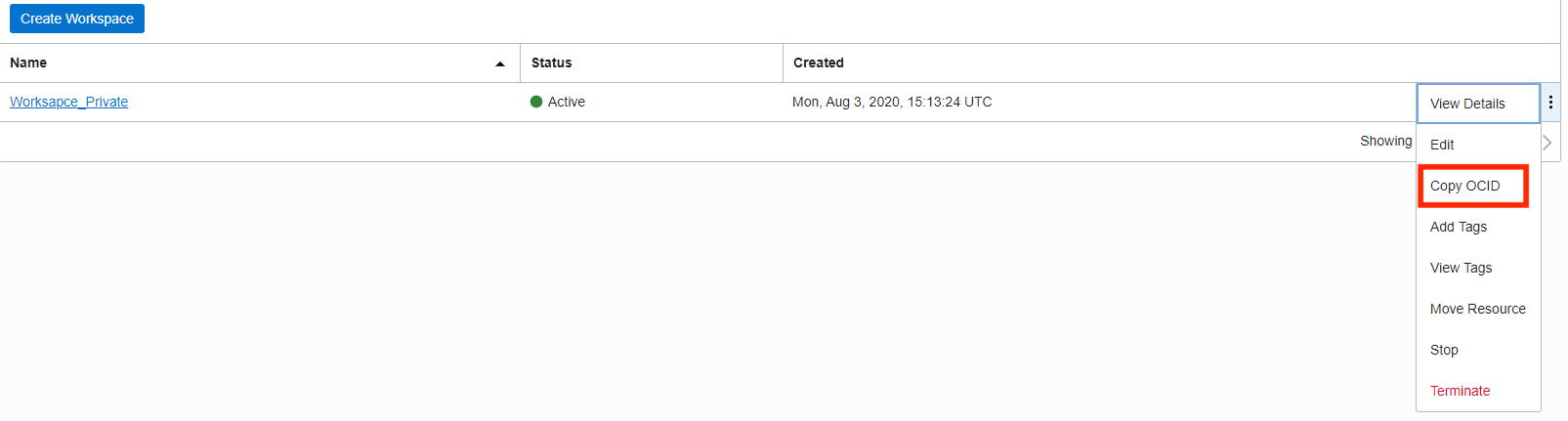
- Get the Workspace OCID by clicking on the Action menu “three dots” – For more information, refer to Workspaces
- Create a policy for DI_Admins so that the administrators can manage the creation of the workspace, access and configure work requests, etc. For this, the policy required is –
allow group <<Group_Name>> to manage dis-workspaces in compartment <<Compartment_Name>>
allow group <<Group_Name>> to manage dis-work-requests in compartment <<Compartment_Name>>
allow group <<Group_Name>> to use virtual-network-family in compartment <<Compartment_Name>>
allow group <<Group_Name>> to manage tag-namespaces in compartment <<Compartment_Name>>
This policy allows the DI_ADMINS to manage complete Oracle Cloud Infrastructure Data Integration Workspaces within the compartment.
-
Similarly, create the policies for DI_Execution and DI_Developers.
With the help of the below policies, the DI_Execution group can only execute the Tasks in the assigned Workspace OCID. The users under the DI_Execution group cannot modify the Data Flow/Task in the given Workspace OCID.
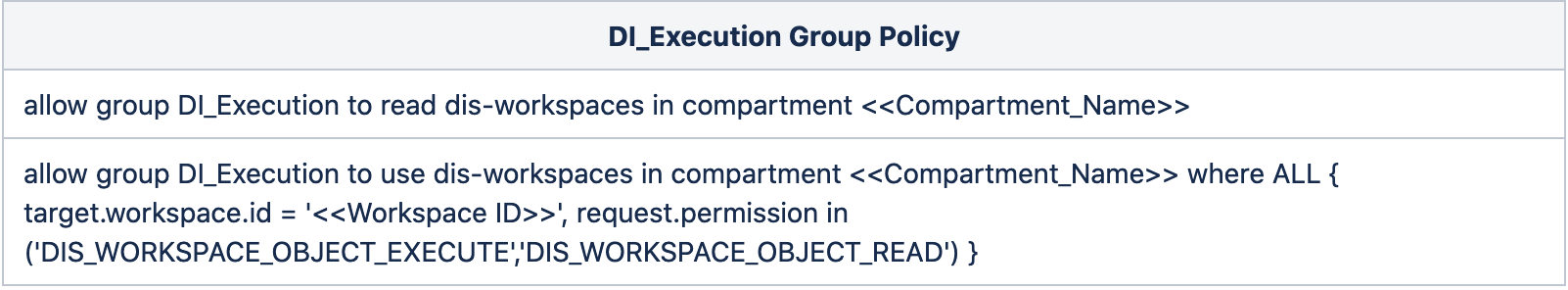
With the help of the below policies, the DI_Developers group can create/modify/execute the Tasks in the assigned Workspace OCID.
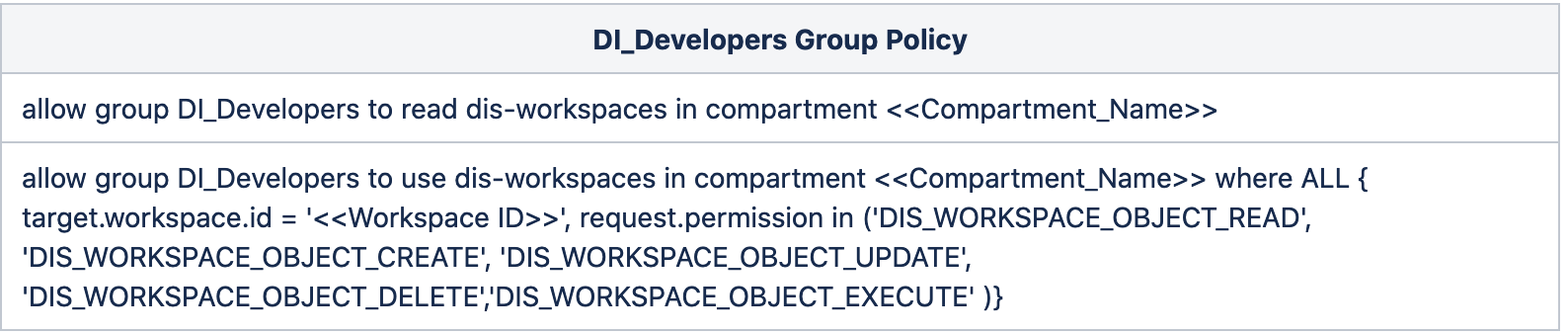
-
Along with the policies mentioned above in point 5, the group (developers/QA) should have access to the Object Storage for execution and development purposes. To understand more, please refer to – Policies in Oracle Cloud Infrastructure (OCI) Data Integration
– allow group <<user_group_name>> to use objects in compartment <<compartment-name>>
– allow group <<user_group_name>> to use buckets in compartment <<compartment-name>>
- Now let us test, how DI_Execution and DI_Developers group are able to access:
DI_Execution Group – DI_Execution group cannot create or edit a Data Flow but they can execute a Task that is consistent with their roles as QA. When the DI_Execution group tries to edit the Data Flow they will encounter the error – “Authorization failed or requested resource not found.”
DI_Developers Group – DI_Developers can create or edit a Data Flow, Create, Publish the Task, and can execute the Task which is consistent with their roles as developers.
This is how Policies can be used with Oracle Cloud Infrastructure Data Integration to get more control over the resources. To get further information on Policies, refer to Policies in the Service Documentation. We hope you are finding these blogs helpful! Let us know what you think.
For more details on Oracle Cloud Infrastructure Data Integration, check out the Tutorials and Documentation as well.
 Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-6-18_17-45-23.png” data-mce-src=”https://confluence.oci.oraclecorp.com/download/attachments/274569972/image2020-6-18_17-45-23.png?version=1&modificationDate=1594614459973&api=v2″ data-unresolved-comment-count=”0″ src=”/wp-content/uploads/sites/121/2025/11/image2-10.png” style=”width: 600px; height: 200px;” title=”Data Integration Service > Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-6-18_17-45-23.png”>
Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-6-18_17-45-23.png” data-mce-src=”https://confluence.oci.oraclecorp.com/download/attachments/274569972/image2020-6-18_17-45-23.png?version=1&modificationDate=1594614459973&api=v2″ data-unresolved-comment-count=”0″ src=”/wp-content/uploads/sites/121/2025/11/image2-10.png” style=”width: 600px; height: 200px;” title=”Data Integration Service > Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-6-18_17-45-23.png”> Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-8-14_17-30-5.png” data-mce-src=”https://confluence.oci.oraclecorp.com/download/attachments/274569972/image2020-8-14_17-30-5.png?version=1&modificationDate=1597406407012&api=v2″ data-unresolved-comment-count=”0″ src=”/wp-content/uploads/sites/121/2025/11/picture_1-3.png” style=”width: 600px; height: 220px;” title=”Data Integration Service > Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-8-14_17-30-5.png”>
Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-8-14_17-30-5.png” data-mce-src=”https://confluence.oci.oraclecorp.com/download/attachments/274569972/image2020-8-14_17-30-5.png?version=1&modificationDate=1597406407012&api=v2″ data-unresolved-comment-count=”0″ src=”/wp-content/uploads/sites/121/2025/11/picture_1-3.png” style=”width: 600px; height: 220px;” title=”Data Integration Service > Use-Cases on Policies for Oracle Cloud Infrastructure (OCI) Data Integration > image2020-8-14_17-30-5.png”>