Oracle Cloud Infrastructure (OCI) GoldenGate has recently been validated for connectivity with Oracle Database@Azure and your natural next questions may be what can I do with that and are there any other GoldenGate integrations with Azure? We’re here to give answers!
Oracle GoldenGate is one of the most popular real-time data fabric tools and already has numerous integrations with Azure (eg: Azure SQL, Azure Database for PostgreSQL, Azure Data Lake Storage, Azure Cosmos DB, Azure Synapse Analytics, Azure Event Hub, Databricks on Azure and Snowflake on Azure) This means that customers using Oracle Database@Azure with GoldenGate are now able to move data in/out of these data stores in real-time. Likewise, Oracle Database@Azure customers who need real-time transactions between Oracle databases in other infrastructure (such OCI, on-premise or other clouds) can also use the OCI GoldenGate service for that.
This investment in seamless connectivity doesn’t stop there. The OCI GoldenGate service has also validated integration for GoldenGate user identities to be fully managed by Microsoft Entra ID (formerly Azure Active Directory). We have certified a new configuration for OCI IAM to federate OCI GoldenGate authn/authz to Microsoft Entra ID. By setting up the federation between Entra ID and OCI IAM, you enable user access to services and applications in OCI GoldenGate using user credentials that are managed in Azure AD. This blog explains how to setup and configure this particular use case for OCI GoldenGate and Microsoft Entra ID in support of the wider set of use cases for GoldenGate and Oracle Database@Azure.
Prerequisites
To use IAM to federate authn/authz to Azure AD in an OCI GoldenGate Deployment, the following pre-requisites need to be met before creating the GoldenGate Deployment.
- An existing IAM domain with the following groups defined, which OCI GoldenGate requires for Role Based Access Control.
- GGS_Administrator
- GGS_Security
- GGS_Operator
- GGS_User
Details can be found here
Please ensure you have at least one active user in the GGS_Security Group. It could be either a local IAM user or a federated user in Azure AD provisioned in the IAM Domain. This user will be used to log in to your GoldenGate Deployment once it is up and running.
- Azure AD federation has been configured and enabled in that domain in the login screen. If this has not been done, here is the detailed tutorial and blog
Implementation Steps
- Log in to your OCI Console with the user with the proper privileges to create an OCI GoldenGate Deployment. The details of OCI GoldenGate Policies can be found here. Use that user to create an OCI GoldenGate Deployment, and make sure you choose IAM for “Credential store” in the last screen. If you don’t see that choice, that means either this tenancy’s IAM domain isn’t configured correctly to use OCI GoldenGate or that the tenancy is not IAM enabled
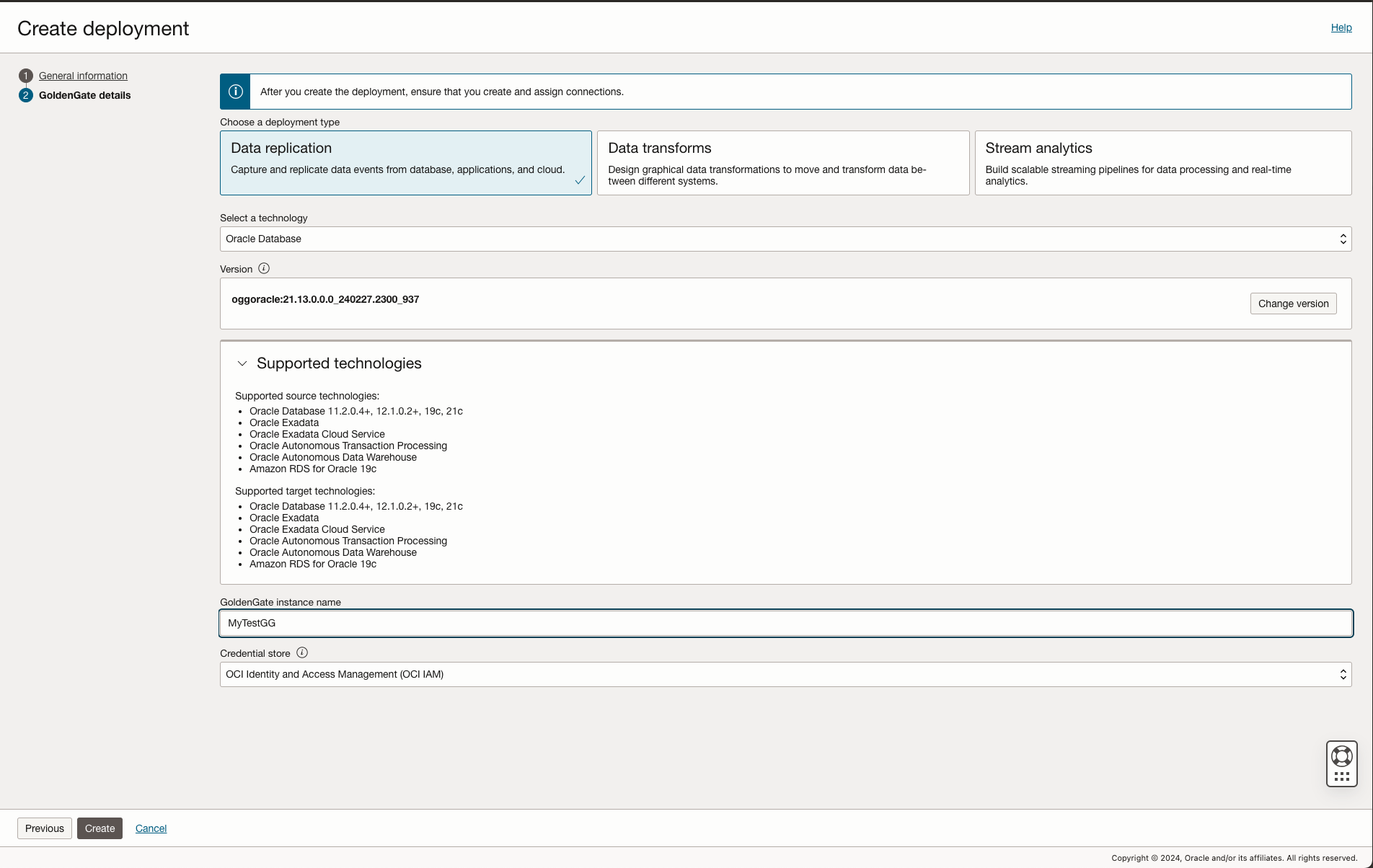
If you need details on creating GoldenGate Deployment, check out the documentation
- When the OCI GoldenGate Deployment is ready, try to access the WebUI console, and you will see that your login request has been redirected to your IAM login screen. Choose the Azure IdP option (The option name could be anything you chose when you created the Azure Federated IdP)
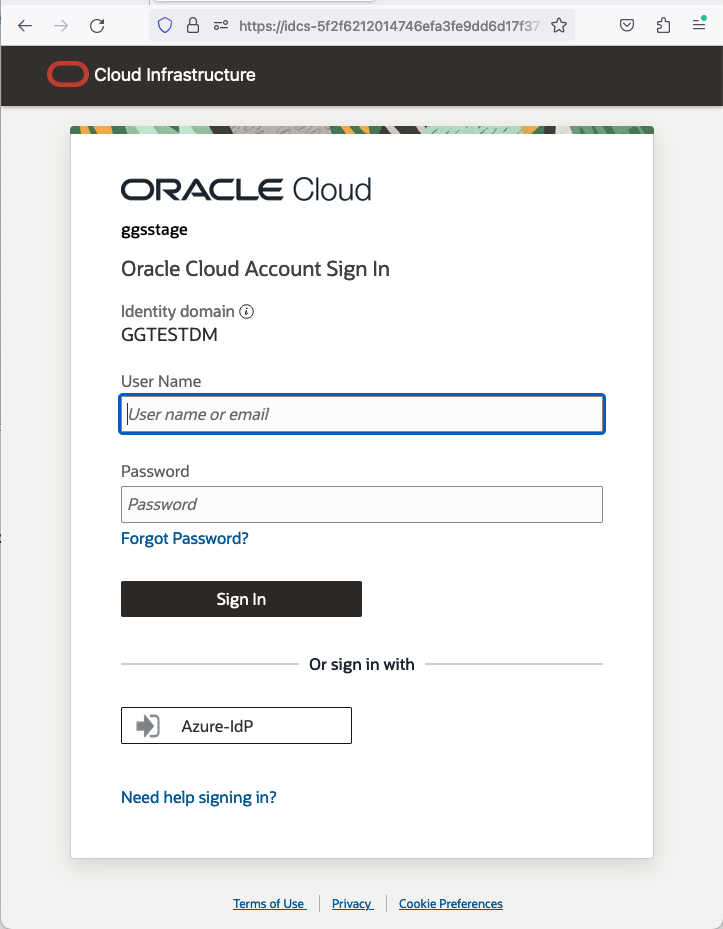
If you don’t see the Azure IdP option, you must perform all the tasks listed in Pre-requisite Step 2.
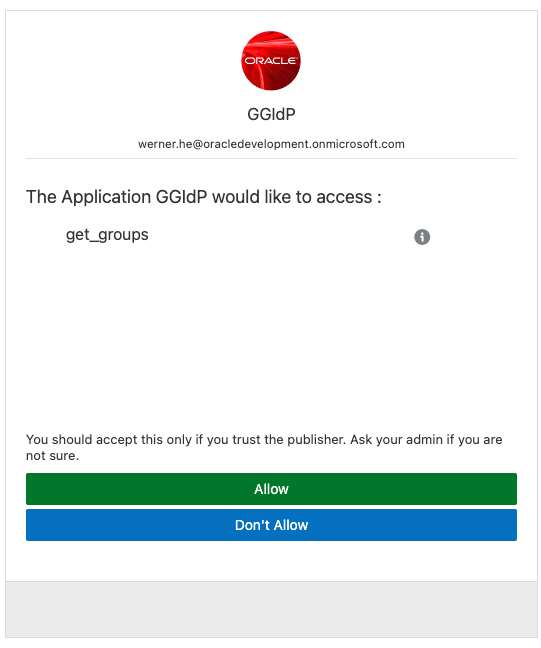
- Once you input your Azure login information correctly, you will see the following screen if this is the first time you log in to GoldenGate deployment. Just click “Allow”.
Then, you will be redirected to the GoldenGate adminsrvr page, as shown below.
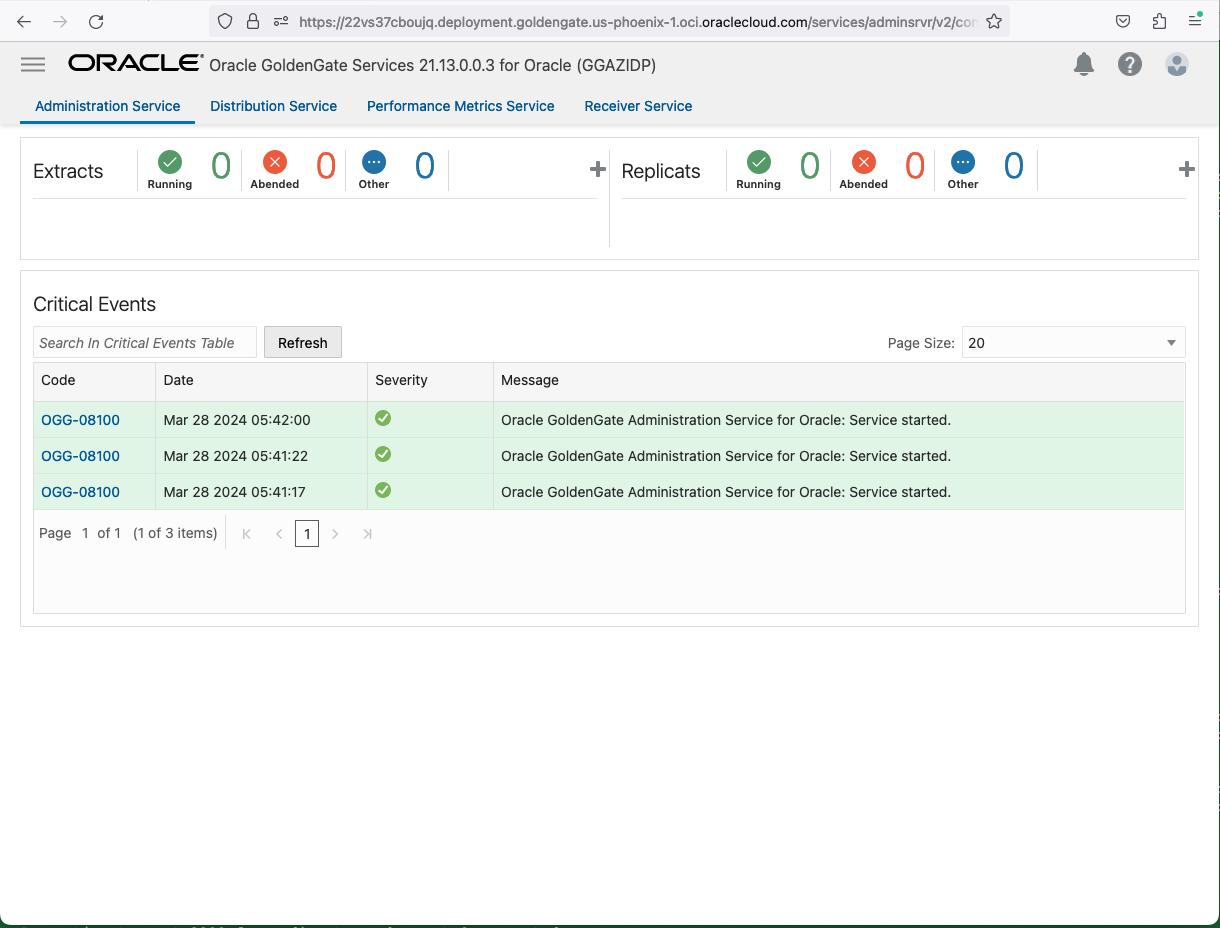
- Depending on which group (GGS_Security/GGS_Administrator/GGS_Operator/GGS_User) this user is assigned in your IAM Domain, it will have appropriate privileges to manage this GG Deployment.
- To access the GoldenGate deployment using adminclient, you will have two choices.
- Use an OCI IAM local user.
To use an OCI IAM local user, you just need to use the username and password in the connect command in adminclient
Adminclient>connect https://<GG Deployment Host> user <username> password <password>
Please ensure this user belongs to one of the four GGS groups in this domain.
OR
-
- Use a token from the IAM Domain for the Oracle Cloud Services Application.
This is a bit complicated but very useful as the userid and password in 5.a might not work in Adminclient when you try to use a userid/password that is managed in Azure AD. This also applies to the user, if that user has MFA enabled in their IdP.
First, we must track down the Confidential Application that was created when you created your deployment with IAM as the credential store.
Goto Identitty->Domains -> <Your Domain>, like the screenshot below
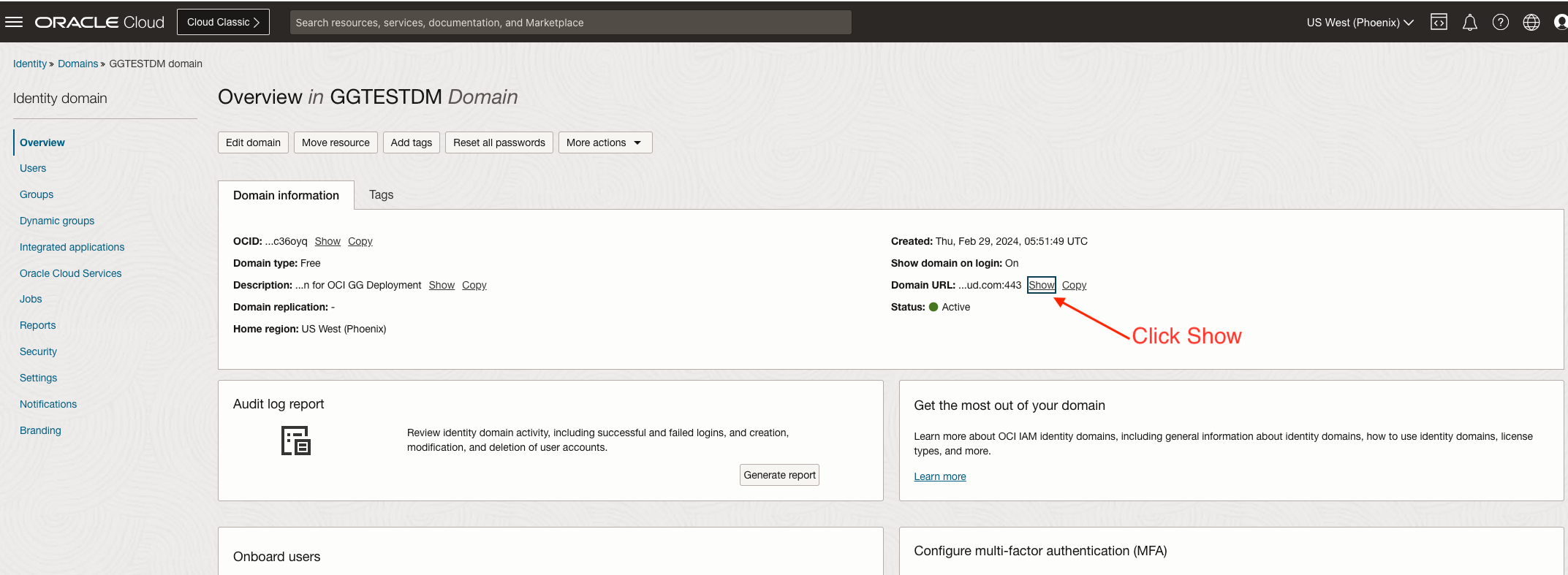
Click ‘Show’, then copy the entire URL. This is your IAM domain URL, which will be used later.
Then click Oracle Cloud Service, as shown in the following screenshot.
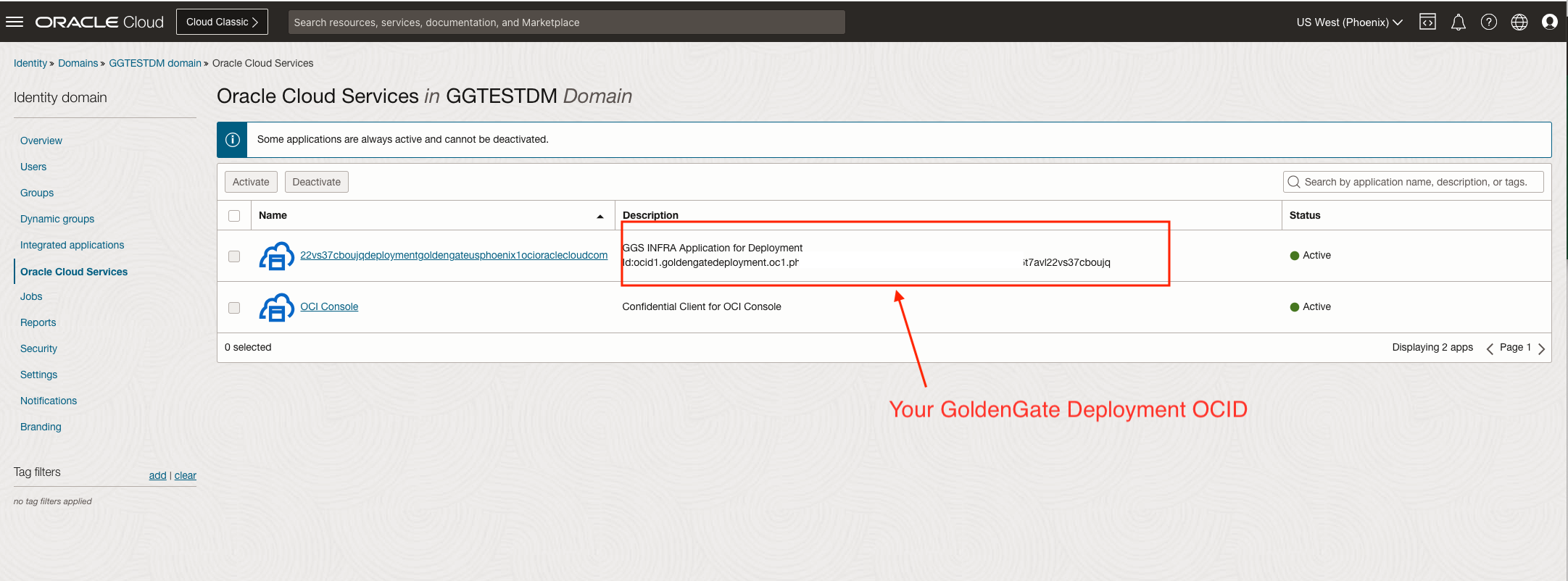
The name of the Application is usually your GoldenGate Deployment FQDN name with all the dots removed. You will also be able to see your GoldenGate Deployment OCID in the description field. Click on the Application name. You will find the client ID, client secret, and scope value, which will be needed to request a token.
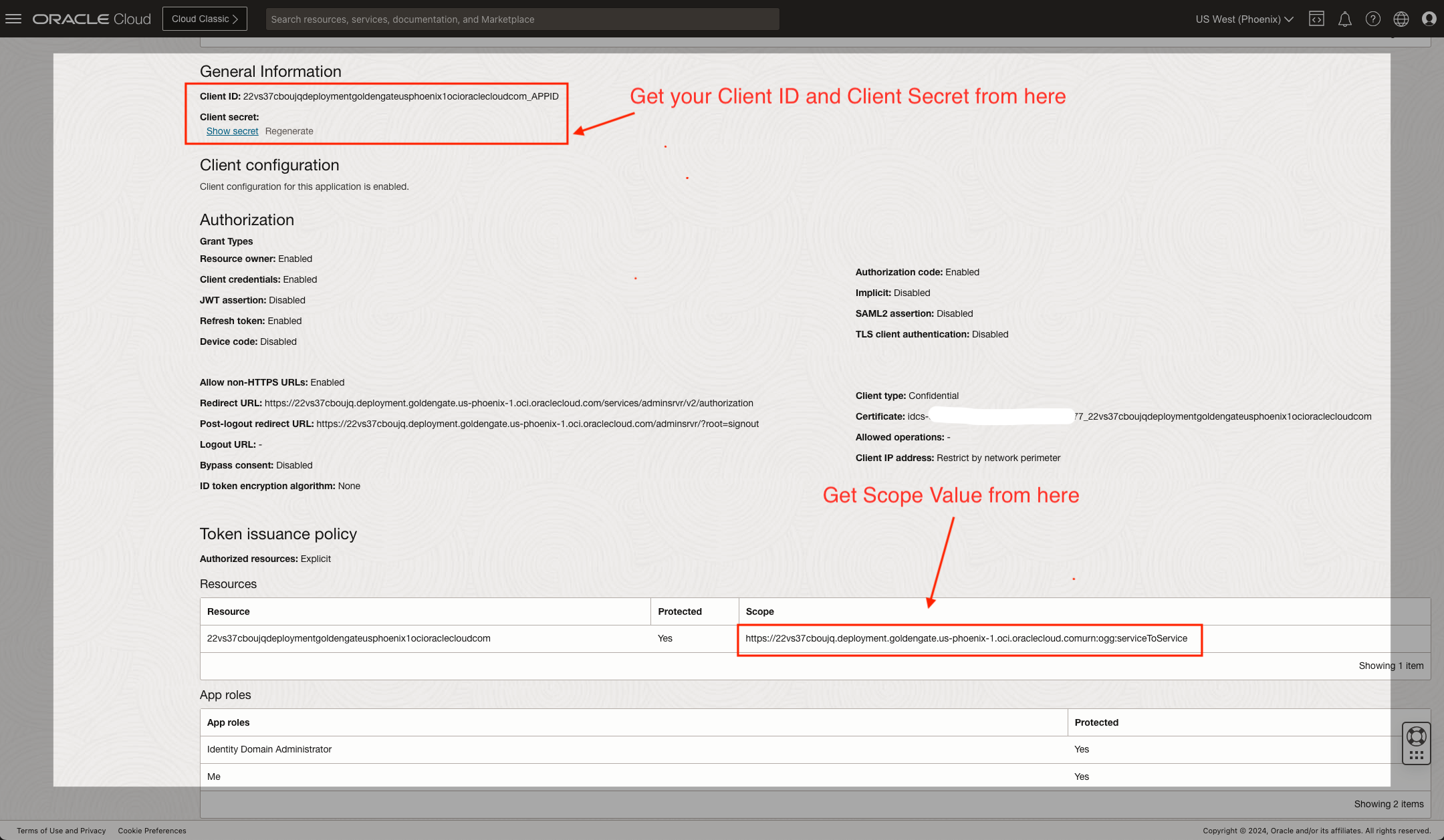
Write down the Client ID. Click “Show secret”, then copy and write down the client secret. Write down the Scope.
Now, with the IAM Domain URL you obtained earlier, append the following to the URL and use the following curl command.
Shell>curl -s <IAM Domain URL>/.well-known/openid-configuration
For example
Shell>curl -s https://idcs-5f2f62120xxxxxxxxxxxxx3777.identity.oraclecloud.com:443/.well-known/openid-configuration
Track down the “token_endpoint” field from the response. It will be something like this.
“token_endpoint” : “https:// idcs-5f2f62120xxxxxxxxxxxxx3777.identity.oraclecloud.com:443/oauth2/v1/token”,
This is the URL that we need to use to request the token. The command
Shell>curl -POST <token_endpoint url> -u <client_id>:<client_secret> –data ‘grant_type=client_credentials&scope=<Scope>’
For example
curl –request POST ‘https:// idcs-5f2f62120xxxxxxxxxxxxx3777.identity.oraclecloud.com:443/oauth2/v1/token’ \
-u 22vs37cboujqdeploymentgoldengateusphoenix1ocioraclecloudcom_APPID:47c8xxxx-xxxx-xxxx-xxxx-xxxx303d63ff \
–data ‘grant_type=client_credentials&scope=https://22vs37cboujq.deployment.goldengate.us-phoenix-1.oci.oraclecloud.comurn:ogg:serviceToService’
Then, you will get the token value returned, as shown in the screenshot below.
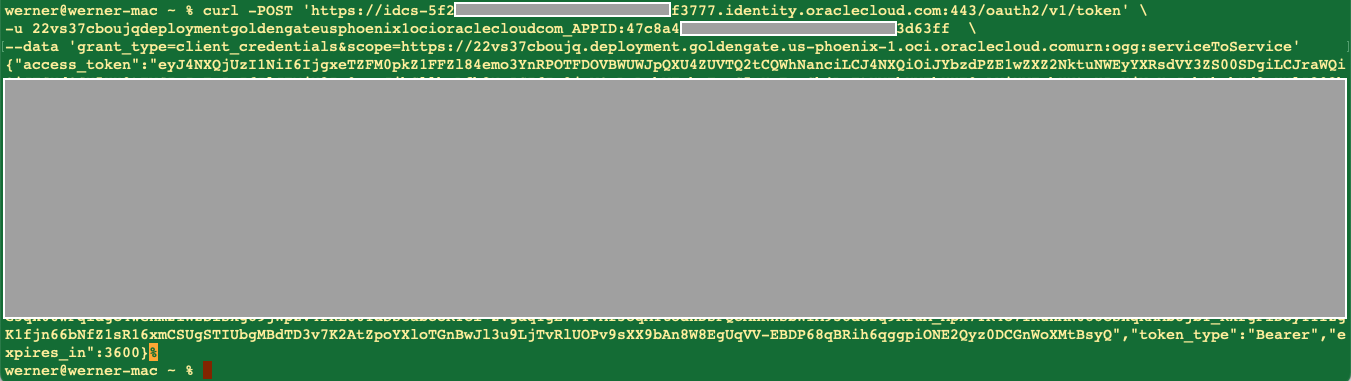
Write down the content of access_token.
You can use it in the adminclient connect command to connect to GG Deployment.
Adminclient>connect https://<GG Deployment FQDN or IP Address> token <access_token_content> !
For example
Adminclient>connect https:// 22vs37cboujq.deployment.goldengate.usphoenix1.ocioraclecloud.com token xxxxxxxxxxxx(the very long token string)xxxxx
You can also store the token as local credentials in adminclient, then refer to the alias when connecting.
For example
Adminclient>add credentials ggs-token token xxxxxxxxxxxx(the very long token string)xxxxx
Adminclinet>info credentials *
Credentials Name Type User Name
——————————– ———– ——————————–
ggs-token Token
Adminclient> connect https:// 22vs37cboujq.deployment.goldengate.usphoenix1.ocioraclecloud.com as ggs-token !
Conclusion
As we’ve shown, it can be pretty straight-forward to setup and manage the OCI GoldenGate user identities from Microsoft Entra ID. With a couple prerequisites and a few setup steps, anyone can externalize user identies for consolidated management in the Azure systems. These identity management capabilities go a long way towards delivering on the shared vision for multi-cloud solutions, and demonstrate Oracle’s commitment to mission-critical services running with Oracle Database@Azure, Azure Cloud, Microsoft Entra ID and OCI GoldenGate.
