Do your systems require compliance with FIPS on security then Oracle Cloud Infrastructure provides the flexibility to meet a key area of compliance for your Windows Server workloads: FIPS (Federal Information Processing Standard) compliance. The ability to create a FIPS-compliant server is a critical milestone in moving to the cloud.
This post discusses how to achieve a FIPS-compliant Windows Server, describing the core steps for Windows Server 2016 server and referring to the necessary resources for Windows Server 2008 R2 and 2012. In particular, this post focuses on how to bring this functionality to Oracle Cloud Infrastructure and some things to consider while attempting to meet the FIPS 140 standard. The reference section provides links to Microsoft sites that define and document FIPS compliance for building Windows Servers that are compliant.
The FIPS 140-2 Standard
The United States and Canadian governments have created specific requirements for ensuring security with in their environments, these requirements have led to the FIPS standard. FIPS is a standard for government computer security. The standard was initially published in May 2001 and then updated in December 2002 by the National Institute of Standards and Technology (NIST) and the Communications Security Establishment of Canada. The standard identifies levels of security and cryptographic module validation. This standard applies to any security system that is used within the US Federal government. The current standard is FIPS 140-2 for all government systems.
For more information, see FIPS 140-2.
Deeper into FIPS
One of the key things to know is that to be FIPS compliant you must disable some encryption algorithms and enable others. The Secure Channel Security Package is forced to use TLS, so the following key Cipher Suites must be disabled:
- TLS_RSA_WITH_RC4_128_SHA
- TLS_RSA_WITH_RC4_128_MD5
- SSL_CK_RC4_128_WITH_MD5
- SSL_CK_DES_192_EDE3_CBC_WITH_MD5
- TLS_RSA_WITH_NULL_MD5, and TLS_RSA_WITH_NULL_SHA
Remote Desktop Protocol is scoped to use the following algorithms:
- CALG_RSA_KEYX – RSA public key exchange algorithm
- CALG_3DES – Triple DES encryption algorithm
- CALG_AES_128 – 128 bit AES
- CALG_AES_256 – 256 bit AES
- CALG_SHA1 – SHA hashing algorithm
- CALG_SHA_256 – 256 bit SHA hashing algorithm
- CALG_SHA_384 – 384 bit SHA hashing algorithm
- CALG_SHA_512 – 512 bit SHA hashing algorithm
For Windows Server 2008 and later, ensure that your disk encryption is AES-256. For .Net, ensure that you are using the correct CNG Validated Cryptographic Modules.
For more information, see FIPS 140 Validation.
Making Your Windows Server FIPS Compliant
Now that you have an idea of what FIPS is, you need to know how to make your Windows Server environment FIPS compliant. Microsoft has done most of the work for the compliant DLLs and encryption integration. Follow the processes outlined in How to Use FIPS Compliant Algorithms to produce a FIPS-compliant Windows Server.
To install and use the FIPS-compliant algorithms, use the instructions in CAPI Validated Cryptographic Modules. You must install the correct DLLs and make some changes to the WebHost\config and MonitoringView\web.config files.
Implementing FIPS Compliance on Windows Server 2016
Start with the base Windows Server 2016 image from the Oracle Cloud Infrastructure Console. After the server is built, connect to it and then start the FIPS update outlined by Microsoft.
The hardest part of the process is getting the gacutil.exe program. To get this program, download the .Net 4.0 SDK. When you have the gacutil.exe program, you can start making the necessary changes.
Follow the instructions from Microsoft to start the process, as shown here.
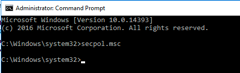
- Open CMD.exe as an administrator, and then run secpol.msc.
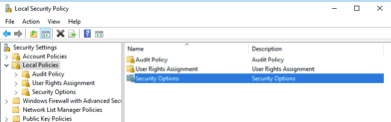
- In the Local Security Policy window, click Local Policies and then click Security Options.
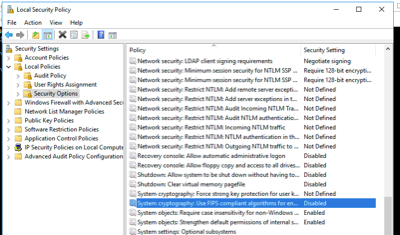
- Scroll to System cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing and double-click it.
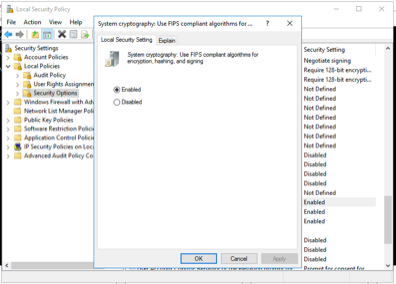
- Select Enabled and then click Apply.
Your Windows Server 2016 is now FIPS compliant. The Microsoft website has more in-depth information about enabling such things as Operations Manager and Web Services and enabling Windows Server 2008 R2 and 2012. Now it is time to go build your own FIPS compliant Windows Servers in the Oracle Cloud Infrastructure to start your free trial make sure to check out the try it page (https://cloud.oracle.com/tryit) for more details.
Resources
- Microsoft FIPS:
- Microsoft FIPS validation: https://docs.microsoft.com/en-us/previous-versions/tn-archive/cc750357(v=msdn.10) or http://technet.microsoft.com/en-us/library/cc750357.aspx
- FIPS algorithm implementation: https://support.microsoft.com/en-us/help/811833/system-cryptography-use-fips-compliant-algorithms-for-encryption-hashi
- FIPS system cryptography: https://support.microsoft.com/en-us/help/811833/system-cryptography-use-fips-compliant-algorithms-for-encryption-hashi
- FIPS 140 validation: https://docs.microsoft.com/en-us/previous-versions/tn-archive/cc750357(v=msdn.10)#_capi_validated_cryptographic
- FIPS 140-2: https://csrc.nist.gov/csrc/media/publications/fips/140/2/final/documents/fips1402.pdf
- Wikipedia: https://en.wikipedia.org/wiki/FIPS_140-2
