Imagine a situation in which you are trying to connect into your Oracle Cloud Infrastructure instance but either you forgot which key you used or, for some unknown reason, your opc user SSH key got corrupted or deleted. It might be scary at first, but the process to recover an opc user SSH key on Oracle Cloud Infrastructure is easier than you think.
So if you get a “Permission denied (publickey,gssapi-keyex,gssapi-with-mic)” error when trying to connect via SSH, follow this process to recover your key.
You can also use Oracle Cloud Infrastructure Serial Console maintenance mode boot option as an alternative method to recover opc ssh key. See “Troubleshooting Instances from Instance Console Connections” public documentation section for more details.
Summary
- Stop the instance that you can’t log in to.
- Detach the boot volume.
- Attach the boot volume to a running Linux instance.
- Run the iSCSI commands to attach the device and make it visible to the local operating system.
- Fix the authorized_keys file.
- Unmount the device and detach it by running the iSCSI commands.
- Attach the boot volume to the original instance and start it.
Process
-
Stop the instance that you can’t connect to. In the Oracle Cloud Infrastructure Console, go to the details page for the instance and click Stop. More details in “the public documentation“.
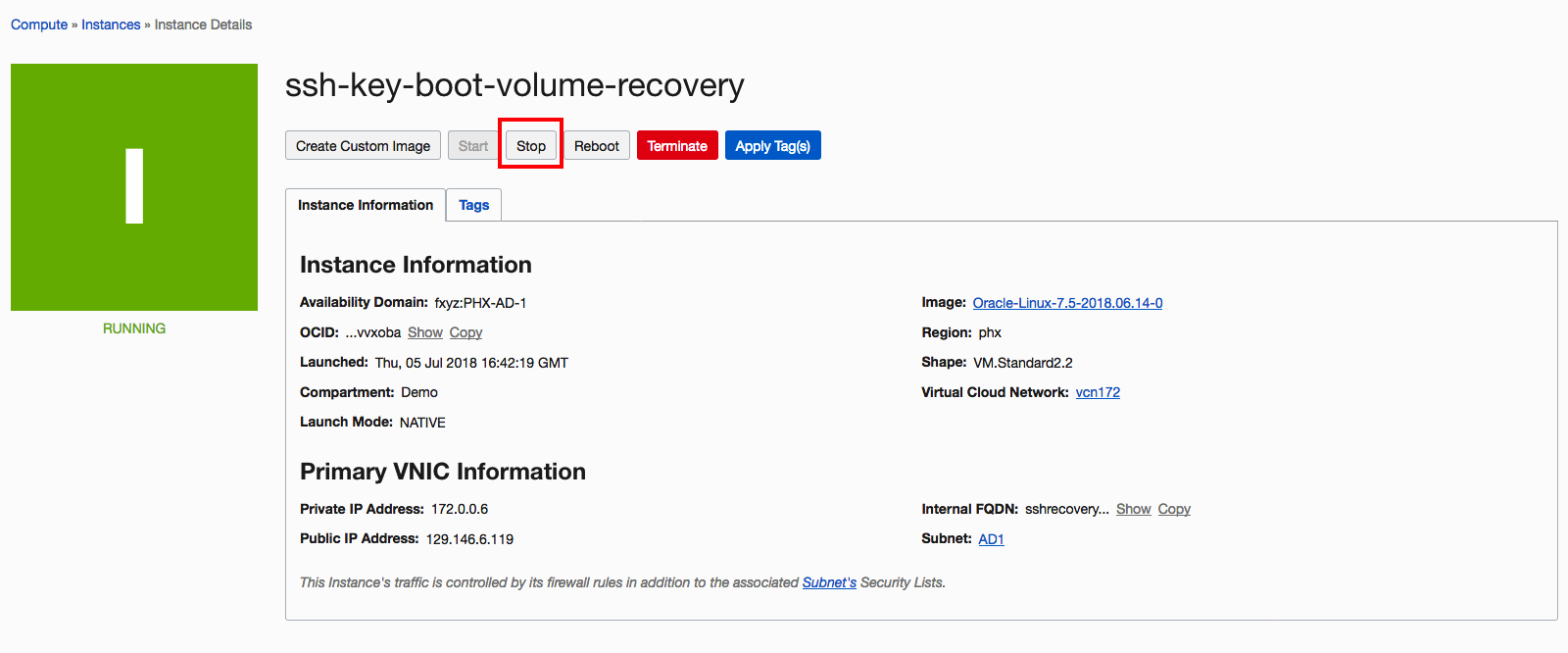
- Detach the boot volume. In the Boot Volume section, click the Actions icon and choose Detach. See “Detaching a Boot Volume” for additional details if needed.
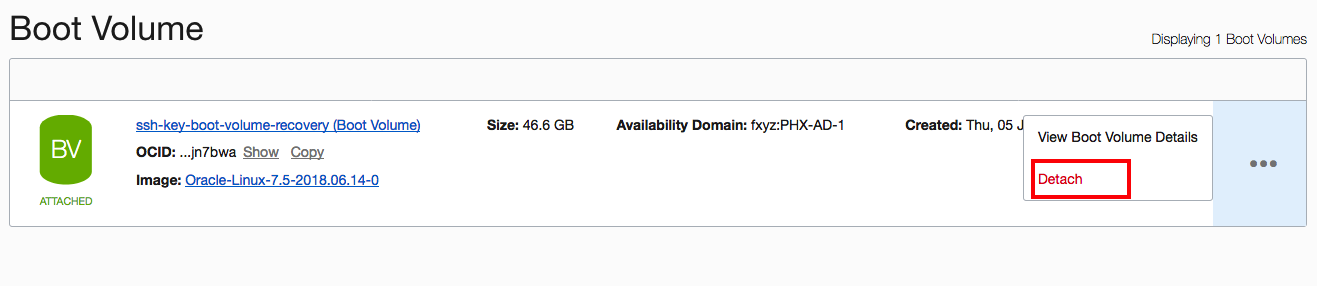
- Attach the boot volume to another Linux instance by going to the details page of a different VM, clicking Attach Block Volume, and then selecting the boot volume that you just detached in the previous step. Be sure to select Read/Write access. For additional details see “Attaching a Boot Volume” option available in the public documentation portal.
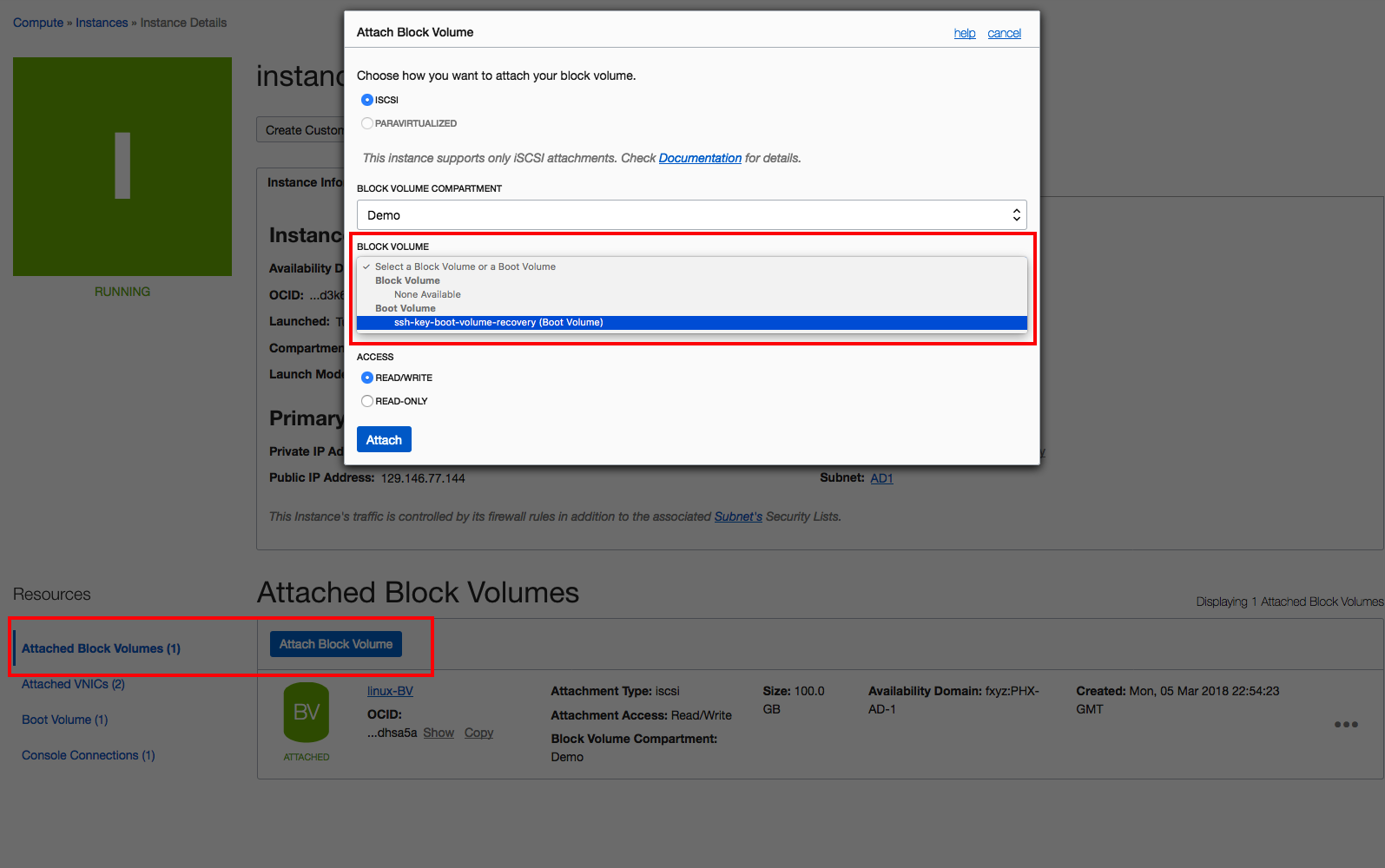
- After the boot volume attachment is completed (the BV icon is green), connect through SSH in the running VM and run the iSCSI commands to make that new disk available and visible by the OS.
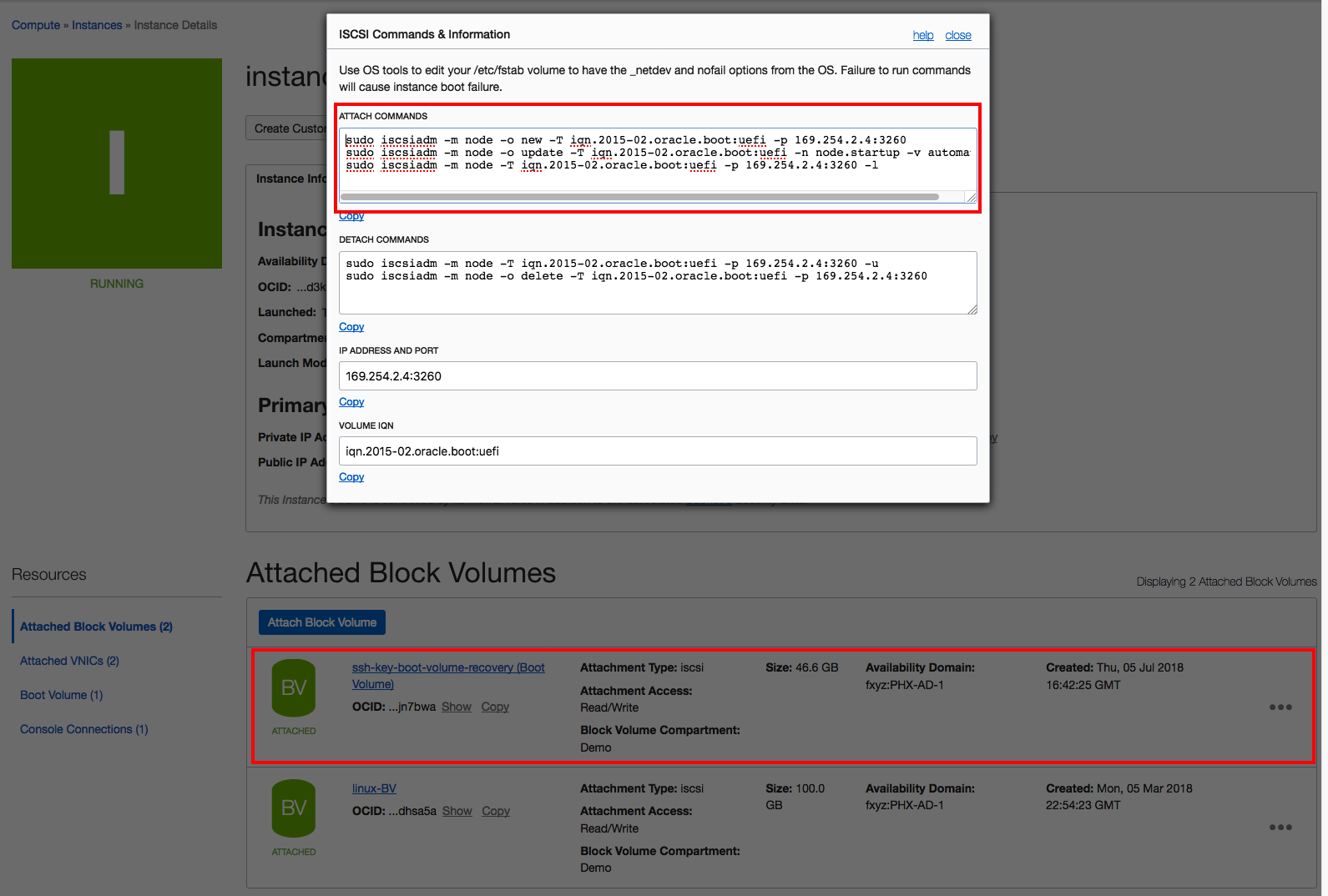
Your boot-volume should appear as /dev/sdb.
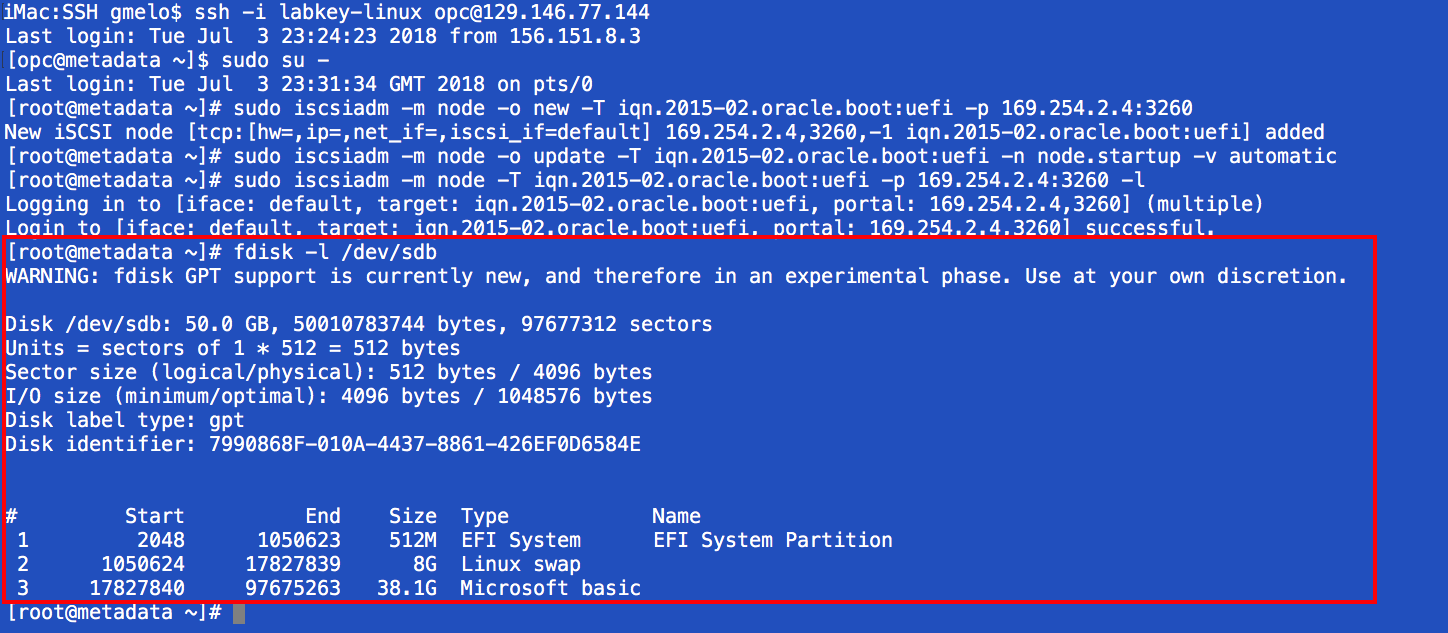
- Make /dev/sdb3, which is the root (/) partition where you can recover the opc SSH key file, available to the local operating system using “mount” command. Be sure to use the -o nouuid option; otherwise, you will see the “mount: wrong fs type, bad option, bad superblock on /dev/sdb3” error message.
$ sudo mount -o nouuid /dev/sdb3 /mnt
- Fix the opc SSH key by editing the /mnt/home/opc/.ssh/authorized_keys file and adding your SSH key public file.
$ sudo vi /mnt/home/opc/.ssh/authorized_keys
After you add or change the SSH public key you need to use, save and exit it.
- Run umount /mnt.
$ sudo umount /mnt
- Detach the iSCSI boot volume by running the detach iSCSI commands.
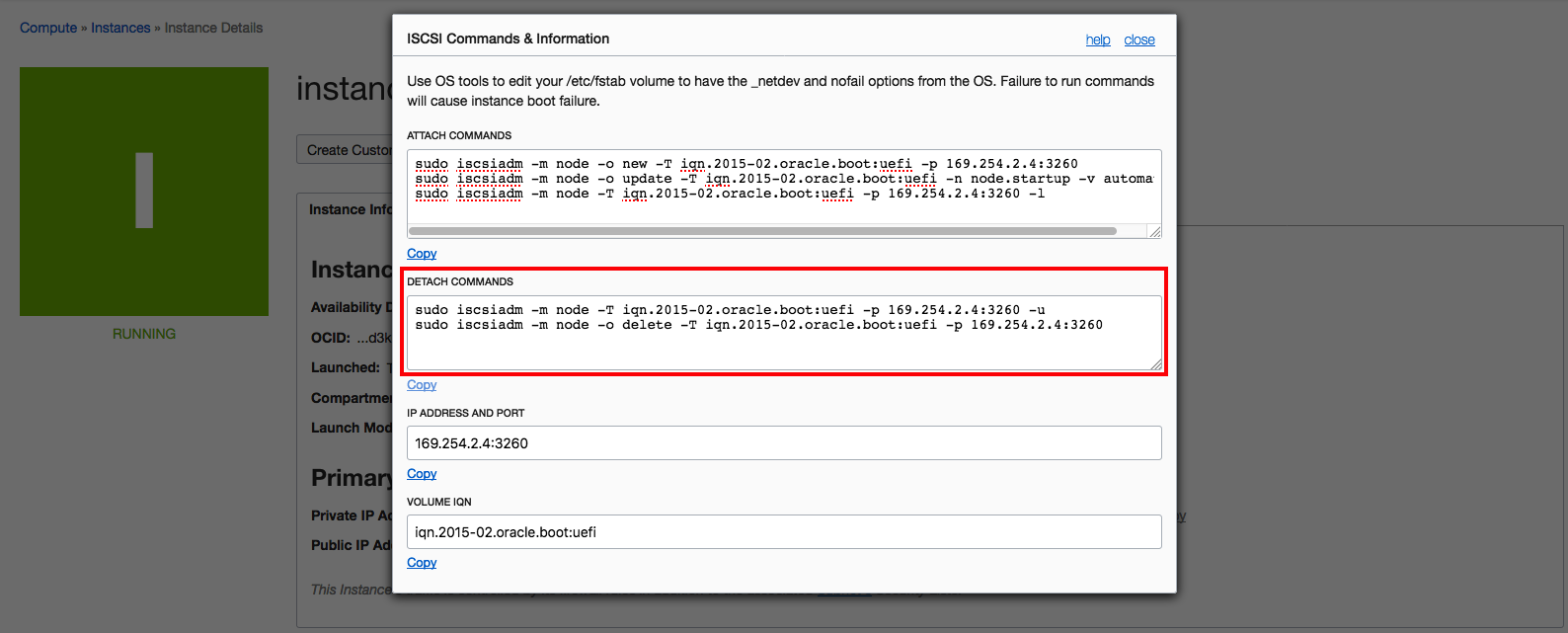
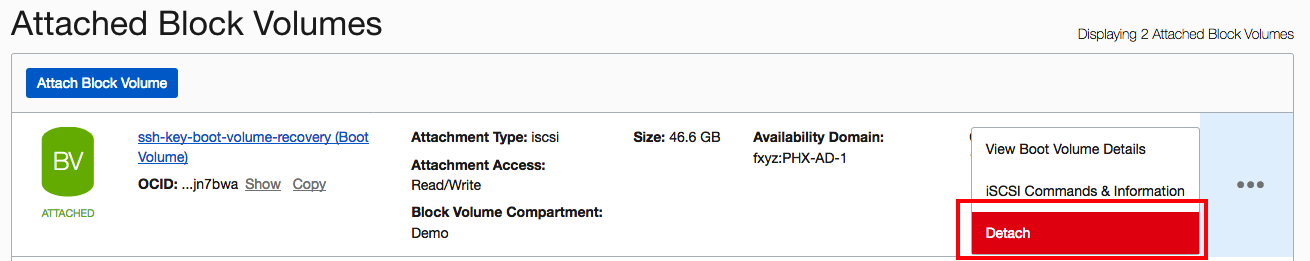
- Ensure that the /dev/sdb disk is no longer available or visible through the SSH connection, and then detach it.
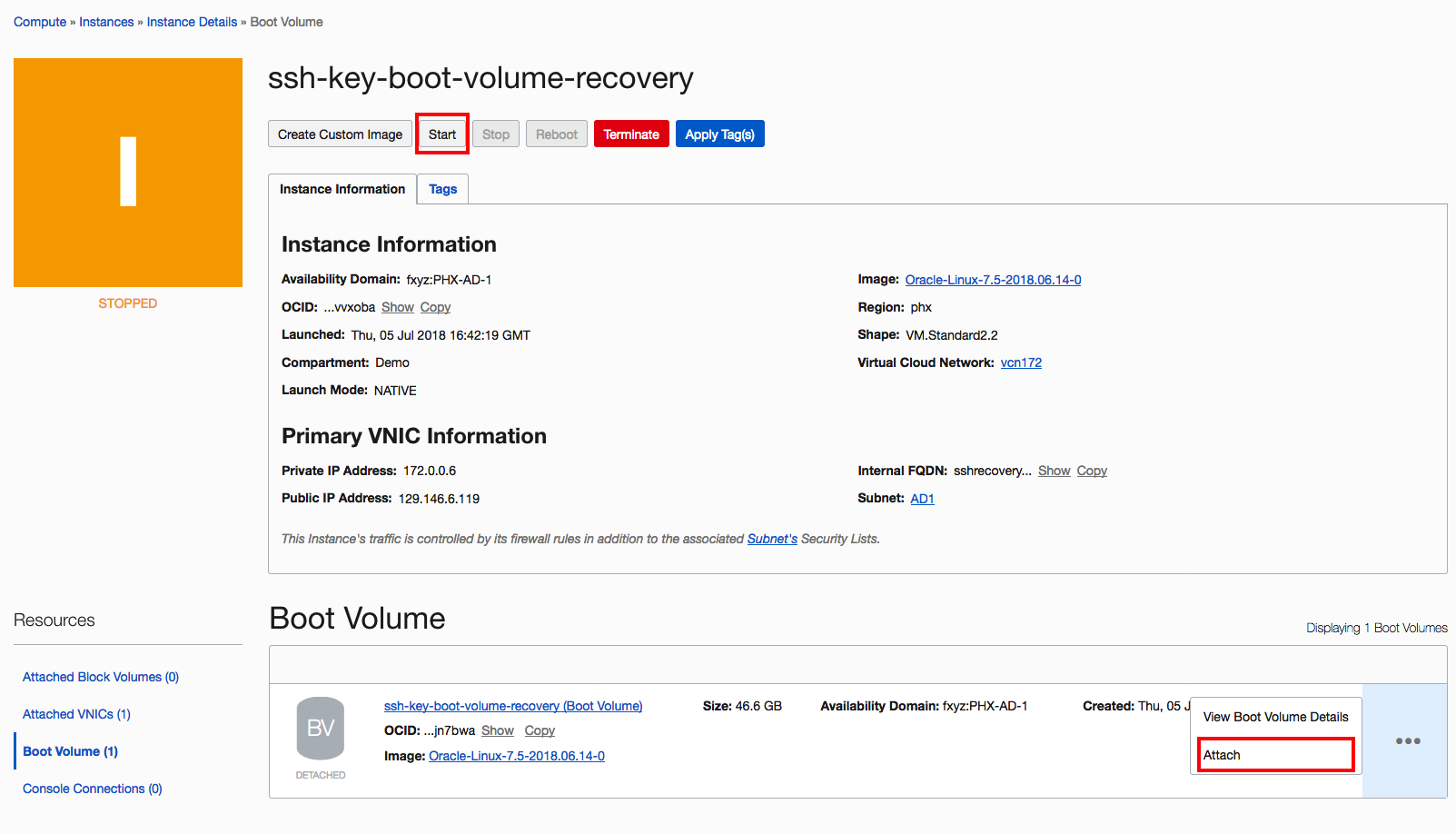
- Reattach the boot volume to the instance where you wanted to recover the SSH key, wait for it to become operational (green icon) and start it.
That’s it. You recovered your opc user SSH key and you can now log back in to the instance. You can also use this process for troubleshooting the root (/) partition.
