Having spent my entire career in technology, I feel like I am pretty savvy about email scams. They used to be fairly obvious and I know better than to try to help a Nigerian prince get their fortune back so that they can share it with me. But as we have all become more savvy, unfortunately so have the threat actors.
There are three primary categories of email-based advance threats including impersonation, imposters, and URLs and attachments. The URLs and attachments scams are looking for someone to click a URL or attachment that performs an action. You can use best practices like only opening attachments and URLs from trusted sources, but having a tool like FireEye helps ensure that mistakes don’t happen.
I think the scariest threats are impersonations and imposters. Once a threat actor has convinced a person that the threat actor is someone else, the imposter is able to convince even the most well-informed end users to provide them with all the access and information they request. For example, if my executive is Mike Smith and he sent me an urgent message to take care of payment, I would fulfill his request. In this example, the email address is clearly not my executive’s email since it was sent from a personal account. This is easier to avoid.
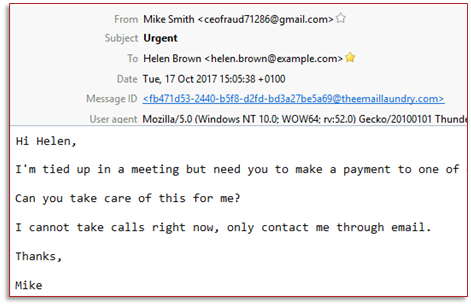
In the following example, the treat actor is getting savvier. If you look closely, observe that the email address has an extra “l” in the domain name. It may be tricky to identify that this is an email scam when reading emails quickly.
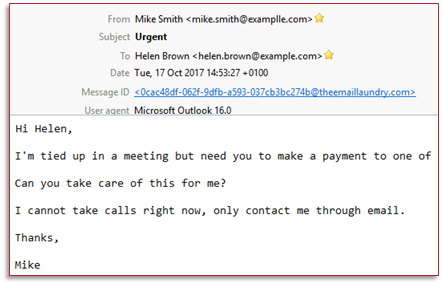
More so, like most of us, I am busy and read many of my emails on my mobile device. I no longer get the visual hint that something is off about this email. Now, the likelihood of action being taken from this email has increased.
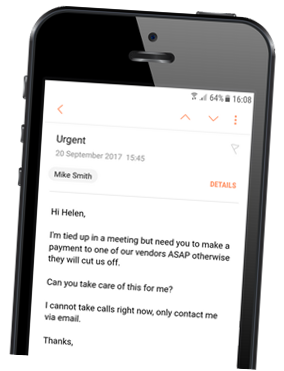
As threat actors continue to manipulate the visual appearance of emails, I no longer feel confident that I can protect myself and my company from email threats. In order for organizations to protect themselves, it is critical to use tools that help identify these threats before they reach employees. To protect against malicious emails organizations, simply route messages to FireEye’s Email Security, which analyzes the emails for spam and known viruses first. It then uses the signatureless detonation chamber, MVX engine, to analyze every attachment and URL for threats and stop advanced attacks in real time. To identify imposters, FireEye’s Email Security also looks for:
- Newly Registered Domains
- Looks-Like & Sounds-Like Domains
- Reply-to-Address & Message Header Analysis
- Friendly Display Name & Username Matching
- CEO Fraud Algorithms
Keeping in mind that email volume is inconsistent, FireEye is able to scale effectively because they have built their product on Oracle Cloud Infrastructure. They can move suspicious emails into separate VMs and can burst up since threat actors are unpredictable.
See our relationship in action by watching the Oracle Cloud Infrastructure and FireEye Webinar or you can experience our joint offering immediately through FireEye’s free Jump Start demo lab environment. In this Jump Start lab, you can follow a step-by-step guide and experience FireEye’s Email Security offering.