Recently, Oracle partnered with a large government customer to set up an Oracle Cloud Infrastructure environment using our latest enterprise landing zone, a Terraform-based template that enables you to quickly configure a cloud architecture that’s aligned with zero-trust principles. This customer then conducted a red team assessment of the environment to see how Oracle security was able to help prevent and monitor attacks. This blog post highlights how you can implement a similar architecture in your Oracle Cloud Infrastructure tenancy by deploying the same practices we used to help prevent professional red teamers who were trying to break through our cybersecurity defenses.
With cyberattacks on the rise, organizations are increasingly using zero-trust principles to improve their security posture, like incorporating stringent controls to help ensure mission-critical solutions are protected from unauthorized access and manipulation. A zero-trust security model implements frequent user authentication and authorization to control access to assets while continuously monitoring the environment for attacks. Because zero trust presumes the environment has been penetrated by a threat agent, security is implemented throughout the environment, instead of simply at the perimeter.
Oracle Cloud is built with a security-first design approach that enables zero-trust architecture. Oracle Cloud security controls are built-in, easy to use, and reduce manual tasks through prescriptive guidance. We offer Oracle Cloud customers features, such as always-on encryption, deny-all network configuration by default, Threat Intelligence Service, and DDoS protection. Oracle Cloud also offers landing zones that use infrastructure-as-code to make security compliance and cloud adoption for mission-critical workloads easier, faster, and more cost-effective.
Enterprise landing zone capabilities
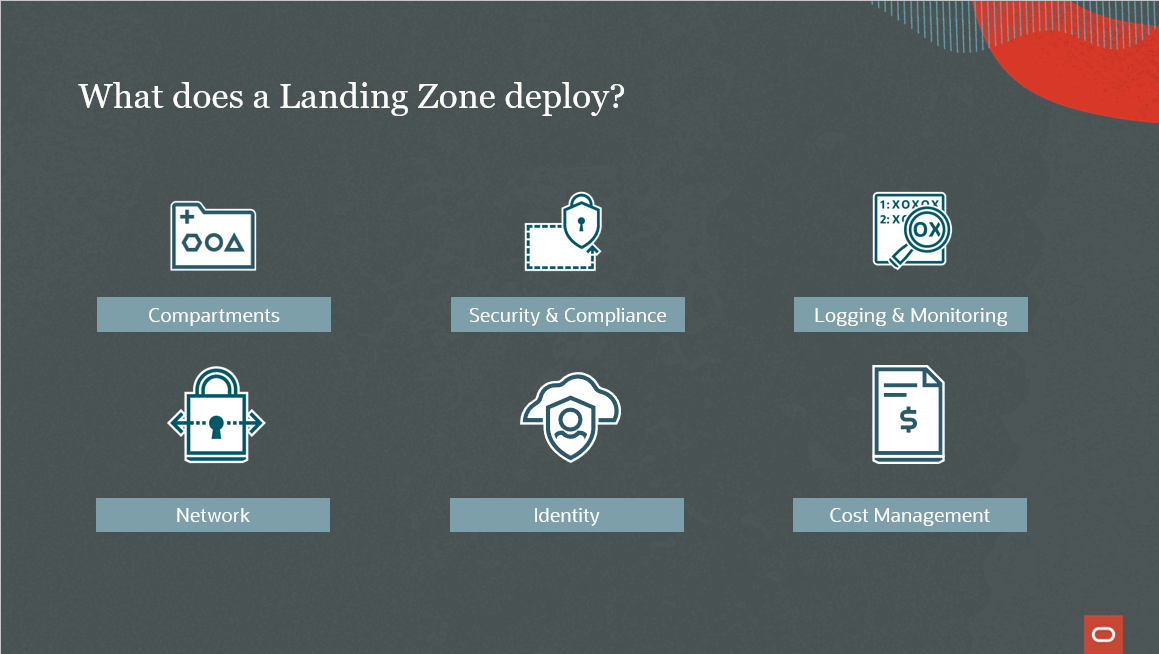
The Oracle Enterprise Landing Zone automates the deployment and configuration of a set of services and components to help you establish a secure foundation for running your workloads. When you deploy a landing zone, it uses automated Terraform scripts to set up your Oracle cloud architecture, starting with the compartment design for the tenancy with groups and policies for segregation of duties.
The enterprise landing zone uses a hub-and-spoke network architecture that provides isolation, scalability, security, governance, and cost optimization. Preconfigured security services are also deployed by the landing zones, including Oracle Cloud Infrastructure Guard, Flow Logs, Service Connector Hub, Virtual Private Vault, Vulnerability Scanning Service, Bastion, and Security Zones. After the landing zone completes its resource deployment, you can add extra protection by setting up notifications that alert your administrators about changes in the deployed resources.
About our sample environment
When our government customer conducted a red team assessment, Oracle deployed an APEX application and a small web-based e-commerce solution into the test tenancy. Oracle’s low-code application platform, APEX comes with a wide variety of built-in security capabilities, so the tenancy required little modification to protect data from inappropriate access. The e-commerce solution included a database system running on a virtual machine (VM), and we also made other VMs available in the environment as attack targets.
We configured Oracle Database Vault in both of our Oracle Autonomous Database instances within the test tenancy. Autonomous Database automates most of the database administration, and Database Vault provides added security to restrict application data from privileged users and reduce the risk from insider and external threats. With machine learning–driven automated tuning, scaling, and patching, the Autonomous Database removes much of the maintenance burden, enabling customers to focus on other security challenges.
Zero trust security that helps protect your sensitive data
We were able to set up a tenancy quickly using the enterprise landing zone and added several other key Oracle Cloud features that help enable a zero-trust architecture. These are the same best practices you can use when you set up your Oracle Cloud Infrastructure tenancy. Oracle deployed a single next-generation network firewall, based on Palo Alto technologies, and structured the tenancy using a virtual cloud network (VCN) to pass all traffic through the network firewall. Oracle used the firewall to manage all traffic into and out of the test tenancy, as well as traffic between test tenancy assets. We were able to monitor traffic and trap and track network events—a critical factor in the success of our test.
Oracle Cloud Guard was a major contributor to the success of the customer test. Cloud Guard automatically detects anomalous behavior to help identify misconfigured cloud resources. Cloud Guard includes standard recipes out-of-the-box that are set to detect common security issues. You can modify and customize recipes, which can also automate responses for immediate action, to meet your specific needs. Cloud Guard even aggregates logs and events and ingests metadata and threat intelligence data so that you have the information you need to take appropriate action.
When our test tenancy was properly set up, we asked our customer’s red team to try to attack the environment. Workloads were exclusively accessed through the Oracle Bastion service. When we established that the red team was unable to attack the site from outside the environment, we provided the red team access through the Bastion service to the internal system. Oracle monitored all the activity that the red team attempted, and we were alerted to all red team activity. Had this been a real event, Oracle’s cybersecurity team would have been engaged to stop the threat.
Integrate your existing technology stack
Oracle understands that customers have tools and services that they trust and want to keep using in their cloud environment. Instead of mandating any particular tool, Oracle provides a robust set of partner solutions that meet your needs and help you achieve a zero-trust security architecture. Oracle Connector Hub helps you manage and move data between Oracle Cloud Infrastructure services and from Oracle Cloud to third-party services. You can direct logs to Object Storage buckets through Connector Hub so that you can analyze them using Log Analytics. You can pull operating system logs from Compute instances using custom logging. You can also send Oracle Cloud Audit and Network Firewall logs to Log Analytics to be reviewed and analyzed.
Oracle supports customers that want to use their own Security Information and Event Management (SIEM) solution, enabling log and event data to exfiltrate into approved third-party tools. You can also deploy many logging and security solutions directly from our partner marketplace, including antivirus solutions and file integrity management services.
Conclusion
Our customer’s red team assessment demonstrated how effective the zero-trust architecture was in defending against malicious attackers. Customers should use patterns that give them the confidence that they can detect and prevent intrusions. Oracle Cloud Infrastructure has the tools that customers can use to help secure their workloads. Enterprise Landing Zone enables customers to quickly set up an architecture to start using security best practices. With the right policies, data encryption, network firewalls, and environment monitoring, you can enable the controls that help protect your assets.
For more information, see the following resources:
