In today’s rapidly evolving threat landscape, organizations face security challenges, such as phishing attacks, unauthorized privileged escalations, stolen credentials, insider threats, and ransomware. A zero-trust security model provides a framework to deploy cloud resources in a secure way. According to the National Institute of Standards and Technology (NIST), zero trust assumes that “there is no implicit trust granted to assets or user accounts based solely on their physical or network location (i.e., local area networks versus the internet) or based on asset ownership (enterprise or personally owned).” The following principles are core to zero trust:
- Verify trust explicitly
- Apply least privileged access
- Always assume breach
These principles are applied across a comprehensive control plane to provide multiple layers of defense.
Adopting a zero-trust model requires significant time and effort. You must commit to making incremental advances over time to establish and maintain secure approaches. It begins with understanding your users, devices, services, and data, assessing their behavior, establishing restriction policies, and removing any inherent trust on the network. Oracle can help with your zero-trust security initiative.
Oracle Cloud Infrastructure (OCI) is designed to provide customers with a built-in security architecture and security services to help quickly and effectively secure your workloads in the cloud. This goal can be a multiteam, multimilestone project, which we break down into actionable steps that you can take to achieve a zero-trust architecture. Learn more about adopting a zero-trust approach on OCI.
Zero trust begins with identity and access management
The first step toward establishing a zero-trust model is to implement identity and access controls. The OCI Identity and Access Management (IAM) service can help start your journey towards implementing a zero-trust model, verifying that only the people, devices, and processes that are authorized to access your resources can access them. OCI IAM serves as the front door into Oracle’s cloud, but it also serves as a standalone identity-as-a-service (IDaaS) platform for both enterprise and consumer audiences. It addresses various identity and access management use cases for applications and services running in OCI, third-party clouds, and on-premises.
Verify explicitly
OCI IAM helps protect users by constantly evaluating their authentication and authorization status as they move from one application to another. Using various signals and policies, it provides a seamless experience allowing single sign-on (SSO) to resources and applications with minimal disruptions. It also helps prevent the use of multiple credentials and weak passwords. If needed, OCI IAM can challenge the user with a wide range of authentication factors, including multifactor authentication (MFA), passwordless authentication, and risk-based authentication.
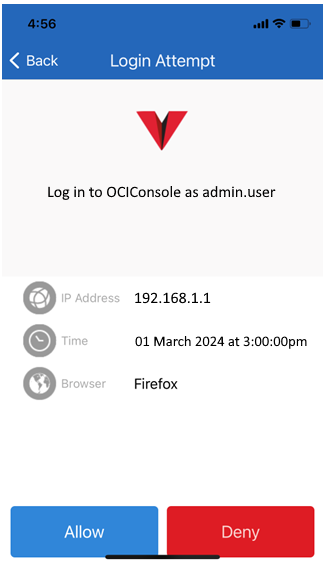
OCI IAM also provides the ability to define course- and fine-grained authorizations for OCI resources through a flexible policy framework.
Apply least privileged access
In OCI, access is denied by default. Administrators can’t access any resources until they’re assigned to at least one group for which a policy has granted privileges. All authorization within OCI is provided through IAM policies, which provide a simple-to-use policy syntax for creating access policies, such as
Allow group DBAdmins to manage database-family in tenancy
Similarly, members of a group have no permissions to access any applications until that group has been mapped to one or more applications or application roles. After a group has been mapped, group members will have the appropriate access.
By having to explicitly grant access where it’s allowed rather than defaulting to “access allowed,” you’re honoring the zero-trust approach.
Always assume breach
OCI IAM evaluates risk at every authentication request. OCI IAM Adaptive Security provides risk-based authentication, enabling the user’s session context to be examined and evaluated against several risk factors, including historical behavior, to determine whether to allow the request, block it, or challenge for an additional authentication factor. This configuration creates an adaptive security model, which is a pivotal feature in implementing zero trust. It also allows you to leverage risk scores from third-party providers, enhancing the accuracy of risk assessments. It enforces strong authentication capabilities for users based on factors such as too many unsuccessful sign-on attempts or impossible travel between locations.
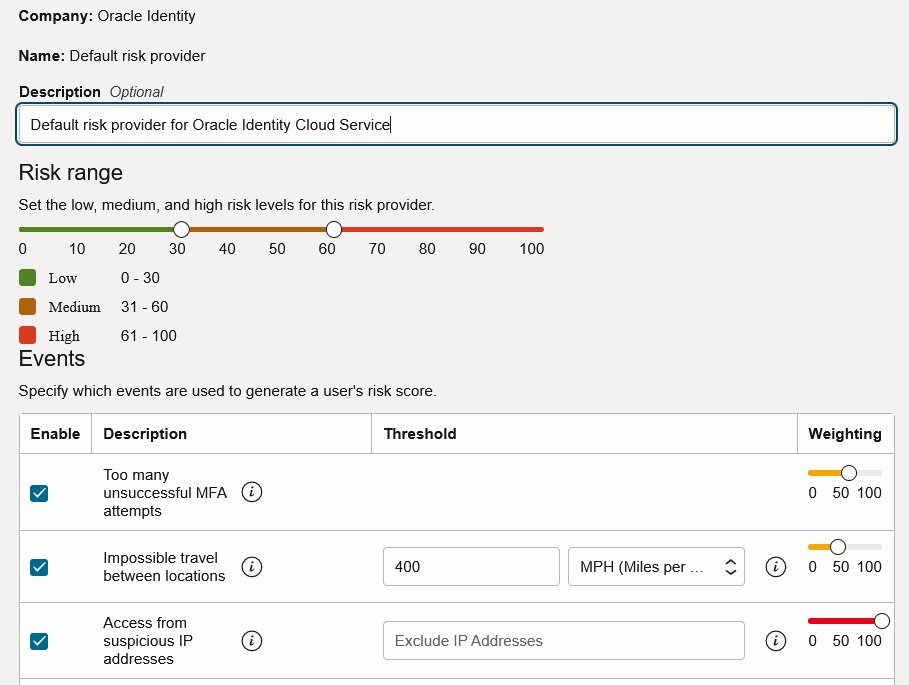
Adaptive Security profiles each user and arrives at its own risk score and an overall consolidated risk level: High, medium, and low. You can use these scores and risk levels with policies to modify sign-on requirements in real time.
Conclusion
Adopting a zero-trust security model provides a strong foundation for addressing risk in cloud platforms. In this post, we focused on implementing strong identity and access controls in support of building a zero-trust approach. OCI IAM enables organizations to enhance their security posture and protect against a diverse range of cyber threats by constantly evaluating authentication and authorization policies, risk scoring, flagging users, and enforcing remediation policies to reduce identity-based attacks like phishing, privilege escalations, stolen credentials, or insider threats.
For more information about the approaches discussed in this post, review the following documentation:
To learn more about Oracle Cloud Infrastructure, start with an Oracle Cloud Free Trial or contact the Oracle sales team today for a demo.
