How secure is your data uploaded into Oracle Cloud Infrastructure (OCI) Object Storage? Very secure! But let’s cover some basics first.
In the OCI Object Storage service, a bucket is a container for storing objects in a compartment within an Object Storage namespace. A bucket is associated with a single compartment. OCI always puts security first and ensures that customer data is always stored and accessed securely.
Encryption is automatically enabled for all data with no action required of customers using Oracle-managed keys. Regulated clients such as banks want to be able to use their own keys for encrypting their objects and entire buckets. This extra level of security meets regulatory compliance requirements. This necessity gave rise to bucket encryption added to Object Storage.
With the bucket encryption capability, you can use server-side encryption with customer-provided keys (SSE-C) or a custom master encryption key from KMS or OCI Vault. Bring Your Own Key (BYOK) allows you to use your own keys as master encryption keys stored in the vault for encrypting objects in a bucket.
OCI uses the 256-bit Advanced Encryption Standard (AES-256) to encrypt all data and encryption keys by default. AES-256 is considered one of the strongest encryption algorithms that exist. Object data and user-defined metadata are encrypted.
You can also create security zones that have recipes to ensure that no public buckets are created, buckets have a customer-supplied vault key for encryption, and so on to enforce your enterprise security policies.
Can I control how my data is encrypted?
Yes, you can! Object Storage supports server-side encryption. All data in Object Storage is encrypted at rest by using AES-256. Encryption is on by default and can’t be turned off. Each object is encrypted with its own encryption key, and the object encryption keys are encrypted with a master encryption key (MEK). The encryption keys are rotated frequently based on a rigorous internal policy.
A vault is a logical entity that you can use to store the encryption keys you use to protect your data. Depending on the protection mode, keys are either stored on the server or on highly available and durable hardware security modules (HSMs). Our HSMs meet Federal Information Processing Standards (FIPS) 140-2 Security Level 3 security certification. For more information, see Managing Vaults and Managing Keys.
Although default encryption keys can be generated automatically when you create certain OCI resources, I recommend creating and managing your own custom encryption keys in the Vault service. Each master encryption key (MEK) is automatically assigned a key version. When you rotate a key, the Vault service generates a new key version. Periodically rotating keys limits the amount of data encrypted or signed by one key version. If a key is ever compromised, key rotation reduces the risk to your data, reducing the impact radius. You can also encrypt data using the following methods:
-
Client-side encryption: Customers can encrypt the data before sending it to Oracle Object Storage. Sending encrypted data gives customers complete control over their encryption keys and provides a second line of defense against unintended and unauthorized data access. To help in this area, Oracle has released SDK enhancements for client-side encryption.
-
Customer-provided keys: Base64-encoded 256-bit AES encryption key sent with the request in optional API headers to encrypt or decrypt the data. These keys aren’t stored by OCI. The keys are provided by the customer with each request.
-
Customer keys stored in the Vault: The KeyId of a key stored in OCI Vault is used for encryption to allow customers to bring their own or create keys using software or HSM and store the keys in OCI Vault. When an OCI service like Object Storage is granted the privilege to use the customer keys for encryption, the service can automatically encrypt objects stored in the bucket, using the corresponding customer key stored in the Vault.

For details on encrypting object data, see Encrypting Data.
OCI encrypts all objects by default with Oracle-managed keys, which are periodically rotated. We now provide options to customers to use their own keys for more security.
Recommended best practices
While using IAM policies that authenticate the users performing the task, a best practice is creating and periodically rotating encryption keys in the Vault service to protect your resources in Object Storage. If you import your keys (BYOK) or create a key using HSM, store it in a vault and use it for bucket encryption as a MEK, which encrypts the object keys for an added level of protection.
How to use bucket encryption
OCI Object Storage provides the flexibility to enable bucket encryption at the time of creation or on existing buckets by assigning a vault encryption key to an existing bucket. You can also reencrypt a bucket and remove vault encryption keys assigned.
OCI Object Storage encrypts your data and user metadata (customer-provided key value pairs) using randomly generated data encryption keys (DEKs). Object Storage allows you to specify your own MEK managed by the Vault service for buckets and individual objects. You can specify the MEK for a given object without having to maintain and manage your own keys. For more details, see To assign a Vault key to a bucket.
You need the required permissions in the Identity and Access Management (IAM) policies to specify your own MEK. Use the following steps to create a bucket with encryption using a customer-provided key stored in Vault:
-
Create the Vault to store your keys. In the menu under Identity & Security, select Vault and click Create Vault.
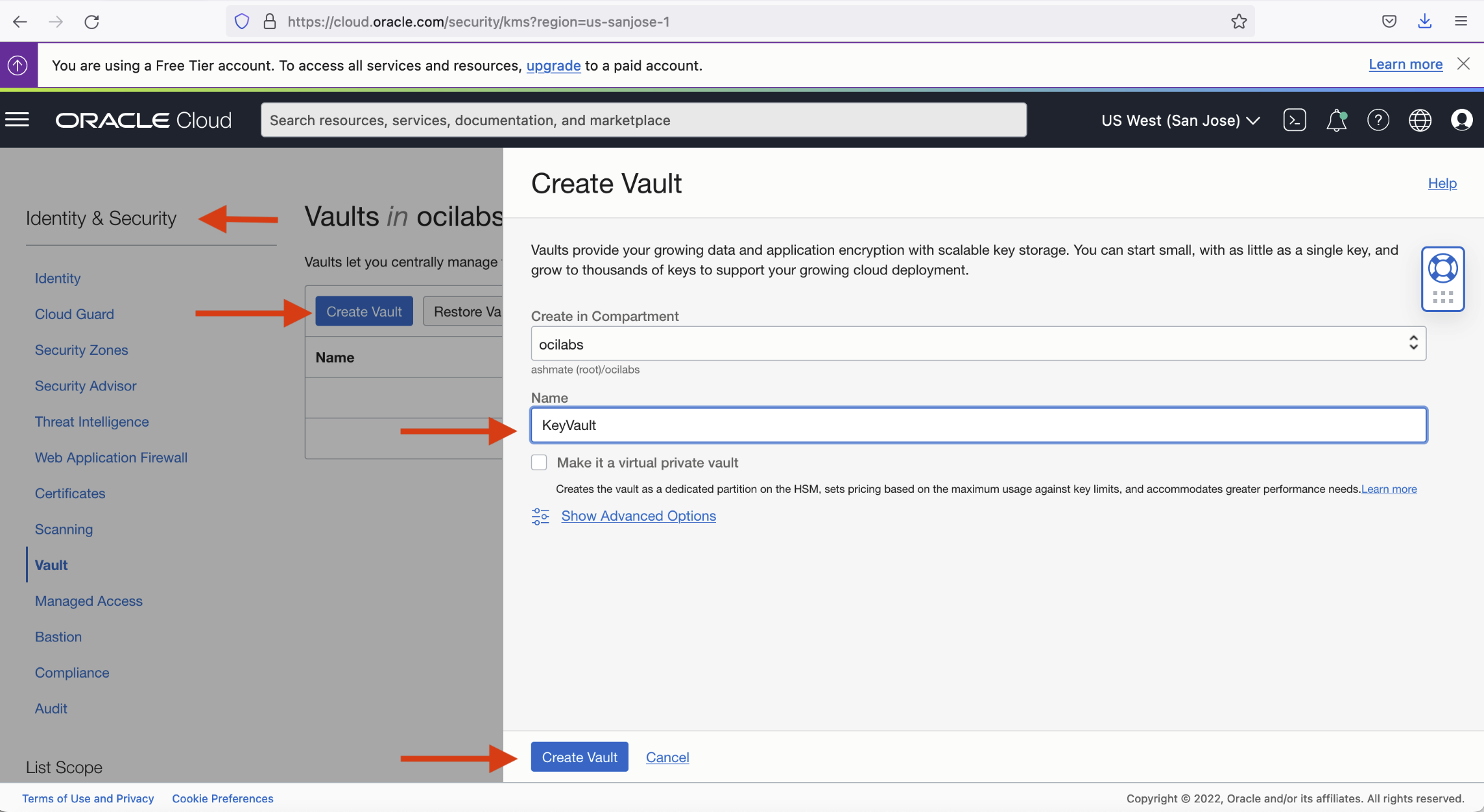
-
Create or import your key into the vault created. In the same menu as the previous step, click Create Key.
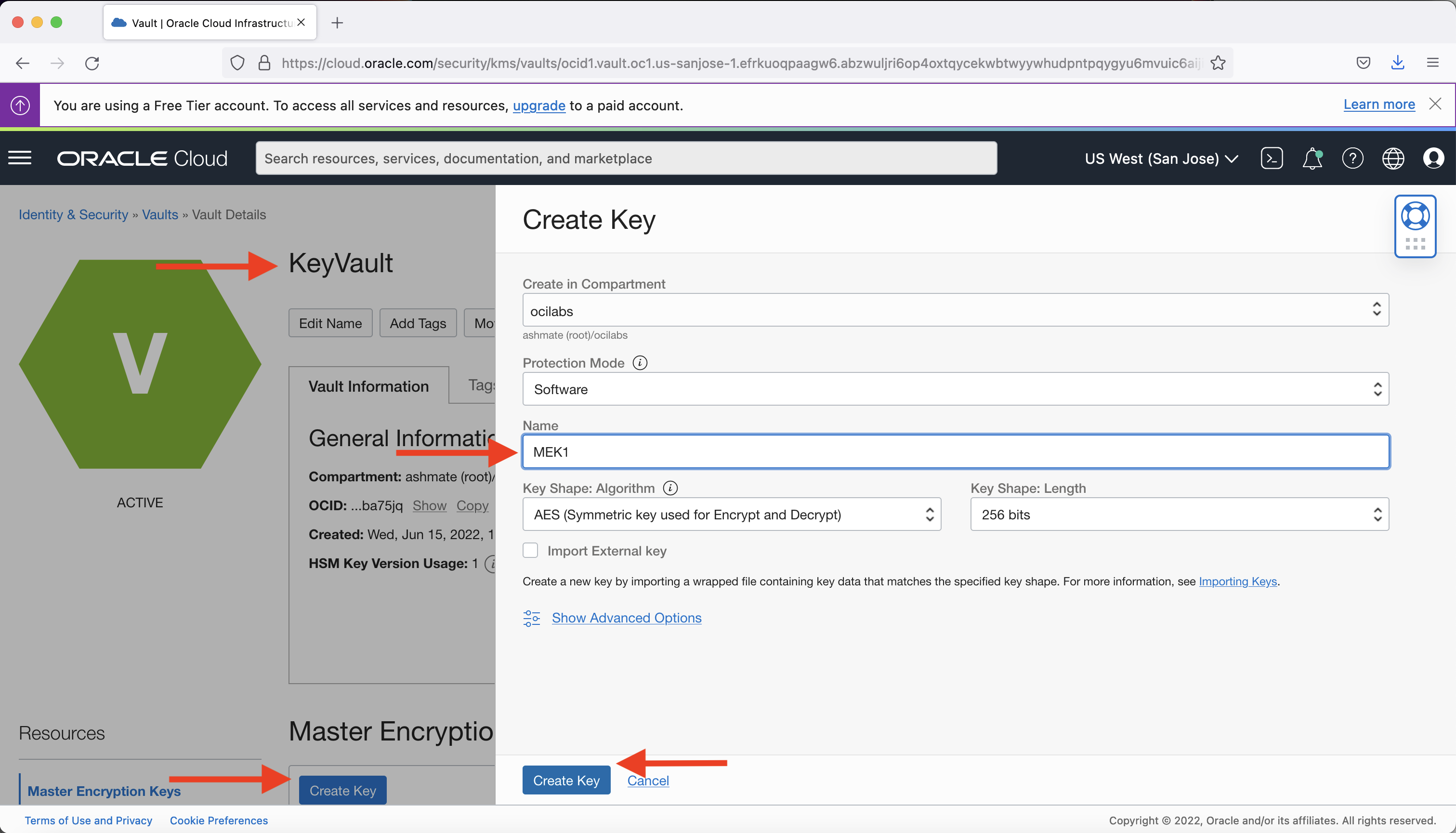
Choose Software or HSM Protection Mode, provide a name to your key, and click Create Key. To BYOK, select Import External Key instead.
-
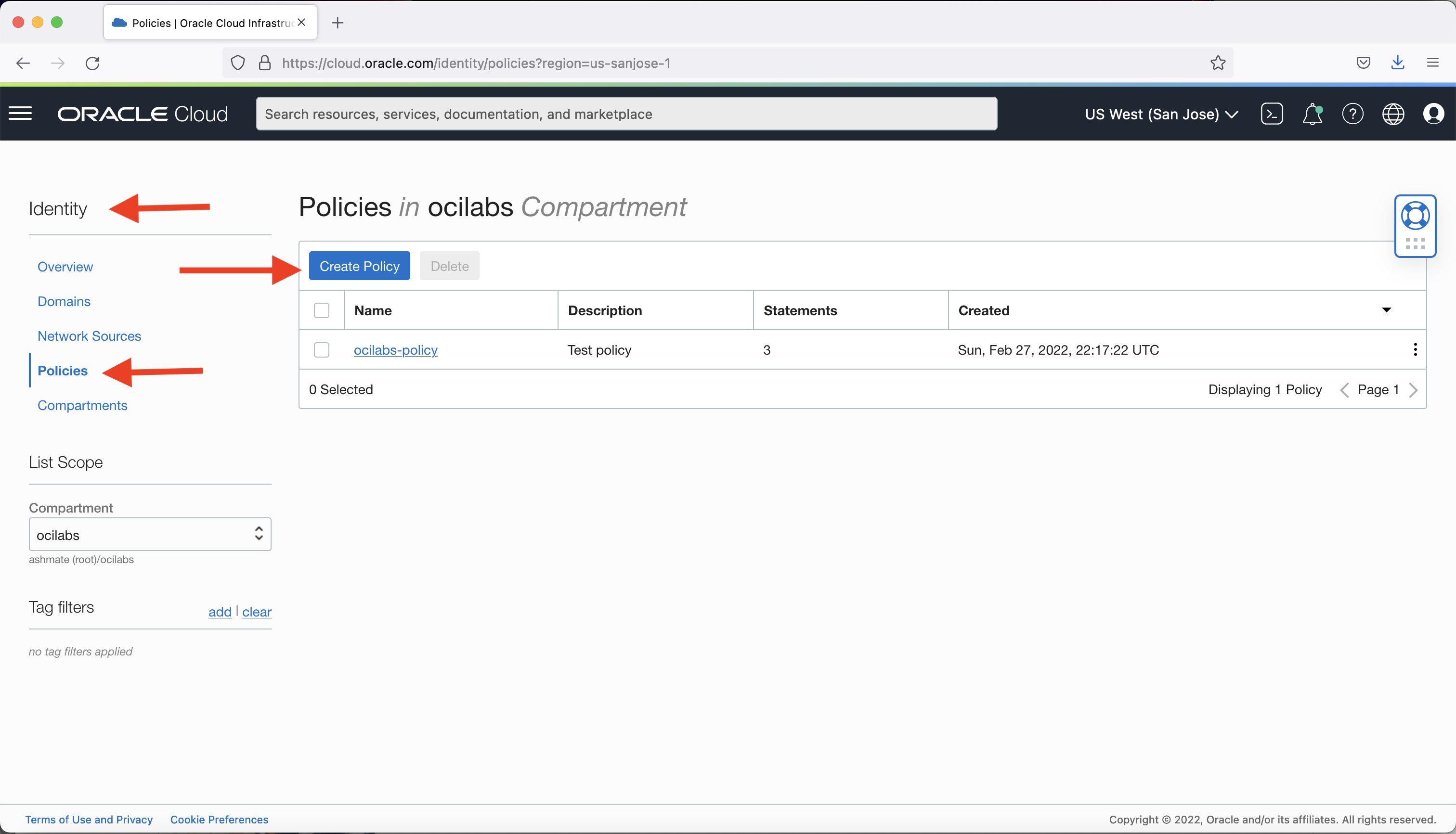
Create or add tenant policies to allow Object Storage to use the key for encryption. Under Identity & Security, select Policies and click Create Policy.
Edit the policy statements to add policies to permit various OCI services to use the key from the vault for encryption in your compartment. This example uses ocilabs.
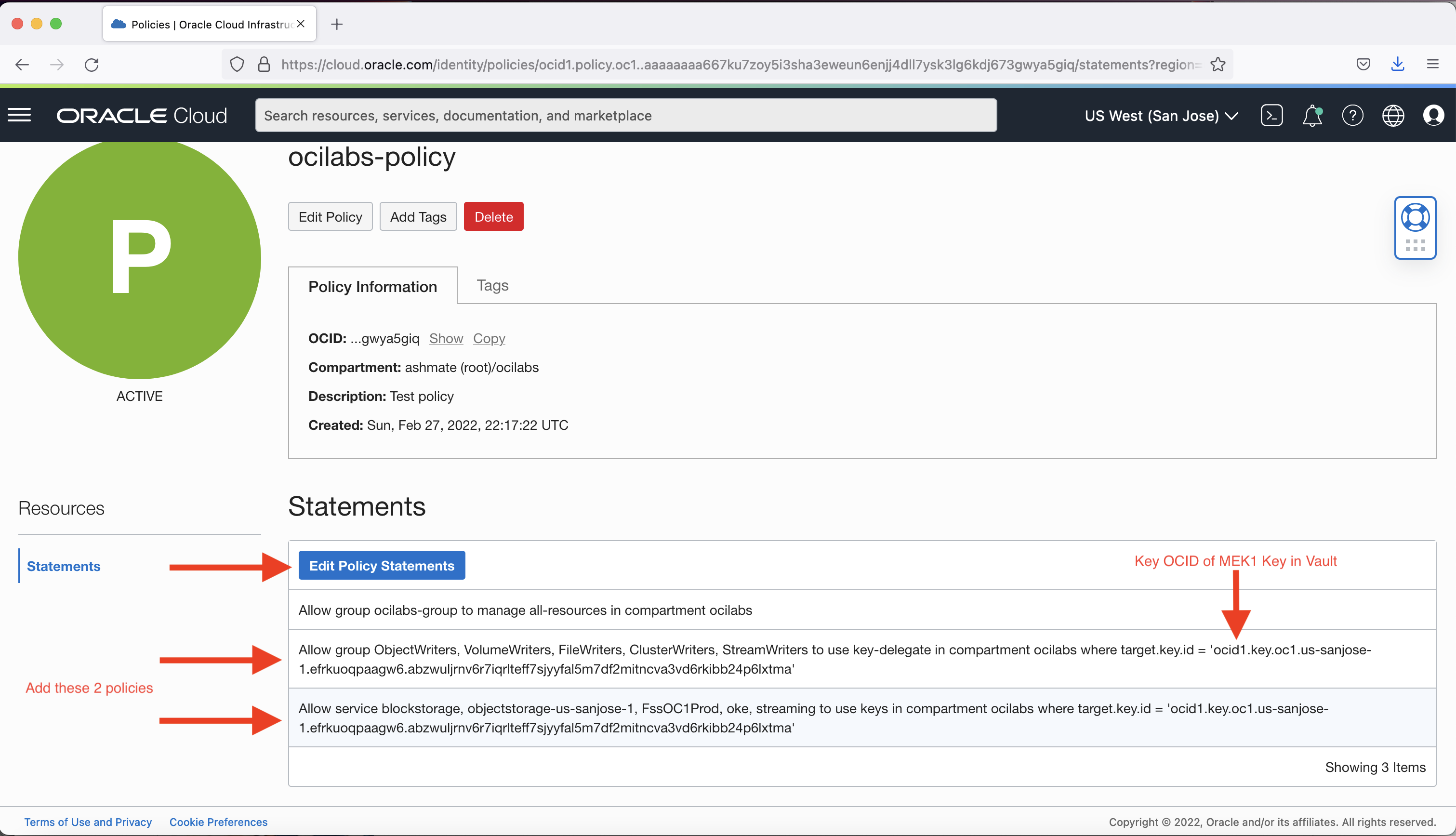
Use the compartment and key OCID for the encryption key created and stored in the vault in the previous step.
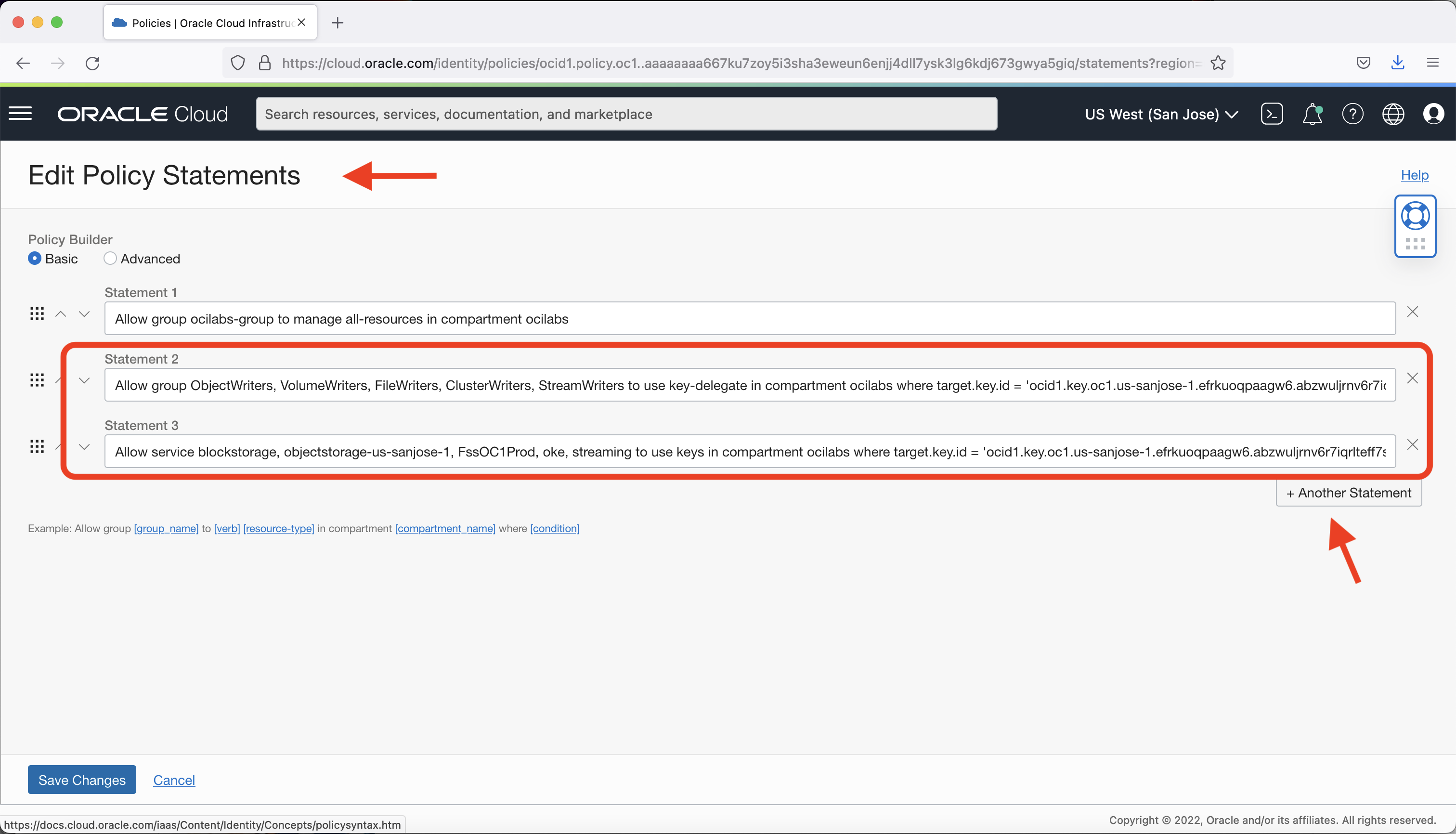
Because Object Storage is a regional service, use the region name of your compartment and bucket to qualify, such as objectstorage-us-sanjose-1 in this example.
-
Create a bucket and enable encryption on it using the customer-managed key created.
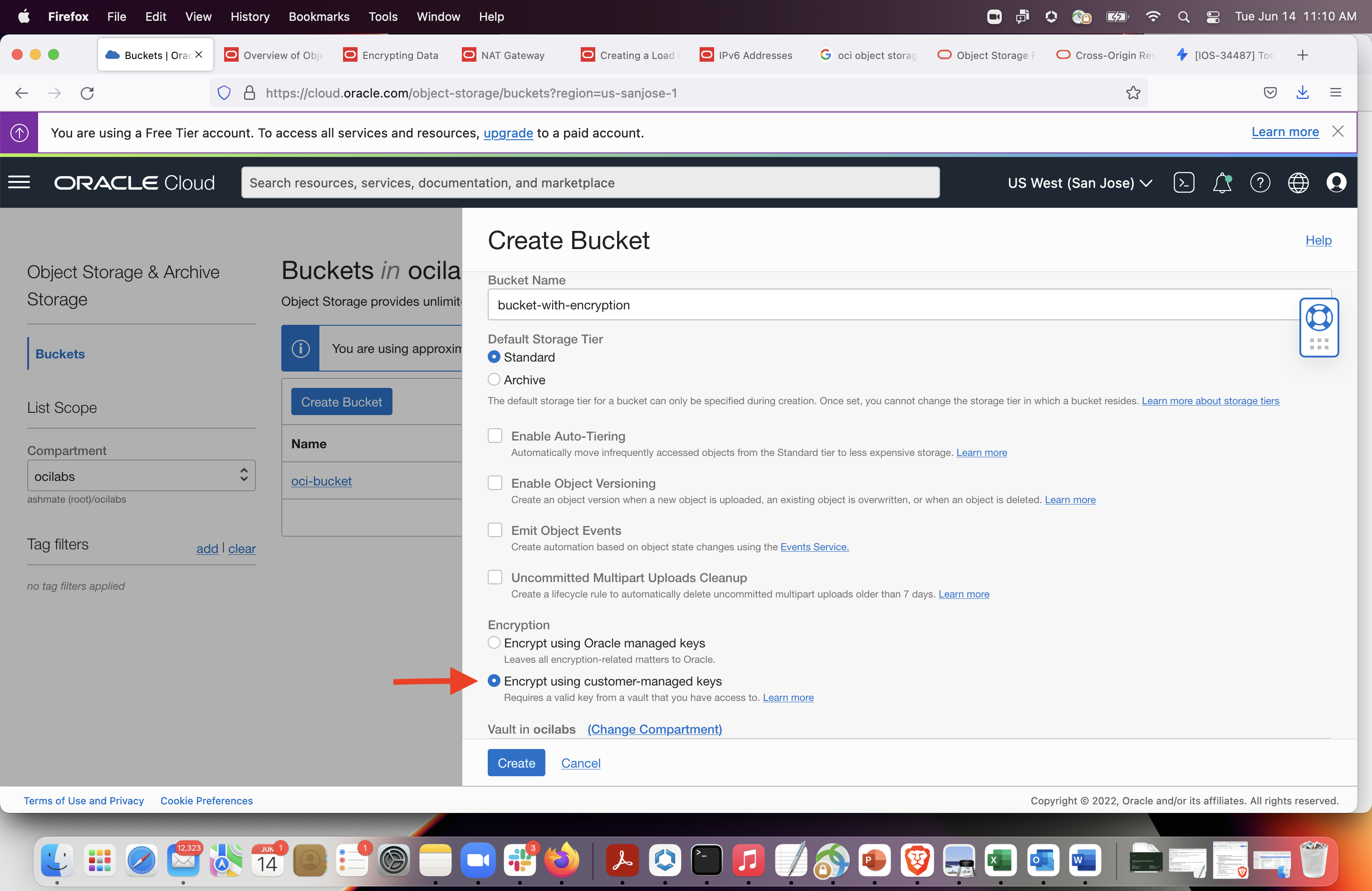
Select Encrypt Using Customer-Managed Keys. Then, select the vault compartment and vault that contain the master encryption key you want to use. Also select the MEK and its compartment and click Create.
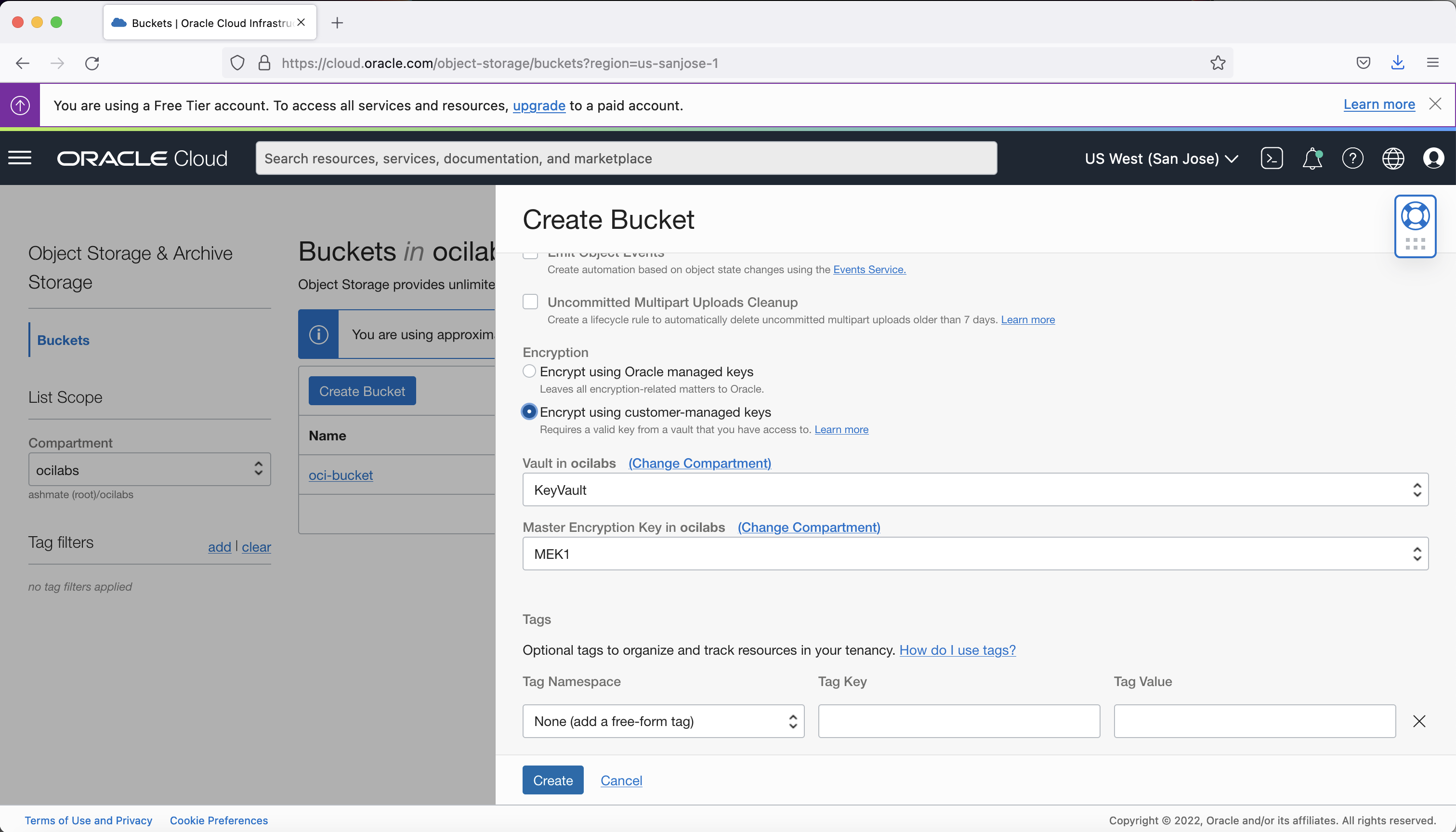
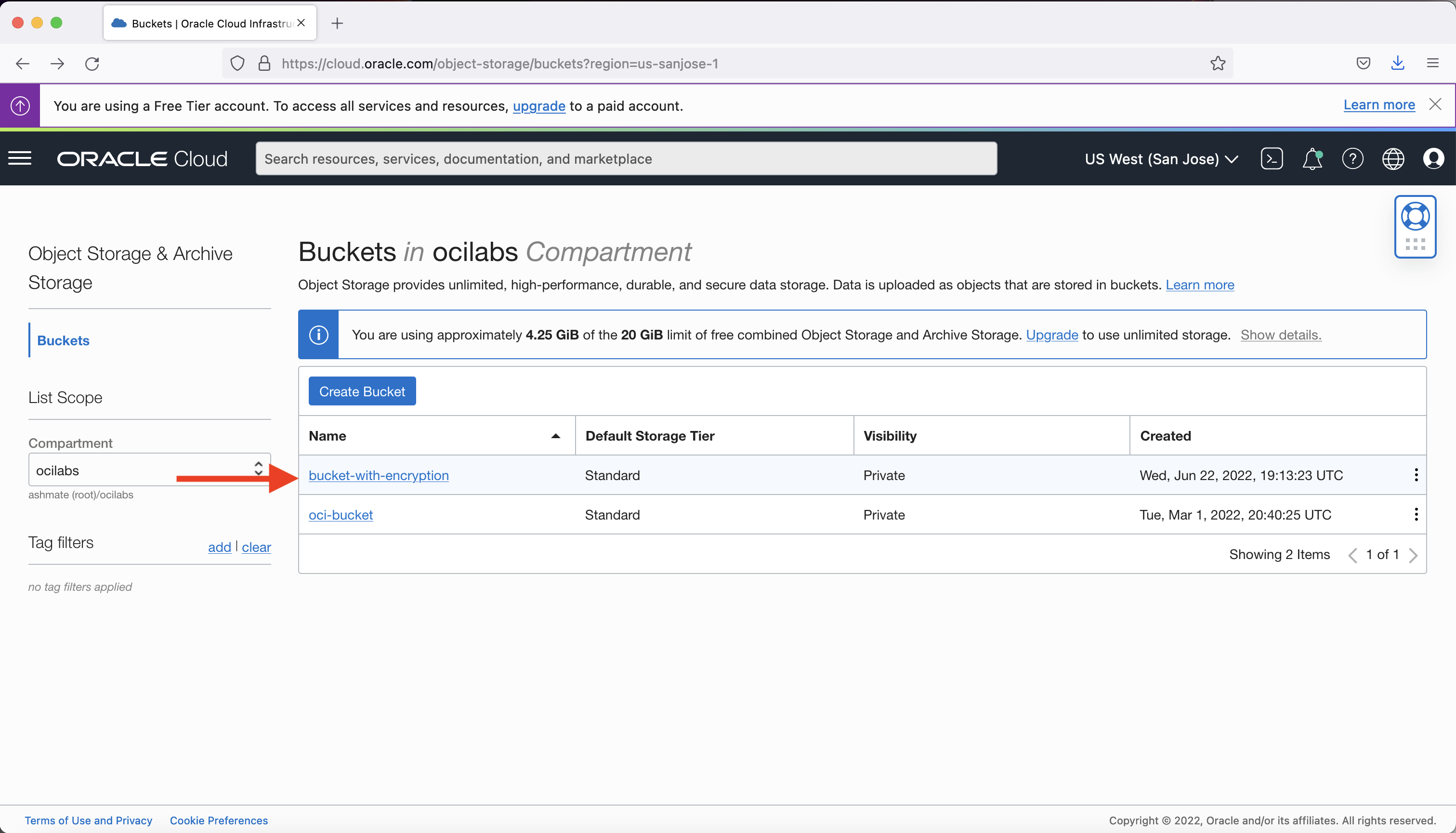
The bucket with encryption created in the example shows the encryption key used (MEK1 in this example) and its OCID.
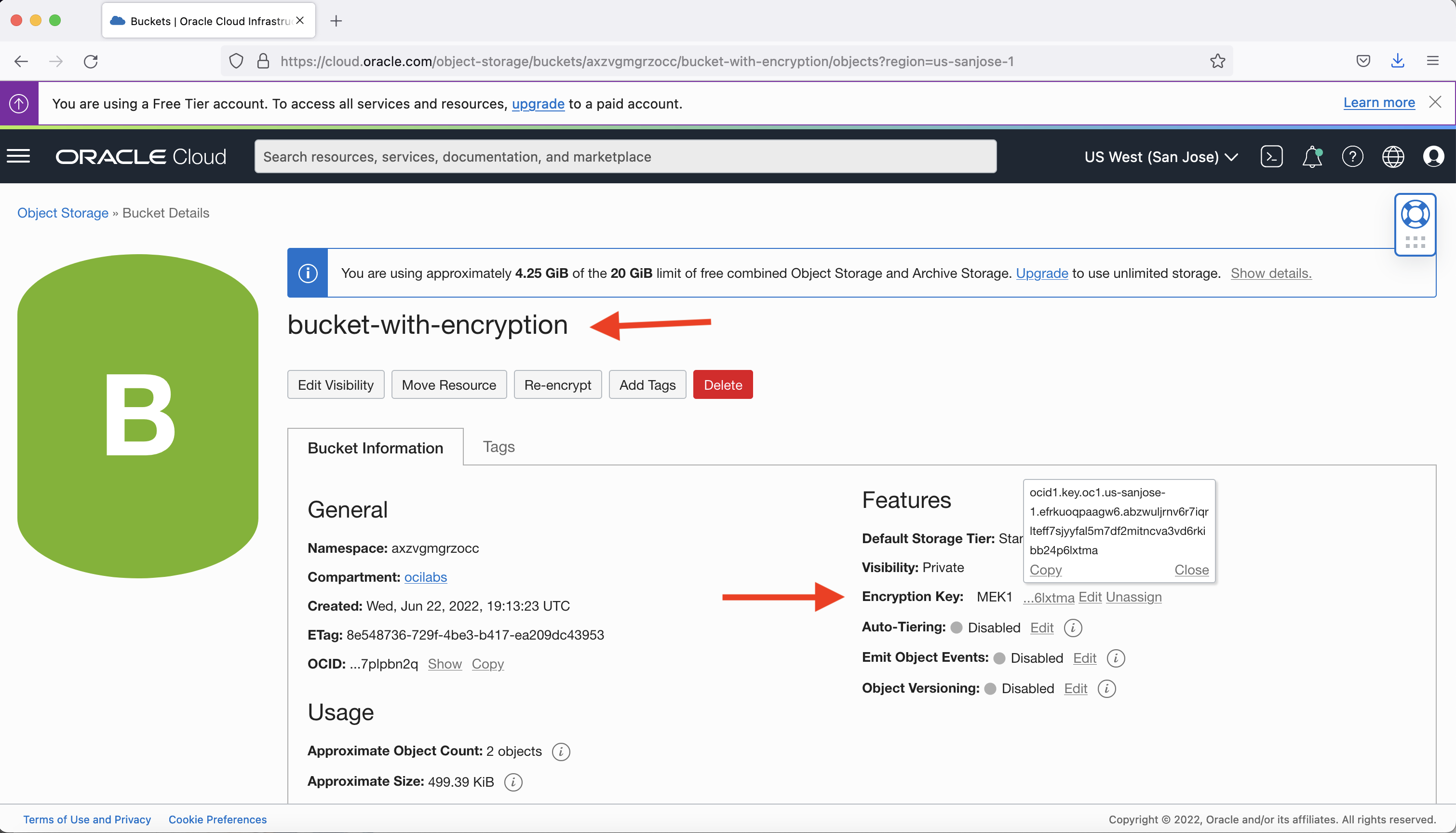
-
For existing buckets, you can assign an encryption key stored in vault: In the menu under Object Storage, select the existing bucket (oci-bucket, for our example),
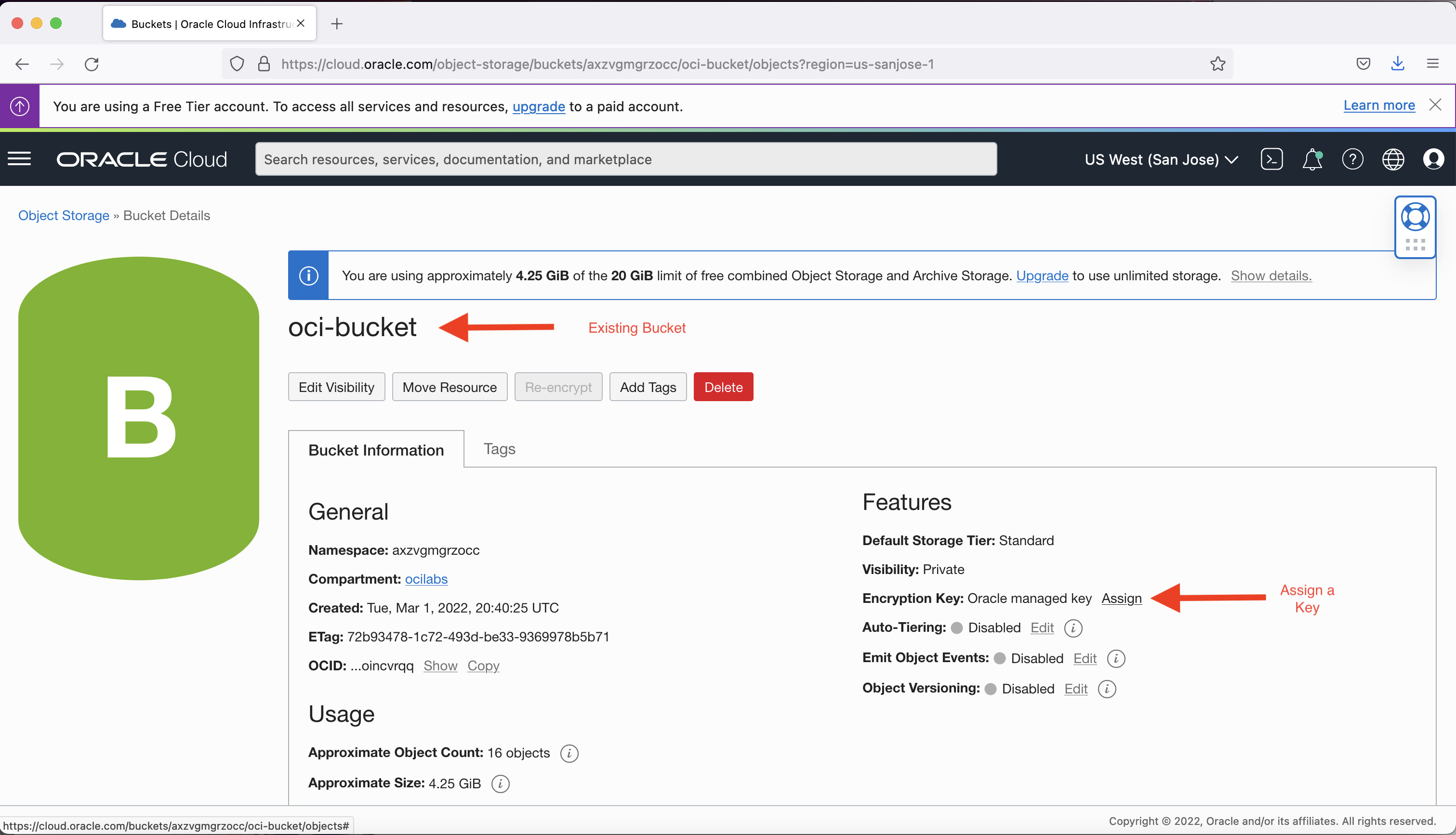
Click Assign to assign a customer-managed key from Vault instead of the default Oracle-managed key.
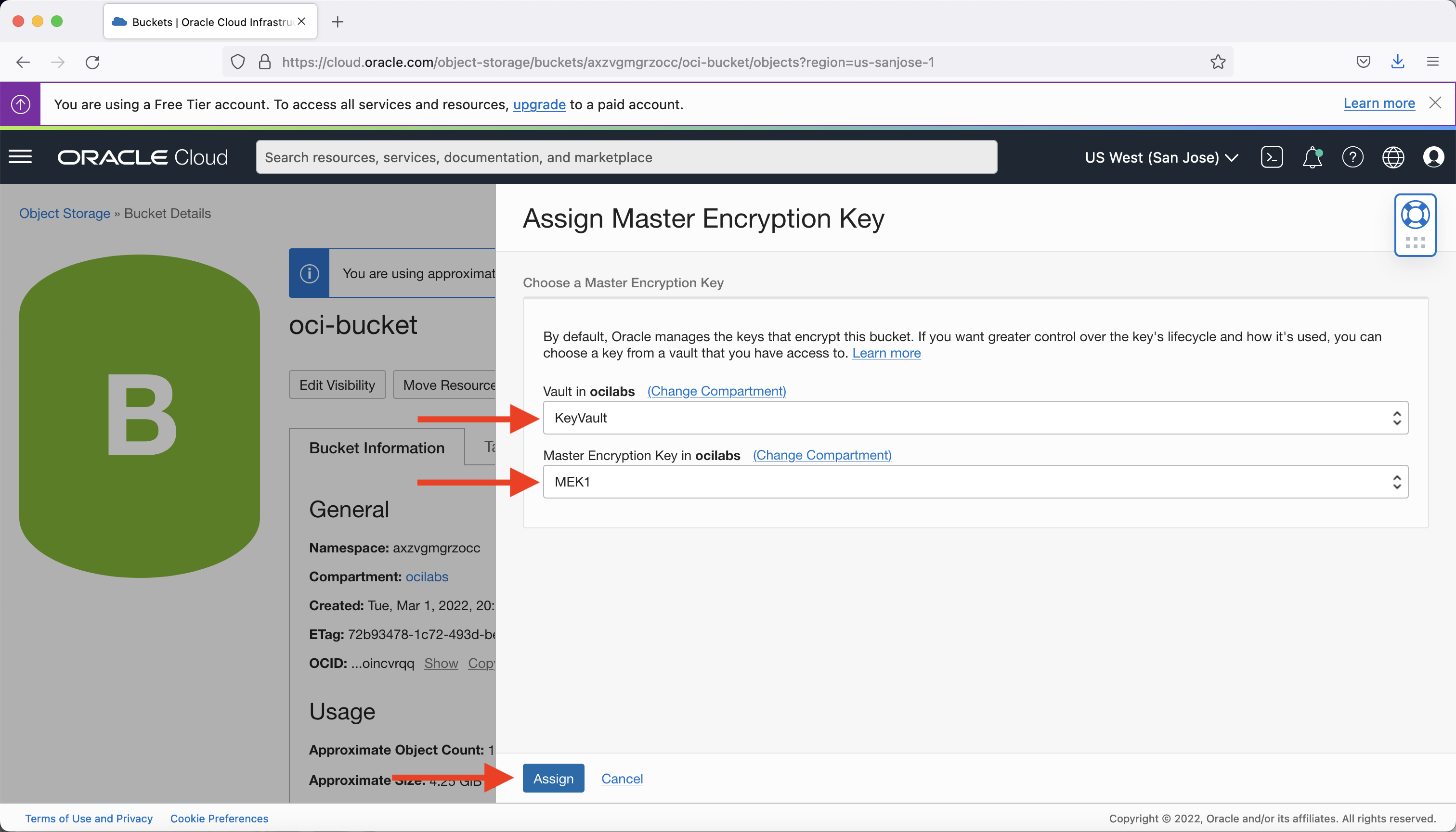
Select the vault and the MEK from the vault to assign and click Assign.
Conclusion
That’s all the steps for using customer-provided keys in vault for bucket encryption in OCI Object Storage. I hope that this blog helps customers and users looking to import their own keys to use for added security with the bucket encryption capability of Oracle Cloud Infrastructure Object Storage.
