In early 2021, Oracle Cloud Infrastructure (OCI) released our next generation site-to-site IPsec VPN service. This service added several enhancements over the original version of the OCI VPN service by adding support for policy-based VPNs, more visibility with logging, greater tunnel availability and resiliency, and improved interoperability with other IPsec VPN solutions. You can read more about this service in the previous announcement blog.
Since then, we’ve continued improving our next generation VPN service with more enhancements, such as greater routing visibility, and the ability to customize IPsec-related features such as dead peer detection (DPD), IKE initiation, and Phase 1 & Phase 2 parameters. You can read more about these specific enhancements in the announcement blog for these features.
This blog details the recommended best practice approach for a self-migration. If you’re an OCI Site-to-Site VPN customer who wants to take advantage of the added benefits or have been notified about a migration of your tunnels and want to proactively upgrade, this blog is for you.
Getting started
This process involves creating a new IPsec connection, configuring your CPE to establish IPsec tunnels with the new VPN endpoints and routing your traffic to use the new tunnels. After traffic is routed over the new tunnels, you can delete the previous v1 IPsec connection.

Before starting, verify that the IPsec connections you’re migrating terminate on the VPN v1 service. You can verify by browsing to your existing IPSec connection and checking the version under the “IPsec Connection Information” tab.
After identifying which IPsec connection you’re migrating, note any that which you want to replicate for your new IPsec connection. Also identify the CPE object and DRG that your IPsec connection uses so you can reuse them.
You can reuse certain settings related to your current IPSec Connection in the new one, minimizing how much you need to configure during this process. You can reuse the following OCI components:
-
CPE object
-
DRG
You can reuse the following tunnel settings:
-
Shared secret
-
Phase 1 and Phase 2 parameters
-
IKE version
-
Routing type, such as border gateway protocol (BGP) and static
The following tunnel attributes must be different:
-
The Oracle VPN public IP address
-
Inside tunnel interface IPs cannot overlap with any existing tunnels. If you want to reuse the IPs on your v1 IPsec Connection, you must delete it first, which we don’t recommend.
Configuration
Create an IPsec connection
Now we can provision an IPsec connection. Any new IPSec connection created automatically uses the next generation site-to-site VPN service and provides you access to all the available enhancements.
Don’t delete your existing v1 IPsec connection until the end. When deleted, you can’t create a new IPsec connection using the v1 Site-to-Site VPN service.

To simplify configuration when creating your new IPsec connection, select the same CPE and DRG used previously.
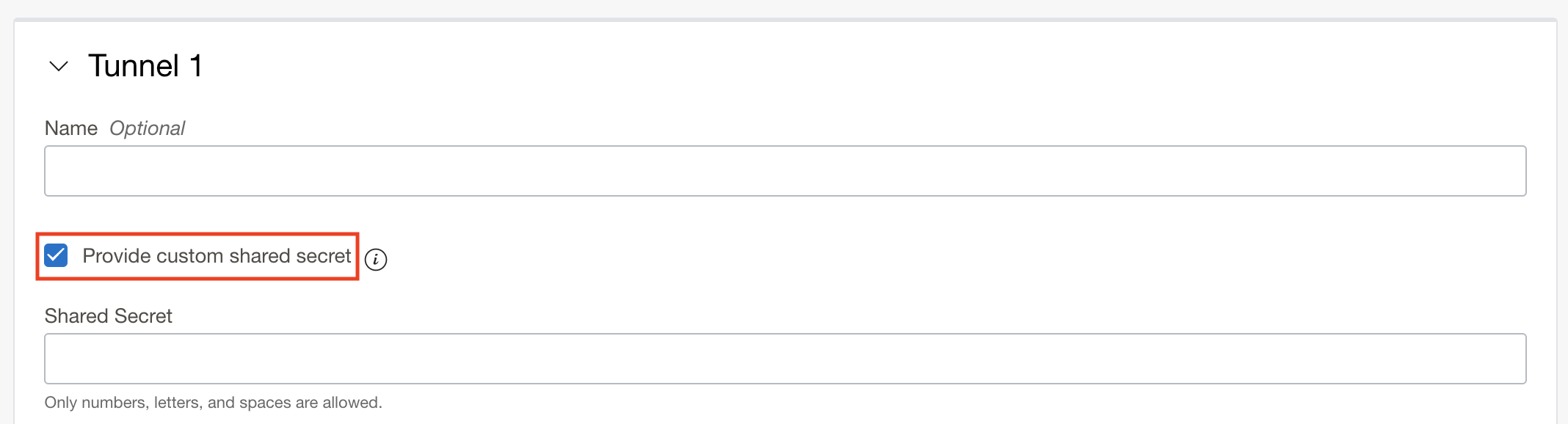
If you want to use the same shared secret, select Provide custom shared secret and input the key used by your existing tunnels. If you don’t select this option, each tunnel uses an automatically generated key.
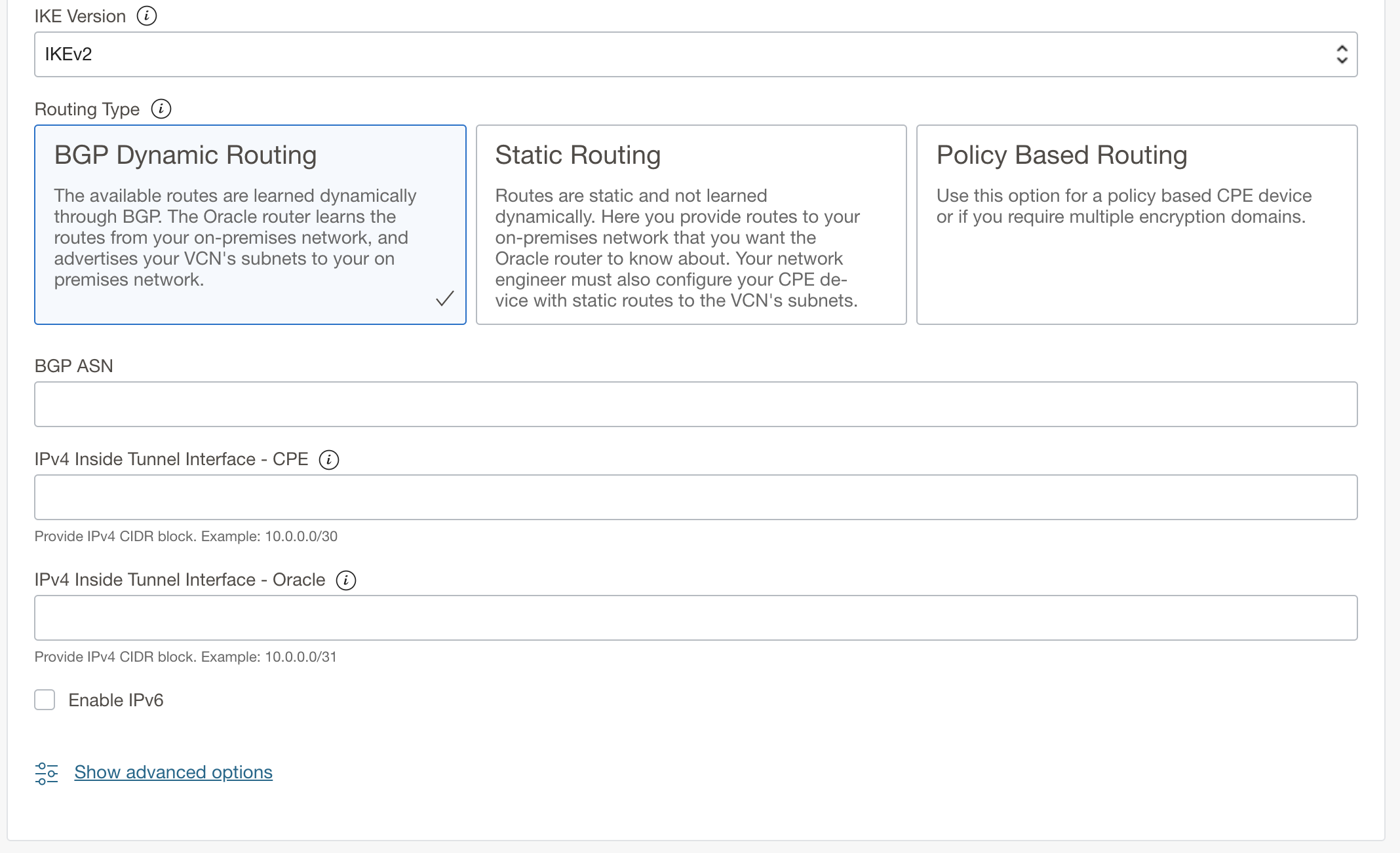
Next, configure all your tunnel settings, including the IKE version and routing configuration. A new option for policy-based routing appears. To learn more about the different IPsec tunnel types supported, see Supported Encryption Domain or Proxy ID.
If you’re using BGP as your routing type (which we recommend), choose a new /30 for your inside tunnel IPs. These settings can’t overlap with your existing tunnels. You can also change them later to match the /30 used by your current tunnels.

Under advanced options, you have some more new options. You can now customize settings related to IKE initiation, NAT traversal, Phase 1 and Phase 2 parameters, and DPD.
After you’ve completed configured all the required IPsec connection settings, click the Create IPSec Connection button so start provisioning the new resource. For more details related to the configuration, see Setting Up Site-to-Site VPN.
OCI verification

Browse to your new IPsec Connection in the Oracle Cloud Console. The version is listed as v2, which confirms that you’re using the next generation VPN service. When you’ve validated that your new IPsec Connection is using the next generation VPN service, you can bring up the new tunnels and configure your routing.
Configure CPE: IPsec VPN
Configure your CPE to bring up the new tunnels. The Oracle VPN IP address column lists the public IP to use for each tunnel. These IPs are different from your previous IPsec connection. For assistance on how to configure your device, refer to the OCI CPE documentation or your CPE vendor’s documentation.
Configure CPE: Routing
When your tunnels are configured, you can verify the state of each tunnel under the IPsec connection in the Console. If you’re using BGP as the routing type, the IPsec Status and BGP Status displays “up.”
After the new tunnels have been configured and you’ve verified the state of each tunnel, you can reroute some traffic to traverse them. You can choose to route all traffic between your on-premises and OCI over the new tunnels or a subset like a single host or a single subnet as a test before making the change for all traffic.
Static routing

If you’re using static routing for your tunnels, use the longest prefix match so the system prefers the new tunnels. Configure the static routes for each IPsec connection so that OCI prefers to send traffic back on the new tunnels. The previous diagram shows an example using static routing to ensure symmetrical routing across tunnels in different IPsec connections.
BGP
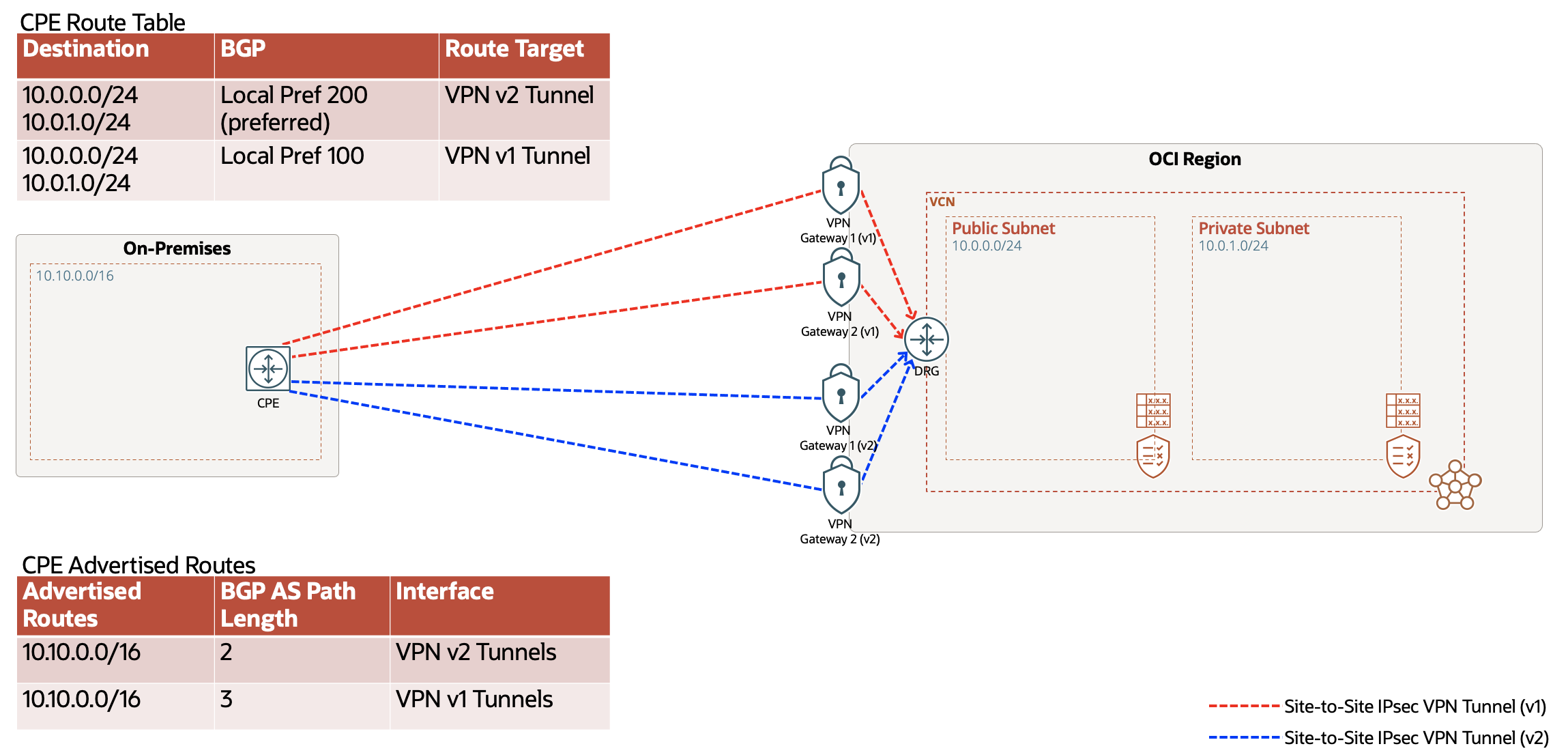
If you’re using BGP, use BGP attributes like local preference to influence which tunnel you use to send traffic to OCI and AS path length to influence how OCI sends the traffic to your on-premises endpoints. Configure routing so that the traffic flowing over the new tunnel is symmetrical. The previous diagram details how to use BGP local preference and AS path prepending to influence traffic in both directions for all subnets. For more information on how to design your routing, see Routing Details for Connections to Your On-Premises Network.
Test connectivity
Use utilities like ping to confirm end-to-end connectivity over the new tunnels. You can also verify that traffic is flowing over the new tunnels by looking at tunnel traffic statistics using the Site-to-Site VPN Metrics.
Delete your IPsec connection
When you’re satisfied that the new tunnels are working, configure your routing so all traffic uses the new tunnels instead of the tunnels in your previous v1 IPsec connection.
Only when all traffic is routed over the new tunnels and reachability has been verified is it safe to delete the previous v1 IPsec connection. Browse to your old IPsec connection and click the red Terminate button to delete it. We recommend deleting any old v1 IPsec connections no longer in use only after all traffic has been migrated to your new VPN tunnels.
You can repeat this process for any existing v1 IPsec connections you have in your tenancy. If you run into any configuration issues during this setup process, open a service request for assistance. For customers impacted by the migration, details on the maintenance, timelines, and more will be sent to you.
