Today, Oracle Cloud Infrastructure (OCI) is making it easier for you to drive informed security decisions with the launch of Oracle Threat Intelligence Service. Oracle Threat Intelligence Service is a new service that provides integrated, actionable threat intelligence to Oracle Cloud Guard and the newly-launched Oracle Cloud Guard Threat Detector to help protect resources in your OCI tenancy.
What is Oracle Threat Intelligence Service?
OCI Threat Intelligence aggregates threat intelligence data across many different sources and manages this data to provide actionable guidance for threat detection and prevention in Oracle Cloud Guard and other Oracle Cloud Infrastructure services. This service provides insights from Oracle security researchers, our own unique telemetry, open source feeds such as abuse.ch and Tor exit relays, and third-party partners such as CrowdStrike, a cybersecurity company that correlates trillions of security events per day to deliver actionable insights to secure endpoints, workloads, identities, and data.
Why do I need threat intelligence data?
According to the National Institute of Standards and Technology (NIST), threat intelligence is threat information that has been aggregated, transformed, analyzed, interpreted, or enriched to provide the necessary context for decision-making processes. Tactical threat intelligence data commonly refers to forensic evidence that can be found in system and network logs such as domains, URLs, IP addresses, and file hashes. Threat intelligence data not only reduces mean time to detect (MTTD), but it also helps reduce mean time to remediate (MTTR) by giving responders contextual awareness about potential threats that enables them to make smarter and faster decisions.
Detecting outbound web traffic to a command and control node might indicate a breach, as could alerting on a user log-in from an IP address that has a historical record of association with malicious behaviors. Intelligence such as the IP address affiliated with these attacks informs incident response teams, who can then use that information to target the scope of their investigation.
An integrated, managed approach to threat intelligence
Using threat intelligence data purposefully and reliably can be a burden on already overworked security operations teams. It requires sourcing, validation, management, storage, and manual integration – which can be money- and time-intensive. Oracle Threat Intelligence Service is a fully integrated approach to gaining threat intelligence, at no additional cost.
Threat Intelligence Service currently integrates with Cloud Guard and Threat Detector.
When you enable Cloud Guard in your tenancy, Threat Intelligence Service will begin correlating your logs against known malicious IPs and support detection such as suspicious IP activity by default.
Adversaries are continuously evolving and adapting. Using threat intelligence data alone is not sufficient to detect threats. Cloud Guard Threat Detector expands the existing threat detection capabilities of Cloud Guard with a MITRE ATT@CK-aligned machine learning platform. It analyzes real-time and historical events together with data from Threat Intelligence Service to produce correlated security alerts called sightings. Read more about Threat Detector here. (see Fig 1).
Threat Intelligence Service is a key component that supports Oracle’s approach to security by enabling simple, prescriptive, and integrated security for customers, and strengthening defense-in-depth. The integrations with Cloud Guard and Threat Detector are only the beginning; we’ll continue to expand defensive threat intelligence-enabled features from the network edge to the identity layer.
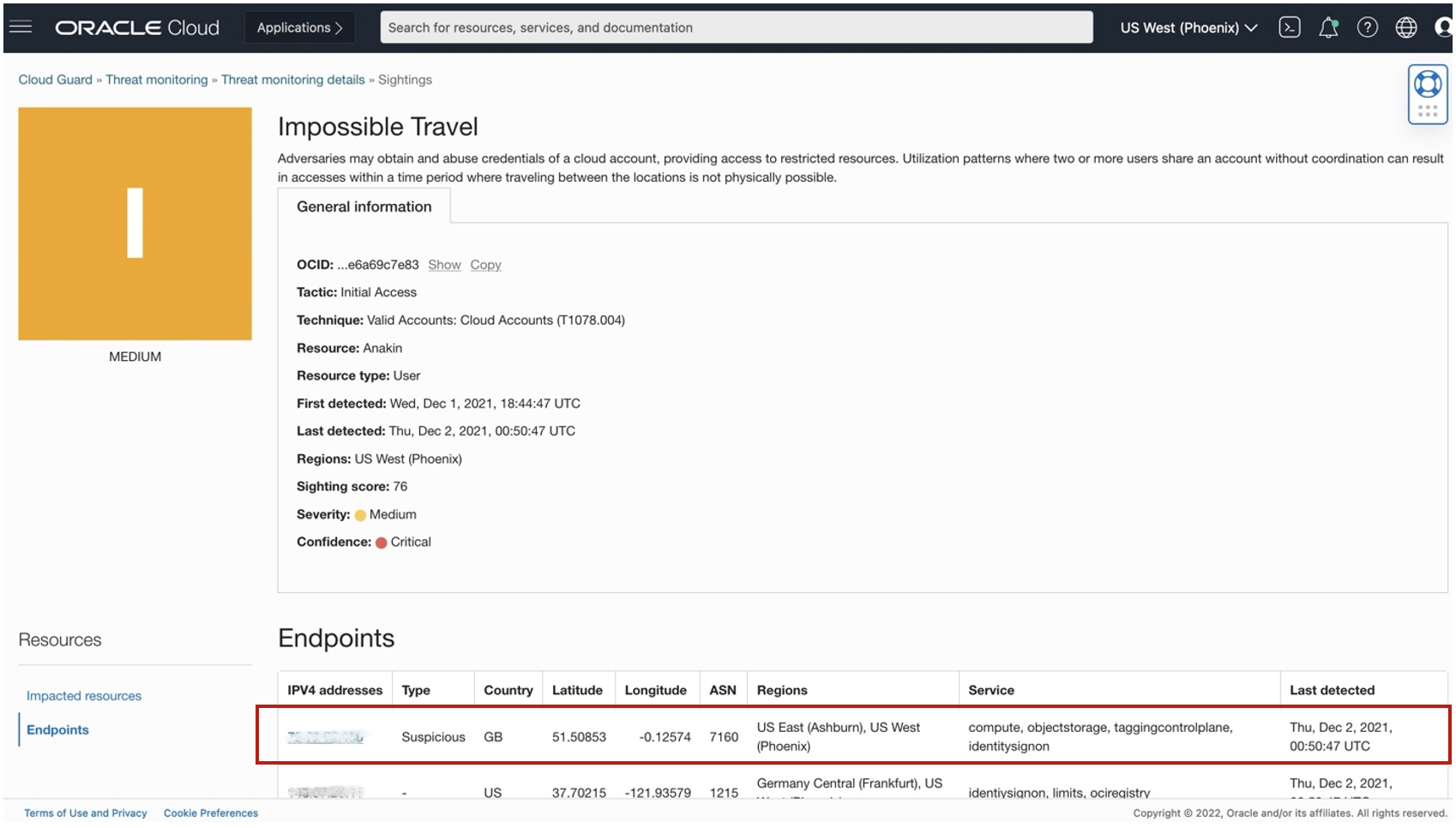
How Threat Intelligence Service works
Having Oracle manage the ingest and curation of threat intelligence data reduces the burden on your security engineers. Threat Intelligence Service ingests, deconflicts, normalizes, and processes the data, and then assigns an overall confidence score indicating potential maliciousness. Factors that affect overall confidence may include quality of the source, observations of behavior, frequency of sightings, and recency. Though overall confidence is a point-in-time assessment, we also provide the indicator history to give responders contextual insights to accelerate alert triage and remediation (see Fig. 2).
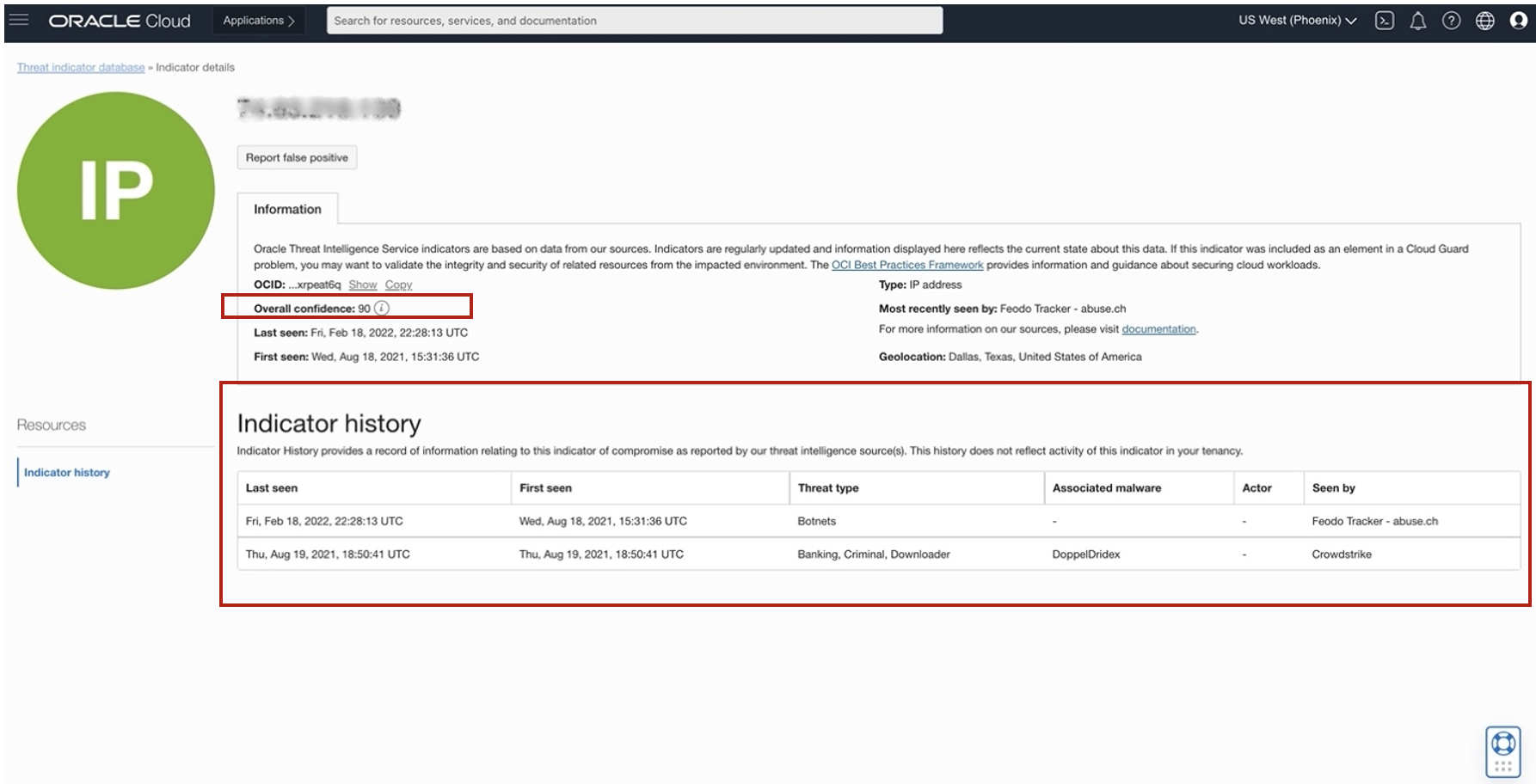
Enabling Threat Intelligence Service
In order to get the value of Threat Intelligence Service-based detections in your tenancy, you must enable Cloud Guard.
The service is integrated with Cloud Guard for out-of-the-box detections, so enabling Cloud Guard will automatically allow you to benefit from those detections.
To get additional contextual information about indicators, or access Threat Intelligence Service database, you must enable Threat Intelligence Service in your tenancy by following the steps in our documentation. To leverage Cloud Guard Threat Detector, you only need to start using Cloud Guard and add a Threat Detector recipe to a target, as shown in the documentation.
Don’t wait, get started today. Also check back here at the Oracle Cloud Security blog for more security product announcements and best practices for securing your cloud resources.
