At Oracle, we engineer best-in-class security for all SaaS products and services in Oracle Cloud Infrastructure (OCI). At the same time, as detailed in the Oracle Shared Responsibility Security Model tech brief, understanding and taking responsibility for the specific areas of ownership in the various cloud application deployment models is important. Organizations must define policies and procedures for their responsibilities of cloud security and implement the controls to meet these policies.
Shared responsibility security model
The cloud software-as-a-service (SaaS) environment has a shared security model, as opposed to an on-premises application deployment. Organizations can implement several best practices as part of their responsibilities in a cloud application deployment, as shown in Figure 1.
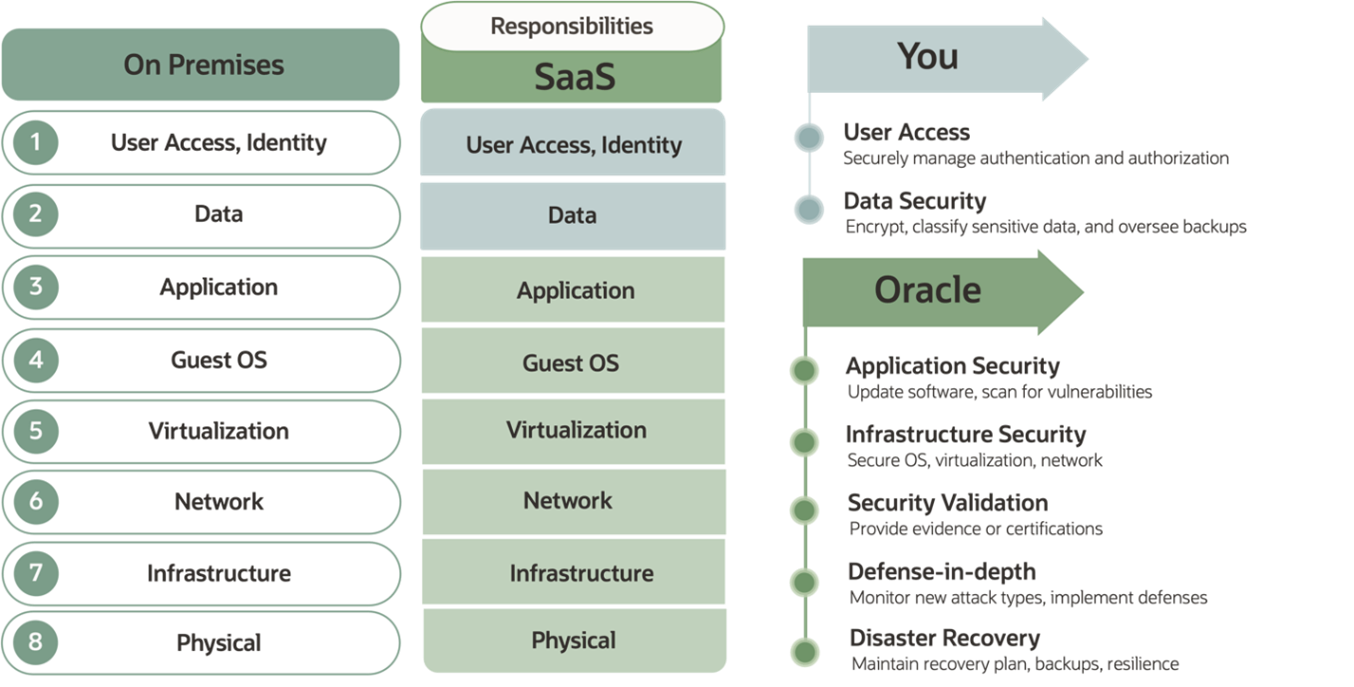
In this blog post, we share some common best practices for customer policies and procedures with specific examples and choices that you can implement in the Oracle Fusion SaaS environment.
Password rotation
We recommend that Oracle Fusion customers implement a password rotation policy to continuously maintain their security posture. Administrators can set this policy to require administrative passwords to be changed every 90 days by navigating to the security settings in the Oracle Fusion application, where they can specify the password expiration period. When set, the system automatically prompts administrators to update their passwords when they’re nearing expiration. Administrators should also create strong, unique passwords each time to ensure the effectiveness of this security measure. This regular rotation of administrative passwords helps to protect against unauthorized access and potential compromise.
Multifactor authentication (MFA)
Multifactor authentication (MFA) is a method of verifying a user’s identity by requiring more than just one log in method. In addition to a password, it can be a confirmation to a mobile device or a code to their email. We strongly recommend using multifactor authentication for all user and administrator accounts in a cloud-based environment. To enable MFA for Oracle Fusion applications, an administrator must create a new Identity and Access Management (IAM) domain and federate it with Fusion. The IAM domain enforces the use of MFA for all or selected users of Fusion applications. Many organizations have chosen to implement a third-party IAM solution and select similar MFA options, enforcement, and logging.
Identity and application logging
As noted in Figure 1, one major responsibility area is identity and data controls. You should not only configure and enforce strong authentication based on MFA , but also collect and retain all identity and application access logs. In the Oracle SaaS infrastructure, all the security logs are collected and monitored by the Oracle SaaS Cloud Security (SCS) organization as part of the Automated SaaS Cloud Security Services (ASCSS) infrastructure and stored in a Security Information and Event Management (SIEM).
However, the identity and application logs are the customer’s responsibility. We recommend that organizations collect, retain, and monitor these logs in their specific systems and tools. We also recommend that you collect them on a regular, frequent interval because not all logs in all applications and services have the same availability, retention, and storage for extended periods of time. Each application is dependent on their specific APIs and available tools to extract audits because most logs aren’t available directly or have automated connectors. For examples and FAQ, check out the Oracle support note 2723316.1.
Location-based access controls
Many organizations have employees and users who access Oracle Fusion Human Capital Management (HCM) application from various of locations and devices. In some of these cases, these users have privileged roles and entitlements and can encounter a significantly higher risk when accessing Fusion HCM from untrusted networks. One recommended best practice is to enable and configure location-based access control (LBAC) to restrict access or remove entitlement for various roles that shouldn’t be permitted from less-trusted locations.
Oracle LBAC is a feature that allows administrators to restrict the access to Fusion Applications and its REST APIs to the IP addresses of the users. If you have your own applications and use Oracle Fusion APIs, we recommend using a specific configuration to ensure that you have the most restricted access based on location and needs.
Risk management service
The Oracle Risk Management service is a cloud-based solution that helps organizations manage risks and comply with regulations related to their Oracle enterprise resource planning (ERP) applications. It allows users to automate the analysis, monitoring, and control of ERP security, configurations, and transactions using data science and AI techniques. It also provides a library of prebuilt controls, a workbench to create custom controls, and tools to streamline compliance assessments and audits. With Fusion Risk Management, customers have a modern system of internal controls that continuously examines user access and activity data as a best practice from a security and compliance standpoint.
Conclusion
Oracle’s defense-in-depth architecture and philosophy of least-privilege and zero-trust give customers the assurance that their data is well-protected and hosted in a world-class application cloud security platform. We hope that this post provides a helpful introduction of recommended best practices for Fusion application security configuration in a SaaS deployment.
If you want to learn more about HCM-specific scenarios, such as protecting employee data, compensation, and payroll, check out the overview of advanced HCM controls. If you want to access more guides, use cases, product updates, security blog posts, and more, we invite you to connect with our growing external community forums.

