This post aims to help you understand some of the technical capabilities of Oracle Cloud Infrastructure (OCI) to build modern applications. Through this brief article, you can not only create step by step an application with Spring Boot and Oracle Autonomous Database, but also natively integrate a Spring Boot application with OCI services, such as Oracle Kubernetes Engine (OKE), OCI Container Registry, and O.C.I Vault.
Why Oracle Autonomous Database?
Oracle Autonomous Database combines infrastructure automation with the Oracle Exadata platform. This database uses machine learning to eliminate the fundamental problems that have existed for decades, including complex administration, security vulnerabilities, downtime because of patching or failures, performance bottlenecks, static configurations, and high costs.
The autonomous database has the following features and capabilities:
-
Creates Exadata Cloud infrastructure, RAC and scale-out database, and active Data Guard standby.
-
Applies security updates online, prevents admin snooping with Database Vault, and encrypts all data.
-
Patches all software online, tunes settings, performs all OS and SYSDBA operations, and diagnoses errors.
-
Automates backup, restore, and application transparent failover within cluster or to remote standby.
-
Instant, automatic, and online scaling of compute and storage enables true pay-per-use.
-
Automatically optimizes data formats, indexes, and parallelism and plans for each workload.
Since Spring Boot 2.4.0 was released, the official support for Oracle UCP has been added! Particularly, we can smoothly integrate Spring Boot with Oracle Autonomous Database. So, we can mainly rely on Spring Boot configuration properties to configure Oracle UCP Connection Pool.
Protecting your credentials with OCI Vault
OCI Vault is a centralized and customer-controlled key management, and it has the following features:
-
Natively integrated to many OCI services: Autonomous, Exadata, Object Storage, and others
-
Fully managed
-
Highly available service: 99.9% SLAs and 99.99% SLOs
-
Supporting regulatory compliance: Meets PCI DSS and is certified HSM FIPS 140-2 Level 3, for cryptographic processing
Hardcoding the database credentials in the configuration files might be acceptable for less critical environments, like local developer station. Using a secret manager is the top security best practice for protecting any sensitive information, such as database credentials for a production environment. With a secret manager, you can store and retrieve any sensitive information and use encrypted keys from Vault.
We can see further how simple integrating a Spring Boot application and oci-sdk. During this demo, we use the OCI Vault encryption key to enable Kubernetes encryption of the etcd and Oracle Autonomous Database. The database secrets are also stored in OCI Vault.
Integration between OCI Vault and your Spring Boot application

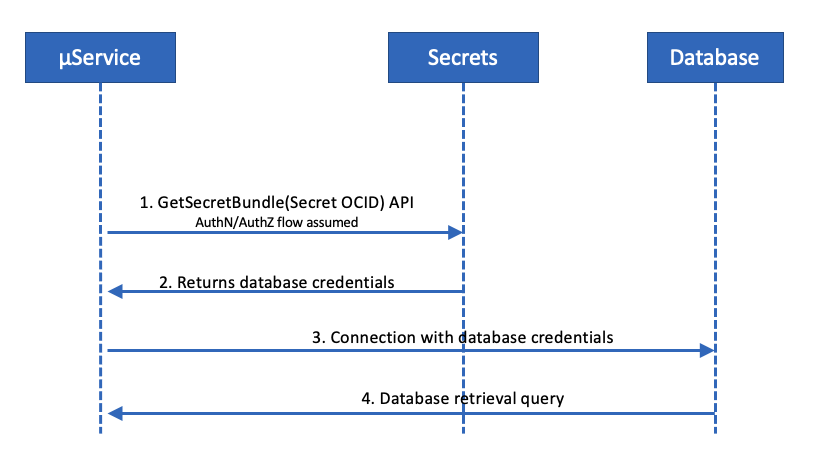
Integration between OCI Vault, Spring Boot, and Oracle Autonomous database
During the startup of the Spring Boot application, we use the oci-java-sdk-secrets to inject the database username and password into the Spring DataSourceProperties Bean.
Sample application description
The following sample application handles a user entity and exposes CRUD REST endpoints. We use swagger and OpenAPI, which provides a simple way to describe the API’s contract for consumers and can be used to share documentation. You can securely expose this API for partners using the OCI API Gateway.
The following sample code shows how you can achieve this retrieval. The integration with Autonomous Database and OCI Vault uses the following dependencies:
The following portion of code handles the retrieval of the secrets, including database username and password, from OCI Vault.
Running the sample application from your integrated development environment
Prerequisites
Provision an autonomous database on Oracle Cloud. If you don’t have an existing instance of Autonomous Database, follow these steps.
Application configuration
Store your database username and password secrets in OCI Vault. Then replace the following properties with your own configuration:
oci.tenant.region=your region
oci.tenant.vault.db-username-ocid=your username vault secret ocid
oci.tenant.vault.db-password-ocid=your passwod vault secret ocid
Running the application
Run the application using the class, HelloAutonomousdbApplication. Then, test that the application is correctly deployed, by accessing the URL, http://localhost:8080.
When you see the swagger-ui page, you can test the different exposed REST APIs:
Building the sample application
Option 1: Executable JAR with Maven
To create an executable jar, run the following command:
mvn clean packageFor testing the executable JAR locally, you can run the following command:
java -jar target/hello-autonomousdb-0.0.1-SNAPSHOT.jar --spring.config.location=/path/configuration/properties/Option 2: Building an OCI image
We can create an OCI image from an executable jar file using Cloud Native Buildpacks. You can build images using the build-image goal. The Docker image is deployed to Container Registry. To create an OCI docker image, run the following command:
mvn clean spring-boot:build-image
Option 3: Building a native image with GraalVM and Spring Native
This step is based on Spring Native and GraalVM. To create a native image, the project relies on the Spring Native project and Cloud Native Buildpacks. The docker image is deployed to Container Registry.
Run the following command:
mvn -Pnative-image clean spring-boot:build-image
Deploying the sample application in your Oracle Cloud Tenant
Prerequisites
-
kubectl
-
Docker CLI
-
Terraform 0.12.16+ is Installed
-
OCI CLI Installed
-
Maven 3
For getting your tenant configuration, you have to set up the required keys and OCIDs. Then follow the documentation for creating a compartment.
Step 2: Provisioning the infrastructure with Terraform
All the Terraform scripts are available in the folder terraform. These scripts create the virtual cloud network (VCN), subnets, security lists, OKE, Autonomous Transaction Processing, and OCI Vault. Example values for the following variables are available on the file variables.tf.
Then create your infrastructure using the Terraform script. You can run the following commands or use OCI Resource Manager to create your infrastructure:
terraform init
terraform plan
terraform applyStep 3: Deploying the application to Kubernetes using buildpacks
All the deployment scripts are available in the folder deployment. These scripts allow you to complete the following steps:
-
Download the database wallet and create a Kubernetes (OKE) secret containing the Autonomous Database wallet.
-
Create the OCI Container Registry secret so that OKE can pull the latest build of the sample application container image.
-
Create a config map containing the Spring Boot application*.yml configuration.
-
Deploy the Spring Boot application to Kubernetes cluster.
Conclusion
We believe that this guidance can help you simplify and enhance the way that you deal with Autonomous Database credentials in Spring Boot applications. The highlights of OCI Vault strengthen the enhanced security mechanisms built into Oracle Cloud Infrastructure.
For more information, see the following resources:
