Every cloud provider talks about “shared security responsibility,” but what is it really? When you’re running your enterprise software on your IT infrastructure on-premises within your own data center, as the customer, you’re responsible for the security of that infrastructure as well as the data and applications that run on it. However, when moving to a public cloud model, such as Oracle, certain responsibilities are redirected to the cloud provider.
This blog post aims to demystify and clarify the distinct roles that Oracle, as a cloud provider, and you, as the cloud customer, are accountable for in the various aspects of security and how we work together to help ensure a secure cloud environment.
So, let’s dive into how your current on-premises applications shift when moving to the cloud.
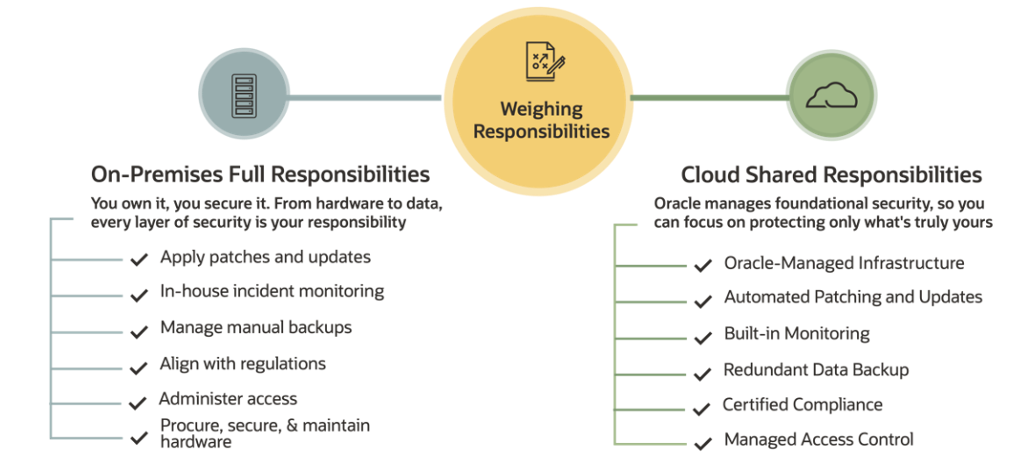
Embracing the cloud’s shared responsibility
Managing the entire spectrum from hardware to applications, including their security, can be very complex, time-consuming, and expensive. Transitioning to a software-as-a-service (SaaS) cloud model realigns these tasks with the SaaS provider assuming most responsibilities. As a SaaS provider, we assume the responsibility of securing everything from the infrastructure to the operating system and applications, freeing you to focus on managing your data, fine-tuning access, and expanding your business.
Identity and data security
In the SaaS Enterprise cloud model, you control identity and access privileges to applications. Your role involves defining, overseeing, and managing access rights to cloud resources including critical data, functions, features, or business objects, including granting, revoking, and updating access to authorized users. Your company’s Identity and Access Management (IAM) policies should govern and manage these rights. Responsibilities like user creation process, password management, log-in mechanisms, single sign-on (SSO), and any multifactor authentication (MFA) are also yours to manage. Oracle provides IAM tooling to use in conjunction with our SaaS applications, and that’s where customer IAM practices and SaaS comes together from an identity management point of view.
Keeping a rigorous standard for user access hygiene is a cornerstone of cloud security, including privileged access management (PAM). As the data custodian, it’s your responsibility to ensure that all data, both incoming and outgoing, is securely managed. Implementing Transport Layer Security (TLS) for encrypting data in transit is vital to protect it before it reaches Oracle’s endpoints and safeguard the confidentiality and integrity of data in transit to and from the SaaS services.
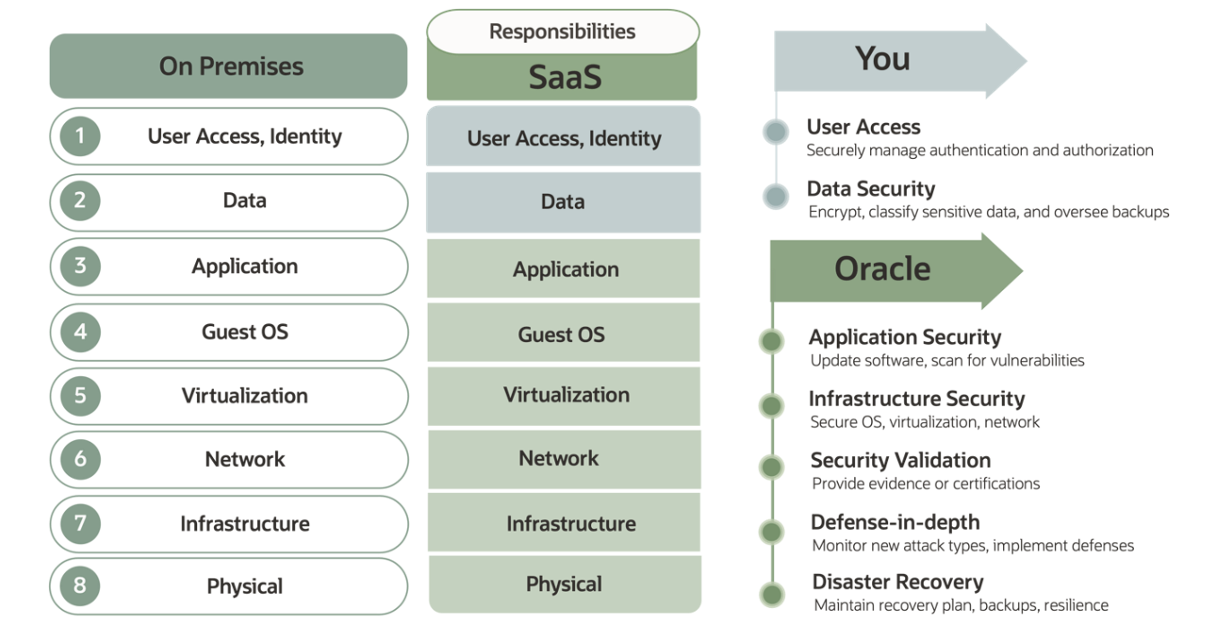
Configuration and security management
Managing configurations plays a big part in securing data in the cloud. Gartner states that “misconfigurations account for 90% of cloud security breaches.” As a customer, you must prioritize configuration management as a core practice, monitoring and validating continuously for any security flaws. Start by understanding and aligning your application security controls with your security policies and best practices. Implement strict governance and conduct thorough audits to maintain correct configurations. Key practices include the following examples:
-
Work with Oracle to configure your VPN correctly with a service request
-
Build and configure your allow/deny IP list with a service request
-
Manage your keys by adhering to best practices through the use of Oracle Key Manager and Oracle Cloud Infrastructure (OCI) Vault service. OCI Vault is exclusive to Fusion customers with Breakglass service.
-
Administer user identity, passwords, roles
Monitoring
Vigilance is key, regularly reviewing and monitoring security across your SaaS applications should be part of your governance practices. Ensure consistent validation and monitoring of all configurations, identity and access rights, and any sensitive data changes. Use udit APIs or tools such as Oracles Risk Management and Compliance service to effectively monitor and detect user access and compliance issues.
Compliance
Oracle undertakes annual compliance audits that follow national, regional, and international framework, helping to ensure that our controls meet industry standards. As a customer, your role is to regularly review our certifications, including Service Organization Controls (SOC), Payment Card Industry (PCI), Health Insurance Portability and Accountability Act (HIPAA), and Federal Risk and Authorization Management Program (FedRAMP) reports, as well as our Oracle Security Practices. Work directly with your customer support executive to obtain these reports.
Communication
Staying informed is a fundamental aspect of your shared security responsibility role. Keep an eye out for our updates, including security alerts, service downtimes, and maintenance plans, and any performance-related notifications.
Similarly, make it routine to review the my Oracle support articles, Oracle blogs, and new feature or product announcements in our Customer Support portal. Engage with experts through our Cloud Customer Connect program. For deeper involvement, join the Voice of the Customer to discuss directly with our SaaS Cloud Security (SCS) team. If you have a question or need to report an incident, file a service request classifying it as a security event.
Trust but verify
As your SaaS Cloud provider, Oracle maintains robust security measures to protect your data. As a customer, it’s your responsibility to regularly verify the security status information for your services. Key resources include the Consensus Assessment Initiative Questionnaires (CAIQ), Security Information Gathering (SIG) Questionnaire, SOC 1 and 2 reports, and annual Security Assessment reports. These reports provide comprehensive insights. If you need an in-depth review, invoke your audit rights according to your contract and visit our Trust Center to learn more about our publicly available materials. Top of FormBottom of Form
Follow best practices
To fortify your SaaS cloud security, align with industry best practices. Adopt thorough data discovery, encryption, key management, and workstation data loss prevention (DLP) solutions. Some Oracle applications have integrated file and document scanning capabilities using Internet Content Adaptation Protocol (ICAP). We always recommend file scanning before uploading them to the cloud to maintain strong security governance and policies.
Education
A critical component of a secure cloud strategy is educating all enterprise users of SaaS cloud systems about their security responsibilities. As a customer, it’s your responsibility to ensure your employees receive proper security training. We, as the Cloud Provider take training our employees, about security, very seriously. Annual training sessions are a good measure to keep teams aware and vigilant, and they cover the following topics:
-
Security policies and practices
-
Maintenance on segregation of duties
-
Awareness of latest threats in areas such as social engineering and phishing
-
Safe browsing
-
Secure data handling
-
Password management
Conclusion
In a world of modern threats where we’re consistently fighting bad actors, protecting our systems, data, and reputation is a joint responsibility. As a SaaS provider, Oracle shoulders a significant part of the security responsibility. However, the essence of shared security is collaboration. Recognize and fulfill your role in safeguarding your assets.
We hope this post has shed some light on what Oracle SaaS Cloud means by shared security responsibility. To gain a deeper understanding and enhance your security strategy, we encourage you to explore the informative links we’ve provided throughout this blog.


