Oracle Cloud Infrastructure (OCI) offers many popular Oracle platform- and infrastructure-as-as-service (PaaS and IaaS) applications, including Autonomous Data Warehouse, Oracle Analytics Cloud, Streaming, Data Safe, and many more.
This blog discusses private access to Oracle services through private endpoints. With this capability, you can access OCI services from within your OCI virtual cloud network (VCN) or on-premises networks directly through private IP addresses, avoiding the unpredictability of latency and performance over the internet. This service addresses the demands for ubiquitous and secure private access when consuming Oracle services.
Private endpoints are available in all Commercial and Government regions. Many popular Oracle services support private endpoints today, and support for other Oracle services continues to roll out.
OCI customers have the following connectivity options for connecting to popular Oracle services, depending on your needs:
- Public access through a VCN: You can access Oracle services from within OCI using VCN routing through an internet gateway for public subnets or NAT gateway for private subnets. In each case, the connectivity is routed publicly. For more information on the use and setup of internet and NAT gateways, see the documentation.
- Public access through FastConnect or site-to-site VPN public peering: You can access Oracle services directly from on-premises through a public virtual circuit with or without a site-to-site VPN, peering between your customer-premises equipment and Oracle’s Edge. For more information on the use and setup of FastConnect public peering, see the FastConnect documentation.
- Private access through a VCN service gateway: You can access Oracle services from within OCI using VCN routing through a service gateway. Service gateways allow customer VCNs or backend premises networks access to Oracle services’ public IP addresses without the need to route traffic over the internet using an internet or NAT gateway. This setup ensures that traffic is routed over Oracle’s private backbone. For more information on the use and setup of service gateways, see Access to Oracle Services: Service Gateway.
- Private access through FastConnect or site-to-site VPN private peering through a VCN service gateway: You can access Oracle services over a FastConnect private virtual circuit or site-to-site VPN. Traffic transits through a VCN, and then through a service gateway to the Oracle service of interest. For more information on the use and setup of FastConnect private peering, see the documentation.
![]() Public access refers to connectivity to a service’s public CIDR. Traffic doesn’t necessarily traverse the public internet. Often, even with the use of internet and NAT gateways, traffic may traverse Oracle’s private backbone.
Public access refers to connectivity to a service’s public CIDR. Traffic doesn’t necessarily traverse the public internet. Often, even with the use of internet and NAT gateways, traffic may traverse Oracle’s private backbone.
Private access through private endpoints
Many Oracle customer cloud networks are designed to prevent outbound connections to the internet. Typical on-premises deployed services are hosted on the enterprise intranet and don’t require public internet access. Migrating these services to the cloud by using the public connectivity model requires customers to enable internet access for their backend clients and punch holes in their firewalls and other security controls. Private connectivity using a service gateway offers a private and secure alternative. Although service gateways enable private access to Oracle services from customer OCI and on-premises networks, this access is over a publicly accessible IP.
Private endpoints are an evolution of the private connectivity model where customers access Oracle service over a private IP taken from a subnet within their VCN. This capability allows a customer experience where the service is hosted in their own private network, either in their own VCN or on their on-premises site. When allowed, private endpoints support reverse connections to allow Oracle services to initiate connections to instances within the customer’s VCN or on-premises data sources—a common use case and pattern for database services that isn’t supported when using the private connectivity with the service gateway access model.
The following architectural diagram depicts how customer-to-service (C2S) or forward direction and service-to-customer (S2C) or reverse direction traffic flows through the private endpoint. Within the customer VCN, the private endpoint is a logical representation of the service’s fully qualified domain name (FQDN) or IP address. Customers access the service using a dynamically allocated free private IP address from their chosen subnet as a target. Private endpoints physically reside outside the customer VCN and are managed on-behalf of the customer by the service provider.
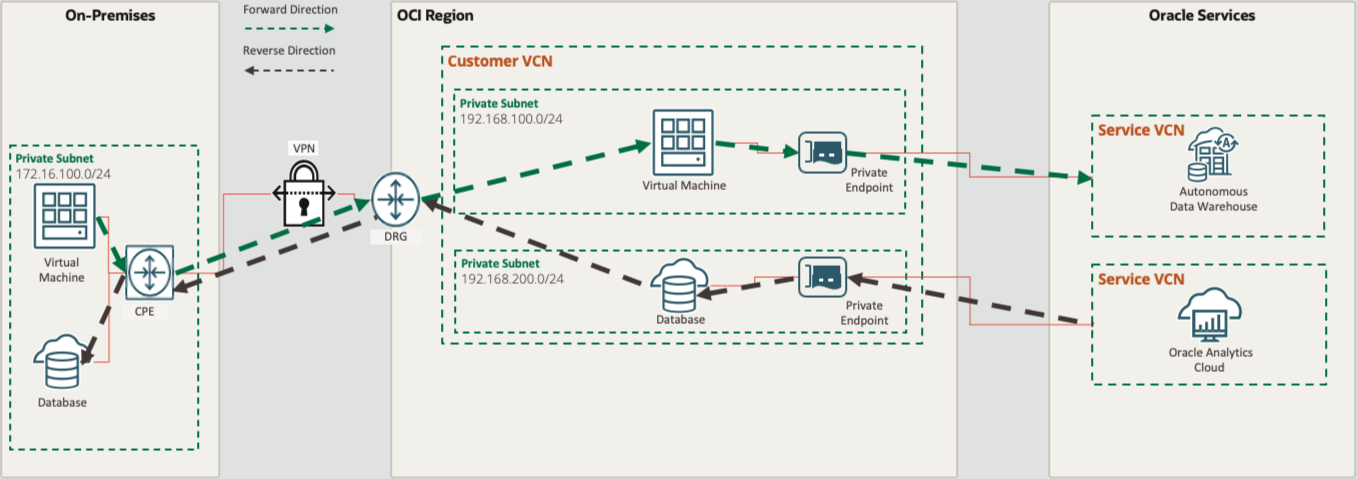
Figure 1: Private endpoints logical architecture diagram
Use cases
Private endpoints provide the following use cases and benefits:
Extended private connectivity
Many Oracle customers are seeking a familiar on-premises private access connectivity model when access to Oracle hosted services is over private instead of public IP addresses. Private endpoints extend private connectivity from customer premises and OCI tenants by ensuring that traffic to Oracle services uses the private Oracle backbone, OCI.
Enhanced security
If your organization has strict security mandates that don’t allow you to have a public endpoint in which traffic isn’t permitted to traverse the internet, private endpoints further provide a secure way to privately connect to Oracle hosted services. You can also use Oracle security lists and network security groups (NSGs) to provide granular access controls to traffic destined to Oracle services using private IP address space as both source and designation targets.
Seamless service integration
Oracle service providers manage the entire customer experience on behalf of consumers for a seamless experience. Consumers only need be concerned with provisioning the individual service they want that supports private endpoints. When interacting with the service console or API, service providers give customers the option to use private endpoints within a customer subnet and NSG. Customers aren’t responsible for managing the lifecycle of private endpoints. When they end the service, the private endpoints associated with the service within their VCN are also deleted.
Simplified management
Private endpoints are easy to use because they remove the need to deploy and manage NAT and service gateways and eliminate the need to modify any route tables for connectivity to a service.
Reverse connection
Reverse connections or S2C functionality enables Oracle services to privately begin connections to instances within the consumer’s OCI VCN or on-premises network. This capability provides Oracle Analytics Cloud (OAC) and similar services the ability to connect to customer database endpoints within a VCN or premises for data ingest using traditional IP and SCAN protocols.
Domain name system resolution
Often, customers access Oracle Services using the service’s FQDN, relying on Oracle’s private Domain Name System (DNS) service to resolve it to an IP address. Private endpoints can resolve the Oracle service FQDN automatically from within the consumer VCN. This feature allows customer instances to use the DNS name when accessing the service to avoid TLS/SSL certificate mismatch errors. For Reverse Connections, private endpoints can also resolve customer FQDNS automatically from within the service provider VCN when initiating connections to customer instances in the reverse direction (S2C).
Single client access name (SCAN)
SCAN is a proprietary protocol owned and used by Oracle databases. SCAN protocol and its listeners are application-level load balancer for Oracle Database Real Application Clusters (RACs). Private endpoints with reverse connection endpoints allow services to support SCAN protocol with Oracle Wallet credentials for added security when connecting to customer database instances.
Private endpoint versus service gateway
Though both service gateways and service private endpoints enable private connectivity between private customer networks and Oracle services, they satisfy private access requirements differently. The following table helps clarify when private endpoints are a good fit.
| Functionality | Private endpoint | Service gateway |
|---|---|---|
| Ease of access | Consumers can’t open access to multiple services with one service private endpoint. They need to create a service private endpoint for each service (or service instance) they need access. | Consumers open access to all services or just Object Storage using a single service gateway. |
| Limiting services |
Further limit traffic using security lists or NSGs applied to a single service. |
Further limit traffic using security lists or NSGs by specifying all services or single service using specific services IP ranges. |
| Private connectivity direction |
Service Private Endpoint support connections in both directions. |
Consumer can initiate a connection to the service, but a service can’t initiate a connection to the consumer private network. |
| Resource limits |
Private endpoint isn’t counted as a customer resource. |
Service gateway is counted as a customer resource. |
| Selective access |
Single endpoint provides access to single service. |
Single gateway provides access to multiple services. |
| Service endpoint representation |
Represented using the private IP address inside the consumer network. |
Represented as a gateway to enable private access. Service is represented using the public IP address outside the consumer network. |
| Specific address |
Need to know specific private IP addresses for the service’s private endpoints, which are inside the VCN’s CIDR. |
Service’s public endpoints are represented as an “all services in OSN” object. |
Usage
Many popular Oracle services support private endpoints today and many have support on the short-term roadmap. You can find more information on the use and setup of private endpoints for the following popular services:
- Oracle Analytics Cloud
- Oracle Autonomous Data Warehouse
- Oracle Data Catalog
- Oracle Data Flow
- Oracle Database Management
- Oracle Data Migration Service
- Oracle Data Safe
- Oracle GoldenGate
- Oracle Container Engine for Kubernetes (OKE)
- Oracle Streaming
![]() Services gateway: All services listed also support services gateway for access to Oracle services.
Services gateway: All services listed also support services gateway for access to Oracle services.
Conclusion
We believe that private endpoints can enhance and simplify how you work with cloud networking and look forward to hearing about how this feature improves your network design and solution development. As private endpoints become available across all services, customers benefit from a secure, reliable, and performant private access methodology for connecting to Oracle services.
Thank you for your interest in private endpoints. On behalf of the Virtual Networking product team, we encourage you to share any product feedback that you have through email to the Virtual Networking group or submit a note in the comments. You can find more information on Private Endpoints and other topics discussed in this blog using our online documentation and the following links.
