This blog post is part 6 of our multipart series on data sovereignty in the cloud.
When understanding encryption, you have a lot of ground to cover. Our last post in the series, Secure your data with enhanced cryptographic solutions, looked at how Oracle Cloud Infrastructure (OCI) customers can benefit from cryptographic solutions, including vaults, hardware security modules (HSM), and confidential computing. Using tools like these can be crucial to maintaining control over the data you place in the cloud.
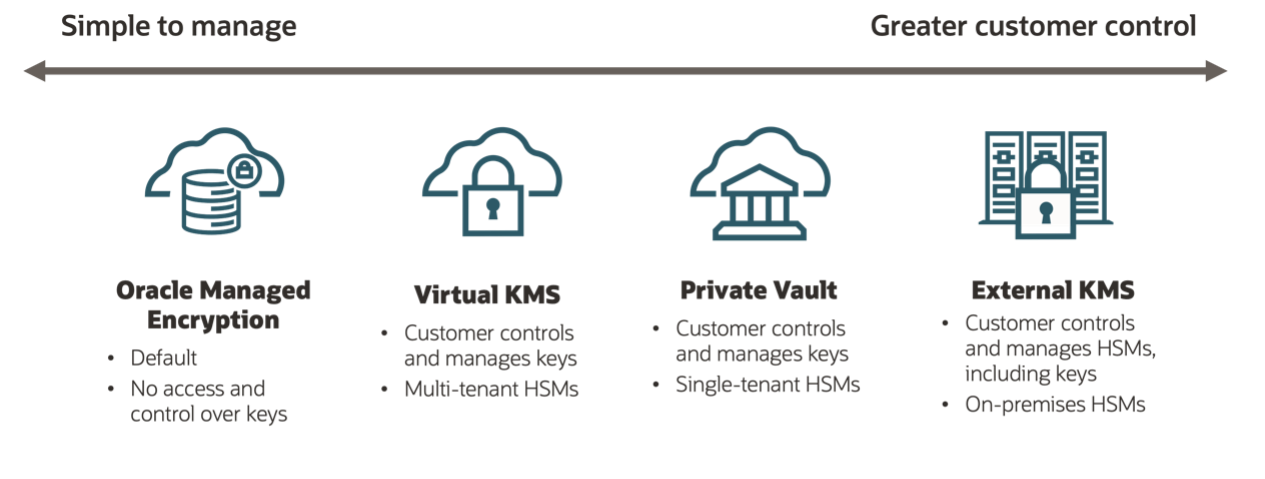
Now, we want to dive deeper into encryption keys, specifically who is managing the encryption keys you use in the cloud and where are the keys being held. To further ensure data sovereignty, many regulators have started to require that the key creation process occur outside the cloud where you host your data. For this reason, OCI offers the Bring Your Own Key (BYOK) feature for OCI Vault to encrypt resources with keys created outside of OCI.
We also recently announced OCI External KMS (EKMS), which goes one step further and keeps your master encryption keys outside of OCI at all times. Often called “Hold Your Own Key” (HYOK), this approach to key management is considered by many to be the pinnacle of enhanced data sovereignty. We’re incredibly excited to add EKMS to our portfolio of key management services and continue providing customers with the tools they need to implement secure data protection strategies.
What is OCI External KMS and how does it work?
Built in partnership with the Thales Group, OCI EKMS enables organizations to store their OCI keys externally on virtual or physical Thales CipherTrust Cloud Key Manager (CCKM) appliances. Using Thales CCKM, organizations can store their keys in a FIPS 140-2 Level 3 appliance and have the flexibility to choose the location of their encryption keys to ensure data can’t be read outside of certain national boundaries. This function includes the capability to store and manage cloud and on-premises keys with the same CCKM appliance for a seamless experience for existing Thales customers.
EKMS uses Thales’ HYOK functionality and enables customers to encrypt their data using encryption keys that are created and managed by the customer outside of a customer’s OCI tenancy. EKMS encryption keys always stay within the custody of the customer and are never imported into OCI, putting customers in control of the physical storage of keys outside the cloud. This service helps OCI customers address their data protection and regulatory requirements and be assured that their keys are never managed by Oracle operators.
Using EKMS also provides an extra level of protection by disabling master encryption keys from your own key management system, and in the event of a security incident, data in the cloud is prevented from being decrypted. Regardless of which OCI deployment model you choose, whether OCI’s public cloud, Oracle EU Sovereign Cloud, or an OCI Dedicated Region, you have access to all of the same key management features.
Combine EKMS with Oracle EU Sovereign Cloud to strengthen your sovereignty posture
If you aren’t already familiar with Oracle EU Sovereign Cloud, these OCI data regions located in EU-based data centers are physically isolated from other Oracle commercial public cloud regions. The EU Sovereign Cloud regions are owned by dedicated Oracle European legal entities and operated and supported by EU residents. These features enable commercial and public sector organizations to place sensitive data and applications in the cloud and align with EU data protection requirements.
Complementing EU Sovereign Cloud with the EKMS feature on Thales CCKM provides customers with more security control capabilities to strengthen their sovereignty strategy. EKMS allows segregation of duty between the key management and custody solution and the encrypted resources in OCI. Furthermore, by using solutions from Thales, an EU company with Common Criteria certified HSM solutions, customer ownership and control of encryption always keeps customers in control of their data encryption.
It’s no coincidence that we launched the Oracle EU Sovereign Cloud regions and OCI EKMS only a few months apart. The data sovereignty landscape is rapidly changing, and nowhere is this shift more apparent than in the EU. For customers in the EU to meet their regulatory requirements, technological solutions need to keep pace with the evolving environment.
Getting started with Oracle Sovereign Cloud solutions
At Oracle, we firmly believe that one cloud doesn’t fit all. We’ve seen firsthand how the needs of our customers vary depending on the region they’re located, the industry they operate in, and the type of data they’re managing. Some customers’ IT strategies involve using multiple clouds or keeping specific applications or workloads on-premises.
We’re committed to building simple, customizable solutions and industry-leading capabilities that help you realize your business objectives and regulatory requirements. This latest partnership with Thales to develop OCI EKMS is just another example of how Oracle is putting the customer first to deliver data security and sovereignty solutions.
In this series, we’ve already covered how access to data is restricted within OCI and how customers can implement a least-privileged access model. But what does this model look like when a law enforcement agency requests access to your data? In the next post in the sovereign cloud series, we focus on how Oracle handles and reports on extraterritorial law enforcement requests for data access, including interactions with local authorities.
If you have any questions about OCI’s new EKMS service or want to learn more about Oracle sovereign cloud solutions, contact one of our representatives. To learn more about the various deployment models that Oracle Cloud Infrastructure offers, see the following resources:
