This post is part 3 of our multipart series on data sovereignty in the cloud.
To enable customers to implement a strong data sovereignty strategy, Oracle developed a distributed cloud approach that provides organizations with more options to control their data. Whether the features and capabilities of Oracle Cloud Infrastructure (OCI) services or the way we build cloud regions, security and access management are fundamental to data protection. Data protection regulations have very specific requirements about who, where, and how data can be accessed, processed, and stored.
One of the ways that security and sovereignty converge is through OCI’s physical and logical isolation between groups of cloud regions, which we talked about in our previous article, Using realms for enhanced cloud isolation. OCI’s unique realm isolation approach provides a construct for restricting who has access to different types of regions and implementing specific compliance standards based on unique customer use cases and requirements. Realms can be characterized as an immutable piece of access management within OCI.
In this post, we’re going to dive further into access management, including how managing access to cloud resources and data can mitigate the risk of unauthorized access, collection, use, or disclosure of data.
How Oracle manages access to OCI
In the cloud computing industry, we often talk about the idea of shared responsibility, where a cloud service provider is responsible for the security of the cloud, and customers or tenants are responsible for security in the cloud. But what does this process look like in practice?
Oracle manages our engineering and operations teams’ access to the parts of OCI that are necessary to develop, administer, and support OCI. Access to OCI is based upon the concept of least privilege, which means restricting role entitlements to the minimum required to perform functions and implementing strict identity authorization policies. Access of operations staff to the infrastructure and services supporting OCI requires multi-factor authentication, a VPN connection, and an SSH connection with a user account and password or private key.
Security doesn’t end with authorization and authentication. Monitoring access is just as critical. OCI employs solutions to continuously monitor authentication logs for servers and network devices supporting OCI services.
The same access controls are implemented across all OCI deployment models. However, sometimes the ability to manage access requires the ability to implement more layers of restrictions based on security clearance and residency of personnel. Thanks to our realm isolation, Oracle has engineered a process to support this type of enhanced access restriction. These added levels of access control stand at the core of our distributed cloud strategy and allow OCI to offer distinct support and operations models for our Government Cloud, isolated regions, and European Union Sovereign Cloud regions.
The number of regions in the following table is current as of May 2023. OCI is regularly opening new cloud regions. For the latest details, refer to Public Cloud Regions.
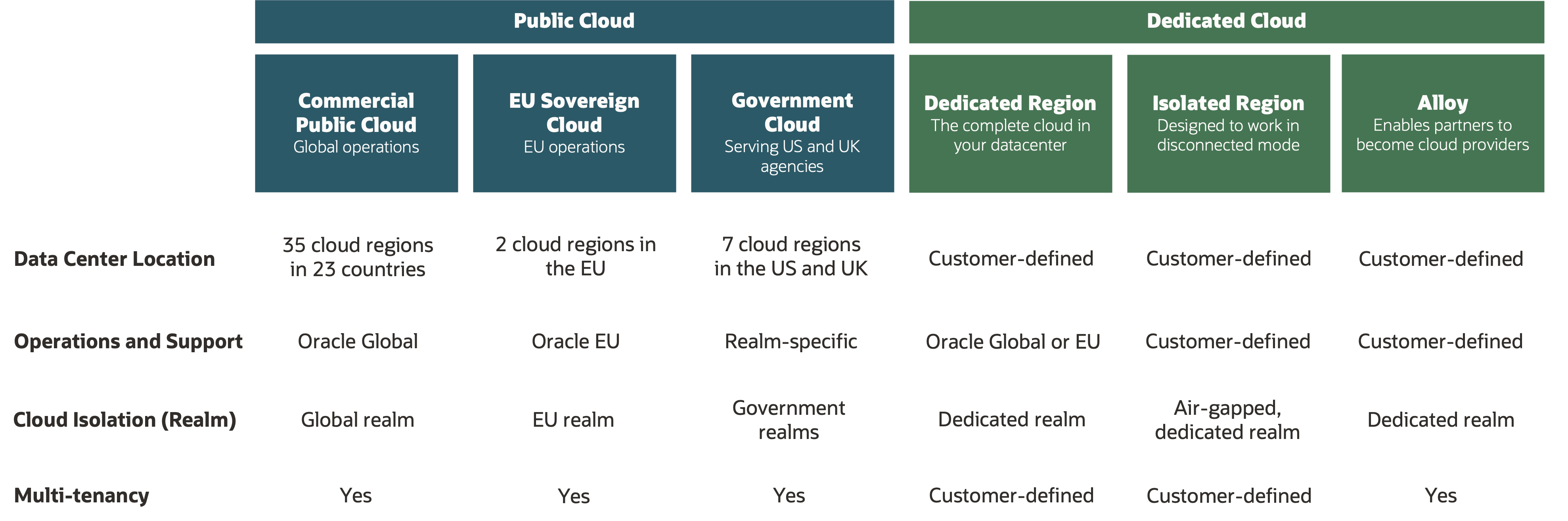
How customers manage access in OCI
As a cloud provider, Oracle has no insight into the customer data that you collect, process, or store in OCI. You are responsible for the security of your data in the cloud, and part of implementing good security practices includes managing access to cloud resources and data, including properly classifying your data and meeting any associated compliance requirements. In data sovereignty, this aspect means protecting against unauthorized access, use, or disclosure of data.
Regardless of which cloud deployment model you select, OCI’s services and capabilities provide features that can limit access to cloud resources and data stored in your cloud tenancy and help monitor access and security risks. Organizations can use the following core OCI services to implement a comprehensive approach to access management:
-
The Identity and Access Management (IAM) service lets customers control who has access to their organization’s cloud resources. IAM is flexible enough to support customer security models across tenancies, or restricted to a single tenancy, compartment, or set of resources.
-
Vault key management provides centralized management of the encryption of customer data with keys that you control. Create, rotate, enable or disable keys, assign keys to resources, and use keys for encryption and decryption to safeguard data. You can implement Vault either as a multitenant software-based key management service or as a dedicated HSM module, as the situation dictates. In either case, Vault is exclusively located within the realm.
-
The Audit service logs calls to the OCI public application program interface (API), whether those calls originate from the Oracle Cloud Console, software developer kit (SDK), or command line interface (CLI). Audit log contents include the activity that occurred, the user who initiated it, the date and time of the request, the source IP address, the user agent, and more. Data from these logged events can help you safeguard your data by enabling you to monitor the activity within your tenancy, including tracking administrative actions on your keys and vaults.
-
Access Governance is a cloud native identity governance and administration (IGA) solution that delivers insights-based access reviews, identity analytics, and intelligence capabilities. It enables you to audit user capabilities and actions to determine current appropriate levels of access to tenancy administration functions.
-
Cloud Guard and Security Zones work together to define and enforce security policies for your configuration and users, monitor changes and activity in your tenancy, and take corrective actions when issues are detected.
Oracle’s Everything Everywhere initiative drives technical and operational parity across all deployment types. So, you can be assured that all the OCI security and identity services are available to you, regardless of the cloud deployment you choose. Managing access to your cloud resources and data contributes to a strong data sovereignty strategy, but it doesn’t end there. Controlling access also means being able to move your data when you need to.
OCI offers portability and availability of data to customers
As more customers are adopting a multicloud approach, the importance of data portability and availability can’t be understated. The ability to control your data, even to the extent of moving it away from a cloud provider, is an important aspect of data sovereignty.
At Oracle, we believe that if you need to migrate your data, you shouldn’t be penalized for it. Unlike other cloud service providers that restrict your data with high pricing for network egress, our approach is to give customers everyday low pricing for network egress and free ingress.
To enhance the portability of data, we offer industry-leading low outbound data transfer rates and services like OCI Data Transfer to move data into or out of your OCI environment securely. Oracle also makes contractual commitments to ensure that your data rights remain intact, even in the event of termination and exit.
Oracle makes it easy and cost-effective for you to move your data in and out of OCI, even for workloads with massive data transfer requirements. It’s your data, and you should be able to have control over it.
Get started with Oracle sovereign cloud solutions
A strong security posture is a critical component of any sovereign cloud strategy, and appropriate access controls need to be in place. Oracle sovereign cloud solutions ensure that you’re in control of your data and have the capabilities and features to mitigate the potential risk of unauthorized access, collection, use, or disclosure of data.
The next article in our sovereign cloud solutions series, Implement more personnel requirements, focuses on how cloud operations and support can provide more protection and controls for the most sensitive workloads. We talk about what this process means for OCI Government Cloud, isolated regions, and European Union Sovereign Cloud regions and why it matters to your sovereign cloud strategy.
If you have any questions about access management or want to learn more about Oracle sovereign cloud solutions, contact one of our representatives. To learn more about the various deployment models that Oracle Cloud Infrastructure offers, see the following resources:
