In our constant pursuit to enhance the security features for our Oracle Cloud VMware Solution customers, we’re happy to announce the availability of shielded ESXi instances.
Shielded ESXi instances for VMware Solution hardens the security of the ESXi nodes by ensuring that only valid and authenticated software is booted on the system. With secure boot enabled an ESXi instance refuses to load any UEFI driver or app unless the operating system (OS) boot loader is cryptographically signed, and only digitally signed vSphere installation bundles (VIBs) can be installed on the ESXi Instances. Shielded ESXi instances uses a combination of Secure Boot and Trusted Platform Module (TPM) to harden the firmware security of ESXi instances.
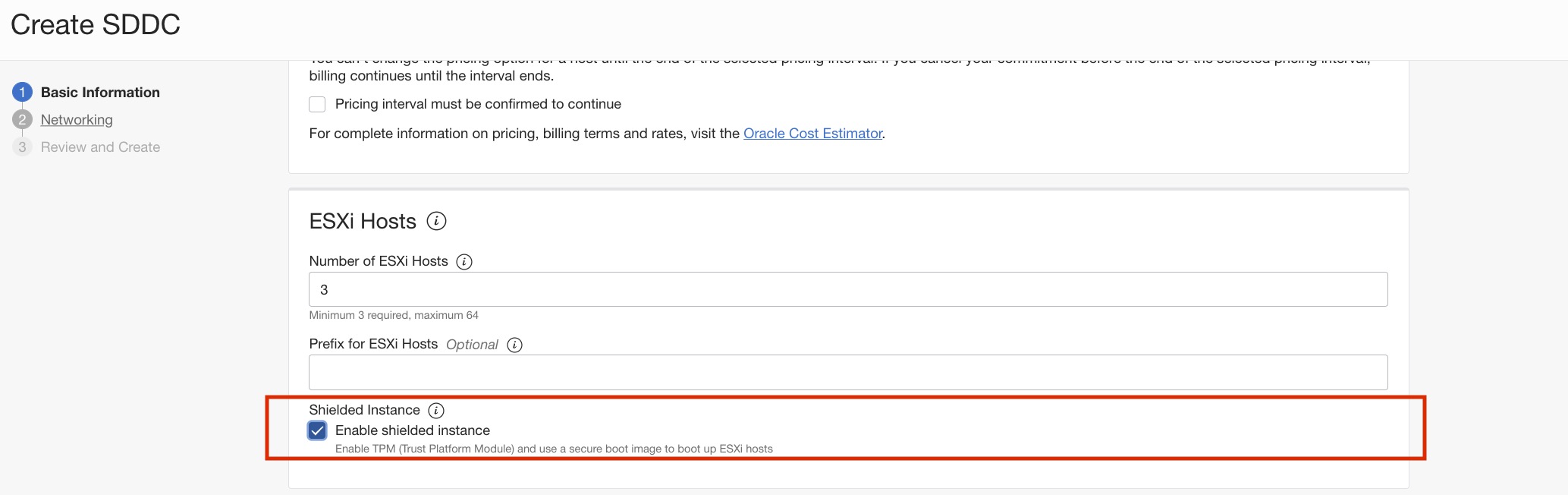
Shielded ESXi instances are enabled at the software-defined data center (SDDC) level at the time of SDDC creation, and all ESXi nodes under the SDDC have this feature enabled. You can’t enable this feature for an existing SDDC.
What are Secure Boot and TPM?
Secure Boot checks the signature of each piece of boot software, including firmware drivers, extensible firmware interface (EFI) applications, and the OS. If the signature is valid, the server boots, and the firmware gives control to the OS. If the signature isn’t found in the valid signatures database, the system doesn’t boot.
Trusted Platform Module (TPM) is a computer chip that can securely store artifacts, such as signatures, certificates, and encryption keys, used to authenticate the platform. vTPM is a software representation of a physical TPM that virtual machines (VMs) can use.
On the ESX hypervisor, Secure Boot and the TPM work in conjunction. So the shielded ESXi instance enables both these features for VMware Solution customers. Secure Boot and TPM have also been cited as a STIG requirement to protect the VMware cluster for ransomware attacks.
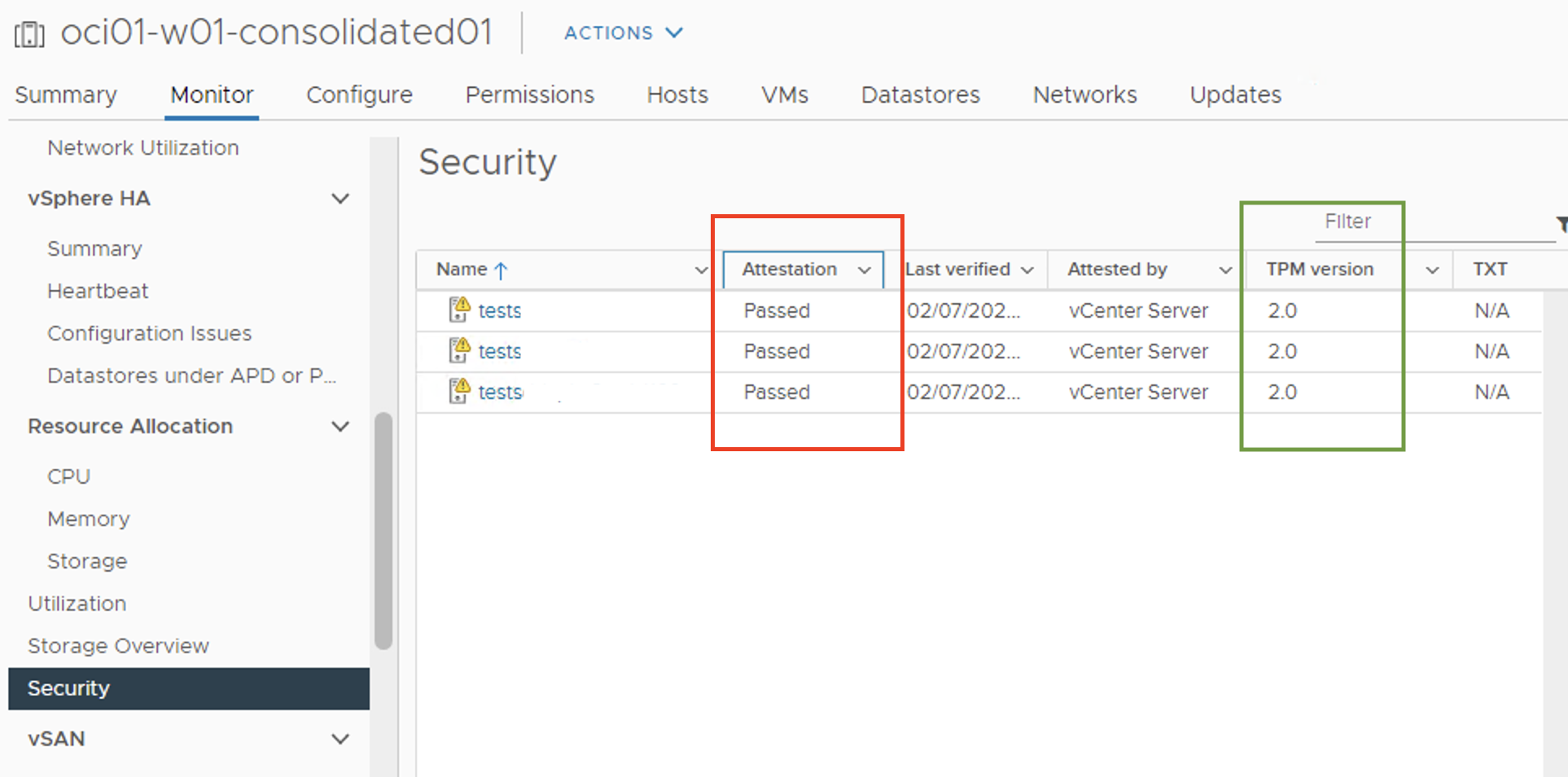
When the SDDC is created, you can validate that the ESXi instances now have attestation passed and have TPM2.0 enabled.
For the Terraform community, you can enable the shielded ESXi instances feature by adding the following parameter to the oci_ocvp_sddc resource:
resource "oci_ocvp_sddc" "test_sddc"{
//Optional
is_shielded_instance_enabled = true
}Conclusion
To learn more about securing the ESXi instance using secure boot and TPM2.0, refer to the documentation. If you have any queries or suggestions, contact us at oci_ocvs_product_ww_grp@oracle.com.
