Enterprise organizations typically use an identity provider (idP) for logging and authenticating users. Administrators can use different idPs, such as Azure Active Directory or Okta, and federate into Oracle Cloud Infrastructure (OCI). Customers can use Oracle identity domains in US Government and Department of Defense (DoD) regions when it completes accreditation.
This blog shows how to federate users in OCI US Government Cloud with Microsoft Azure Active Directory (Azure AD). When federation is set up, users get a single sign-on experience where they can use their Azure AD login and password to access OCI US Government Cloud. Once approved, the idP authenticates the user and grants access to services and resources inside the Oracle Cloud tenancy.
Achieving federation in government tenancies from Azure AD has three important steps—a crucial distinction between commercial and government cloud.
- Disable Holder of Keys (HoK).
- Enable token encryption in Azure
- Use group IDs to map to OCI groups.
Disabling HoK is a critical step in the process because federation do not work with idPs that don’t support HoK assertion. HoK is enabled when customers onboard government tenancies. To disable HoK, open a support request. This process can take 1–2 days, so plan ahead.
For step-by-step instructions, see Federating with Microsoft Azure Active Directory.
Please note that steps 6 and 8 in the following High-levle steps are different from commercial cloud.
High-level steps
- Download the SAML cert from the federation page in the Oracle Cloud Console. In the menu under Identity and Security, select Identity and then Federation.

- In the Azure portal, create Azure Enterprise application and select Oracle Cloud Infrastructure Console.
- Select Single Sign-on and upload the OCI SAML document, this will autofill several fields. Verify the sign-on URL. This value is the sign-in page URL for your application.
- Edit the Attributes and Claims section and change the name identifier to Persistent before saving.
- Add a group claim and select Source Attribute as the Group ID.
- In advanced options, check the box that says, “Customize the name of the group claim” and set the name to GroupName and the NameSpace to https://auth.oraclecloud.com/saml/claims.
- Click Save.
- Download the Azure Federation Metadata XML, this file will be used later to create idP in Oracle Cloud Console.
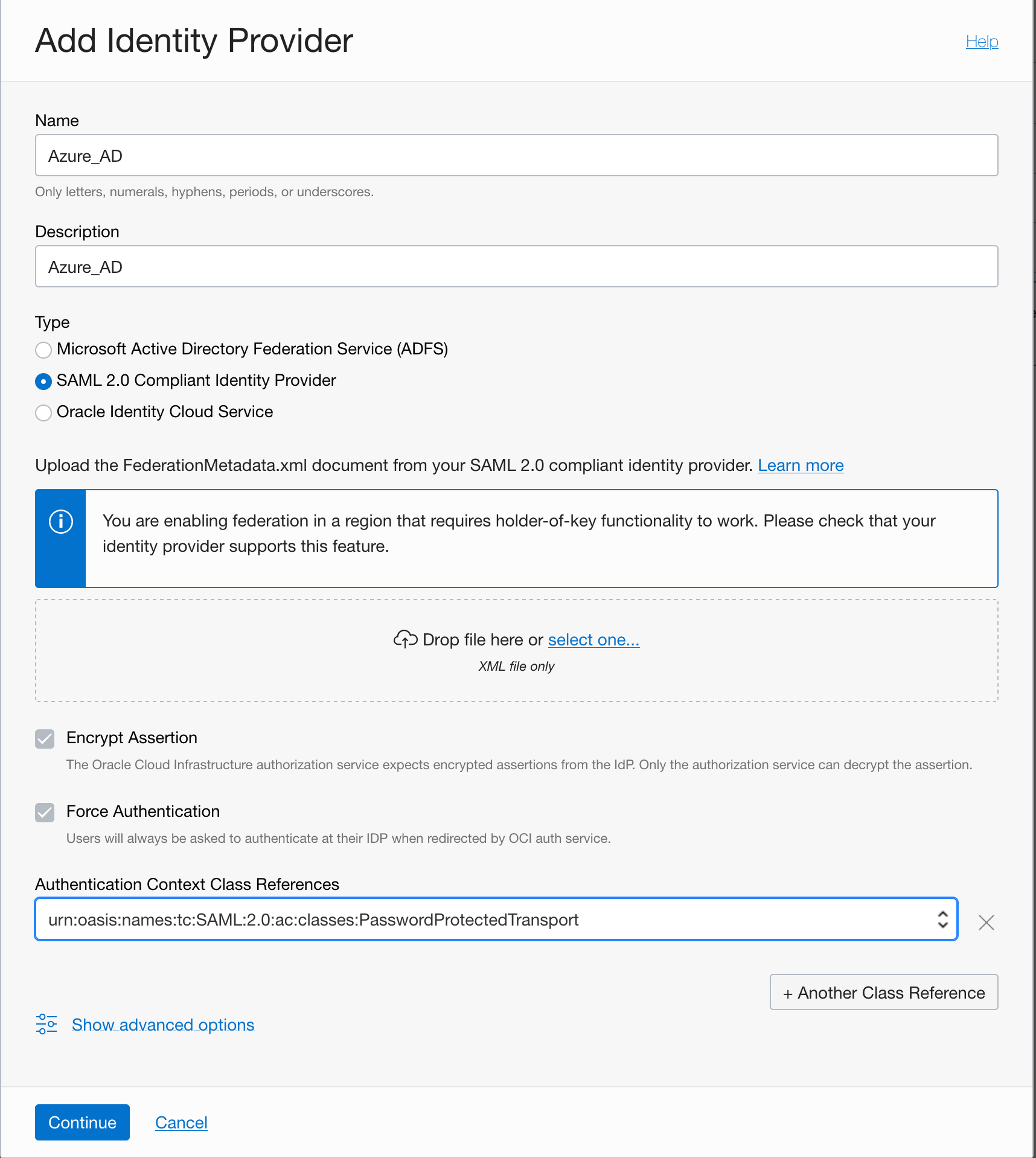
- From the OCI Federation page in the OCI Console under Identity and Security, click Add Identity Provider. Fill in the name and description. For the type, select SAML 2.0 compliant IDP, and then upload the SAML XML doc from step 5 above. Figure 3
- *In Oracle Government Cloud, Encrypt Assertion is enabled by default, so enable token encryption in Azure. Copy the x509 “encryption” certificate, shown in Figure 1, from the OCI metadata SAML document (the document in step 1) and format into .cer (with the BEGIN and END tags), as shown in Figure 2.
- Once a .cer file is created. In the Azure Application console, navigate to Token Encryption and select Import Certificate to upload the file. Once uploaded select Activate token encryption from the three-dot menu on the right.
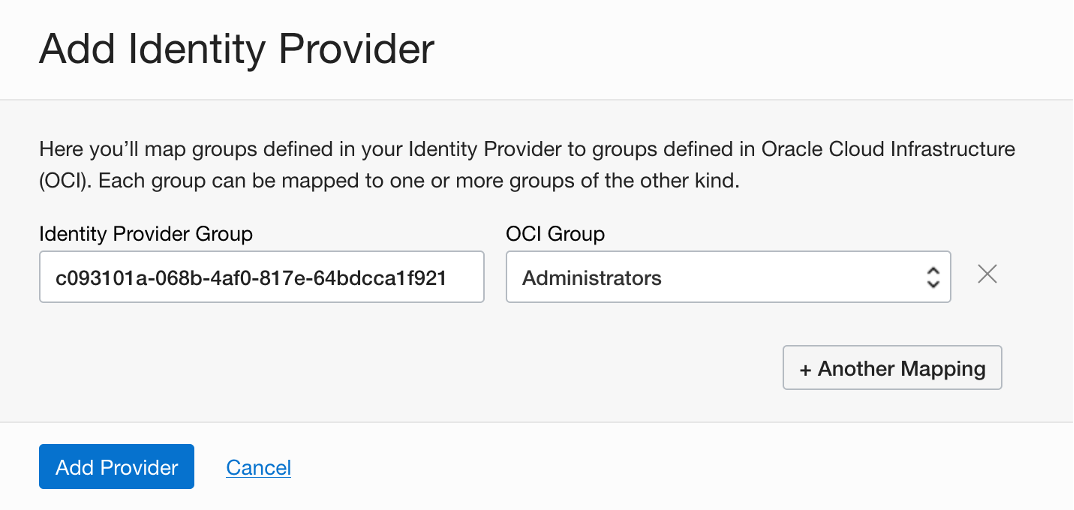
- Continuing Step 6 in the Oracle Cloud Console, click Add Identity Provider. Click Continue to map Azure groups to OCI and select Add Provider, as shown in Figure 3. For group mapping, add the group-id, such as c093101a-068b-4af0-817e-64bdcca1f921, to the OCI group, such as Administrators, as shown Figure 4.
- When these steps are complete, sign into the Oracle Cloud Console with the newly created Azure idP and use the user ID and password of the Azure AD user.


Conclusion
OCI US Government Cloud has achieved FedRAMP High JAB P-ATO accreditation, as have all the OCI and platform-as-a-service (PaaS) services generally available in those regions. OCI provides a secure platform to host service and workloads that serve the US Government, whether you’re considering cloud computing to reduce costs or improve performance. Oracle has a dedicated team and established resources ready to support your migration and help you achieve your cloud migration goals.
For more information, see the following resources:
