Oracle Cloud Infrastructure (OCI) has recently released two additions to the OCI Network Load Balancer service in commercial regions globally: a DNS health check and support for backends in some remote networks. This new functionality significantly expands the utility of our NLB into a specific and commonly requested use case: the load balancing and fault tolerant handling of DNS traffic to more than one DNS server.
Utilizing this new Network Load Balancer functionality, you can compose domain name system (DNS) architectures that more accurately detect and handle DNS server failures. You can now also place the DNS servers in those architectures flexibly within OCI or in your on-premises networks. You can apply these benefits to architectures for public and private DNS resolution.
Setting up the DNS health check
Network load balancers utilize a health check policy to determine if a backend server is healthy. The new DNS Health Check is exposed by selecting DNS as the health check protocol.

For details on these fields, see the documentation, but let’s look at some specific items. The query name is the DNS name that the health check requests from the backend server. Select the targeted query name to test the desired DNS functionality of the backend server. For example, use a query name on the internet, such as oracle.com, if the backend DNS server provides internet recursion. Or use a query name for which the backend DNS server is authoritative to test just the server and not its use of DNS recursion or forwarding.
The new “Enable instant failover” option is required for the DNS health check policy. DNS uses the user datagram protocol (UDP) and can have extremely high numbers of requests and responses, so much so that a DNS client might need to reuse UDP source ports. This option ensures that, even if one request from a source IP and port is directed to a healthy backend server, if that server becomes unhealthy, subsequent requests from that same source IP and port are directed to another healthy server.
Enhanced use cases
You can generally use this new Network Load Balancer functionality in two scenarios. The first scenario uses the new DNS health check to improve local load balancing of DNS traffic. This scenario is common when a customer is operating multiple self-managed DNS servers inside OCI and wants those servers presented through a single IP address. Here, DNS clients or other DNS servers would direct queries to the network load balancer’s IP address.
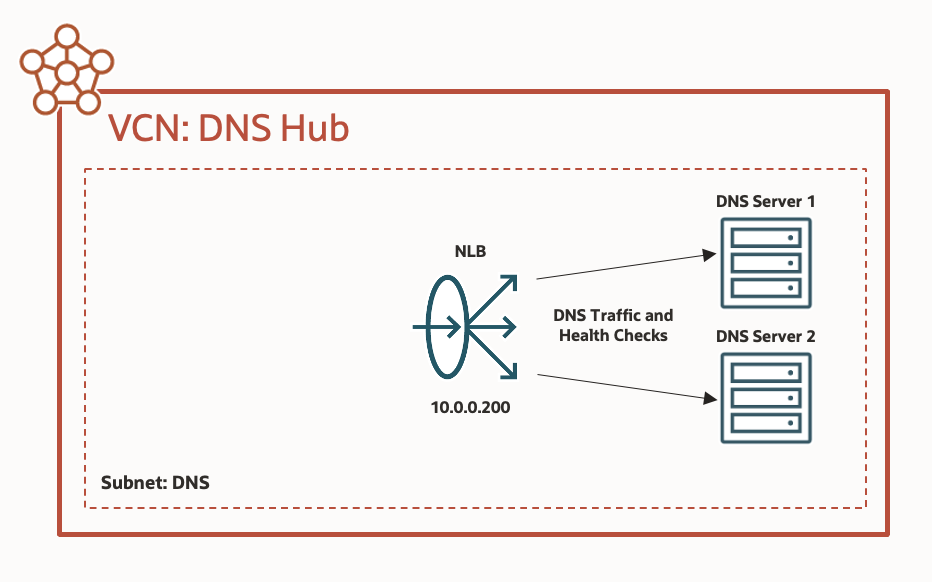
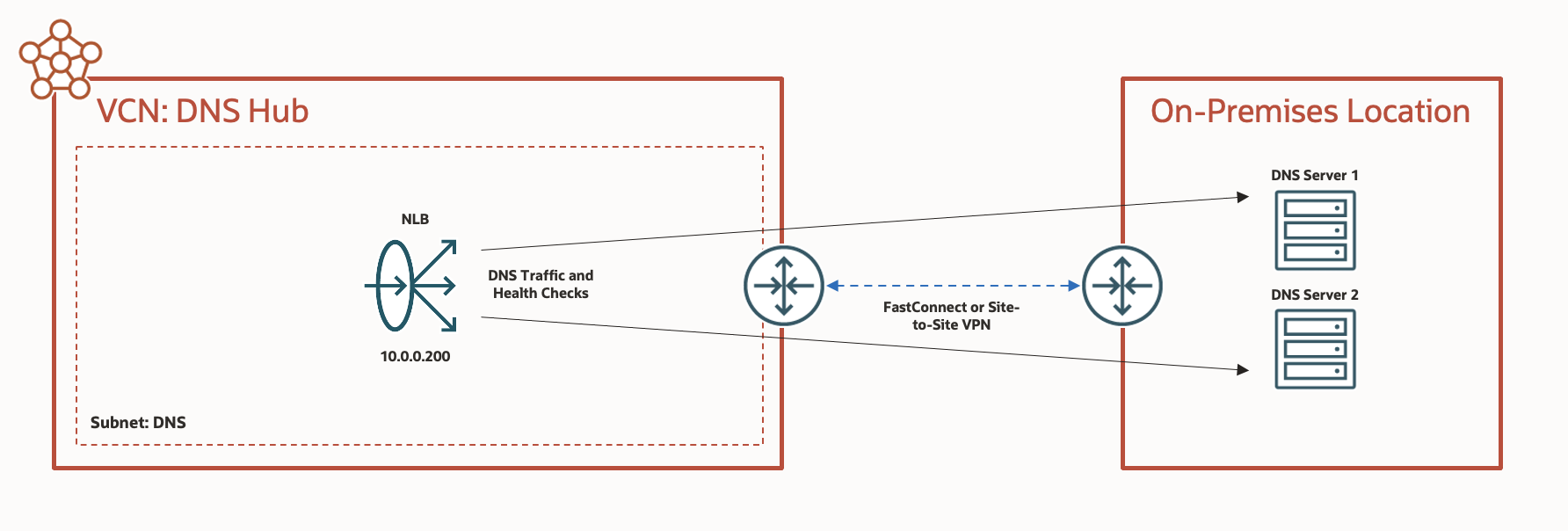
The second DNS architecture to benefit from this new functionality—specifically support for on-premises backends and DNS health checking—uses a network load balancer in OCI to load balance and forward traffic in a highly available fashion towards servers in your on-premises location. This approach facilitates DNS resolution of internal, on-premises DNS names, often in support of Microsoft Active Directory.
Integrating with OCI Private DNS
This new functionality is a particularly useful addition to the above architectures when using OCI Private DNS in combination with customer-managed DNS servers. OCI Private DNS supports the conditional forwarding of DNS requests to another DNS server. This use case is common when forwarding DNS requests to another virtual cloud network (VCN), potentially in another OCI region, or forwarding DNS requests to customer-managed servers in OCI or on-premises.
In this scenario, the conditional forwarding rules are configured to send traffic to a network load balancer. That network load balancer has two or more DNS servers configured as backends and uses the new DNS-aware health check. OCI Private DNS forwarding rules specify the IP address of the network load balancer as the destination server IP address. This approach relies on the network load balancer, bolstered by the new DNS health check, to determine the health of the destination DNS servers and balance traffic accordingly.
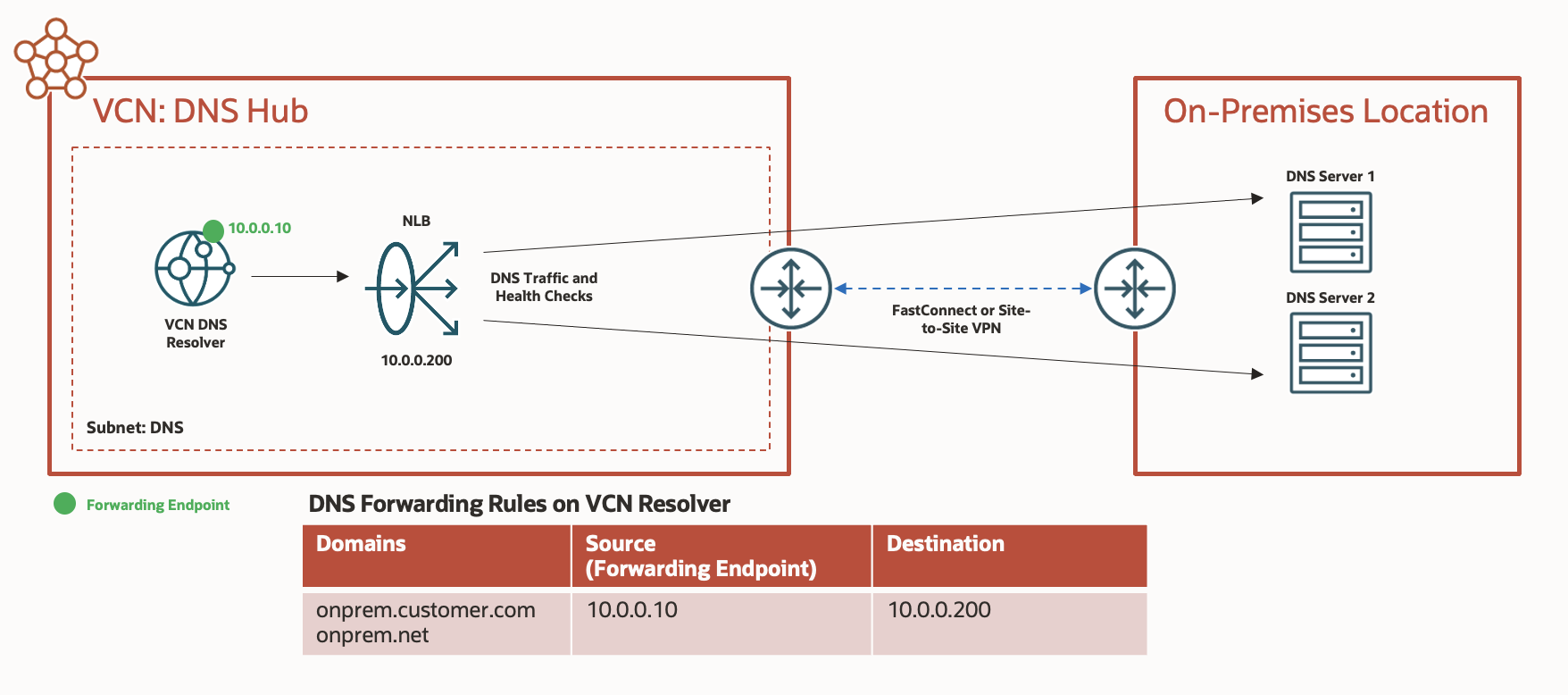
A common misconception is that the creation of two or more OCI Private DNS forwarding rules with identical conditions and different destination IPs adds fault tolerance. This setup doesn’t provide more fault tolerance because traffic is always sent to the first destination IP address. Instead, add a network load balancer to the network as described.
Implementation best practices
Consider the following items when constructing a DNS architecture with the OCI Network Load Balancer service:
- Utilize stateless security lists extensively: DNS uses many short-lived flows that can quickly consume space in the connection tracking table of resources in OCI, including a network load balancer. Configuring and using stateless security rules in any network security groups configured on the network load balancer and its backends and in security lists applied to their subnets is critical. Not doing so can cause packet loss during periods with a high rate of DNS requests and responses.
- Use UDP/TCP network load balancer listeners for DNS traffic: DNS requires UDP and TCP traffic to work correctly. DNS clients automatically use TCP if a DNS response is too large for a single UDP packet.
- Backend DNS servers must have identical DNS data and forwarding and recursion configurations: DNS queries arriving at the network load balancer are distributed to backends regardless of the contents of the queries. You can’t direct some names or types of queries to one backend and not another. For the fidelity of DNS responses and stability of the overall system, both servers must have identical DNS data and configurations so that a given query produces the same response regardless of which backend services the request.
Conclusion
The release of this new Network Load Balancer functionality addresses a common request from customers and fortifies key use cases with DNS. If you have Network Load Balancer deployments today for DNS use cases, we recommend that you review them with our new DNS health check and the demonstrated best practices in mind. For more information, see our documentation.
