Organizations that use Kerberos and Lightweight Directory Access Protocol (LDAP) for identity management often want to integrate their storage systems for secure centralized authentication and authorization. OCI File Storage Service (FSS) can be integrated with Kerberos and LDAP to secure your FSS-based NFS shares. You can enable this in the OCI Console or by using OCI CLI, API, SDK or Terraform at no additional cost.
This blog post introduces Kerberos and LDAP integration with FSS, providing an overview of the features and their general configuration requirements. This blog post will be followed by two separate parts, one for Windows Active Directory environments and the other for Linux environments.
Benefits of Kerberos and LDAP integration with OCI File Storage
You get the following benefits with Kerberos and LDAP integration:
- Centralized Management – Use your Windows Active Directory or Linux based Kerberos/LDAP identity management system to organize users and enable tailored access rights.
- Address security compliance requirements with following modes of operations
- krb5 – Kerberos authentication/authorization.
- krb5i – Integrity to protect against man-in-the-middle attacks and unauthorized modification.
- krb5p – Privacy or confidentiality to prevent eavesdropping (in-transit encryption).
- Scale Users with more groups – increase the maximum number of secondary Unix groups FSS supports for authorization to 256 (from 16).
- Windows Active Directory integration – Access FSS NFS shares from Active Directory joined Windows workstations and have Unix permissions for Active Directory Users (based on user, group and others).
Using Kerberos and LDAP with FSS
You can enable Kerberos access to FSS with an Active Directory or Linux based Kerberos Key Distribution Center (KDC) with RFC2307 enabled LDAP directory. In Linux environments, you can also use an opensource identity management system such as FreeIPA or a custom built solution based on openLDAP server and MIT Kerberos KDC. The following figure illustrates integration of FSS with Linux based KDC and Oracle Directory Server for identity management. The integration provides:
- Secure communication with users and KDC server.
- Secure communication with a Kerberos-enabled FSS exports – data integrity and in-transit encryption.
- Communication with customer-managed DNS service.
- Communication with customer-managed LDAP service via encrypted LDAPS channel.
- Data encrypted at rest in File Storage.
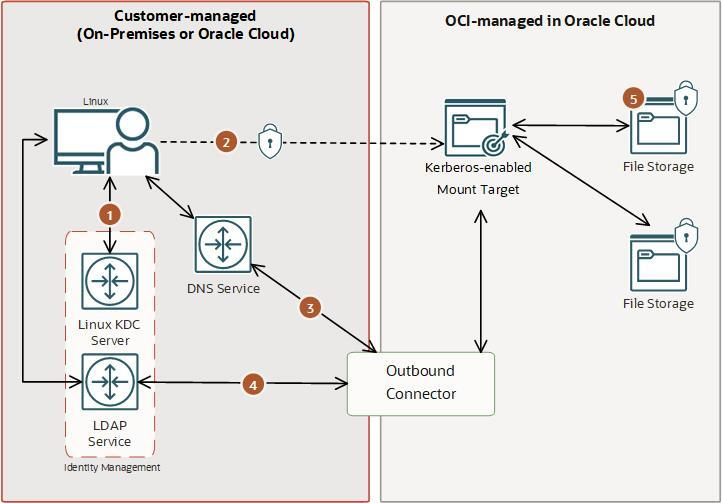
The above scenario also applies if you have a Windows Active Directory environment. All users and groups using FSS require Unix attributes (RFC2307 attributes) in the LDAP directory. You can also use Kerberos exports along with Unix style authentication for the same file system. The Kerberos and LDAP feature is integrated with OCI Logging and Metrics to optimize and provide transparency to your secure file sharing environment with FSS.
Get Started with Kerberos and LDAP
This section assumes that you already have your own infrastructure with KDC, LDAP and DNS. The following are the steps required prior to configuring Kerberos and LDAP on Mount target(MT)
- Obtain fully qualified domain name (fqdn) of LDAP server, a bind user and password to LDAP server, and search base for users and groups.
- Add mount target’s fqdn to DNS for both forward and reverse lookup.
- Join the mount target to KDC offline.
- Add MT in to KDC database and assign nfs/<MT fqdn>@<REALM> principal to it.
- Extract the keytab with needed ciphers from KDC and convert the file to a base64 encoded string.
- Configure OCI Vault secrets for LDAP bind password and keytab. Create password secret as plain text and keytab as base64 encoded string.
- Configure OCI IAM policies for MTs to access the secrets.
Create Outbound Connector for LDAP
An outbound connector is a resource that holds the configuration to connect to an LDAP server and perform queries. One outbound connector can be attached to multiple mount targets. One mount target can have up to two outbound connectors for seamless operations during LDAP server password rotations or changing LDAP endpoints.
In the Oracle Cloud Console, select File Storage. Select Outbound Connectors. Click Create and enter details collected from the steps above.
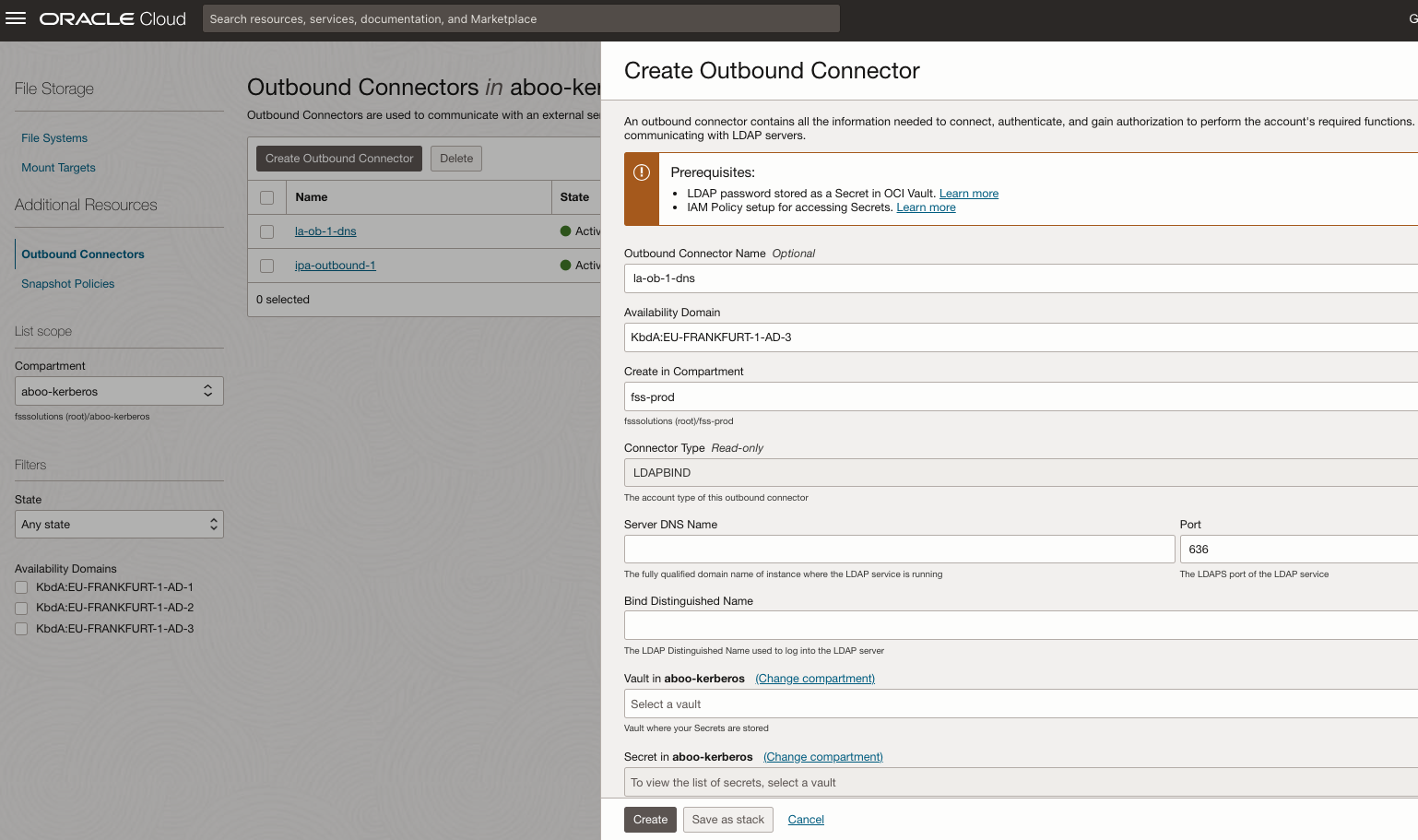
LDAP Configuration
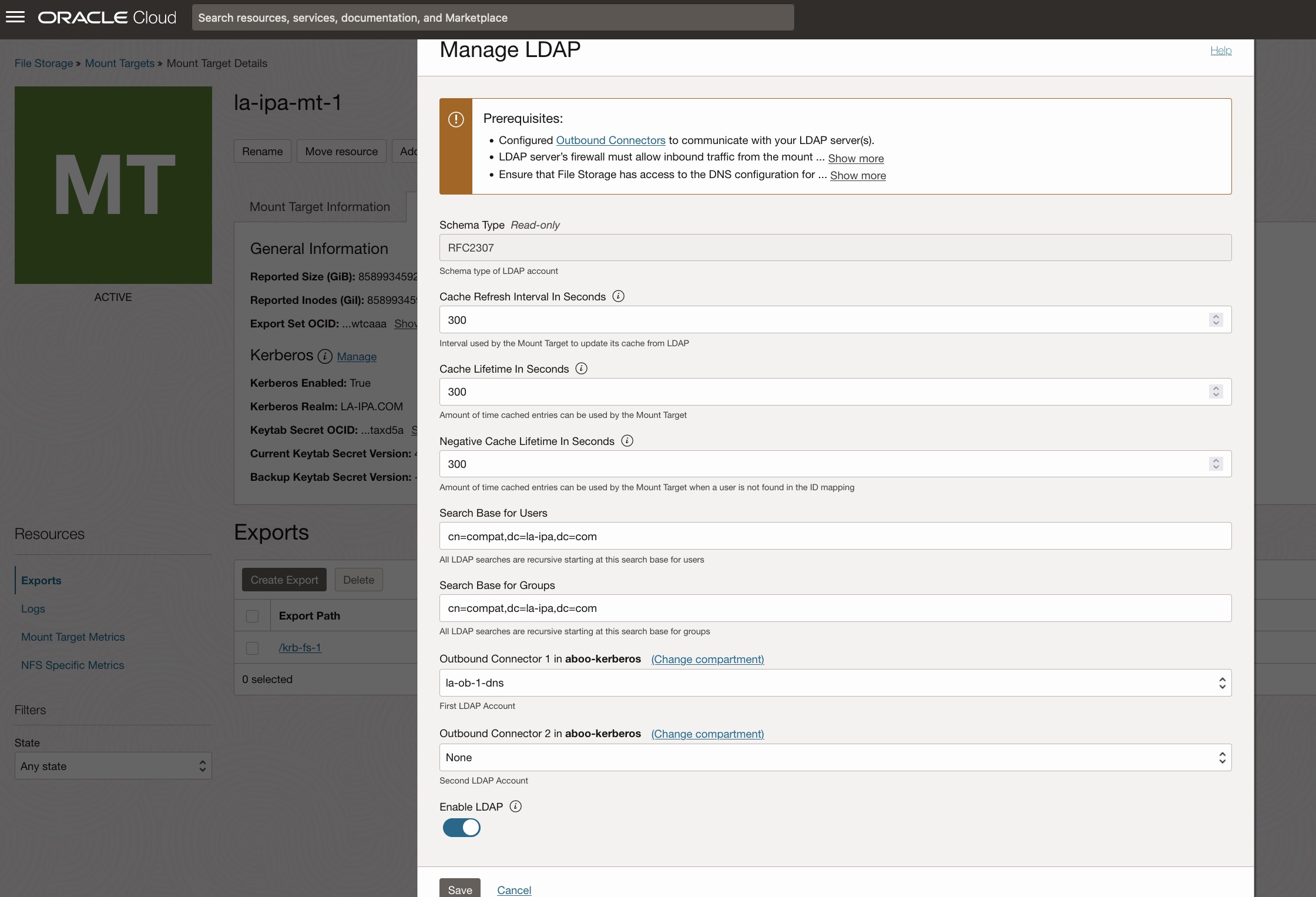
Attach the outbound connector to the mount target. From the Mount Target Details page, in NFS tab, click Manage under LDAP.
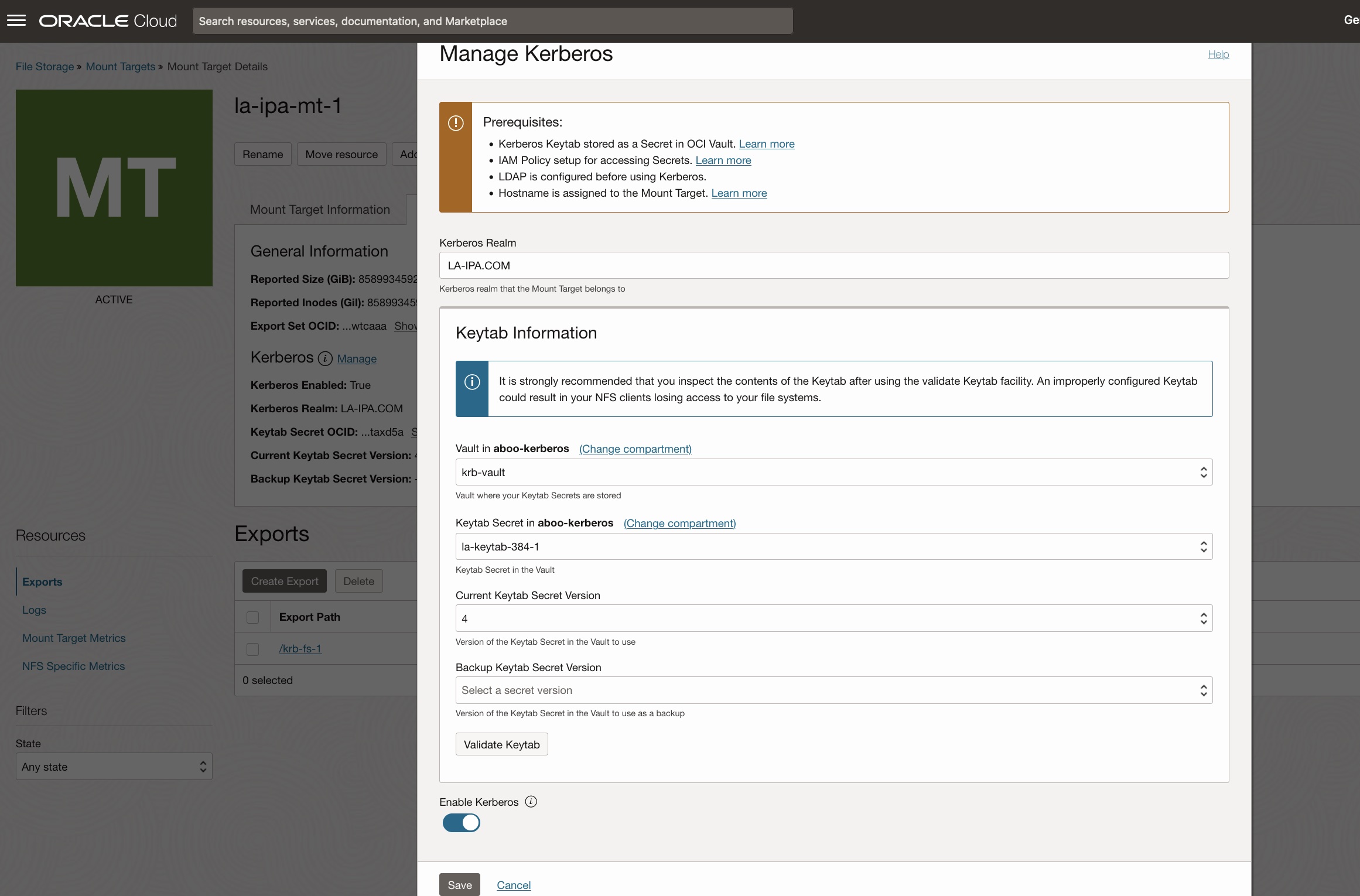
Kerberos Configuration
In OCI Console, from File Storage, select mount target to be configured. From the Mount Target Details page, in NFS tab, click Manage under Kerberos.
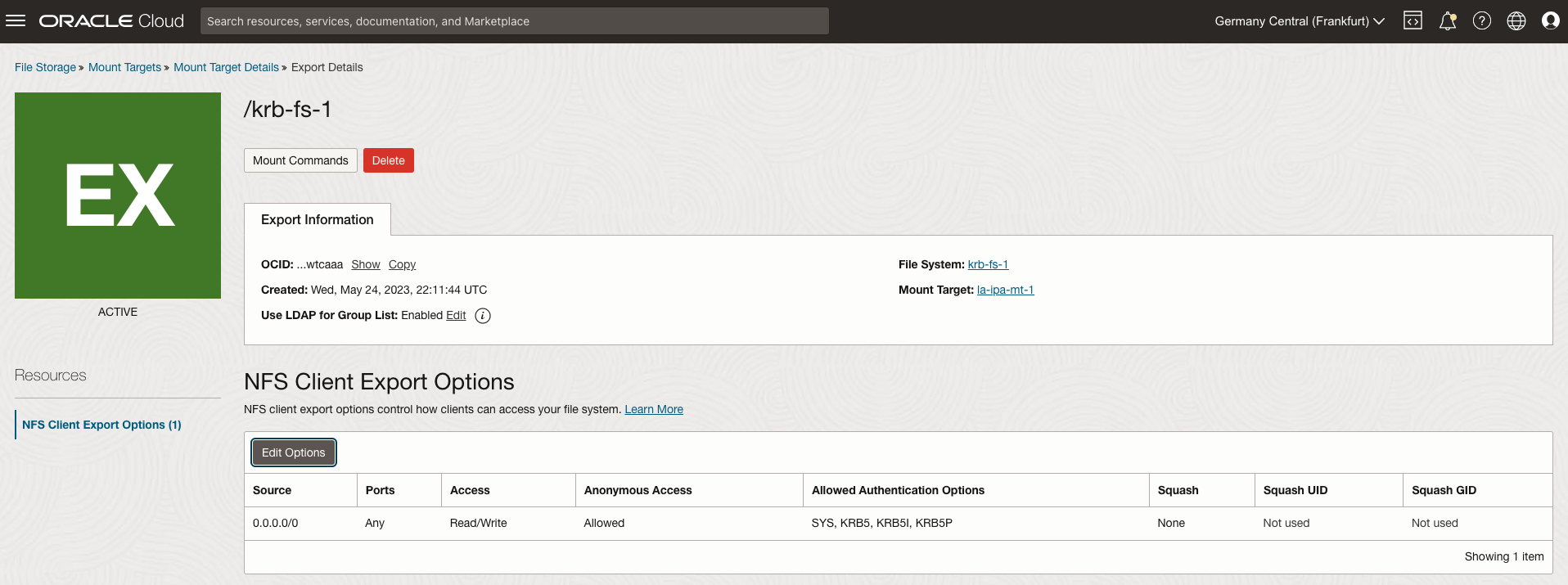
Export Configuration
From the Export Details page, enable LDAP by clicking Edit button next to Use LDAP for Group List. Then enable the required access modes (KRB5, KRB5I and KRB5P) for Kerberos by editing the export options.
Mount the export from NFS Client
[root@la-freeipa-client-1 opc]# mount -v -o sec=krb5p la-freeipa-mt-1.la-ipa.com:/krb-fs-1 /mnt
...
mount.nfs: trying text-based options 'sec=krb5p,addr=10.9.1.198'
mount.nfs: prog 100003, trying vers=3, prot=6
mount.nfs: trying 10.9.1.198 prog 100003 vers 3 prot TCP port 2049
mount.nfs: prog 100005, trying vers=3, prot=17
mount.nfs: trying 10.9.1.198 prog 100005 vers 3 prot UDP port 2048
[root@la-freeipa-client-1 opc]# grep " nfs" /proc/mounts
la-freeipa-mt-1.la-ipa.com:/krb-fs-1 /mnt nfs rw,relatime,vers=3,rsize=262144,wsize=262144,namlen=255,hard,proto=tcp,timeo=600,retrans=2,sec=krb5p,mountaddr=10.9.1.198,mountvers=3,mountport=2048,mountproto=udp,local_lock=none,addr=10.9.1.198 0 0
[root@la-freeipa-client-1 opc]# df -kh /mnt
Filesystem Size Used Avail Use% Mounted on
la-freeipa-mt-1.la-ipa.com:/krb-fs-1 8.0E 0 8.0E 0% /mnt
Try it for yourself
We want you to experience Kerberos and LDAP integration and all the enterprise-grade capabilities that Oracle Cloud Infrastructure File Storage offers.
Get started with the service overview documentation and video series. Provide your feedback on how we can continue to improve. More feature updates are on the horizon for our cloud storage platform.

