As organizations embrace cloud technologies and construct hybrid multicloud architectures, they encounter both opportunities and challenges. The convergence of functional and nonfunctional business needs introduces complexity, while heightened security risks and stringent regulatory requirements demand robust solutions. Enterprises recognize that security is no longer an afterthought. It must be designed from the outset. Safeguarding sensitive data and ensuring compliance are paramount.
In this dynamic landscape, businesses seek architecture options that seamlessly support the adoption of the newer technologies. Cloud adoption, containerization, and microservices architectures offer immense potential. Drawing from its extensive innovations in identity and access management (IAM), Oracle has crafted solutions that align with these business priorities.
Traditional IAM deployment
Figure 1 shows the three key components of Oracle’s enterprise IAM suite, which have traditionally been deployed on-premises: Oracle Directory Services, Oracle Access Management, and Oracle Identity Governance.
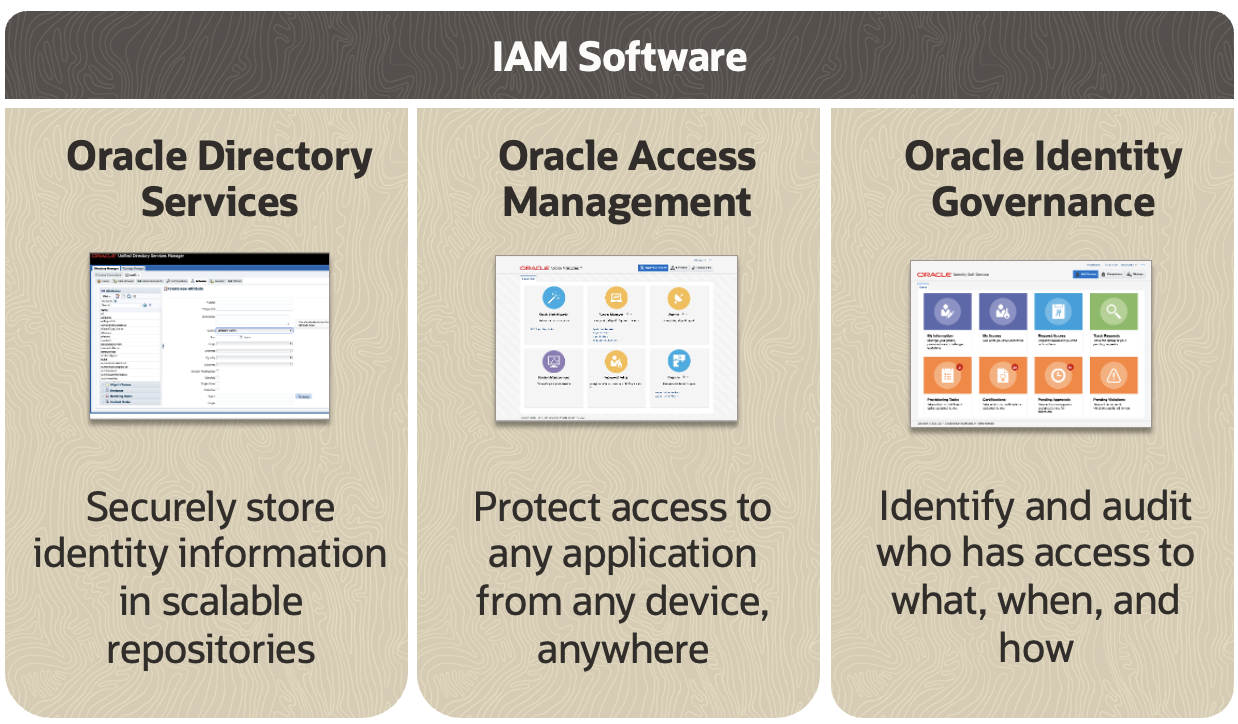
Oracle Directory Services are a set of identity management products that provide centralized management of user and application identities, authentication, and authorization. They provide a centralized repository for storing and managing user identities, credentials, and attributes. Oracle Unified Directory is the directory service that provides high-performance, highly available, and secure storage for identities and access information.
Oracle Access Management is a web access management solution that provides authentication and authorization for web-based applications. It enables organizations to secure their web applications and resources by enforcing access control policies that determine who can access what resources and under what conditions.
Oracle Identity Governance provides a centralized platform for identity governance and administration. Identity Governance automates and streamlines the process of managing identities, including the creation, modification, and removal of user accounts, and the assignment and revocation of access privileges.
IAM modernization
Oracle’s approach encompasses the technological and strategic modernization of its existing product portfolio and introduces new cloud native services that support its customers’ business objectives.
Figure 2 describes the following paths to modernizing identity and access management:
- Move and improve: Also known as “lift and shift”, this approach helps enable technology modernization by moving your IAM workloads to the cloud. In this approach, Oracle IAM software is migrated to Oracle Cloud Infrastructure (OCI) and deployed on cloud compute, enabling customers to take advantage of cloud benefits, including scalability and manageability. This method also makes it easier to quickly integrate these security technologies with the enterprise applications running on OCI.
- Containerization: Many of our customers have been containerizing their workloads, driven by benefits including portability, scalability, and efficiency. Oracle has adopted the developer operations (DevOps) delivery models by using containers for Docker and Kubernetes to modernize the lifecycle management of Oracle IAM products. This approach simplifies the deployment and maintenance of Oracle IAM products across various deployments in physical data centers, private cloud, or public cloud.
- IAM microservices: Purpose-built microservices offer independent and focused functionality with the added benefits of scalability and resilience. Oracle’s IAM solution portfolio includes microservices, such as Oracle Identity Role Intelligence, Oracle Advanced Authentication, Oracle RADIUS Agent, and Oracle Adaptive Risk Management.
- Cloud native software as a service (SaaS): Oracle’s cloud native IAM and Identity Governance and Administration (IGA) services are modern, redesigned solutions that use artificial intelligence and machine learning (ML) to provide intelligent and intuitive analytics and automations.
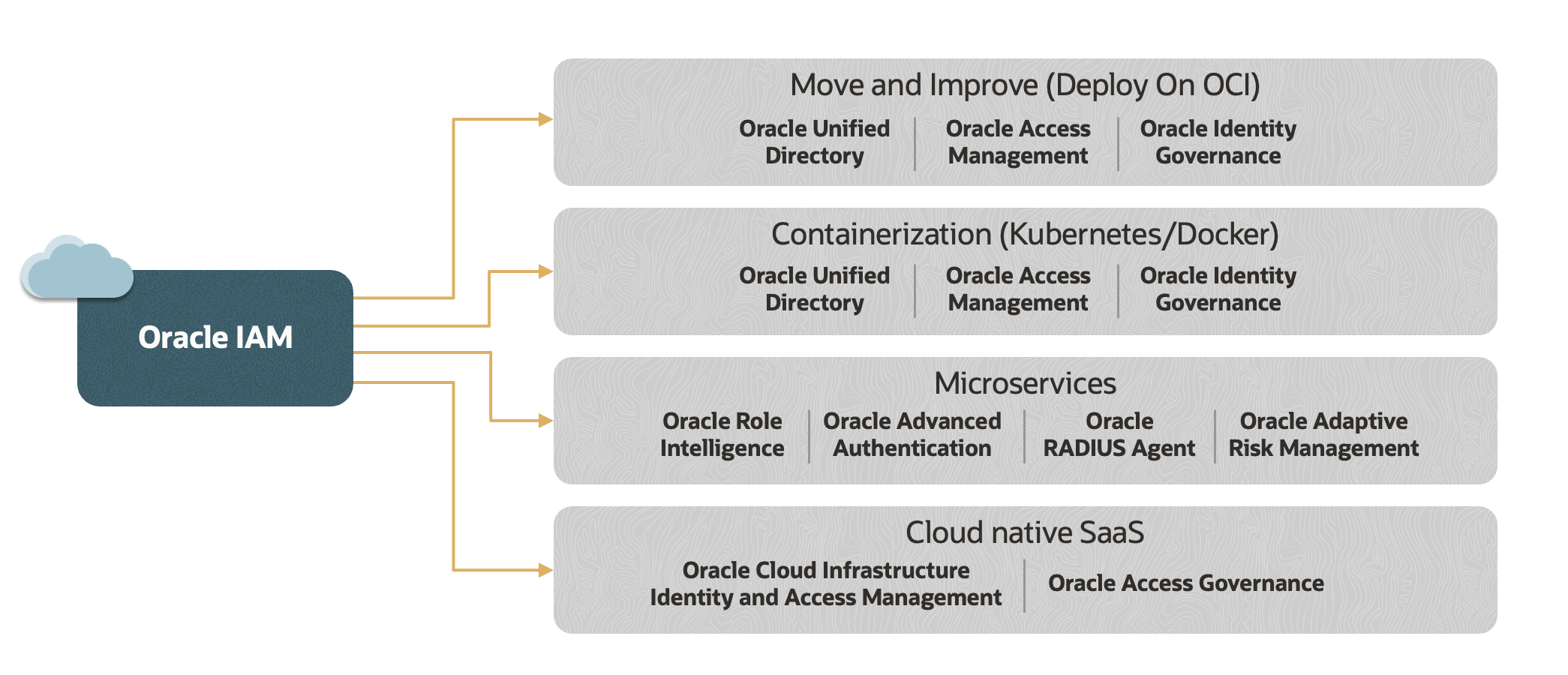
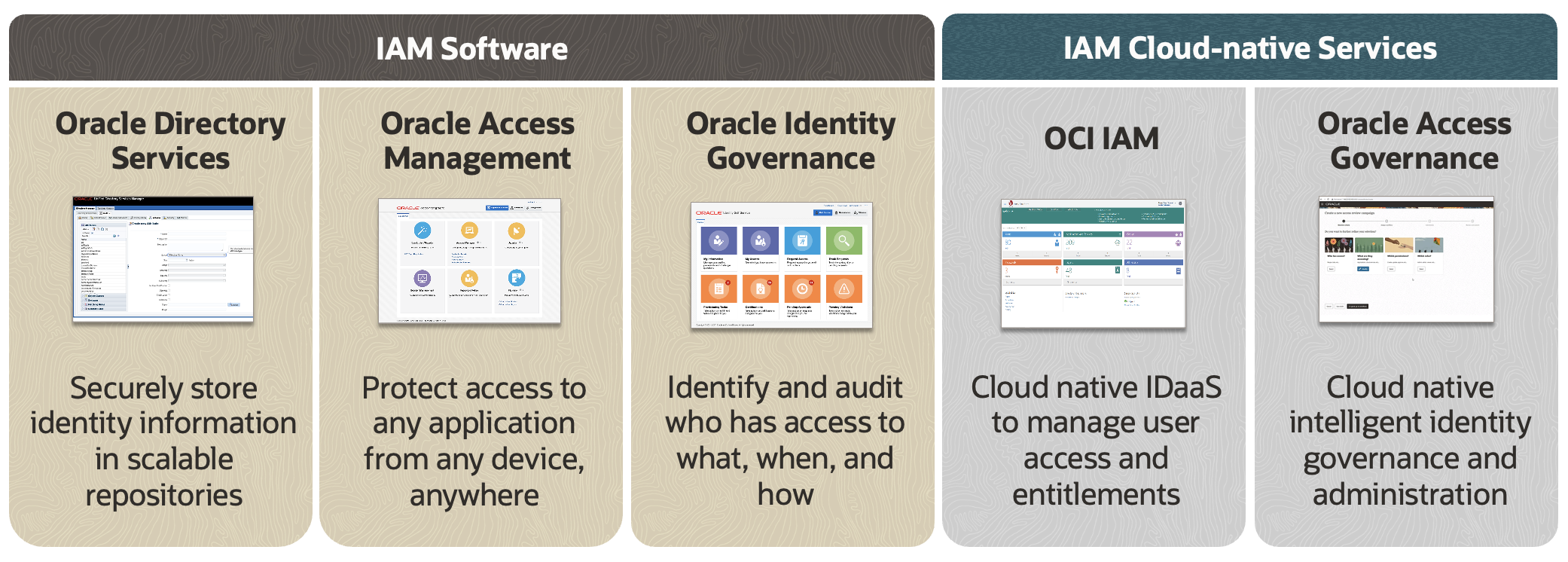
Figure 3 depicts the complete portfolio of Oracle IAM solutions, including IAM software and cloud native SaaS. Oracle customers can enjoy flexibility in the path they may choose to achieve an ideal target architecture based on their current architecture, and business drivers. Oracle’s cloud native IAM SaaS products include OCI IAM and Oracle Access Governance. OCI IAM encompasses a suite of identity and access management features, such as authentication, single sign-on (SSO), and identity lifecycle management. Oracle Access Governance is a cloud native IGA solution that provides insights-based access reviews, analytics, and identity intelligence capabilities.
Conclusion
As customers modernize their Oracle IAM solution to address evolving threat landscapes and increased compliance requirements, you can expect flexible options and prescriptive guidance from Oracle. Oracle has released training content to help you embark on your modernization journeys with Oracle. These courses are available as part of the Oracle Cloud Infrastructure Learning subscription, which is currently free to customers and partners.
Learn more about each course and participate:
Journey 1: Deploying Oracle Identity and Access Management software as virtual machines (VMs) in OCI
- Create the necessary OCI artifacts like networks, security lists, and virtual machines (VMs) for an Oracle IAM installation in OCI
- Perform installations of Oracle IAM Software on OCI resources
- Migrate existing on-premises deployments into OCI
- Take advantage of the many maintenance and monitoring features to better manage the stack within OCI
Journey 2: Deploying Containerized Oracle Identity and Access Management on OCI
- Use Oracle IAM container images to quickly deploy Oracle Identity Governance
- Run Oracle Access Management and Oracle Unified Directory 12c in Kubernetes environments
- Use Oracle IAM containers to move complex workloads to any public or private cloud vendor, significantly reducing operational cost and modernizing security infrastructure
- Enable DevSecOps with maximized velocity
Journey 3: Deploying Oracle Identity and Access Management Microservices
- Learn the key features of Oracle IAM microservices
- Understand the architecture
- Review the use cases for Oracle IAM microservices
- Learn how to install and configure
Journey 4: Introduction to Oracle Access Governance
- Basics of identity governance and administration
- Oracle Access Governance basics and architecture
- Set up and configure Oracle Access Governance
- Identity orchestration concepts
- Integrate with authoritative and nonauthoritative systems
- Create access controls based on attributes, policies, and roles: ABAC, PBAC, and RBAC
- Ensure governance and compliance with certification campaigns and access/policy reviews
- Obtain identity intelligence using prescriptive analytics and insights
