In a previous article, where we discussed the use of external identities with Oracle Cloud Infrastructure (OCI), we recommended the use of OCI Identity and Access Management (IAM) as the single point of entry into OCI, rather than using point integrations.
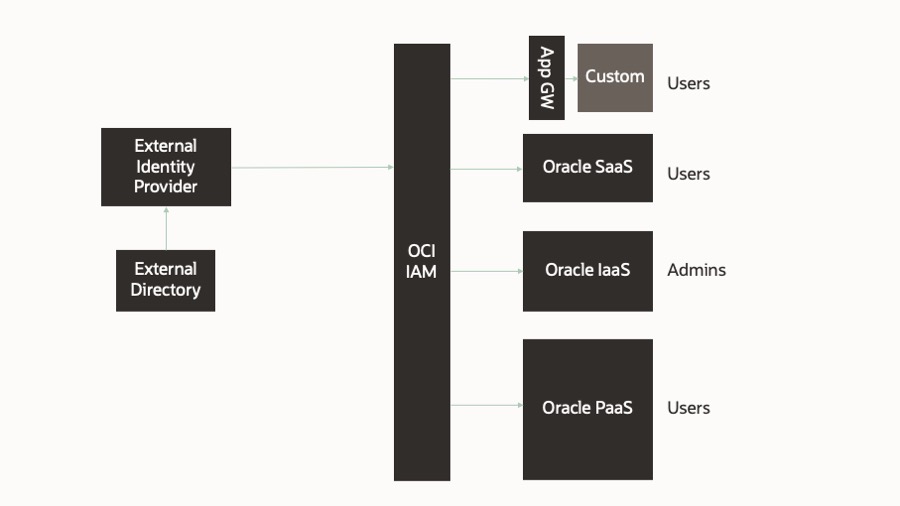
Multiple environments for IaaS and PaaS
In this post, we expand on that recommendation to discuss how you approach the architecture when you have multiple environments. For example, when you subscribe to OCI applications, such as Enterprise Resource Planning (ERP), you provision two environments by default. One is the production environment, and the second is the staging environment. Many customers also subscribe to multiple other environments for development, testing, and so on. Depending on how and when you subscribe to different OCI services, you might also have multiple OCI tenancies. The following example architecture explains our approach and recommendation.

In this example, we have one OCI tenancy containing five instances of Oracle Fusion SaaS applications. Another separate OCI tenancy housing the platform- and infrastructure-as-a-service (PaaS and IaaS) workloads across all the environments. Finally, we have an external identity provider.
When thinking about the correct solution approach for identity, consider the following factors:
- Isolation: As you make changes to your environments, being able to make changes in one environment without impacting other environments is important.
- Administrative control: Enabling the ability for different administrators and administrative groups to have control over different environments.
- Security compliance: Designing a solution that can help meet regulatory compliance, such as preventing unauthorised access from development to production.
The following recommended architecture helps address each of these considerations:
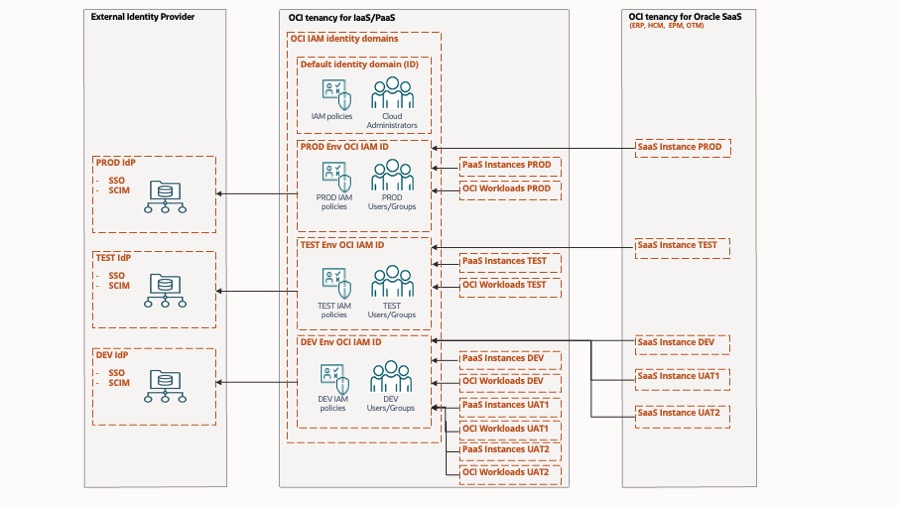
The application identities have been separated into three separate OCI IAM identity domains: Production (PROD), testing (TEST), and development (DEV). These domains are added to the default identity domain provided with all new tenancies. All the production software-as-a-service (SaaS), PaaS, and IaaS resources are integrated with the PROD identity domain. All the test SaaS, PaaS, and IaaS resources are integrated with the TEST identity domain, and all other nonproduction SaaS, PaaS, and IaaS environments are integrated with the DEV identity domain. Each of the three identity domains integrates with its respective identity environment in the external identity provider.
The default identity domain is reserved for OCI tenancy administration. OCI administrators authenticate to the default domain to manage the tenancy’s configuration and assign administrators for OCI resources, such as compute, storage, networking, and security. Don’t add application users to the default domain, and similarly, other than the identity administrator for a domain, don’t add OCI administrative users to the PROD, TEST, and DEV domains. These assignments create a clear separation between OCI administrative users and application users and a clear separation between application users across the different environments.
If your tenancy has been migrated from Oracle Identity Cloud Service (IDCS) to OCI IAM identity domains, in addition to the default domain, you get an OracleIdentityCloudService domain. In this case, check Guest Blog: Five considerations for OCI IAM in IDCS-migrated tenancies, which covers some considerations for these environments.
Conclusion
Edge cases that require more design considerations and possible tweaking to this architecture always exist. However, this blueprint acts as our starting point when talking to customers about their identity management strategy for OCI, and now it can be yours too.
We hope you found this information useful. You can read more about Oracle Cloud Infrastructure, or sign-up for a free trial. Furthermore, you can read more about OCI IAM here.
