This is a guest blog written by Manas Chowdhury from Accuknox.
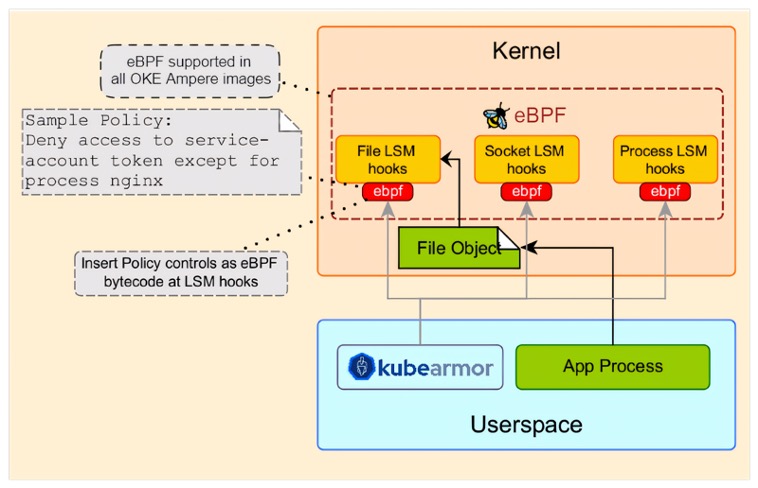
KubeArmor is a cloud native runtime security enforcement system that models the application behavior of pods, containers, nodes, and virtual machines (VMs) at the system level, based on process execution, file access, and networking operations. It then recommends allowlisted policies to achieve a zero-trust architecture by denying unknown request execution before they run. It uses Linux security modules (LSMs), such as AppArmor, SELinux, or BPF-LSM, to enforce user-specified policies. KubeArmor generates rich alerts and telemetry events with container, pod and namespace identities using Extended Berkeley Packet Filter (eBPF).
The AccuKnox platform secures Kubernetes environments and supports Oracle Cloud Infrastructure (OCI) Ampere A1 Compute. AccuKnox Zero Trust CNAPP solution strengthens the Kubernetes ecosystem and provides deeper observability through intelligent mechanisms. It can help you identify risks, detect anomalies, and respond to invasive threats.
This blog post describes our tailored support for OCI Ampere A1 Compute in detail. Let’s see possible scenarios for adopters to use our security solution, KubeArmor on Oracle.
With their cost-efficiency and scalability, Ampere-based compute platforms are gaining prominence, offering users an opportunity to optimize their deployment costs, while maintaining or even exceeding performance levels compared to traditional x86 platforms. The OCI Ampere A1 compute infrastructure seamlessly integrates with Kubernetes-based orchestration, simplifying deployment and management tasks. AccuKnox further complements this synergy by providing robust security foundations, particularly for workloads deployed on Ampere A1 compute-based Oracle Container Engine for Kubernetes (OKE).
OCI Ampere A1 shapes and security strategies with AccuKnox
OCI Ampere A1 shapes are a game-changer when it comes to cost-effective cloud infrastructure. Utilizing OCI’s Ampere A1 shapes on OKE can reduce expenses without compromising performance. However, security remains a top concern in any cloud environment. AccuKnox steps in to address this concern by offering advanced security strategies designed to be tailored for A1 shapes on OKE.
AccuKnox’s strength lies in its ability to provide enhanced observability and auditing capabilities, both of which are crucial for addressing runtime security concerns in A1-based OKE deployments. This two-pronged approach not only grants deep insights into the Kubernetes environment but also helps to identify vulnerabilities within the security posture.
AccuKnox harnesses the power of eBPF for comprehensive observability. This technology enables real-time monitoring and analysis of system activities, including process runs, sensitive asset access, network interactions, and security-sensitive system call activities. Organizations can use this technology to proactively detect security anomalies and runtime characteristics, allowing for swift response to potential threats.
KubeArmor-supported security features for OCI Ampere A1
Strengthening OKE with KubeArmor
OKE is a managed Kubernetes service that simplifies containerized application operations, offering scalability, reliability, and automation. Kubernetes infrastructure gets automatic updates, patching, and scaling, with resource releases.
The chosen distribution for OKE, Oracle Linux, is crucial for a stable and secure environment for enterprise applications. It’s supported by the Unbreakable Enterprise Kernel (UEK). KubeArmor is a robust security solution for Oracle Linux and UEK environments, designed to safeguard the integrity and security of workloads in Kubernetes clusters. Version 0.5 introduced integration with BPF-LSM for pod- and container-based policy enforcement. For more information, see the release announcement. Since then, it has enabled granular policy controls. It also builds on the security of Kubernetes pods hosted on OKE, limits system behavior, and restricts access to sensitive tokens. The policies within OKE can help prevent unauthorized modifications and shield critical certificates.
Observability and monitoring through eBPF
KubeArmor helps protect sensitive information, such as Kubernetes secrets and x509 certificates, within the container. You can specify policy rules in KubeArmor so that any attempts to update the root certificates in any of the certificate’s folders, including /etc/ssl/, /etc/pki/, or /usr/local/share/ca-certificates/, can be audited. It restricts binary processing in containers, providing real-time insights into system behavior, resource utilization, and application performance. It integrates with eBPF for pod and container-based policy enforcement, a new Linux Security Module introduced in kernels above 5.7. This enforcement allows KubeArmor to attach bpf-bytecode to LSM hooks with user-specified policy controls.
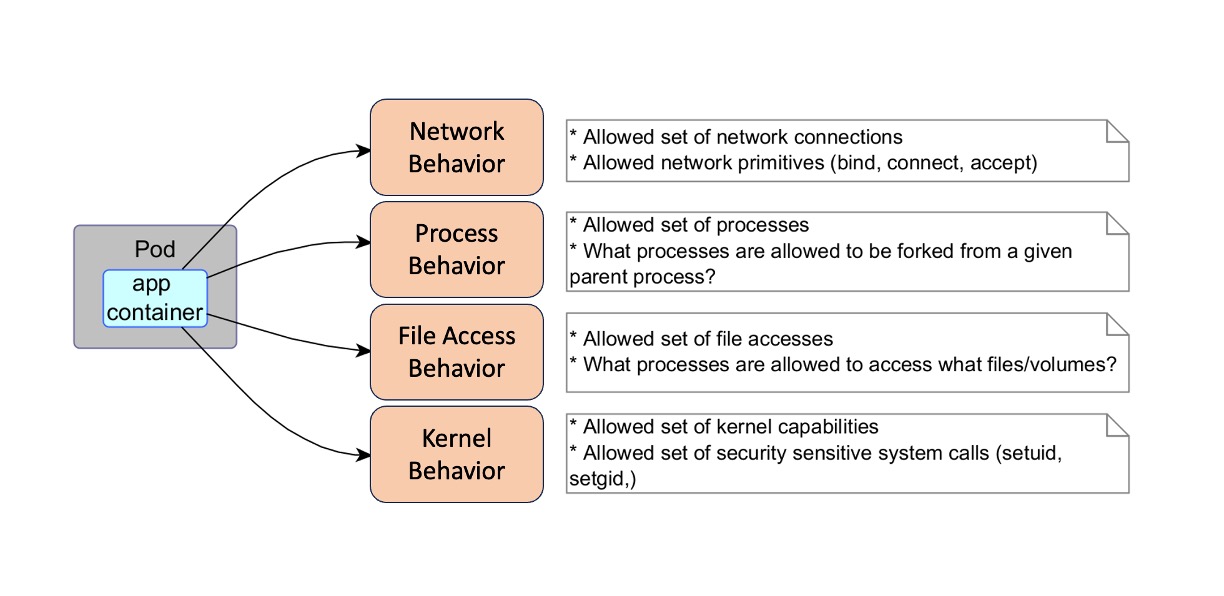
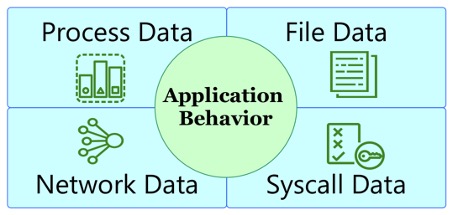
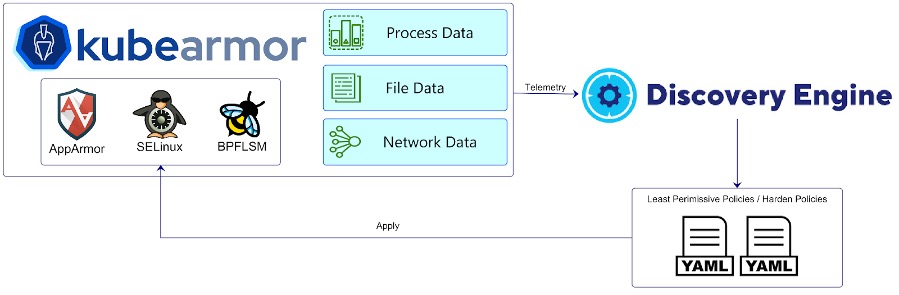
The following graphic shows the application behavior:
- Process data
- What are the processes running in the pods?
- What processes are running through which parent processes?
- File data: What are the file system accesses made by different processes?
- Network accesses:
- What are the ingress and egress connections from the pod?
- What server binds are done in the pod?
Network microsegmentation
Security is inherently linked to network segmentation, and AccuKnox is designed to deliver on this front. It allows isolating workloads, limiting lateral movement, and cutting the attack surface. KubeArmor tackles this issue in the following ways:
- Cluster-level isolation
- Network-level control
- IP-based segmentation
- Network security enforcement
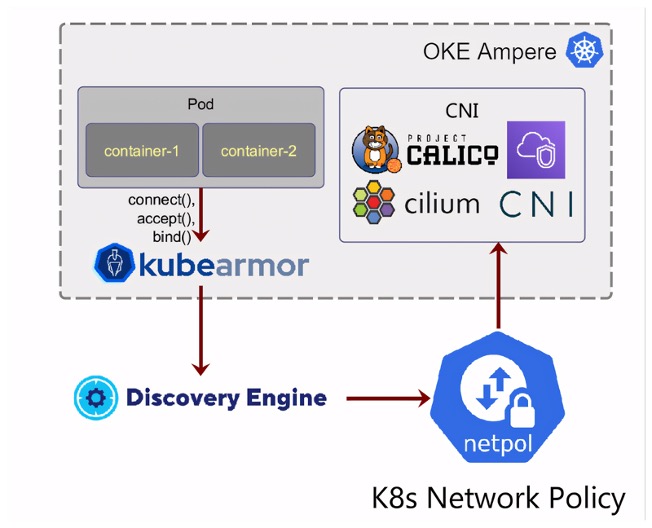
In the OKE environments powered by Ampere A1 shapes, KubeArmor seamlessly integrates with containers within pods. KubeArmor’s Discovery Engine uses Kubernetes network policies to facilitate the delivery of vital statistics from Cilium, Container Network Interface (CNI), and Project Calico. This integration enhances security measures, providing comprehensive insights and control within your OKE Ampere A1-based deployments.
Workload hardening through policy-based rules
KuebArmor includes hardening strategies based on industry-leading compliance and attack frameworks, such as CIS, MITRE, NIST-800-53, and STIGs. These policies help secure workloads and reduce attack surfaces by implementing block-based policies. These policies are automatically recommended, and you can develop them individually. In-line mitigation helps prevent policy infringement. Businesses can design and enforce tight policies that control application behavior and access rights by using audit-based rules, reducing the risk of illegal activities.
Automatic discovery of zero-trust security posture
Zero-trust policies with default audit behavior
The zero-trust least permissive policy allows NGINX to run in the pod and denies others. KubeArmor incorporates the attitude of zero trust, which is a driving principle in modern cybersecurity. The platform enforces audit behavior by default, meaning every action is rigorously logged and inspected, in accordance with the principles of zero trust. It allows declaring which actions are allowed and which are denied or audited. Security posture specifies what happens when operations not on the approved list are performed. By default, the security posture is audited and should be set to deny with the following command:
kubectl annotate ns default kubearmor -file-posture=block --overwrite
For other ready-to-use policy templates, see Policy Examples for Containers.
Conclusion
KubeArmor, a cloud native solution, supports OKE to secure pods and containers using eBPF for observability and auditing purposes. In Kubernetes, pods are processing units exposed to external entities, requiring a layer of defense to limit attackers’ ability to exploit vulnerabilities. KubeArmor uses Linux kernel primitives on the Unbreakable Enterprise Kernel (UEK) to harden pods, further fortifying the Kubernetes engine.
The AccuKnox platform offers security and observability in cybersecurity challenges, supporting Oracle on Ampere A1 Compute. Features include observability, network segmentation, workload hardening, and zero-trust policies. AccuKnox, Oracle Linux, and KubeArmor work together to create a fortified cloud native ecosystem.
AccuKnox’s collaboration with OCI on Ampere A1 and KubeArmor in OKE demonstrates proactive security measures. Oracle Cloud Infrastructure helps you confidently navigate cloud landscapes while prioritizing digital asset integrity and protection.
For more information, see the following resources:
- KubeArmor official documentation
- Oracle Container Engine for Kubernetes documentation
- Cloud Native Computing Foundation (CNCF) resources
- OCI Ampere A1 Compute
- Oracle Cloud Free Tier
- OCI Arm Accelerator