The Oracle Cloud Infrastructure (OCI) Key Management service (KMS) provides centralized control of encryption keys for data in OCI. KMS offers customer managed encryption through a diverse set of key management solutions, including Vault, which features the following options:
-
Virtual Vault: A cost-effective, multitenant service for managing keys.
-
Private Vault: A single-tenant service providing enhanced isolation and security.
We’re excited to announce the general availability of crossregion replication for Virtual Vault. Now, Virtual Vault and Private Vault both safeguard your applications against regional failures and help achieve higher availability through crossregion failover. Crossregion replication is supported for software and hardware-protected master encryption keys used for symmetric or asymmetric encryption. Vault maintains FIPS 140-2 Level 3 security during regional replication, and these keys never leave the hardware security modules (HSMs) in plaintext. Instead, they’re exported as encrypted binary objects and restored exclusively within Oracle-provided FIPS 140-2 Level 3 HSMs within your tenancy.
This release supports replication between any two regions. Keys are automatically and asynchronously copied from the source to the destination region. Although you can both manage keys—creating, deleting, and so on—and use them for encryption and decryption in the source region, you can use replicated keys in the destination region only for runtime encryption and decryption operations. As with all other OCI features, the steps taken to start and delete replication are logged in OCI Audit logs, which helps customers meet their compliance goals.
Crossregion replication for OCI Vault provides the following benefits:
-
Strengthened disaster recovery: Replicating keys across regions helps ensure data accessibility and recovery if regional disruptions occur.
-
Enhanced data protection: Maintaining redundant key copies safeguards against accidental loss or unauthorized access to help bolster overall security.
-
Compliance and data residency: For regulated industries or those with specific data residency requirements, replication helps you address your compliance objectives and adhere to relevant laws.
Crossregion replication’s RPO and RTO
Let’s define some terms before we describe the experience you get. Recovery time objective (RTO) is the maximum time your applications might be unavailable while recovering in the destination region. The recovery point objective (RPO) is the maximum amount of data you might lose on the source region. For our crossregion replication solution, the RTO is near zero in a steady state because every key you create in the source region is immediately replicated to the destination region and the delay is mostly from the milliseconds network latency between regions. Your application can fail over to the destination and access keys almost instantly. The RPO is also zero because we don’t confirm success in the primary region until your key is committed to persistent HSM storage, helping to ensure no data loss.
Enabling crossregion replication
Enable crossregion replication has the following essential prerequisites:
-
Vault creation: Ensure that you’re using a vault created after this feature’s general availability. Older vaults aren’t eligible for replication and can’t be migrated to support it. If needed, create another vault to utilize this feature.
-
Identity and Access Management (IAM) policy: An appropriate IAM policy must be in place to allow the Vault service to perform replication (copying vaults and keys) in the destination region on your behalf.
Vault creation
The following images can help you identify if your vault is suitable for cross-region replication.
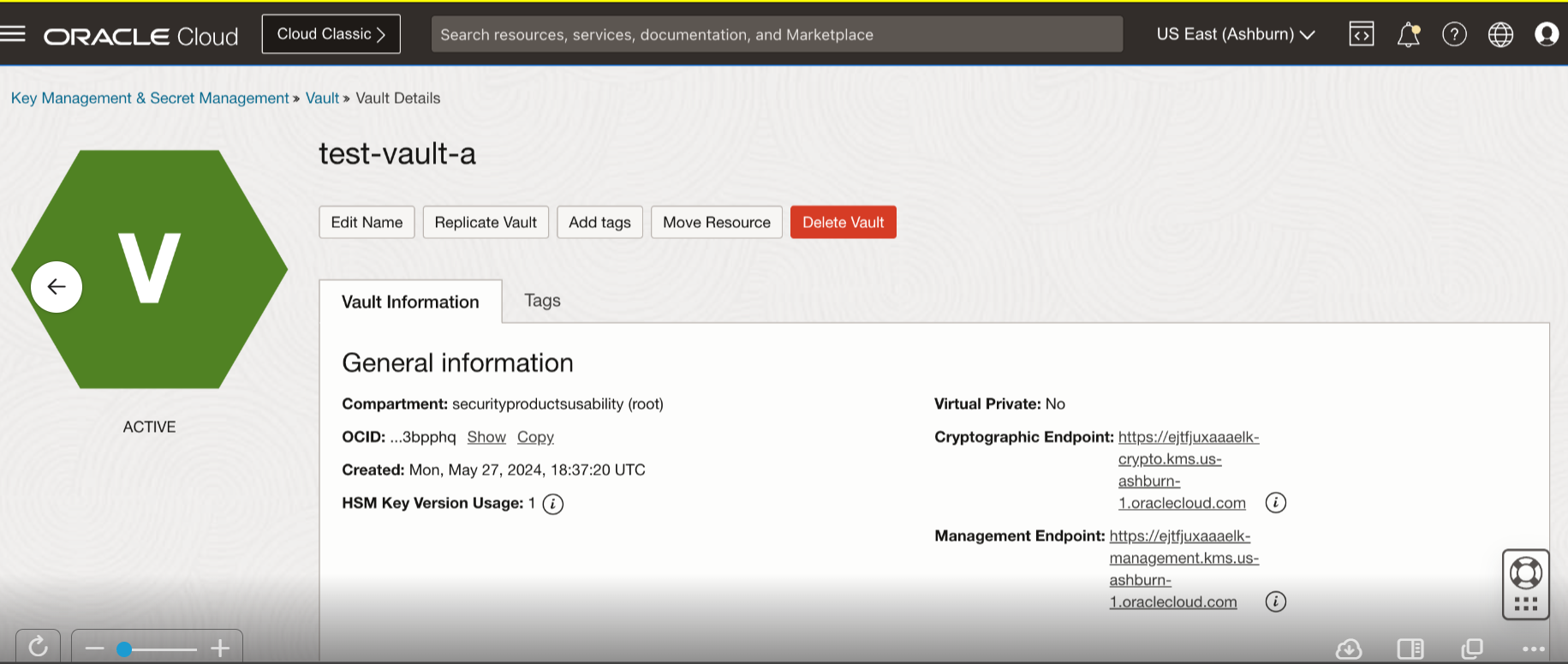
Figure 1: A vault that can be replicated cross region has the Replicate Vault action button
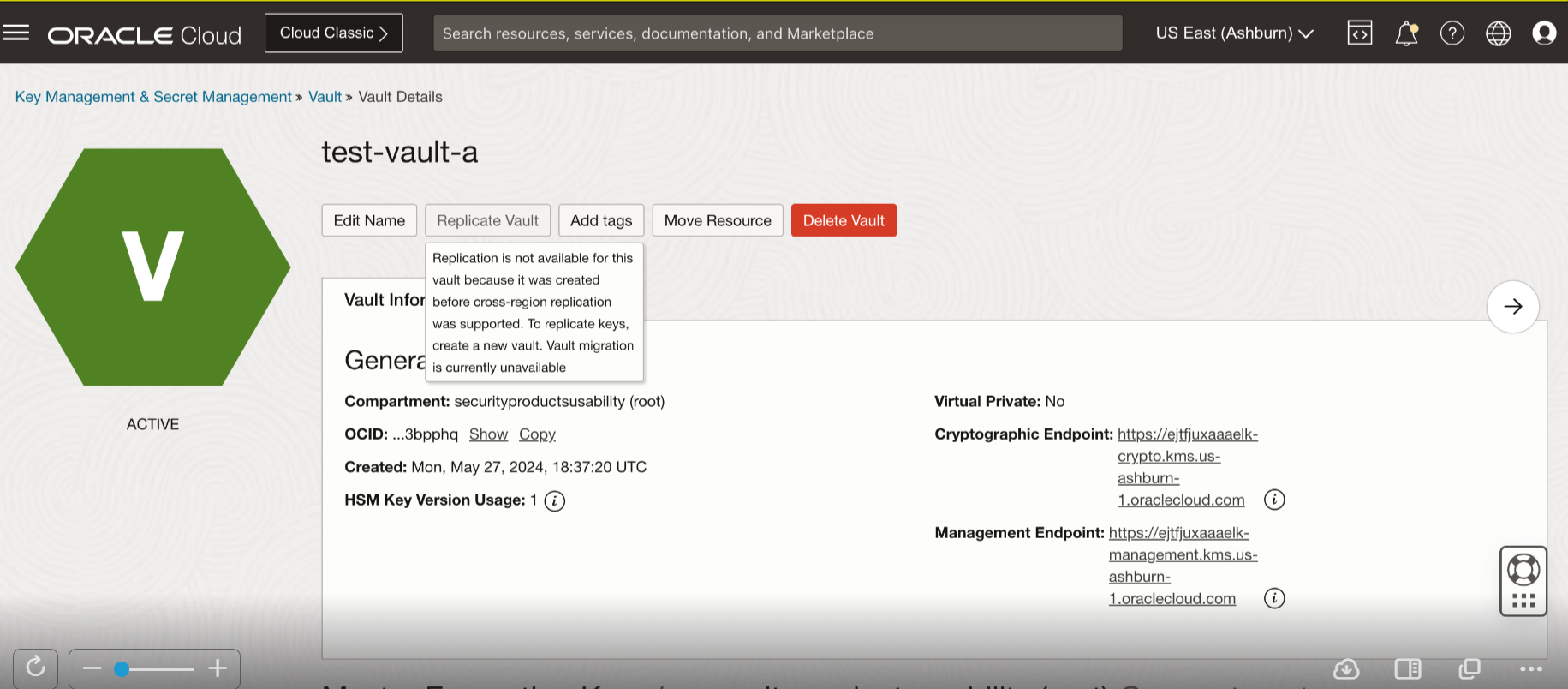
Figure 2: Vault that can’t be replicated cross region has a disabled Replicate Vault button
IAM policy
A policy must be in place to allow the Vault service to perform replication, copying vaults and keys, in the destination region on your behalf.
The policy, “Allow service keymanagementservice to manage vaults in tenancy,” grants replication permission to the service across all compartments within the tenancy.
After you create a vault and set the appropriate IAM policies, replicating it is as simple as a single selection or API call, where you simply select the destination region. Replication occurs at the vault level, allowing all your keys to be copied efficiently. For detailed instructions on replicating vaults, refer to the OCI KMS documentation.
Pricing
Enable crossregion replication in the Vault service incurs no extra charge, but charges apply for each key version created in the source and in the destination region according to the OCI KMS documentation.
Next steps
This new capability significantly enhances data availability and disaster recovery capabilities for KMS customers. It enables seamless access to encryption keys even in the event of a regional outage, helping to minimize application downtime and data loss.
To try it yourself, learn more about Oracle Cloud Infrastructure Vault and sign up for a Free Tier account.

