Security is one of the core tenets of Oracle Cloud Infrastructure (OCI). OCI’s security-first design principles incorporate network infrastructure security with isolated network virtualization and firmware security with hardware-based root of trust, ensuring that hosts boot from a clean firmware for each new customer.
However, threats like rootkits and bootkits that have kernel-level privileges can infect the firmware and operating system and are difficult to detect. Rootkits containing low-level malware allow an attacker to perform the following tasks:
-
Take control of the system without the owner’s knowledge
-
Run files remotely
-
Change system configuration
-
Steal passwords and encryption keys
-
Perform data exfiltration
Bootkits are a type of rootkit that targets the boot code and can cause system instability and inability to launch the operating system. These tactics are commonly used to perform ransomware attacks.
Unfortunately, rootkits and bootkits are hard to detect because they activate even before the operating system boots and can block antivirus and antimalware software, rendering them ineffective. That’s why we’re now enhancing our security portfolio with new shielded instances, which protect virtual machines (VM) and bare metal instances against these low-level threats.
Shielded instances for Compute
Shielded instances are comprised of the following features:
-
Secure boot
-
Measured boot
-
Trusted platform module (TPM)
These services are provided for the OCI platform at no charge.
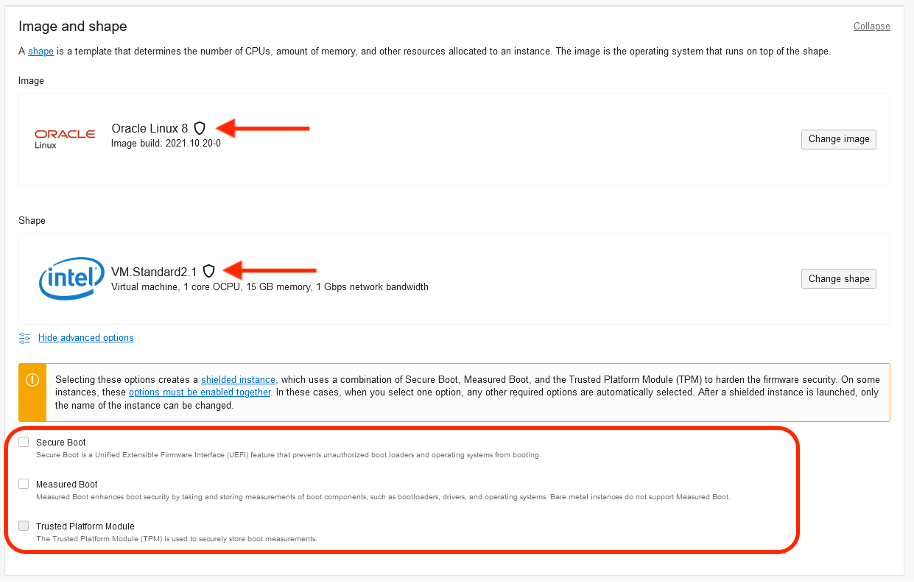
Secure boot is a unified extensible firmware interface (UEFI) feature that prevents unauthorized boot loaders and operating systems from booting. Secure boot validates that the signed firmware’s signature is correct before booting. This extra check prevents rootkits, bootkits, and unauthorized software from running before the operating system loads. Boot components that aren’t properly signed are not allowed to run, preventing the system from booting.
Measured boot complements and enhances secure boot by storing measurements of boot components, such as bootloaders, drivers, and operating systems, and verifies that these measurements don’t change from one boot to the next.
Trusted platform module (TPM) is a specialized security chip used by measured boot to store the boot measurements securely. For VMs, a virtual TPM (vTPM) is used for the boot measurements.
Setup
Enabling shielded instances is easy. You follow the standard instance deployment flow. Images and shapes that support shielded instances have a shield icon next to the image and shape. When you choose the image and shape that support shielded instances, you can enable secure and measured Boot in the Advanced Options. Enabling measured boot for VMs automatically enables vTPM as well.
After the VM or bare metal instance boots securely, the instance information page lists if secure boot, measured boot, and TPM are enabled. You can view and download the boot component measurements stored in the TPM from the Shielded Instance tab. Subsequent reboots then use the measurements to verify that the boot components weren’t modified by any malware and validate the integrity of the boot process.
Want to know more?
-
Test out shielded instances.
-
If you don’t have an account, try out Oracle Cloud Free Tier.
