For this posting, I have contributing guest authors Praveen Kollaikal and Miranda Jiménez from Technical Product Management in the Oracle SaaS Cloud Security (SCS) organization.
Running businesses on the Cloud is second nature to organizations in this digital age. As companies increase their reliance on private or public applications, the attack methods become increasingly varied and sophisticated.
The Web Application Firewall (WAF) for Fusion further strengthens layer-7 security and safeguards both public and private facing Fusion applications from incoming traffic, reducing the associated risks. By including WAF as part of Fusion security, Oracle is further extending our existing defense-in-depth architecture where a variety of security controls are already deployed.
What is WAF for Fusion Applications?
WAF for Fusion is Oracle’s managed second-generation, enterprise cloud-based security solution that works as an additional security control providing always-on layer-7 protection against targeted attacks. Specifically, WAF for Fusion can monitor and detect malicious HTTP and HTTPS traffic sources to help safeguard your Fusion applications, workloads, and critical data from DDoS attacks, as well as the top 10 OWASP risks and other web application threats. WAF is embedded and deployed within OCI Load Balancer instances running in front of Fusion applications. For example, it can sit in front of a supplier portal where bad actors can try to perform a DDoS attack or exploit other classes of vulnerabilities. WAF for Fusion will inspect every traffic request and can detect anomalies to apply Out of the Box (OOTB) layer-7 policies that assess the incoming traffic attributes and determine if an attack is being attempted, and then send log entries to the Oracle SIEM.
Layer-7 policies within WAF for Fusion are composed of a set of rules that support access controls, OWASP Core Rule Set protection capabilities, and rate limiting, while also considering the availability, performance, and scalability requirements of Fusion Applications. WAF for Fusion can also propagate rules updated to the load balancer for enforcement. WAF for Fusion is designed to detect and block potential threats while also supporting application security and compliance requirements at any scale, including for PCI, HIPAA, GDPR, and other industry and regulatory frameworks.
Stopping Attacks Beyond the Edge
Common use cases for these OOTB layer-7 policies range from blocking malicious attempts to flood an online service to protecting against specific targeted requests attempting to take over an application’s systems. Some examples include:
- HCM Recruitment portals are a warehouse of personal information where bad actors may want to gain access for data exfiltration or take the service down through a DDoS attack. WAF for Fusion can inspect for such attack patterns and apply rate-limiting rules to either deny or redirect the traffic requests that overpass the threshold interval. Such actions can help mitigate risks associated with application downtime and slowing down or stopping a customer’s recruitment process.
- CX Customer Relationship Management tools often provide opportunities for potential customers to accept content from untrusted servers and get compromised. To help ensure that traffic reaching your applications is coming from trusted servers and safeguard it from Cross Site Scripting (XSS) and SQL injection, WAF for Fusion’s built-in XSS detection rule can detect and block the access to the vulnerable/arbitrary script for its execution.
- Protection rules. For a long time, Remote Code Execution (RCE) vulnerabilities have been considered complex since they allow the injection of arbitrary code that is then interpreted or executed by the application. WAF for Fusion can detect and block RCE exploitation attempts with its capability to deliver detailed information of these requests and responses, such as the insertion of values into your error logs, web application parameters, and HTTP header fields.
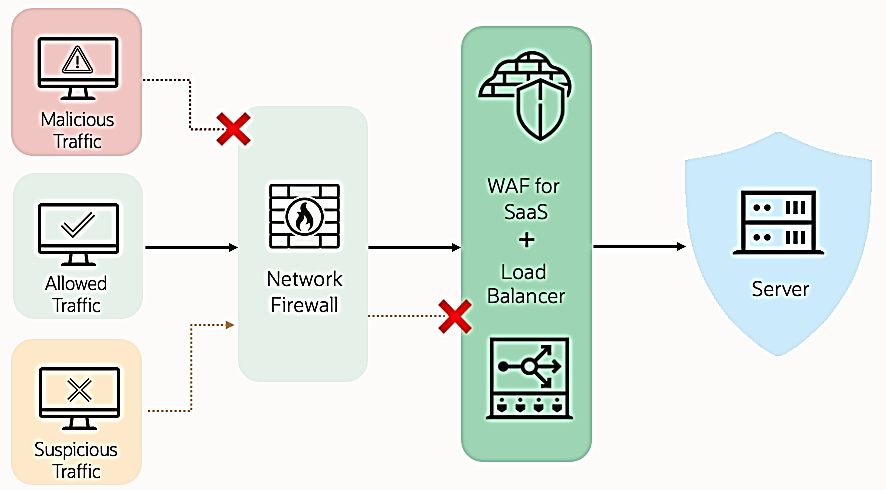
Policies/Rules and logs will only be available to Oracle’s SaaS Cloud Security team.
WAF for Fusion is integrated with Oracle SaaS Cloud Security’s SIEM to receive WAF logs for monitoring. These enrich the detection capabilities of SIEM, and the Oracle Security Operations Center (SOC) will be alerted when these anomalous behaviors are detected in order to help take appropriate corrective actions.
Summary
WAF for Fusion is completely transparent to customers and managed by Oracle’s subject matter experts in an end-to-end fashion. With this out of the box offering, customers are supported with a 24/7 Security Operations Center responsible for helping update, monitor, manage, respond, and protect Fusion applications, without impacting on any application resilience or availability.
WAF for Fusion improves our customers’ security posture by providing the Oracle SCS team with additional visibility into SaaS application attacks and to serve as a shield against a range of attack vectors. It is available free of charge for all Fusion customers hosted on Oracle Cloud Infrastructure.


