The business-to-business (B2B) payments industry has been growing consistently, and the innovations it has produced are a key enabler of B2C transactions growth for companies around the globe. Despite having already gone though significant change, which the COVID-19 pandemic accelerated, the payments industry is still experiencing a major transformation driven by not only the macroeconomic and geopolitical environment, but also by the modernization of technology happening at all stakeholders of the payments ecosystem, including banks, payment networks, financial technologies (fintechs), solution providers, and merchants.
For payments solutions providers, a direct implication of this industry transformation is the need to provide real-time payments solutions. The solutions they provide need high performance and enough elasticity to accomodate demand spikes at their customers. In this view, the cloud assumes a strategic importance. Oracle Cloud Infrastructure (OCI) is an optimal cloud platform with its global presence, allowing solution providers to deploy in the regions they intend to work in, offers market-leading price-performance, and has redefined how security should be delivered in the cloud.
These reasons led a customer of ours to consider OCI as the platform of choice for hosting their payments solution in the cloud. The work we did with this customer directly inspired this post. If you’re a CTO or CISO of a payments solution provider and you’re thinking of delivering your company’s payments solution in OCI, this post covers the most important technical choices you and your teams must consider to maximize the value from your cloud deployment.
Account governance
When it comes to governance in OCI, you must design with the following factors in mind:
-
Governance in OCI that aligns to your operating model: You must set up your tenancy by defining the compartments, user groups, and resource access policies that match your operating model. We recommend that you take the OCI Center for Internet Security (CIS)-compliant landing zone design as your baseline for this task and adjust if needed. This adoption can speed up this process and provide you with a best-in-class security posture.
-
Identity and Access Management (IAM): For OCI resource access management, use the OCI IAM service. For your application users, decide between using OCI IAM and a third-party IAM solution. We recommend using OCI IAM for a fully featured IAM platform delivered as a service, so you don’t need to manage infrastructure, patching, availability, and scaling. If you need to integrate with third-party identity providers like Azure Active Directory or Microsoft Active Directory, OCI IAM makes integration easy. If you use the recommended approach, identifying your user populations and having a clear view of their distinct requirements inform the important design choice. With this information, you can define the identity domains that best suit your tenancy and workload.
Workload placement
You should be able to place your workload closest to the markets you operate in. With OCI having more than 40 public cloud regions worldwide, you have choices. If you can’t deploy in a public cloud region, and depending on the scale of the deployment, Oracle provides OCI Dedicated Region, which you can deploy in an in-coutry data center. Solution providers, such as in Switzerland, have installed a dedicated region to host financial applications of their end customers.
Deployment architecture
To design the networking architecture in OCI, keep the following requirements in mind:
-
Traffic coming in from different origins and inspection of that traffic (North-South network direction)
-
Zero trust and traffic inspection between each tier of the application (East-West network direction)
-
Application Isolation
-
Removing complexity
In your on-premises deployment, you most likely have several LANS or vLANs to isolate the different tiers of the application, plus several demilitarized zones (DMZs) and firewalls to control traffic. You can replicate this architecture in OCI. However, when moving to OCI, take advantage of the networking capabilities to enhance your existing design. OCI networking capabilities enable you to keep your design simple, secure and scalable.
We recommend that you follow these networking principles for deploying a robust solution. Although they’re best practices for any workload, they’re paramount when moving a payment solution to the cloud by assisting with security compliance.
-
Minimize the number of virtual cloud networks (VCN): If you’re deploying only a production environment in the cloud, you need only a single VCN. On the other hand, if you deploy several environments, have no more VCNs than the number of environments plus one. The extra VCN is a hub VCN for hosting your public services and inspecting public traffic. Carefully evaluate any exceptions to this rule.
-
Minimize the number of publicly exposed components. You want to minimize your attack surface. We advise exposing public services through a load balancer and keeping the rest of the infrastructure private.
-
Minimize the number of subnets while preserving isolation by using network security groups (NSG). Group components in the same tier into the same subnet to keep the number of subnets low. Use NSGs to differentiate between different application security requirements.
-
Concentrate your traffic inspection: Configure a maximum of two OCI network firewalls, one for public traffic inspection, such as Access Control server traffic coming from the Internet, and one for private traffic inspection.
-
Beyond TCP insepction, include HTTPS inspection in your design. Add an OCI WAF policy to each network traffic entry point.
The following diagram depicts an architecture that follows this architectural guidance.
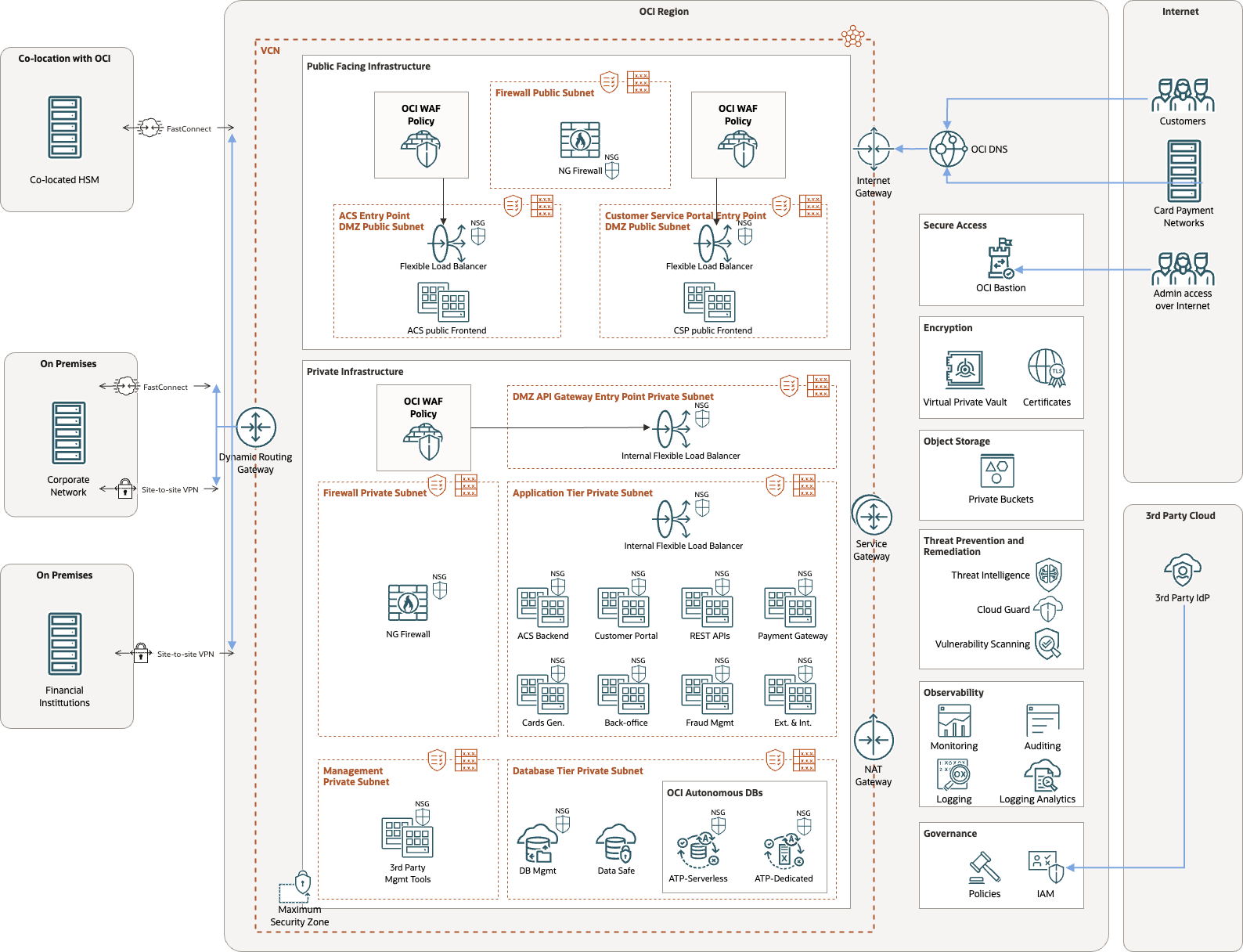
Connectivity model
You must decide on the type of connectivity you want to establish between your workload running in OCI and the sites or parties you need to integrate with, such as the following examples:
-
Financial institutions: If you provide card and payment services to financial institutions, you must establish connectivity relying either on IPSEC VPN or dedicated circuit through OCI FastConnect. Consider your own service license agreements (SLAs), distance to the workload, and cost of the connectivity. For example, if the distance to the workload on a dedicated circuit is too expensive, a VPN is an acceptable choice.
-
Cards and payments network: Typically, these networks rely on the Access Control server that implements a 3-D Secure protocol, placed in a demilitarized zone (DMZ) with a public IP address as illustrated in the architecture diagram.
-
Your own corporate network: Decide between an IPSEC VPN and OCI FastConnect using the mentioned criteria.
Encryption management
For a multitude of use cases within the payments domain, a hardware security module (HSM) is a fundamental component of a payments solution. When delivering this solution from OCI, you must decide between having the HSM capability delivered as a service by OCI Vault or having it delivered by an industry appliance. Both are feasible, but they represent different ways of realizing this capability.
OCI Vault is a key management service that stores and manages master encryption keys and secrets for secure access to resources. It uses an HSM that meets Federal Information Processing Standards (FIPS) 140-2 Security Level 3 security certification to protect your keys. An HSM appliance is the appliance you’ve already been using. Keeping your existing HSM adds another layer to the architecture and can add more capital costs to your budget.
Choosing OCI Vault over a colocated HSM appliance offers the following advantages:
-
Shorter time-to-market
-
Fully managed
-
Continuous improvement of functionality and capabilities
-
FIPS 140-2, Level 3-certified, hardware security module
-
Integrated with other OCI services
You might need to make some application level changes to integrate OCI Vault into your process. Evaluate the trade-off between having a managed service that might require some application changes and using the appliance you already use, which might require budget for colocation and connectivity. Involve your application development team or your OEM software supplier in this decision.
BLOG UPDATE
Introduction of OCI External Key Management Service
In October 2023, the OCI External Key Management Service (KMS) was launched. This introduces a new encryption model option for customers who have regulatory needs to store encryption keys on-premises or outside OCI, while migrating their applications to OCI. OCI External Key Management Service (KMS) encrypts data in OCI using encryption keys that are managed in a third-party key management system, hosted outside OCI. OCI External KMS supports Thales CipherTrust Manager and support for other third-party key management systems is expected in the future. OCI External KMS supports symmetric encryption keys and is compatible with applications and OCI Services that are already integrated with OCI Vault.
Enhancing your security
You must consider other capabilities to make your workload more secure in the cloud. The most important choice you must make is choosing between OCI’s built-in security services and 3rd party security solutions.
We recommend using OCI’s security services to have a smoother and more cost-effective experience, complementing with Oracle Cloud Marketplace security solutions for added capability. Try to avoid replication of the security stack you have on-premises and keep the deployment as simple as possible. Simplicity drastically reduces the time to implement your workload while ensuring you have cloud best-in-class security services.
The architecture diagram follows this approach through the use of the following OCI services:
-
OCI Bastion: OCI Bastion provides restricted and time-limited access to target resources that don’t have public endpoints. Bastions let authorized users connect from specific IP addresses to target resources using Secure Shell (SSH) sessions. When connected, you can interact with the target resource by using any software or protocol supported by SSH. For example, you can use the Remote Desktop Protocol (RDP) to connect to a Windows host, or use Oracle Net Services to connect to a database.
-
OCI Network Firewall: OCI Network Firewall is a next-generation managed network firewall and intrusion detection and prevention service for your OCI VCN, powered by Palo Alto Networks. The Network Firewall service offers simple setup and deployment and gives you visibility into traffic entering your cloud environment (North-south network traffic) and traffic between subnets (East-west network traffic).
-
OCI WAF: OCI Web Application Firewall is a regional-based and edge enforcement service attached to an enforcement point, such as a load balancer or a web application domain name. WAF protects applications from malicious and unwanted internet traffic. WAF can protect any internet facing endpoint, providing consistent rule enforcement across a customer’s applications.
-
OCI Certificates: The OCI Certificates service provides organizations with certificate issuance, storage, and management capabilities, including revocation and automatic renewal. If you have a third-party certificate authority (CA) that you already use, you can import certificates issued by that CA for use in an OCI tenancy. Integration with OCI Load Balancing service lets you seamlessly associate a TLS certificate issued or managed by Certificates with resources that need certificates.
-
OCI Vault: Vault lets you securely store master encryption keys and secrets that you might otherwise store in configuration files or in code. Specifically, depending on the protection mode, vault keys are either stored on the server or on highly available and durable HSMs that meet FIPS 140-2 Security Level 3 security certification.
-
OCI Cloud Guard: Cloud Guard examines your OCI resources for security weakness related to configuration and your operators and users for risky activities. Upon detection, Cloud Guard can suggest, assist, or take corrective actions, based on your configuration.
-
OCI Threat Intelligence: OCI Threat Intelligence aggregates threat intelligence data across many different sources and manages this data to provide actionable guidance for threat detection and prevention in Oracle Cloud Guard and other OCI services.
-
OCI Vulnerability Scanning: OCI Vulnerability Scanning Service helps improve your security posture by routinely checking hosts and container images for potential vulnerabilities. The service gives developers, operations, and security administrators comprehensive visibility into misconfigured or vulnerable resources and generates reports with metrics and details about these vulnerabilities including remediation information.
-
OCI maximum security zones: Security zones let you be confident that your resources in OCI, such as Compute, Networking, Object Storage, Block Volume and Database resources, comply with your security policies. When you create and update resources in a security zone, OCI validates these operations against the list of policies that are defined in the security zone recipe. If any security zone policy is violated, the operation is denied.
Further considerations: PCI compliance
While PCI compliance is beyond the scope of this post, you must consider it for deploying your payments workload in OCI. The considerations in this post can enable you to significantly achieve PCI compliance in OCI. The following articles can provide more information:
You must likely meet other compliance frameworks, such as ISO27001, SOC1/2, ISO 27017, and so on. OCI is certified with many of these frameworks. For the latest information, see the latest Oracle Cloud Compliance list.
Conclusion
We hope that you have a clearer understanding of the most important technical considerations for a successful deployment of your payments solution in OCI. Consider the following key takeaways:
-
Think governance in advance, so you can design and implement in OCI according to your operating model.
-
Architect for running as simply as possible in the cloud. Don’t try to replicate on-premises architecture exactly in the cloud.
-
Utilize OCI’s native security services for your workload to keep the deployment as simple as possible.
-
Evaluate the trade-offs for HSM implementation and choose based on your needs.
If you want to discuss how you can deploy your workload in OCI, contact us. We can work with you to ensure that the best design is produced. If you want to go hands-on with Oracle Cloud Infrastructure and try it yourself, visit Oracle Cloud Free Tier.

