As a product manager focused on Oracle Cloud Infrastructure’s core platform capabilities, I’m often asked for best practices on how to use features like compartments and tagging to optimize cost management, simplify operations, and maintain governance.
In this post, I discuss some best practices for using compartments to organize your resources, set your access control boundaries, and target your management and governance actions.
The Results of a Well-Designed Compartment Strategy
A well-organized tenancy that uses a hierarchy of compartments has many benefits:
- Access control policies can be easily and correctly written.
- Administrative privileges can be delegated to compartment administrators, who can manage just their portion of the compartment tree.
- Charges can be allocated back to a department if that department is given a compartment tree. When you divide cost centers by compartment, it becomes obvious where the money is spent.
Compartment Basics
Compartments allow you to organize your resources so you can delegate cost controls and administrative access. These logical containers house your resources, aren’t tied to any data center, and can span all data centers. All resources reside in a compartment.
The tenancy administrator can design the layout of the resources so that access control policies give the correct access to the correct groups. Compartment design also makes it easy to govern resources by assigning budgets and quotas, and applying tags to the resources.
Compartments are the only hierarchical organizational resource in Oracle Cloud Infrastructure. They’re also the only resource that can have policies attached to it. Therefore, I recommend that you structure your compartment layout to achieve your access-management goals.
Best Practices for a Creating a Sound Compartment Hierarchy
To add organizational hierarchy to all your resources, nest your compartments.
Design your compartment hierarchy to reflect your access control boundaries. If a certain group needs to access only one set of resources, put those resources in their own compartment.
Nested compartments also make it easier to delegate administrative access to compartment administrators. When you create a compartment for a department, the members can create subcompartments to reflect their own organization. You can delegate administrative tasks to the department and govern the usage by the entire department rather than getting into the details of projects. Access control policies enforce this delegation.
Compartments provide boundaries for user access control and governance, but resources can be accessed across compartment boundaries. For example, you could put all your virtual cloud networks (VCNs) in one compartment. All compartments can access and attach to those VCNs, but you make administration easier when you limit management access to those VCNs to only the network administrators.
The following example from the mythical BlueCat Corp tenancy illustrates some of the common design patterns for compartment hierarchies. It also demonstrates a few compartment organization principals.
- BlueCat organizes their resources by project in the SmartAlec compartment. Inside the project, they subdivide their resources into resource compartments (ADW and DBBackup) and by environment (Dev, Test, and Prod).
- BlueCat groups their high-value networking resources in their own compartment to make the access policy easier to write and more precise. Resources can still connect across compartment boundaries (as illustrated by the green dotted lines that connect compartments to the Networking compartment).
- BlueCat segregates the resources for customer rendering in its own compartment (Customer Rendering).
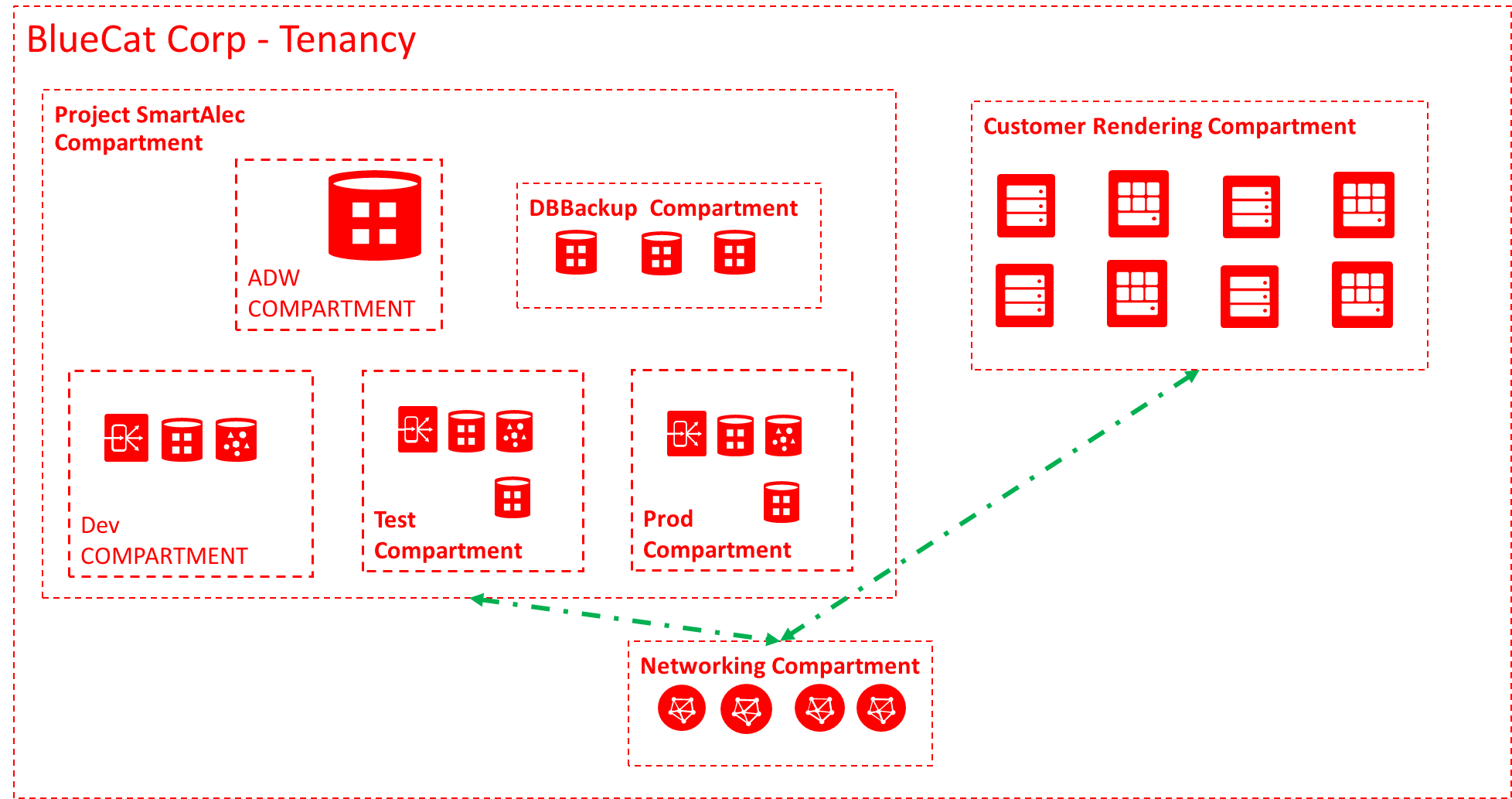
These organization schemes are effective for both governance and access control. I recommend that you follow a compartment organizational scheme that meets your access control and governance needs.
Use as many compartments as you need. Compartments are free, and a tenancy can have hundreds of compartments. The only significant limit for your design is that you can create only six levels of nested compartments. The customers I’ve talked to have never had an issue with that limit.
Policies and Compartments
The main consideration for the design and layout of your compartment hierarchy is to enable easy policy writing that sets the correct access control for your tenancy.
A policy is written as follows:
Allow group <group_name> to <verb> <resource> in compartment <compartment_name>It’s easy to write a policy that allows a certain level of access to a group for all resources or a single type of resource in a compartment.
Delegated Administration
Setting up a compartment hierarchy allows you to delegate the administrative tasks for that entire compartment tree, while ensuring that the delegated administrator can’t change the entire tenancy.
Set up a compartment for each team that you want to delegate to. Then set up an administrative group that you want to delegate administration to for that compartment (for example, SmartAlec_Admins). Then, write the following policy and place it in the root compartment:
Allow group SmartAlec_Admins to manage all-resources in compartment Project_SmartAlecNow the SmartAlec_Admins group has full control over the Project_SmartAlec compartment. They can set up policies for existing groups to grant them access to resources inside their compartment tree.
For example, the SmartAlec_Admins group wants to allow the Operations team full control of the Prod compartment. However, the DevTeam group should have managing permissions of the Dev and Test compartments. A member of the SmartAlec_Admins group would write the following policy:
Allow group Operations to manage all-resources in compartment Prod
Allow group DevTeam to manage all-resources in compartment Dev
Allow group DevTeam to manage all-resources in compartment TestThe SmartAlec_Admins group also wants to separate access to the Autonomous Data Warehouse (ADW) backups from the Autonomous Data Warehouse server resources. In this case, the Operations team manages the backups, and the DB_ADW group manages the servers. The following policy would grant them that access:
Allow group Operations to manage all-resources in compartment DBBackup
Allow group DB_ADW to manage all-resources in compartment ADWManaging Your Compartments
Trying to create the perfect compartment layout the first time might be a bit daunting. But don’t worry—you can change your compartment structure after it’s been created.
We’ve also released a new tool called Compartment Explorer. The tool helps you view all the resources in a given compartment across your regions. So, it’s easy to visualize all your resources and see how they’re organized across compartments.
Currently, you can use the tool to view the details of resources and move a resource between compartments. You can also choose to view resources recursively across subcompartments. We’re continually improving this tool and adding more management capabilities soon.
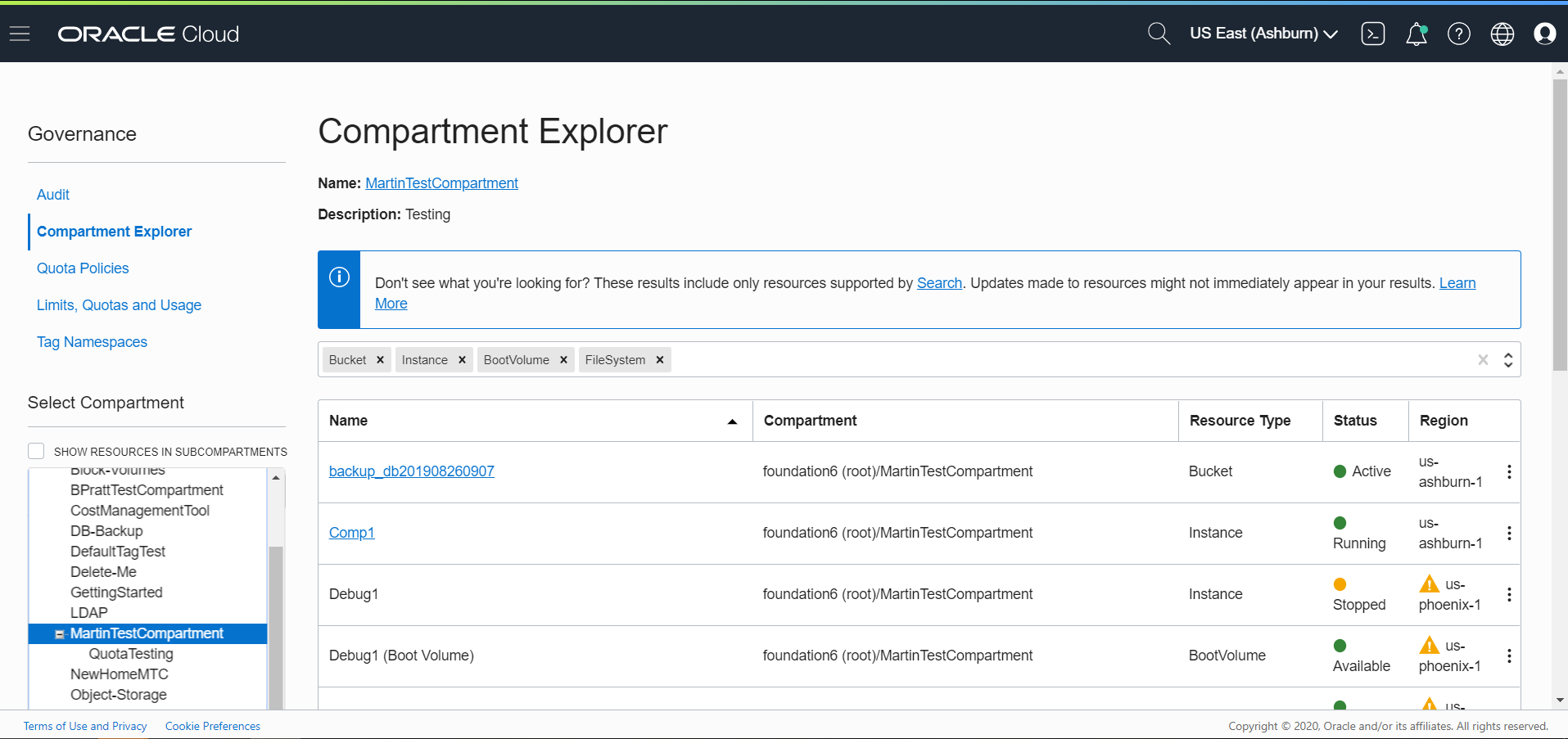
You can reorganize the hierarchy by moving compartment trees anywhere around the tenancy. This flexibility gives you the ability to quickly react to reorganizations. To further manage your compartments, you can also rename, delete, and restore a compartment.
Using Compartments for Governance
Most governance features can be targeted in a compartment tree. This targeting allows great flexibility in how you want to manage your tenancy with compartment and governance tools.
Budgets and Quotas
You can set cost budgets and resource quotas for a compartment tree in your tenancy.
- A budget alerts you when the spending (or forecasted spending) in a compartment exceeds a threshold.
- A quota allows you to set the amount of a resource that you want to allow. For example, you could restrict the number of Compute instances of a certain shape that may be deployed to a compartment.
Creating compartments that reflect your departments or projects makes it easy to set budgets and quotas for those departments or projects.
These budgets and quotas are aggregated in the compartment tree. So, you can set a budget for a department that resides in the compartment Data Analysis, and the department itself can set budgets for their subcompartments. For example, if you have a budget of $2000, and the Data Analysis team creates two subcompartments for data and analysis, they can create budgets of $1000 for each compartment. They’d get an alert if either of those compartments was forecasted to exceed $1000.
You can therefore create hierarchical budgets and quotas, which allow you to turn over the maintenance and cost control of your tenancy to your compartment administrators. To learn more about Oracle Cloud Infrastructure cost management features, read the Cost Management page.
Tag Defaults
Tag defaults automatically apply tags to any resource created in the compartment that the tag default is attached to. For example, an administrator could create a tag default that applies a tag called Operations.CreatedBy with the value of ${iam.principal.name}. This tag would be expanded to the user name of the creator of the resource. Tenancies are now created with two automatic tag defaults: CreatedBy and one that captures the time the resource was created.
To save time and effort, the administrator can use this tag default on the root compartment of the tenancy, which would tag every resource created in the entire tenancy with that tag default.
Similarly, if a compartment administrator wanted to apply a tag to any resource in their compartment tree, they can create a tag default in the top compartment of their compartment tree. To learn more about tagging features, see the Tagging product page. You can also read more about our best practices for tagging in my Best Practices for Using Tags To Manage Costs, Operations, and Governance blog post.
Summary
There are many benefits to having a well-designed compartment hierarchy. I hope you continue to use compartments with your tenancies, because it’s the best organizational tool we have at our disposal to govern a tenancy. All our new governance features use compartments to make it easy to target the features at exactly the resources in your tenancy.
If you’re new to Oracle Cloud Infrastructure, get started today by creating a free account.
