Cloud scale protection is a vital part of enterprise cybersecurity, particularly in the context of distributed denial of service (DDoS) attacks. These attacks are designed to overwhelm a server or network with a flood of internet traffic, disrupting the targeted system’s normal functioning. In an age where data is king, and our lives are intrinsically tied to digital platforms, the ability to mitigate such threats is crucial.
DDoS attacks at a cloud scale are an amped-up challenge because of the sheer scale of the operation. The enormous volume of legitimate traffic makes spotting malicious traffic more difficult, and a surge in legitimate traffic can easily be mistaken for an attack, causing potential false alarms and unnecessary panic. Cloud providers must quickly identify and counteract attacks, or risk service disruption, user dissatisfaction, and reputational damage. In this blog post, we don’t delve into the minutiae of our current DDoS detection and mitigation mechanics, but we share some of how hyper scale clouds effectively mitigate these threats.
The relentless rise of DDoS attacks
In the early 1990s, I had just started working for iSTAR internet, the first national ISP in Canada, when most of us had 2400 baud modems or 2.4kbps. How does this compare to the internet service you currently have at home or the 5G service on your smartphone? Back then, the concept of DDoS attacks wasn’t even on our radar in terms of security concerns. As I transitioned to internetMCI in the following years, the security landscape was dominated by challenges such as the rising tide of SPAM, blocking outbound port 25, and the early waves of Denial of Service (DoS) attacks.
We saw the first basic DDoS attacks in 1996, targeting Panix, a New York-based ISP. This early attack overwhelmed the target system with requests and rendered it unresponsive. The turn of the millennium saw the rise of more sophisticated DDoS techniques like botnets, resulting in notable attacks, such as those in 2000 on Yahoo!, eBay, and CNN, generating unprecedented media attention and showcasing the vulnerabilities of the most prominent websites. It’s estimated that the attack on Yahoo! alone caused a drop in the company’s stock value and resulted in $1.1 billion in global economic impact. As the digital landscape evolved, DDoS attacks surged, and the subsequent years witnessed an exponential growth in malicious traffic, reaching an astonishing 40 Gbps by 2007.
By 2010, DDoS attacks had escalated to an even more potent scale of 100 Gbps. This surge was fueled by amplification attacks, exploiting vulnerable protocols to increase the volume of the traffic sent to the victim and expanded botnets because of the increasing usage of internet of things (IoT) devices, which often lacked effective security measures. In 2016, Mirai exploited poorly secured IoT devices to orchestrate an unprecedented 620 Gbps attack. Unlike previous DDoS attacks that focused on network and transport layers, Mirai targeted the application layer, diversifying attack vectors and making defense more challenging.
Because of the continued proliferation of IoT devices, faster internet connections, and the widespread availability of DDoS tools, we’re facing a staggering 13 million attacks a year, as counted by Netscout in their yearly report, with DDoS attacks exceeding 3 Tbps. The complexity of attacks, including multivector strategies exploring various security or network design flaws, has led to a highly complex threat landscape that poses detection and mitigation challenges.
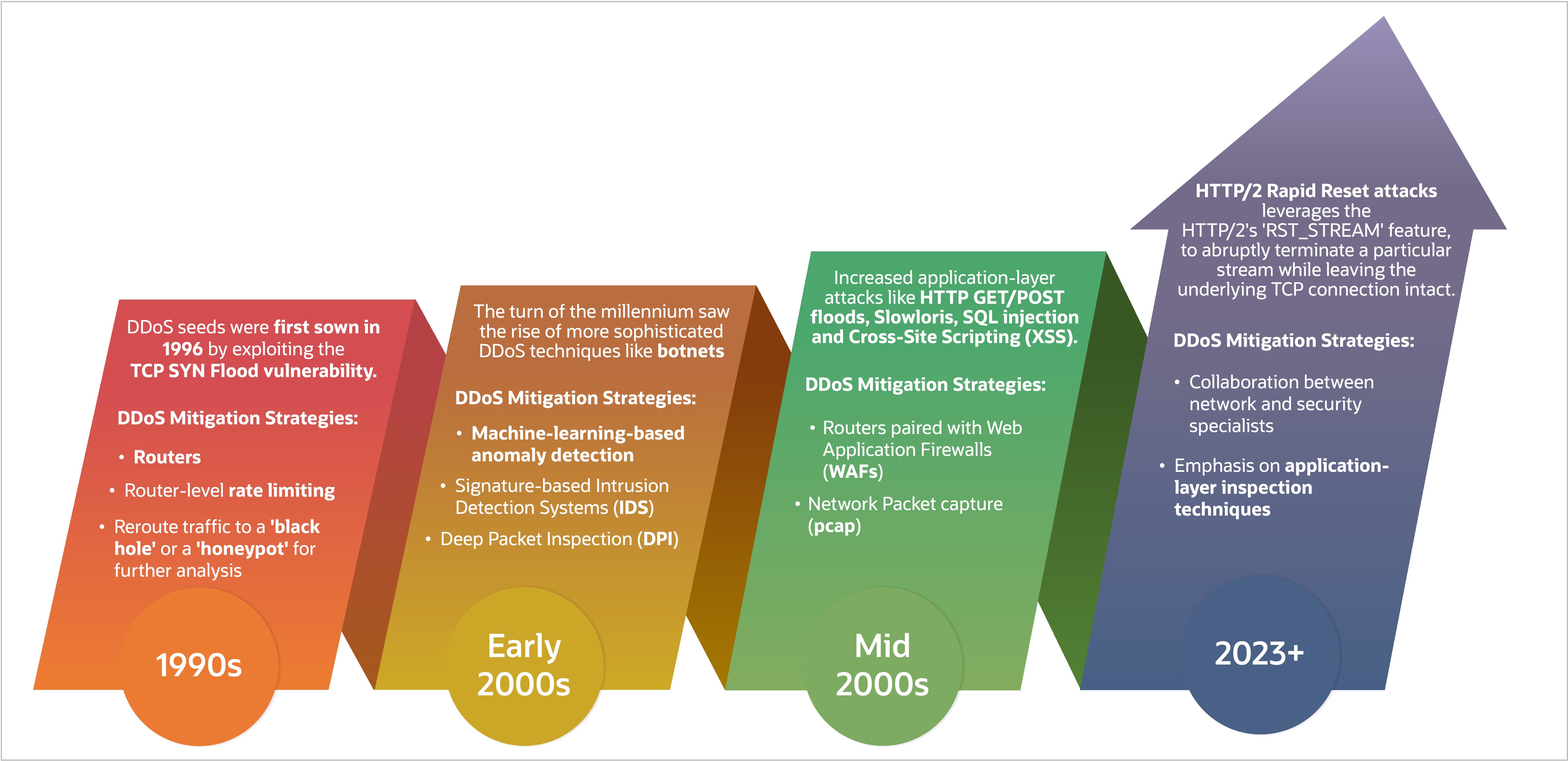
Figure 1: Evolution of DDoS attacks
Managing DDoS
Before we dive into the details of cloudscale DDoS management, let’s look at the strategic approach to counter this ever-morphing DDoS behemoth in data centers, where the majority of an enterprise’s servers and storage are located, operated, and managed.
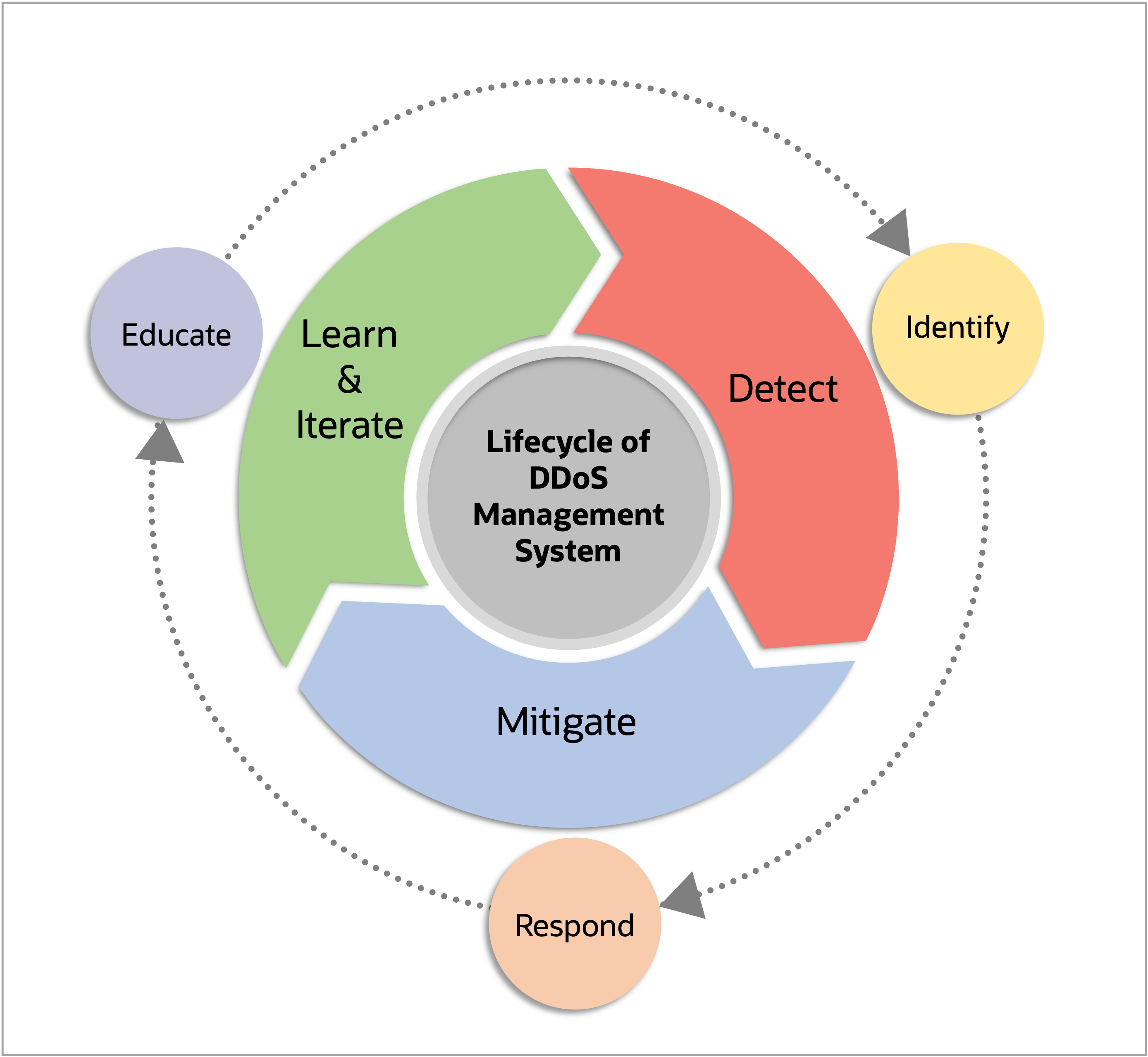
Figure 2: Lifecycle of DDoS management system
DDoS detection
Before we can do anything about an attack, we must spot it. Here, DDoS detection steps in. Picture your services as a colossal digital stadium, hosting myriad digital beings, such as applications, services, and data. The network traffic is the crowds, swarming in to witness the spectacular show. Now, imagine DDoS attacks as an unwanted mob, wearing disguises, attempting to storm the gates and overcrowd the stadium to the point of chaos. The art of detecting DDoS attacks is like stationing vigilant bouncers at the gates, scanning the incoming crowd to analyze the baseline: Understanding the regular fans who always show up.
DDoS attacks can be crafty, disguising themselves as legitimate users and making your bouncers second guess themselves. For example, IP spoofing is like wearing someone else’s fan gear to blend in. Often paired with web application firewalls (WAF), routers come into play like high-tech scanners, scrutinizing everyone for hidden motives. They look at things like the IP addresses involved and the type of data being sent.
DDoS mitigation
The alarm bells are ringing, and the attack is on. How do you protect the sanctity of your digital stadium? Behold the DDoS mitigation services, your superheroes. They swoop in and divert the crowd to alternate venues (in DDoS terms, scrubbing centers), sift through the traffic, send the genuine fans back to your stadium, and block the hooligans. However, even the mightiest shields have their limits, and false positives are like accidentally turning away true fans—a terrible idea if you want to stay in business.
The key is resilience, adaptability, and eternal vigilance. Keep your tech, tactics, and knowledge cutting-edge, because a sufficiently large volumetric attack can overwhelm even the most cybernetically enhanced bouncers. In the digital stadium of dreams and data, let not the storm of DDoS lay waste to the wonders you’ve built.
Learn and iterate
Let’s talk about learning from DDoS attacks and closing the loop on these digital storms. Imagine the overwhelmed concert venue calm after the previous night’s chaos. Now, how do you learn from the attack pattern and prepare staff and systems for future onslaughts?
First things first, analyze the attack like a cyber detective. Did they send an army of bots? Or was it a tsunami of data? Understanding the nature of the attack is pivotal to craft strategies and realign defenses.
Second, learn to differentiate between legitimate users and malicious DDoS traffic. How, you ask? AI and machine learning (ML) can help you create models to identify abnormal traffic patterns and discern friend from foe. Next, amp up your communication channels: Having a clear, orchestrated response plan that’s as finely tuned as an electric guitar riff. Inform your team and your internet service provider (ISP), and if you’re using a DDoS mitigation service, let them know too. Everyone should be aware.
After the worst has passed, conduct an analysis of what happened. What slipped through? What could have been done better? Document these findings like they’re sacred texts because the crux is learning to evolve. The digital landscape changes constantly, and your system needs to be in a constant state of evolution. With each DDoS attack you counter, imagine your system growing, learning, and becoming a sentient guardian of your digital realm.
Finally, share your wisdom. The cyber community is a band of rebels and pioneers. By sharing your findings and learning from others, the community becomes a collective shield against the digital marauders of the DDoS world. And there you have it: A roadmap to learn from, adapt to, and close the loop on DDoS attacks.
Now, this all sounds great, but it’s not always as easy as it seems for a cloud service provider (CSP).
Challenges
CSPs have an increasingly challenging role in preventing business impact for all their customers effectively and efficiently. Customers are less capable of mitigating DDoS in the cloud because they don’t see the impact until costs accumulate. Their mitigations still cost them because the traffic has to reach them before it’s suppressed, and some cloud services, such as object storage, automatically scale so that they don’t see the problem until billing time when it’s too late. So, all clouds should offer mandatory and complimentary DDoS detection and mitigation to avoid the agency hazards and use all the available low-level tools to deflect the problems as far upstream as possible, which many currently do.
Even with DDoS detection and mitigation, the challenges get magnified when operating a cloud service because of the sheer scale and geographic scope. Because traffic doesn’t originate from a single place, but from all corners of the world, a DDoS attack can strike from anywhere and at any time, requiring constant vigilance to detect and handle these attacks.
DDoS attacks on a cloud service can manifest in various forms: Flooding the network in a volumetric attack, disrupting the data processing mechanisms in a protocol attack, or targeting specific applications in an application layer attack. The diverse range of services offered by the cloud mean that an attack can unleash a cascade of disruptions, impacting not just a single website or company, but potentially affecting thousands or even millions of users. Failing to swiftly identify and thwart attacks disrupts the service and customer dissatisfaction can hurt the cloud provider’s reputation. However, you can tackle this challenge effectively with the right strategies, cutting-edge technologies, and a dedicated team of professionals. The nature of the cloud is to manage things at scale, and that most certainly includes security.
The power of hyperscale cloud protection
The cloud’s scalability and flexibility provide a robust platform to deal with DDoS attacks. With its vast, globally distributed architecture, the cloud has an innate capacity to handle sudden influxes of traffic that typically overwhelms traditional ISP defenses. This method is the essence of cloud scale protection, and it operates on several levels.
One of the most significant efficiencies of a cloud-based DDoS service is resource allocation. When you’re running your own DDoS mitigation, you’re dedicating a lot of resources to that task, both human and technical. But with a cloud-based service, that responsibility shifts to the provider. So, your team can focus on what they do best: Running your core business operations. If a massive DDoS attack comes your way, a cloud-based service can scale up to meet the challenge, thanks to the vast network and resources of the cloud provider. If you were running your own system, you’d have to prepare for the worst-case scenario, which means investing in and maintaining a lot of infrastructure that might sit idle most of the time.
Cloud scale protection offers the following key benefits in the fight against DDoS attacks:
- Scalability: The cloud’s vast resources can easily scale up or down to handle sudden traffic surges, making it an ideal solution for mitigating DDoS attacks.
- Resilience: With its globally distributed architecture, the cloud provides a high level of resilience. Even if one part of the network is affected by a DDoS attack, the rest of the network can continue to function.
- Intelligence: Advanced ML and AI technologies allow cloud scale protection services to analyze and filter traffic intelligently, identifying and blocking malicious requests.
- Cost-effectiveness-: By using the cloud, businesses can access powerful DDoS mitigation services without the need for significant upfront investment in hardware and infrastructure. This availability makes cloud scale protection a cost-effective solution for businesses of all sizes.
- Flexibility: You can deploy cloud-scale protection services quickly and easily integrate them with existing systems, providing your business with a flexible and adaptable solution to the evolving threat landscape.
- Global reach: The cloud’s global presence allows for traffic to be rerouted and absorbed across a vast network, minimizing the impact of a DDoS attack on any single point of failure.
- Near Real-time response: Cloud-scale protection services monitor traffic in real-time, enabling them to respond quickly to potential threats and adapt their defenses as needed.
- Collaboration: The cloud facilitates greater collaboration between ISPs and cloud-based DDoS mitigation services, enhancing overall system resilience and ensuring a more coordinated response to threats. ISPs, and now hyper scale clouds, hire and retain some of the best computer security talent because of the scope and frequency of interesting events. While customers want to handle as few attacks as possible, security folks want to see everything. They go where the work is most interesting and their services are most needed—the cloud.
Using a cloud-based DDoS service can bring significant efficiencies. However, always remember to consider your specific needs and circumstances when deciding on DDoS mitigation.
DDoS cloud scrubbing centers
DDoS detection and mitigation at the cloud scale is more complex and interesting than most network engineers imagine. But how does Oracle Cloud Infrastructure (OCI) innovate continuously to make DDoS less of a problem for its customers?
When it comes to keeping the internet running smoothly and protecting it from the bad guys, like those who launch DDoS attacks, OCI has DDoS scrubbing centers. They’re like giant virtual sponges that soak up all the attack traffic before it can do any harm. But debate about how best to set these up exists: Should we have a few super-sized scrubbing centers or lots of smaller ones spread all over the place?
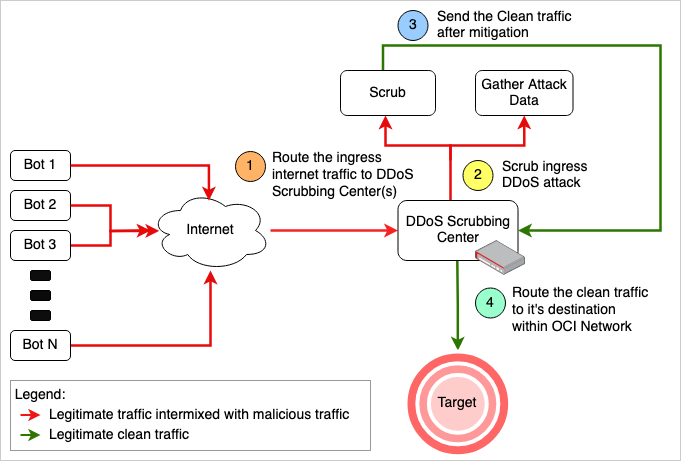
Figure 3: The basic traffic flow of scrubbing an incoming DDoS attack
Let’s start with the idea of having a few big centers. They’re like huge fortresses that can handle a ton of attack traffic all at once. The upsides of this method include cost-effectiveness, because you only build and run one facility, and the ease of managing and monitoring one place. On the other hand, if the traffic must travel far to get to the center, it can slow things down, which is annoying for users. If the center goes down for some reason, whether a mega DDoS attack or a technical hiccup, everyone relying on that center is out of luck.
The alternative is having lots of smaller scrubbing centers all over the globe. Traffic doesn’t have to travel as far to get cleaned up, things run faster, and users have a safety net. However, this option can be pricier because you must set up and maintain lots of centers, and when you have centers everywhere, it can be tricky to keep track of what’s going on and handle any problems that pop up.
The big versus small debate isn’t an easy choice and depends on how much you’re willing to spend, how fast you want things to run, and how prepared you want to be for any issues. Some folks might lean towards the cheaper and easier-to-manage big centers, while others might prefer the faster, more fail-safe option of having lots of smaller centers.
Conclusion
Operating your own DDoS mitigation system can feel like running a small, private police force in the sprawling cityscape of data. You’re in control with your hands on the levers. However, maintaining such a system is labor-intensive, resource-heavy, and demands constant vigilance, not to mention a substantial expense for equipment and personnel. It’s hard work, particularly if you’re up against a tsunami of malicious traffic.
In contrast, consider cloud-based DDoS services, the razor-sharp corporate enforcers of the digital city. They bring with them the raw power of the cloud’s expansive infrastructure, an army of digital defenders ready to step in when trouble looms. With their geographically diverse data centers, they stand watch over the global data highways, ready to absorb and dissipate the brunt of an attack.
These cloud warriors bring efficiency to the frontlines. They stand vigil, allowing your own tech wizards to focus on what truly matters: Your core business. When trouble comes, they scale up, their vast networks diluting the impact of even the most aggressive DDoS barrages. Their costs? Predictable, a steady trickle rather than the sudden, crippling expense of upgrading your in-house defenses. In the ever-shifting digital landscape, the promise of cloud DDoS services offers a shield against lurking threats. But remember, in this vast cyber sprawl, every choice carries its own consequences and, “We have to elevate the priority of security.”
This blog series highlights the new projects, challenges, and problem-solving OCI engineers are facing in the journey to deliver superior cloud products. You can find similar OCI engineering deep dives as part of Behind the Scenes with OCI Engineering series, featuring talented engineers working across Oracle Cloud Infrastructure.
For more information, see the following resources:
