As today’s modern organizations grow and scale, so do the size and complexity of their IT infrastructure. The Oracle Cloud Infrastructure (OCI) Resource Manager is a fully managed Terraform-as-a-service solution that allows you to automate the process of provisioning cloud infrastructure resources on OCI. While Terraform codifies infrastructure provisioning through declarative configuration files, Resource Manager enables you to deploy, share, and manage these configuration and state files across teams and platforms. The service also provides a wide range of benefits, including collaboration, auditability, reliability, and repeatability.
We’re taking this system one step further and are excited to announce the general availability of private access support for Resource Manager. This new feature enables you to access private resources on OCI or on-premises environments connected to an OCI tenancy directly from the Resource Manager. For example, you can now configure a private Compute instance using Terraform’s remote-exec functionality and access Terraform configurations in a private GitHub server.
You no longer need to expose resources in your tenancy to the public internet to access them from the Resource Manager service during resource provisioning. It allows you to reap the benefits of infrastructure-as-code and full infrastructure automation while maintaining a strong security posture. This new feature offers the following capabilities:
-
Connect to and configure nonpublic resources, including Compute and database instances in your private virtual cloud network (VCN) with remote-exec using Resource Manager
-
Retrieve Terraform configurations from private Git servers using Resource Manager
Use the new private access capability from Resource Manager
Let’s walk through step-by-step instructions for two critical use cases made possible with the new Private Access feature.
Access a private resource with remote-exec
The remote-exec provisioner in Terraform invokes a script on a remote resource after creation. You can use it to run a configuration management task or bootstrap into a cluster.
In this example, we create a Resource Manager private endpoint and a stack with a VCN, subnet, and a private instance to connect to from a template in a few clicks.
To try this example, create the following policies to grant a group permission to create, update, move, and delete private endpoints in the tenancy, including the ability to select VCNs and subnets when creating private endpoints. For more details about private endpoint permissions, see orm-private-endpoints.
Allow group <group_name> to manage orm-private-endpoints in tenancy
Allow group <group_name> to use virtual-network-family in tenancy
where any request.operation={’CreatePrivateEndpoint’}"Create a stack from one of the existing Terraform templates that we have curated for you.
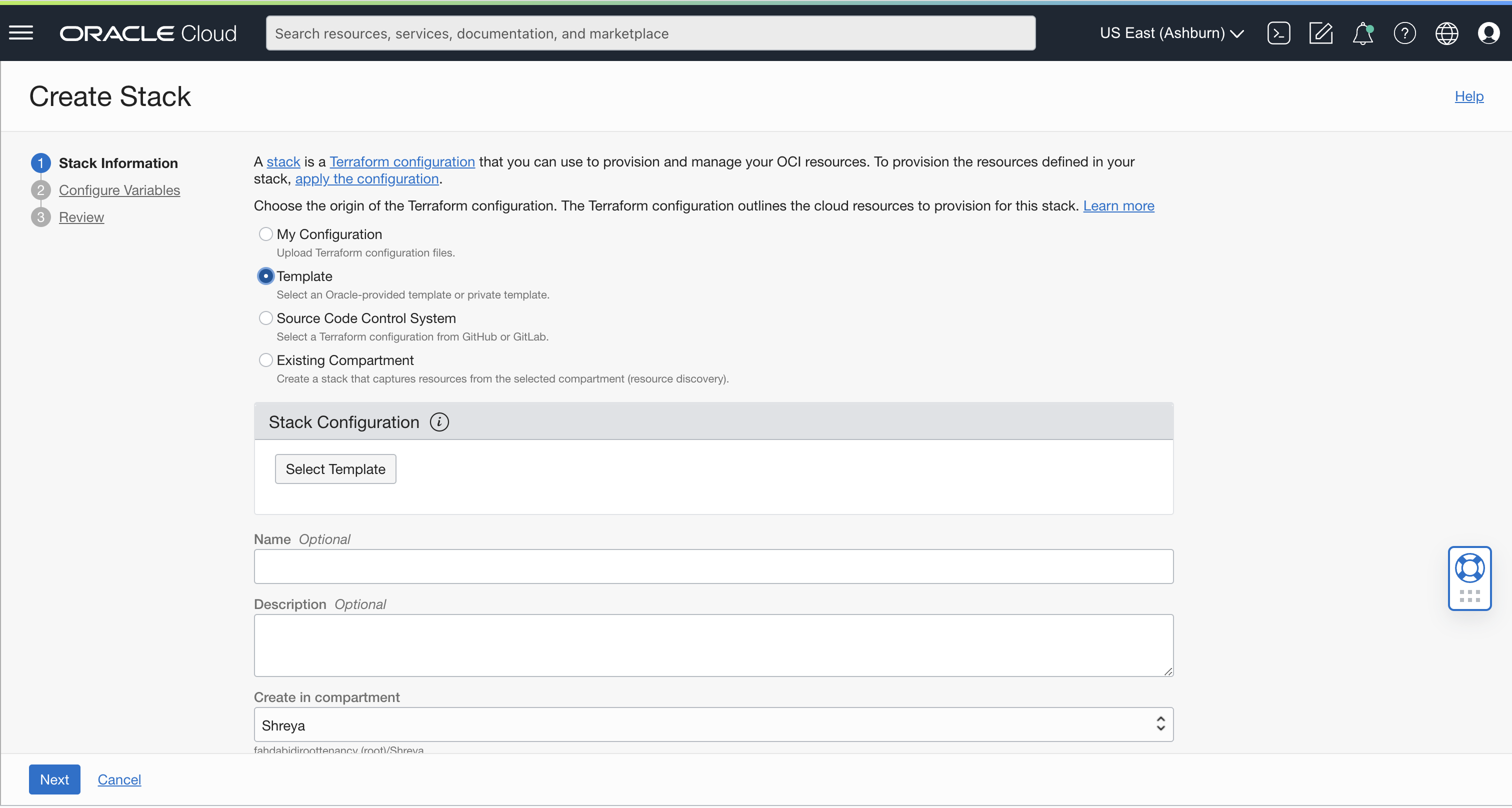
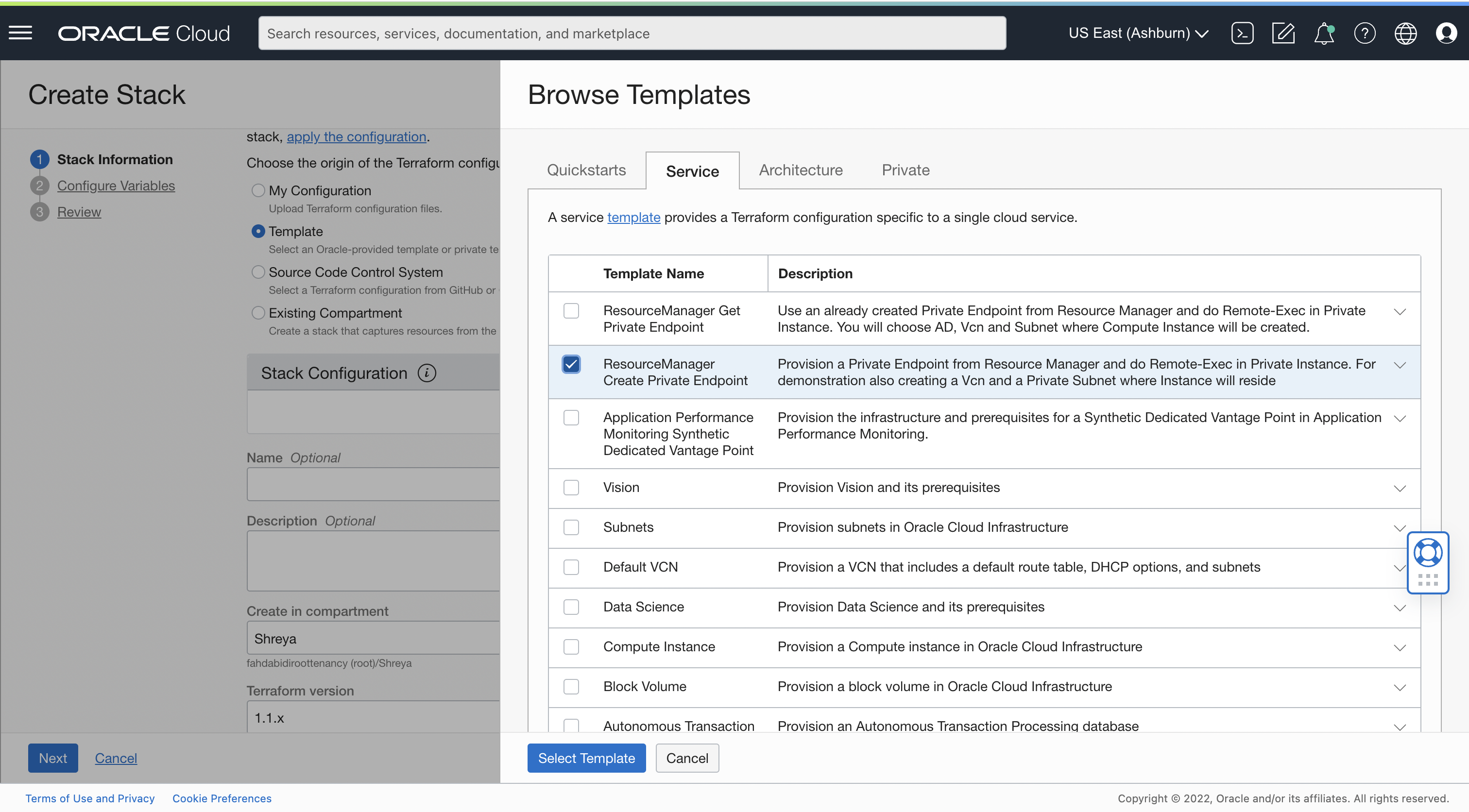
Under the services tab, select the ResourceManager create Private Endpoint template to set up your test infrastructure.
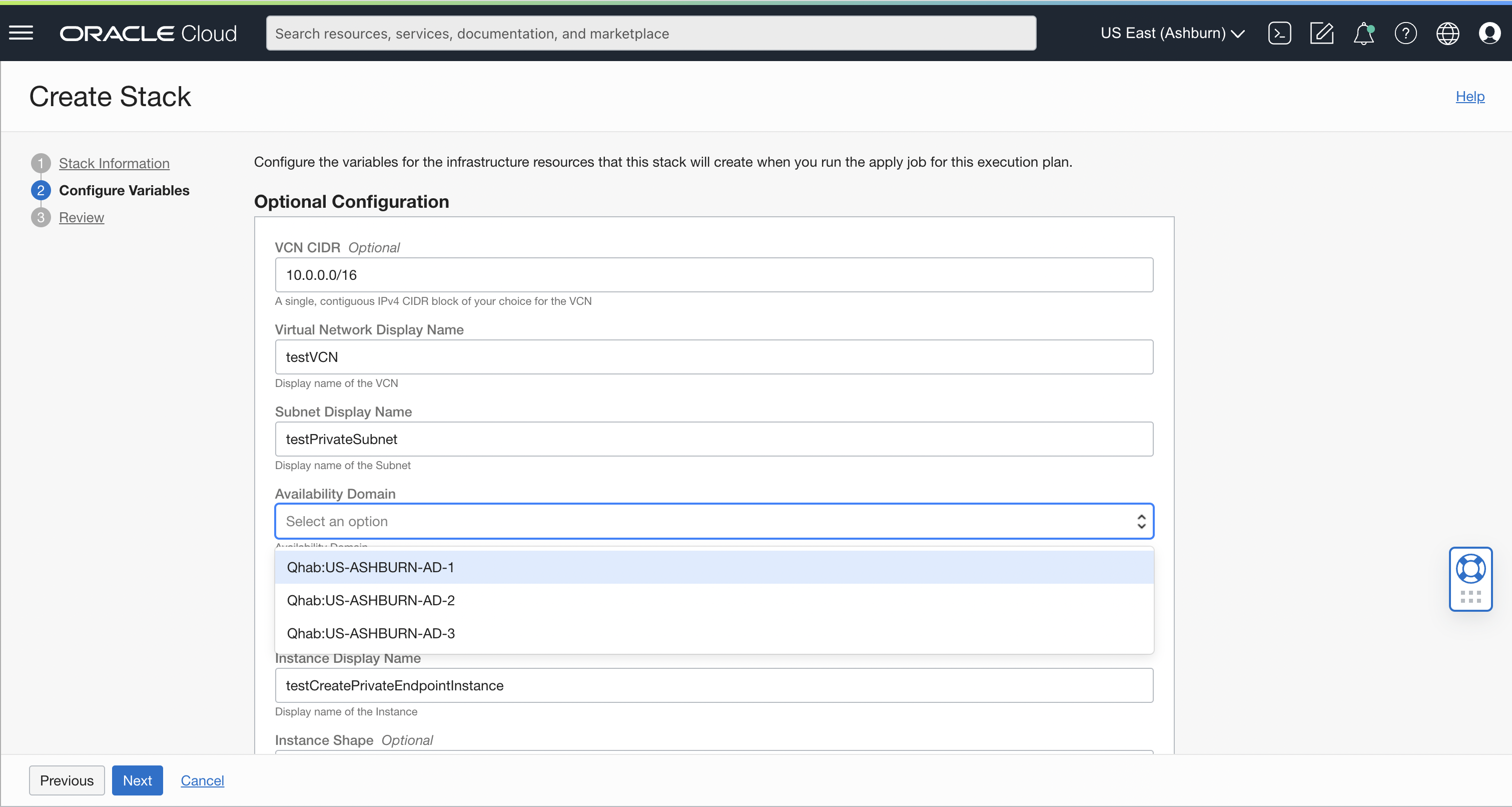
The variables for the infrastructure resources are prepopulated, so choose an availability domain from the menu to go to the next step.
Create the stack and run an apply job on the stack.
This process automatically creates a Resource Manager private endpoint, a VCN with a subnet, and a private Compute instance and connects to it through remote-exec to run. You can view the logs to verify the results.
Retrieve Terraform configurations from a private Git server
Import the SSL certificate associated with your private Git server.
Create a private endpoint and check the option to allow this private endpoint to be used by the configuration source provider.
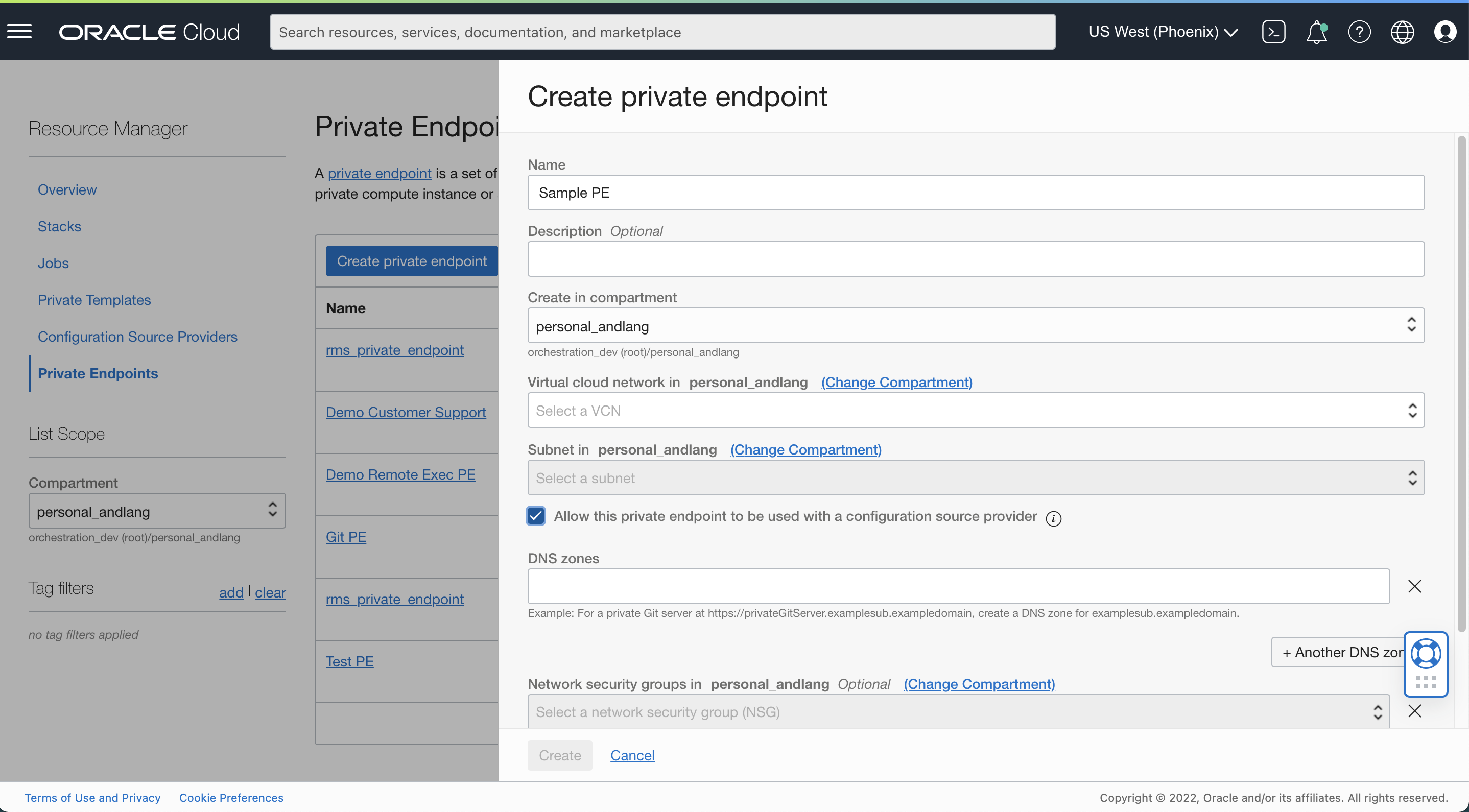
Fill in the required details including the name of the private endpoint, compartment, and the VCN and subnet where the private Git server is hosted.
Select the check box to allow the private endpoint to be used with a configuration source provider.
Fill in the DNS zone. For example, if your private Git server’s URL is https://privateGitServer.examplesub.exampledomain, enter examplesub.exampledomain.
You can also select an appropriate network security group to control traffic if applicable.
Create a configuration source provider that references this private endpoint.
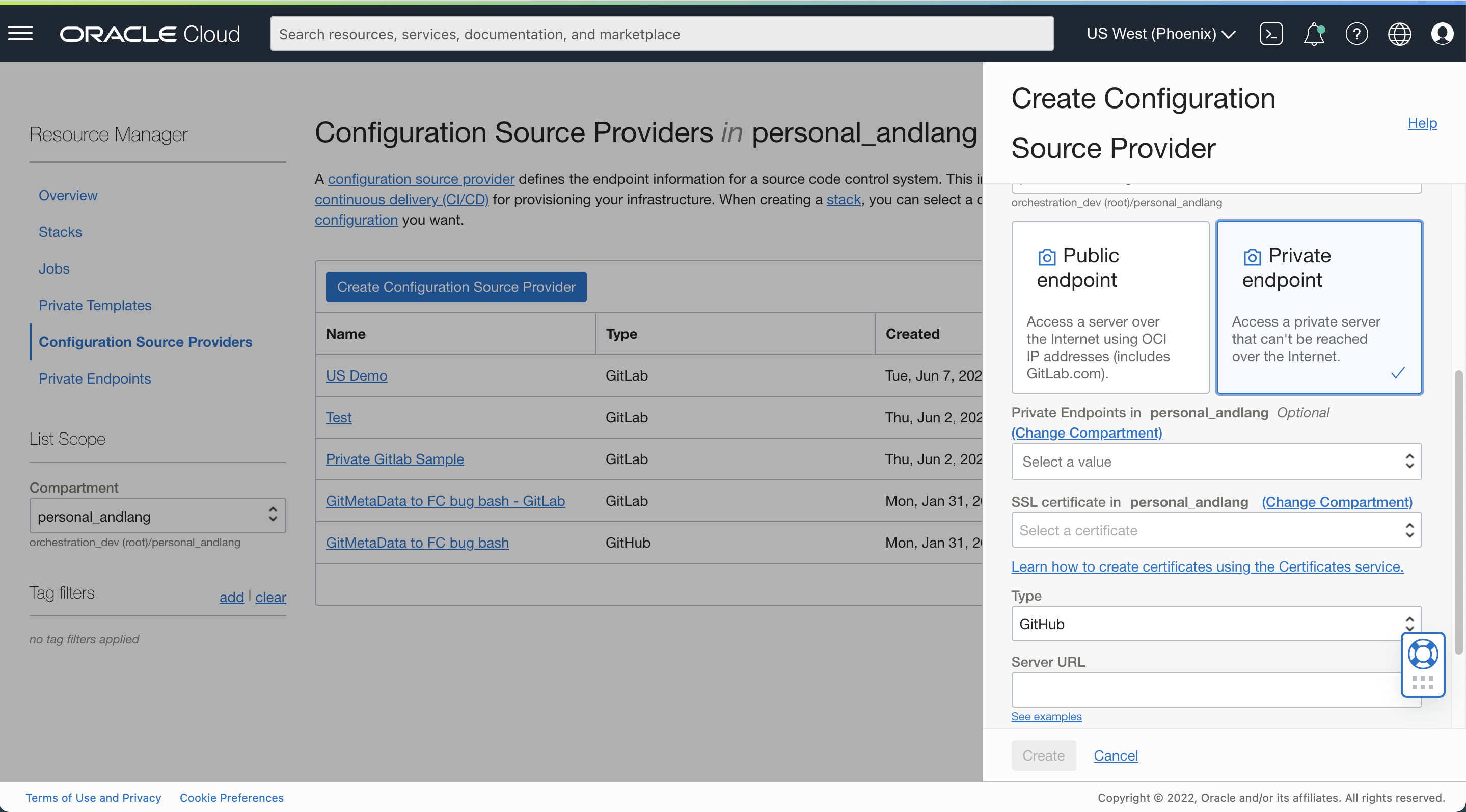
Select the SSL certificate for the private Git Server from the right compartment and the type of the configuration source provider, such as GitHub or GitLab.
Enter the server URL and your private access token.
Create a stack that references this configuration source provider.
Get in touch
We’d love to hear from you! Reach out if you have any questions or feedback.
If you’re new to OCI, we urge you to take advantage of the Oracle Cloud Free Tier to get acquainted.
For more information, see the following resources:
