Today, we’re announcing the general availability of Oracle Cloud Infrastructure (OCI) Site-to-Site VPN over FastConnect private peering in all commercial regions.
Previously, we announced MACsec support for FastConnect Direct 10G and 100G connections. Now, we’re expanding the encryption options available to customers to secure your FastConnect traffic by providing the ability to establish IPsec VPN tunnels to the OCI Site-to-Site VPN managed service over any FastConnect Partner or FastConnect Direct private peering virtual circuit.
What is Site-to-Site VPN over FastConnect?
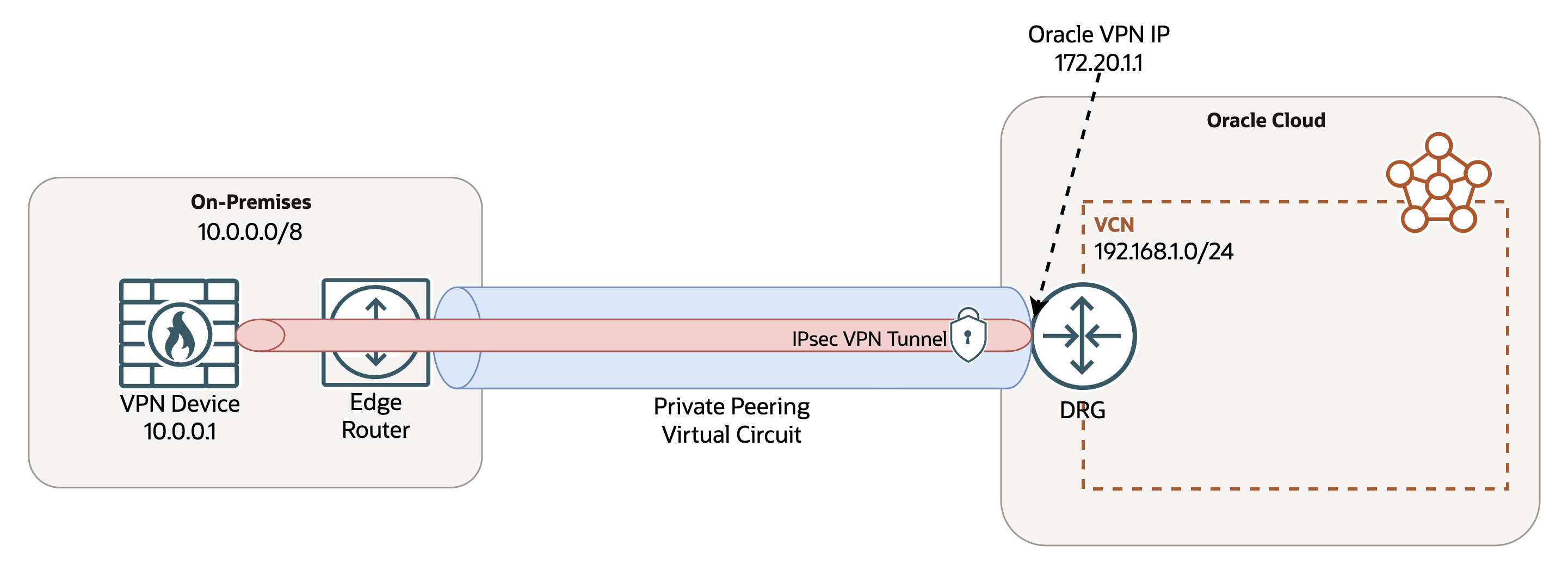
Site-to-site IPsec VPNs are frequently used to secure and protect traffic between on-premises environments and OCI. The OCI Site-to-Site VPN service provides a highly resilient and redundant IPsec VPN managed service, enabling you to encrypt your private traffic before sending it to OCI.
Traditionally, the encrypted IPsec traffic is routed over the internet between the customer premises equipment (CPE) and the OCI Site-to-Site VPN public IP endpoint. OCI is now expanding this functionality by allowing the Site-to-Site VPN endpoint to be any customer-defined, nonoverlapping IP address reachable by a FastConnect private peering virtual circuit. This VPN endpoint is reachable through the dynamic routing gateway (DRG), where your virtual circuit is attached, allowing you to use existing, enhanced DRG functionality to have full control over your routing policy for east-west traffic flows. For more information on the available functionality of an enhanced DRG, refer to the announcement blog.
Benefits of Site-to-Site VPN over FastConnect
The added functionality of Site-to-Site VPN over FastConnect offers the following features and benefits:
- Combined benefits of FastConnect and IPsec: With Site-to-Site VPN over FastConnect, you can take advantage of the benefits of dedicated connectivity provided to you by FastConnect while encrypting your traffic with industry standard IPsec. FastConnect offers a dedicated, private, high bandwidth circuit with consistent and predictable network performance, and Site-to-Site VPN provides data confidentiality, integrity, and authentication for your traffic. Combining the two into a single solution allows you to maintain high-performance connectivity between dependent applications in the cloud with no re-architecture.
- FastConnect partner virtual circuits: FastConnect partners offer optimal performance and connectivity costs savings along with on-demand provisioning. With Site-to-Site VPN over FastConnect, customers who prefer to use FastConnect partners now have an OCI-native encryption solution for both Layer 2 and Layer 3 partner virtual circuits.
- Flexibility: Enable IPsec encryption for any existing or new FastConnect private peering virtual circuits. Configure one or more tunnels over the same virtual circuit and utilize the granular routing policy control offered by the enhanced DRG to control how traffic is routed over these tunnels or unencrypted over the same virtual circuit.
- OCI-managed service: Before the release of Site-to-Site VPN over FastConnect, if you needed IPsec encryption over FastConnect, you were required to either manage a third-party network virtual appliance to terminate IPsec VPN tunnels in your virtual cloud network (VCN) or by combining the two services manually using FastConnect public peering to reach the OCI Site-to-Site VPN public IP endpoint. Now, you can gain all the benefits of a Site-to-Site VPN managed service over FastConnect with simple to use provisioning through the Oracle Cloud Console, API, CLI, and Terraform.
- Compliance: Encrypt your OCI traffic to help address regulatory compliance objectives, such as FIPS, HIPAA, or PCI. Adhere to internal best practice configuration standards with flexibility in tunnel provisioning allowing for network segmentation of traffic to reduce your attack surface area.
How Site-to-Site VPN over FastConnect can secure your traffic
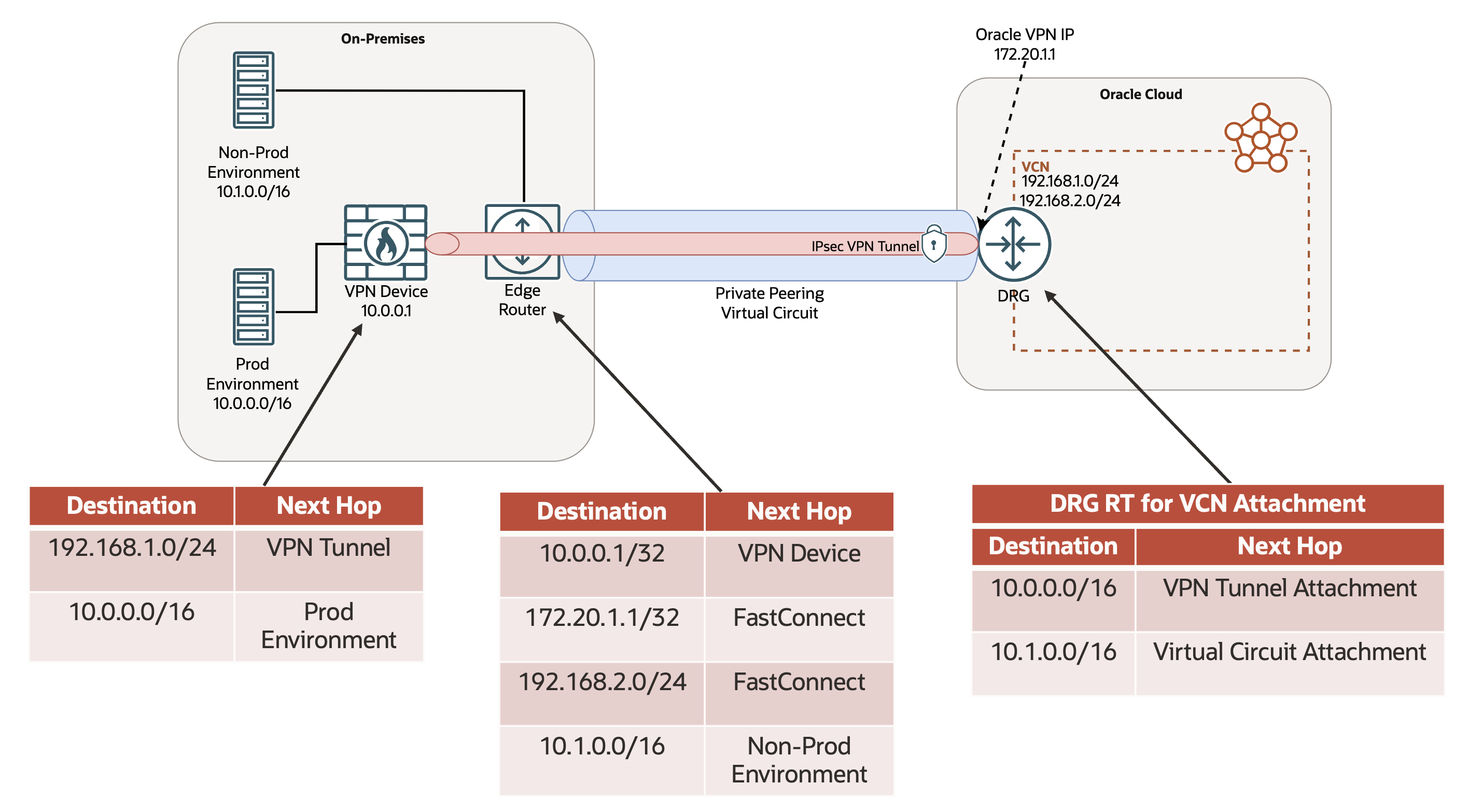
Figure 1. Send unencrypted and encrypted traffic over the same FastConnect private peering virtual circuit.
Send unencrypted and IPsec encrypted traffic over the same FastConnect private peering virtual circuit. Use DRG route tables with route advertisements from your on-premises environment to control whether traffic is sent directly over a virtual circuit unencrypted or route it to a VPN tunnel attachment for encryption before sending the traffic over the same virtual circuit. Figure 1 shows an example where nonproduction traffic is sent from OCI to an on-premises environment unencrypted, while production traffic is first encrypted with IPsec and only then sent by FastConnect from OCI to an on-premises environment.
With granular routing control on the DRG you can also guarantee that no traffic is ever sent unencrypted by forcing all traffic destined for on-premises to route through the VPN tunnel associated with your virtual circuit. You can manually configure your DRG route tables for isolation or enable a simple toggle on an individual virtual circuit to prevent sending of unencrypted traffic.
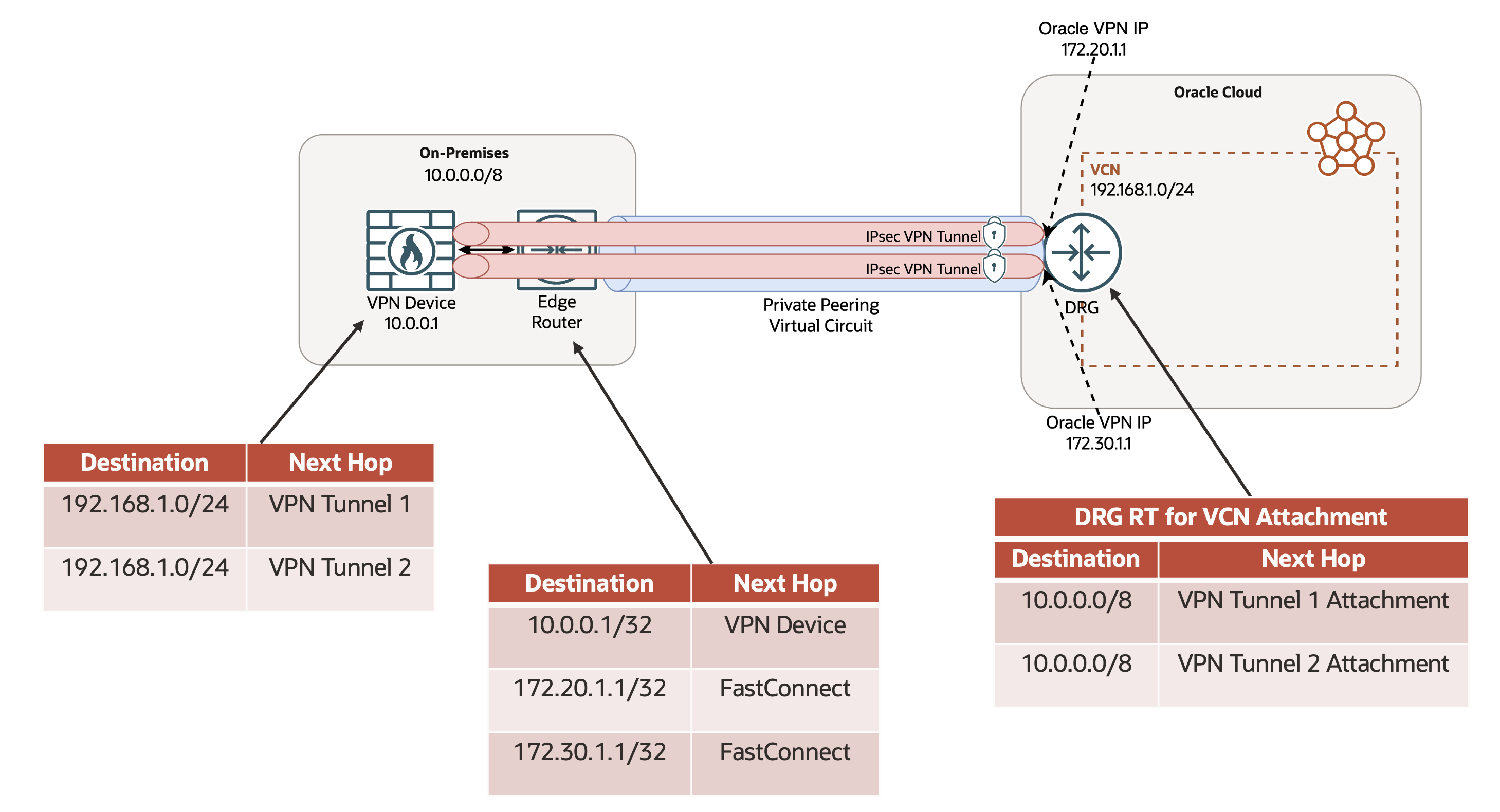
Figure 2. Use ECMP across multiple tunnels associated with the same FastConnect virtual circuit.
Configure multiple tunnels over the same FastConnect private peering virtual circuit. Enable equal-cost multipath (ECMP) to perform active-active, flow-based load balancing across multiple parallel VPN tunnels to achieve greater overall bandwidth for your encrypted traffic. OCI supports ECMP across up to eight redundant VPN tunnels. Depending on the provisioned bandwidth of the underlying virtual circuit, you can increase the number of VPN tunnels to scale your available bandwidth for encrypted traffic of a single virtual circuit, as shown in Figure 2. Alternatively, perform ECMP across VPN tunnels associated with redundant virtual circuits.
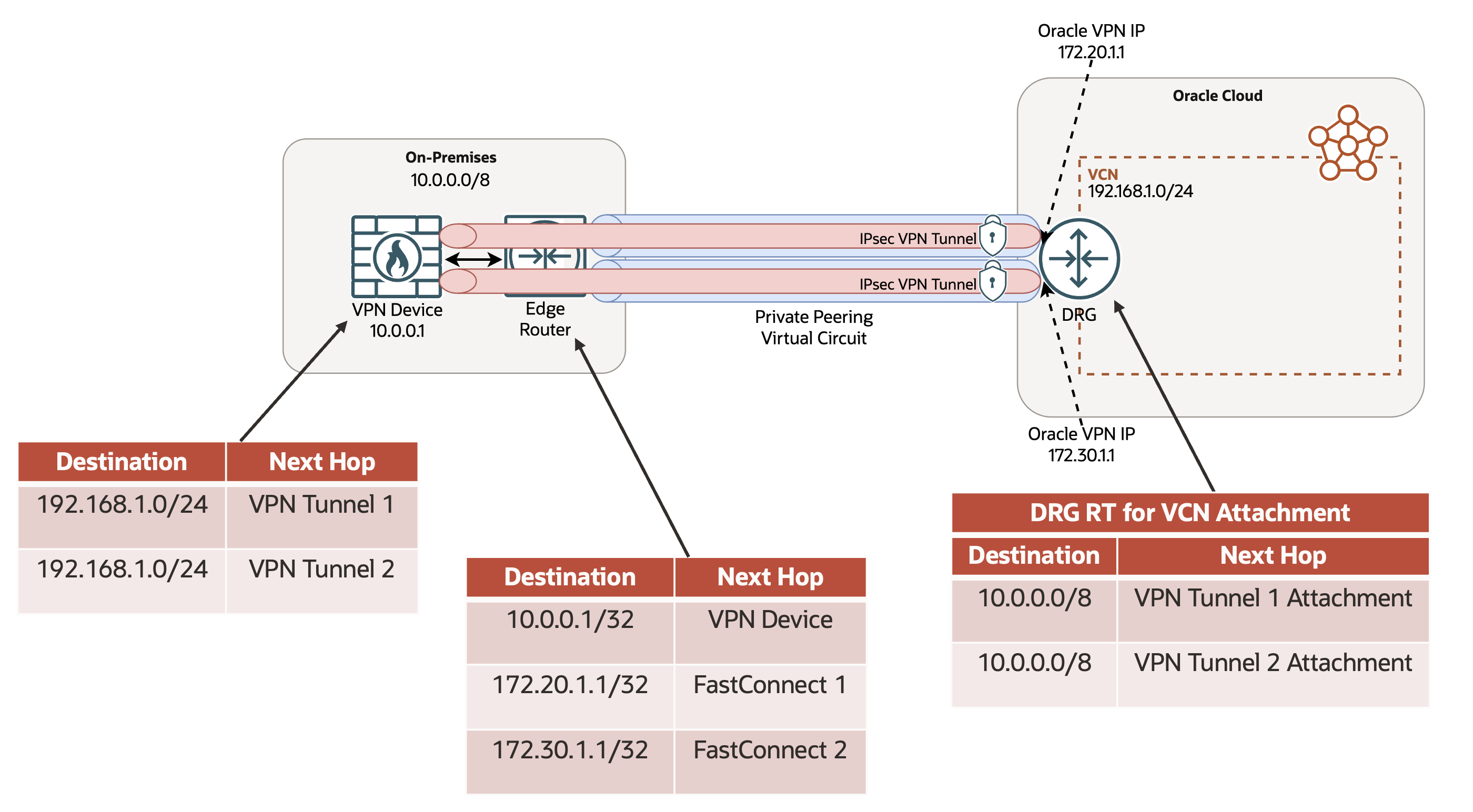
Figure 3. Achieve redundancy across multiple Site-to-Site IPsec VPN tunnels.
Whether you’ve already enabled redundancy between your on-premises environment and OCI with redundant FastConnect virtual circuits or are provisioning new redundant connections, you can achieve redundancy across the IPsec VPN tunnels enabled over these same virtual circuits. Configure your on-premises environment and OCI routing for active-active or active-passive redundancy across Site-to-Site VPN tunnels associated with redundant virtual circuits. Oracle recommends using route-based VPNs with border gateway protocol (BGP) for easier manageability and greater control over your routing policy. Use local preferences or similar BGP attributes to control which tunnel you use when sending traffic to OCI, and AS Path prepending to influence which tunnel OCI uses to send traffic in the return direction. For more details on how to influence route selection between OCI and on-premises environments, see Routing Details for Connections to Your On-Premises Network.
Introducing the DRG loopback attachment
A DRG represents a virtual router in OCI that can attach to VCNs, remote peering connections (RPC), Site-to-Site IPsec VPN tunnels, and FastConnect virtual circuits. DRG route tables and route distributions define routing policies that route your traffic between attachments. You can dynamically import and export routes through these attachments. For example, VCN attachments export VCN subnet or VCN CIDRs, and VPN tunnel and virtual circuit attachments export routes advertised from on-premises.
With Site-to-Site VPN over FastConnect, we’re also introducing a new DRG attachment called a loopback attachment. In the context of Site-to-Site VPN over FastConnect, the loopback attachment logically represents the VPN endpoint for the Site-to-Site VPN service and is always paired with a specific VPN tunnel attachment. The loopback attachment is read-only and uses a unique DRG route table and import distribution, which the system fully manages. Based on customer intent configured during the Site-to-Site VPN over FastConnect provisioning process, the loopback attachment imports routes learned from the associated virtual circuit, representing on-premises BGP route advertisements, and allows for the advertising of the VPN endpoint IP to on-premises as a host route over the BGP session for the same virtual circuit.
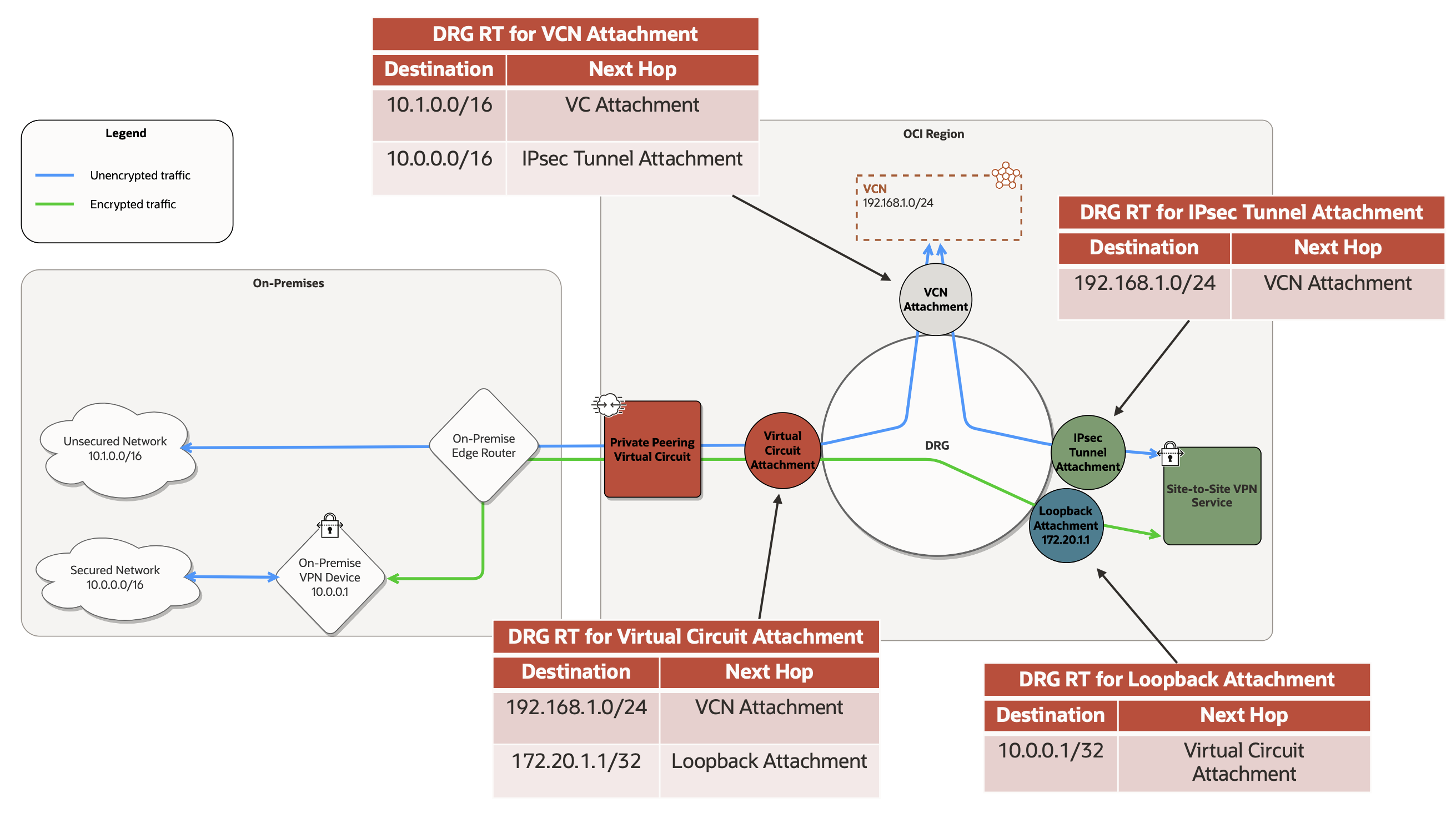
Figure 4. DRG loopback attachment architecture for Site-to-Site VPN over FastConnect.
Figure 4 illustrates the traffic flow for both encrypted and unencrypted traffic over the same virtual circuit. The key concept to understand is that IPsec encrypted traffic is always routed to the loopback attachment when it arrives at the DRG through the virtual circuit attachment. Encrypted IPsec packets are forwarded through the loopback attachment to the Site-to-Site VPN service for decryption. When decrypted, traffic then loops back to the same DRG through the associated IPsec VPN tunnel attachment where another route lookup occurs based on the DRG route table associated with the VPN tunnel attachment before sending traffic to its destination—in this case, a resource in the VCN.
In the reverse direction, unencrypted traffic from a VCN attachment is routed to the VPN tunnel attachment for encryption, no different than with traditional Site-to-Site IPsec VPN over the internet. From there, traffic is encrypted by the Site-to-Site VPN service before being looped back to the same DRG through the associated loopback attachment where another route lookup occurs before routing the encrypted traffic to the appropriate virtual circuit attachment, and ultimately to on-premises. Alternatively, unencrypted traffic can be routed directly from the VCN attachment to the virtual circuit attachment to be sent over the FastConnect as it is, and vice versa.
Want to know more?
Thank you for your interest in Site-to-Site VPN over FastConnect private peering. Site-to-Site VPN over FastConnect is available for all new and existing private peering virtual circuits. It has support for both FastConnect Partner and Direct with any virtual circuit bandwidth setting. For more details on this new feature and the new DRG loopback attachment, refer to FastConnect Security and Setting Up Site-to-Site VPN.
To learn more about any enhanced DRG capabilities, see the DRG documentation.
We encourage you to read more about this feature and provide any product feedback that you may have.
