We’re pleased to announce the general availability of Media Access Control security (MACsec) Encryption for Oracle Cloud Infrastructure (OCI) FastConnect. MACsec is available for 10g and 100g FastConnect direct single connections or link aggregation groups (LAGs) in all commercial and government regions.
With the release of MACsec, FastConnect now natively supports line-rate encryption between the FastConnect edge device and your CPE without concern for the cryptographic overhead associated with other methods of encryption such as IPSec VPNs. With MACsec, customers can secure and protect all their traffic between on-premises and OCI from threats, such as intrusions, eavesdropping, and man-in-the-middle attacks. Customers with use cases that require high throughput for their workloads and strict compliance or security requirements can use MACsec to protect their data as it crosses FastConnect.
MACsec overview
MACsec is an industry standard encryption protocol defined by IEEE 802.1AE. It operates hop-by-hop at Layer 2 and provides authentication and encryption of all traffic on a single network segment between two MACsec enabled hardware devices. As a Layer 2 protocol, MACsec offers protection for IP traffic and other Layer 2 protocols, such as ARP.
Enabling MACsec provides the following benefits to your FastConnect:
-
Line-rate encryption: Take advantage of the full bandwidth capacity of your FastConnect. MACsec encryption is performed in hardware, allowing for reduced bandwidth penalties when encrypting traffic.
-
Data confidentiality: Each frame’s EtherType and payload are fully encrypted, ensuring that data isn’t accessible to unauthorized entities.
-
Data integrity: Provides protection from data being altered during transit.
-
Data origin authentication: Verify that the data received is sent by an authenticated MACsec peer device.
MACsec for OCI FastConnect also supports hitless key rollover for when you’re ready to rotate your encryption keys, preventing loss in communication when keys are updated on both hardware devices along the MACsec-enabled network segment. To ensure no loss in communication during a key rotation, refer to the MACsec documentation for the recommended step-by-step process.
Configuring MACsec
MACsec uses preshared keys exchanged between two hardware devices on a network segment for mutual authentication. MACsec is enabled when the keys are exchanged and verified. The preshared keys are composed of a connectivity association key name (CKN) and a connectivity association key (CAK). The CKN and CAK must match on both devices.
Before enabling MACsec for your FastConnect, configure a vault in OCI Vault service. Vault allows you to centrally manage and secure your encryption keys in OCI and can also store the CKN and CAK. For more information on Vault and how to create a vault with encryption keys, see the Vault documentation.
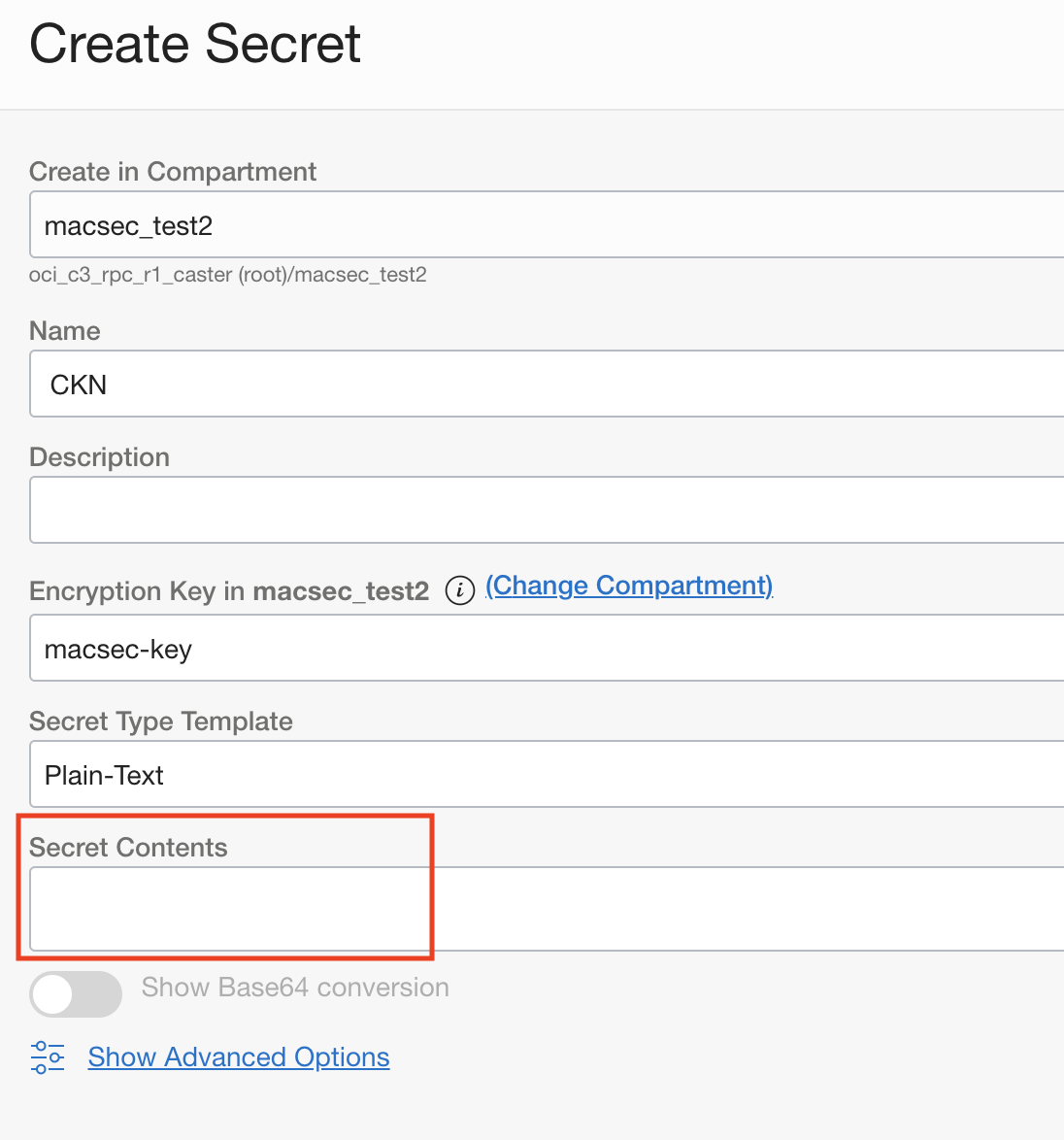
When your Vault has been created with the master encryption key used by your Vault, you can configure the CKN and CAK. Both the CKN and CAK values must be stored in your Vault as separate secrets before being applied to your FastConnect.
-
When creating a secret in your Vault, select the master encryption key, then input the CKN or CAK value under the Secret Contents field. Repeat this process until you have created two secrets, each representing your CKN or CAK.
-
Now that your CKN and CAK values are stored in your Vault, you can either create a FastConnect or edit an existing one to enable MACsec.
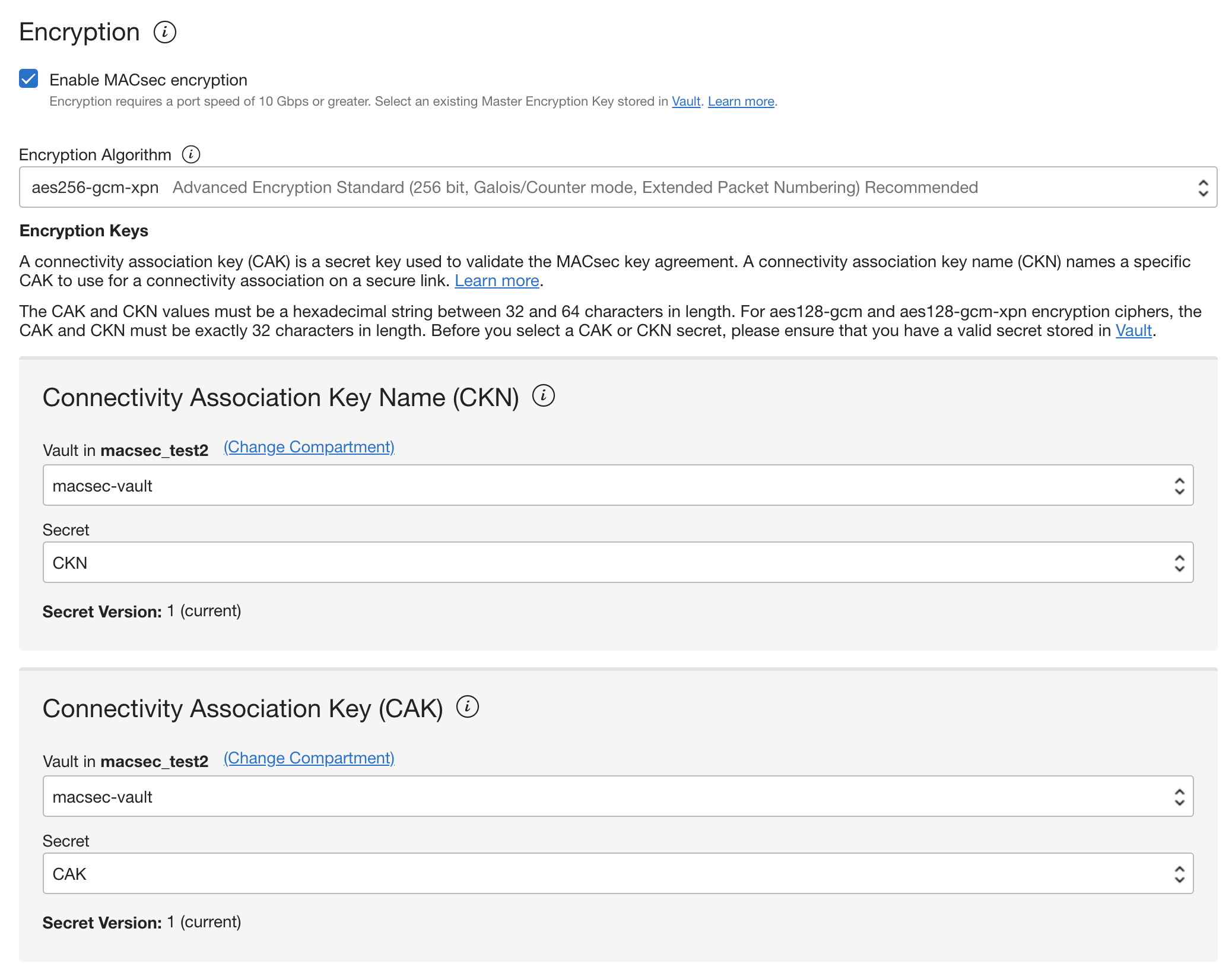
If you create a FastConnect Direct connection, initiate the workflow to create a FastConnect. Enable MACsec by selecting the Enable MACsec encryption check box.
If editing an existing FastConnect, browse to the relevant FastConnect crossconnect or crossconnect group and click the Edit button. If you have an old 110gFastConnect, your crossconnect might not be MACsec capable. In that case, you can see an indicator in the crossconnect information tab under your FastConnect crossconnect, stating that its MACsec encryption status is incapable. In these cases, you need to reprovision FastConnect to enable MACsec.
-
After enabling MACsec encryption, select your encryption algorithm, then the relevant Vault and secret for both your CKN and CAK through the available menus. Save your changes before continuing.
-
After saving your MACsec configuration on the OCI side of your FastConnect, proceed with configuring MACsec on your CPE using the same CKN and CAK values as configured in OCI. When your crossconnect has been activated and you complete your CPE MACsec configuration, you can see MACsec encryption status as “Up” in the OCI Console.

That’s the process for configuring MACsec on your FastConnect Direct connection. For more a more detailed setup process, best practices for hitless key rollover, and required specifications for other MACsec parameters, see the MACsec documentation.
Conclusion
Thank you for your interest in MACsec support for OCI FastConnect. MACsec is supported for all 10g and 100g FastConnect Direct connections. Now that you have enabled MACsec, you can expect that data sent between your on-premises and OCI is secure and protected. In addition, Oracle uses MACsec to secure all backbone connections between OCI regions so that your data is secure when sending traffic across a MACsec enabled FastConnect to not only the local region, but also any remote regions over Oracle Cloud Infrastructure. We encourage you to read more about this feature in the available MACsec documentation and provide any product feedback you have.
