***Updated 04/15/2024***
We’re pleased to announce the general availability of a simplified user experience, policy scale, and performance increases to the Oracle Cloud Infrastructure (OCI) Network Firewall service in all commercial regions. These significant enhancements aim to assist OCI customers in effectively safeguarding their OCI and on-premises infrastructure.
Simplified user experience
Several changes to the policy model now make it easier to build efficient, accurate, and cohesive rules within a policy. The general availability release includes the following changes to the policy model:
- Services and service lists: Services are now decoupled from applications. With this change to the user experience, applications and application lists are independent resources and created separately from services and services lists to make it easier for users to create policy for Layer 3, 4, or 7 services and applications. Services are an independent and reusable resource, matched by an applications layer 3 and layer 4 protocols and ports. Service lists are created using one or more services to permit or restrict traffic to a single service or collection of services. To simplify the creation of security policies, you can combine services that have the same security settings into service lists for a more simplified user experience.
- Applications and application lists: Applications use application identification technology, which use multiple classification mechanisms—application signatures, application protocol decoding, and heuristics—to accurately identify traffic streams on your network where services and services lists identify traffic strictly by layer 4 protocol and port. A wide range of applications across different categories, such as web-browsing, email, file sharing, social media, video streaming, remote desktop, and gaming are now possible. With this announcement, ICMP or ICMPv6 and their type codes are the only two supported applications. Like services, you can reuse applications across different application lists to permit or restrict traffic to a group of applications. Create application lists using one or more applications to permit or restrict traffic to a single application or collection of applications. To simplify the creation of security policies, you can combine applications that have the same security settings into application lists for a more simplified user experience.
- Bulk policy components import: You can now bulk import policy components using a JSON file either through the Console or programmatically using the API. You can import the maximum allowed components for resources in one file up to 5 MB. The Network Firewall service provides a JSON template for each component type that you can download and use to construct your import file. Bulk import policy functionality in a firewall enables administrators to import large sets of firewall rules or configurations in a streamlined way.
- Reorder security and decryption rules: When you create or edit a rule, you can specify its position of the rule in relation to other rules in the policy. With specifying the rule as the first or last rule in the list, you can also specify a custom position for the rule. A custom position lets you set the rule position as being before or after another rule in the list. Easily reordering security and decryption rules of a firewall can offer several benefits and use cases for network administrators and security teams.
- Search for components: Search is an important element of positive user experience when dealing with large scale policy. With this announcement, for each firewall resource listed under policy resources, you can use the newly introduced search field to search for components within each resource by name.
Common use cases and benefits
These changes to simplify the policy model offers the following features and benefits:
- Lift and shift: When transitioning from one firewall vendor to another or upgrading to a new version, bulk import policy simplifies the process of migrating existing firewall rules and configurations. Administrators can import rule sets in bulk, reducing manual effort and ensuring a smooth transition.
- Rule reconciliation: When consolidating multiple firewall rule sets, such as after a merger or acquisition, administrators can use bulk import policy to bring together rules from different sources. This capability enables admins to compare and reconcile rule sets, identify duplicates or conflicts, and create a unified policy.
- Disaster recovery: Bulk import policy helps administrators quickly synchronize firewall rules and configurations from backup files. This ability enables customers reproduce the same firewall rules and configurations within and across their regional deployments.
- Rule templates and template libraries: Administrators can create rule templates or template libraries that encompass frequently used rule configurations. You can import these templates in bulk, saving time and effort when deploying consistent rule sets across multiple firewalls or when adding new rules to existing firewalls.
- Prioritizing rule execution: The OCI Network Firewall processes rules in a sequential order from top to bottom. By being able to easily reorder rules, administrators can prioritize the execution of certain rules over others. For example, you can move critical security rules to the top for faster processing, ensuring that important traffic is inspected and controlled before less critical rules.
- Handling rule conflicts: Reordering rules allows administrators to resolve conflicts that can arise between different rules. Conflicting rules can lead to unintended consequences, such as blocking legitimate traffic or allowing unauthorized access. By rearranging the rules, administrators can place conflicting rules in the appropriate order to ensure that the desired security policies are enforced correctly.
- Implementing compliance requirements: Compliance regulations often require specific security measures, such as enforcing certain encryption protocols or blocking specific traffic types. Reordering firewall rules help administrators with these requirements by ensuring that the necessary rules are positioned and applied in the firewall policy correctly.
- Responding to security threats: In the event of a security incident or emerging threat, administrators might need to react quickly to modify the firewall. Easy reordering capabilities enable swift response by enabling administrators to promptly move critical rules, block specific traffic, or implement more security measures to protect the network from the identified threat.
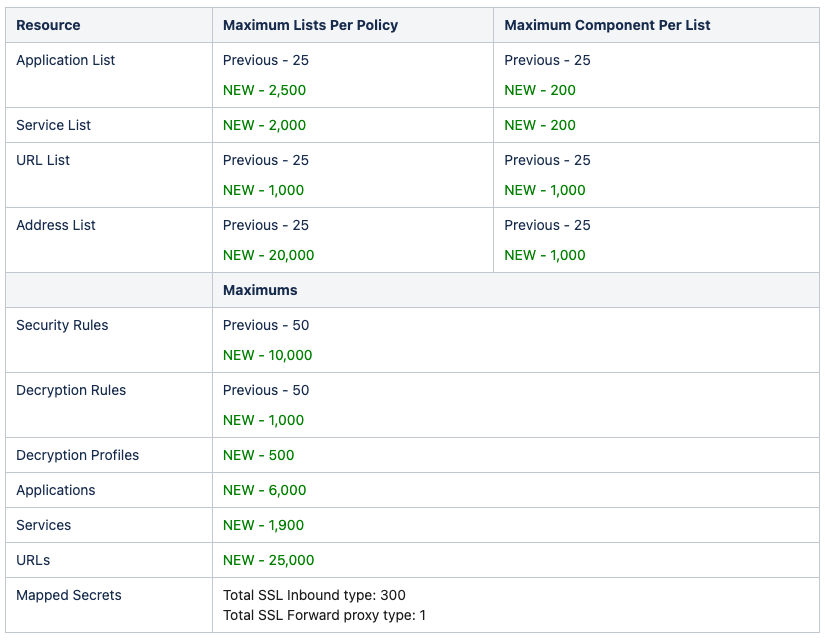
Increased scale limits for policy resources
Enterprise firewall policy scale is a concern for customers who have complex network infrastructures with numerous subnets, multiple data centers, branch offices, and a significant number of network devices. To address these concerns, users can now benefit from a substantial increase in the number of policy resources and components you can have in each associated policy. Table 1 highlights the differences between previous and current policy scale numbers. In some cases, we made more than an 800-times increase in scale. For scale limits across all policy resources and components, see our documentation.
Performance and availability enhancements
With this announcement, customers deploying OCI Network Firewall service can benefit from the following performance enhancements:
- Increased throughput: Throughput is an important metric that represents the amount of data that can be transmitted. You can use it to measure the capacity of the infrastructure to carry the data. Higher throughput results in more data transferred, resulting in faster communication and improved performance. The OCI Network Firewall has a default aggregate throughput of 4 Gbps. The service throughput can now be horizontally scaled by three times to meet the needs of customers who require more capacity by contacting to Oracle Cloud support or your Oracle Account Team (subject to approval)
- Policy update time: Reducing the time it takes for a firewall policy change to become active is critical to operational efficiency and enables you to rapidly respond to emerging threats or changing network requirements. We’re excited to announce a five-times improvement in the time it takes for changes to authored policy changes to become active on the firewall.
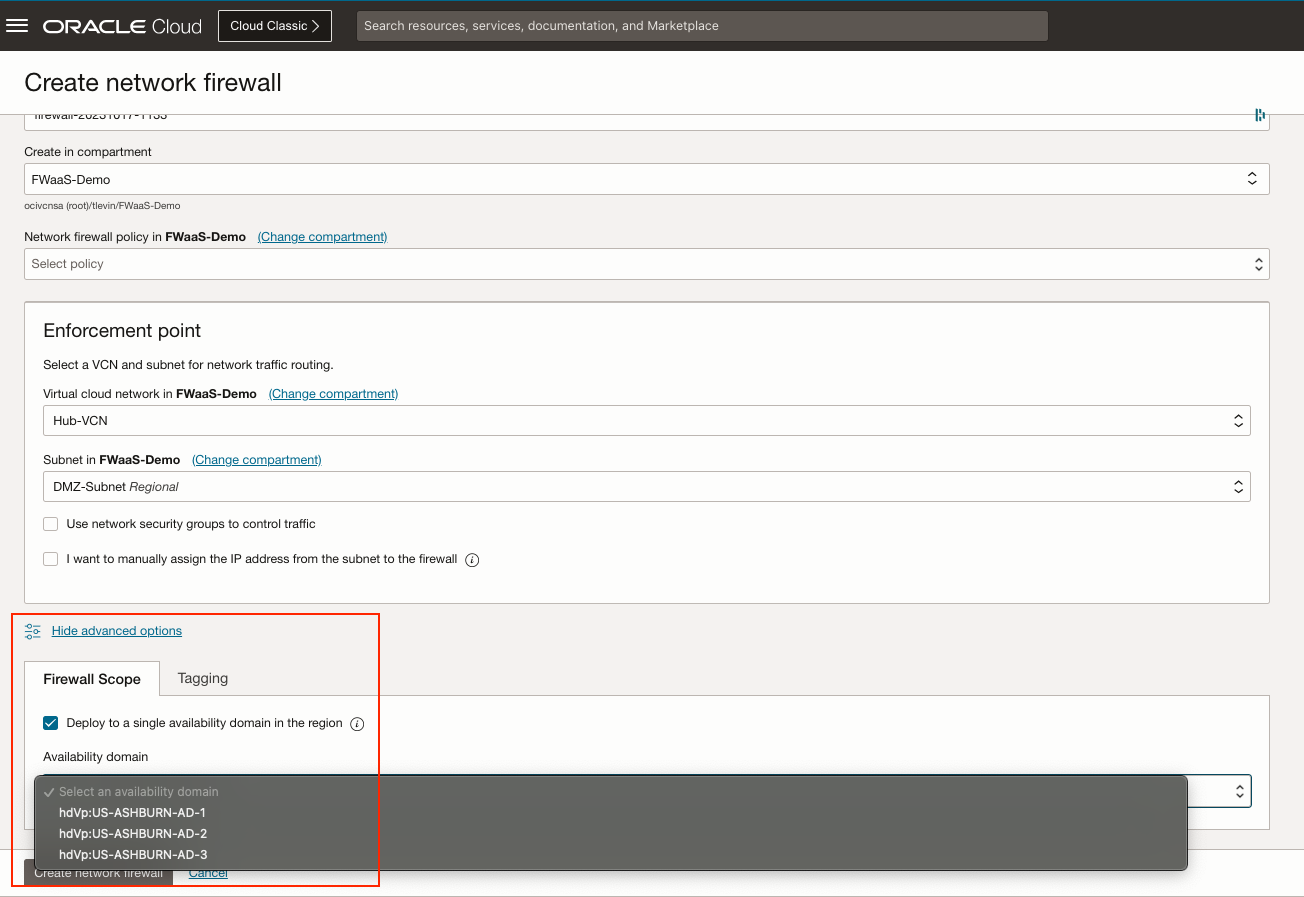
- Regional high availability: High availability is crucial for cloud services to ensure uninterrupted operation, minimize downtime, help to reduce data loss and maintain business continuity. With this announcement, customers now have two deployment types when deploying the OCI Network Firewall in multi-availability domain regions; regional and availability domain-specific. Regional is the recommended and default option for critical applications and ensures continuous protection, even in the event of one or more availability domain failures. Availability domain-specific provides redundancy across one or more fault domains within a single availability domain and is useful for applications that require a combination of high availability and low latency. Customers can gain this benefit without the need for more infrastructure or complex configuration. High availability configuerations can be found in the advanced options section. See the following figure for an example of deploying a OCI Network Firewall with high availability for within a region with multi-availability domains.
Upgrade to the new policy model
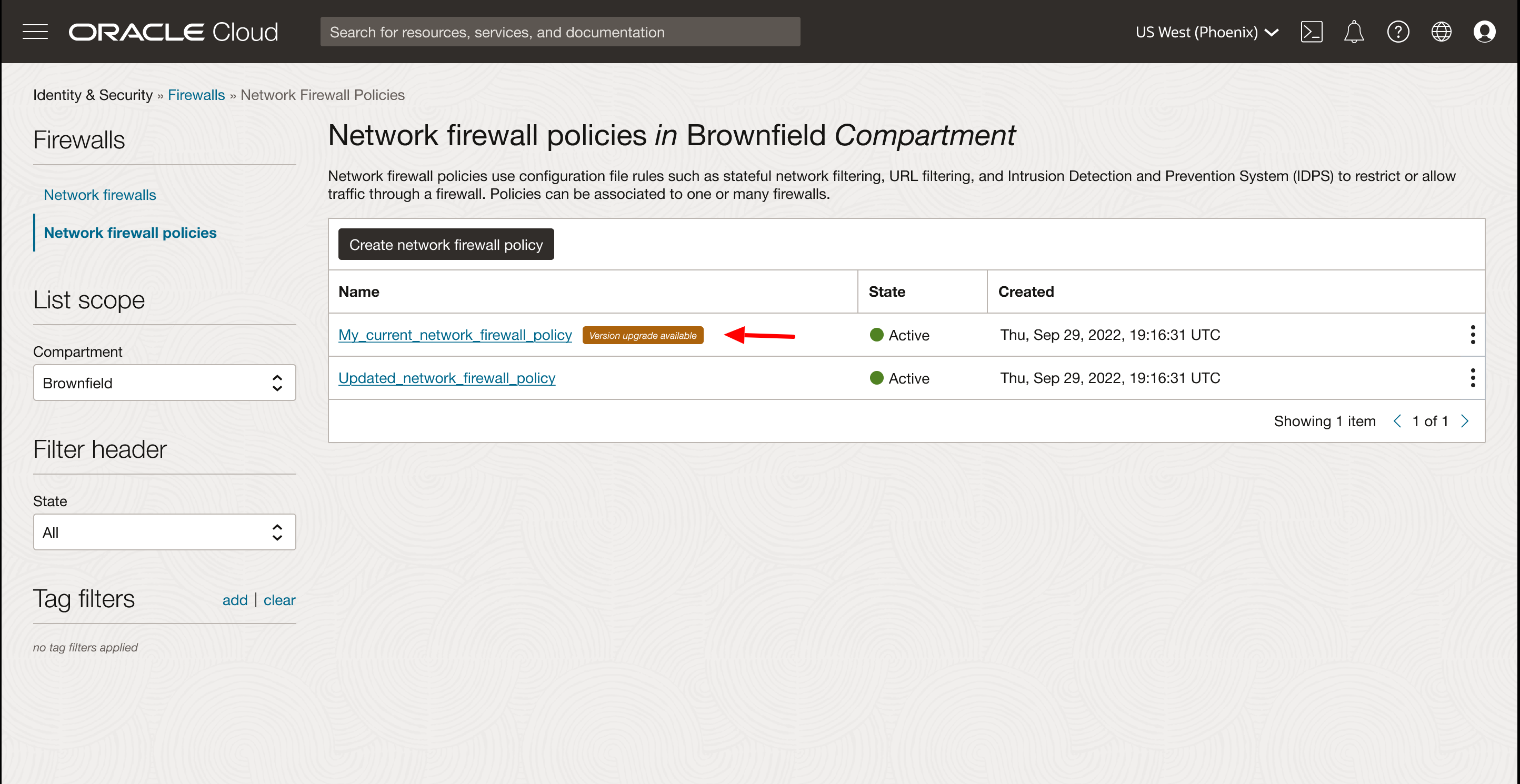
Existing policies can’t benefit from the policy enhancements. You must perform a policy upgrade for all existing policies. Eligible policies for upgrade are indicated by a “Version upgrade available” note next to the policy. The following figure shows an example of an existing policy eligible for upgrade.
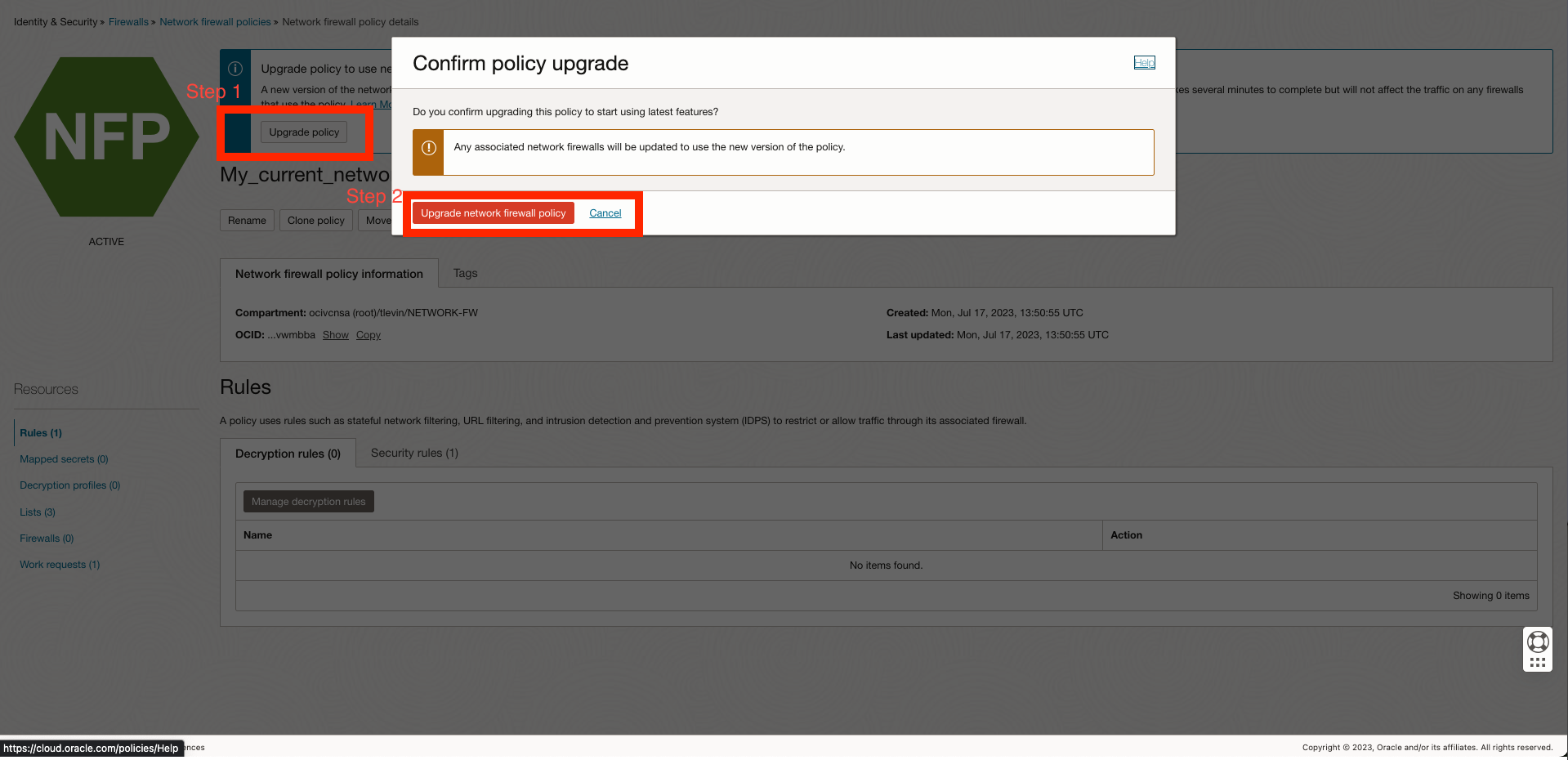
You can perform policy migration with a one-click automated process, which you can initiate by clicking the eligible policy and then the upgrade policy button. The upgrade process takes several minutes to complete but doesn’t affect the traffic on any firewalls that use the policy. Migrating to the new policy model incurs no downtime. However, the policy itself is unavailable for any edits during the migration phase. Figure 3 shows an example of the upgrade policy button.
After a policy is upgraded, applications and application lists resources that contain internet control message protocol (ICMP) and ICMPv6 don’t migrate to services and service lists resources. All other applications and application lists are automatically migrated into services and service lists resources. After a firewall is attached to an upgraded policy, it can no longer make use of a non-upgraded policy. Any new policies created automatically benefit from all the policy enhancements and don’t require an upgrade.
Conclusion
For more details on the OCI Network Firewall, refer to the documentation. We look forward to hearing about how this release improves your user experience and network design. We encourage you to explore these new features and all the enterprise-grade capabilities that Oracle Cloud Infrastructure offers. You can share any product feedback that you have through email to the Virtual Networking group or submit a comment.
For more information, see the following resources:
- Announcing Oracle Cloud Infrastructure Network Firewall
- Defense in Depth, Layering using OCI Network Firewall
- OCI Network Firewall – Concepts and Deployment
- Intro to OCI network firewall | CloudWorld 2022
- OCI Network Firewall Cloud Security Services
- OCI Network Firewall Reference Architecture
- Get Ready for Best-in-Class Security Built for Oracle Cloud Workloads
