Today’s cybersecurity challenges demand cross-functional solutions to achieve an effective level of capability in the domains of identification, protection, detection, response, and recovery. As a result, enterprise security controls represent significant investments for IT departments. Repeatedly, incidents demonstrate that even well-resourced organizations don’t leverage solutions to their fullest potential. As organizations strive to achieve a capability baseline, the concept of control efficacy is increasingly important.
Today’s IT leaders are asking, “How effective is a given solution working, under real world conditions, and what can be done to improve it?” During an incident—whether it’s an attempted network intrusion, a phishing email, or a DDoS attack—simply having a control in place isn’t enough. You must also understand how that control is behaving and what can be done to improve it with hard data.
Internet Intelligence
To that end, Oracle deployed a deep monitoring network of sensors—known as vantage points—to collect publicly available data about internet performance and security events all over the world, with real-time information about degradation, internet routing changes, and network anomalies. Oracle Cloud Infrastructure products, such as Market Performance and IP Troubleshooting, are based on Internet Intelligence.
(red dots: network sensors)
Oracle’s Internet Intelligence Map monitors the volatility of the internet as a whole, based on this telemetry. With more organizations relying on third-party providers for their most critical services, monitoring the collective health of the internet can give users an early warning of impending attacks. Organizations can react and prepare before the danger reaches them.
Data gathered by Oracle’s Edge Network provides valuable insight about border gateway protocol (BGP) route changes and distributed denial-of-service (DDoS) activation worldwide. Oracle can monitor 250 million route updates per day, including where DDoS protection is being activated and when attacks are occurring. We measure the quality, in near real time, of any cloud DDoS protection activation by most cloud-based DDoS vendors. This information can be used to measure the effectiveness of protection solutions.
DDoS Attack Example
Monitoring DDoS activation provides visibility into where attacks are happening, the length of the attack, and the effectiveness of route coverage, in near real-time. A DDoS attack at the end of summer 2018 provides a timely example of the importance of DDoS mitigation telemetry.
The attack, which intermittently affected access to a company’s website and services, was easily identified by Oracle’s vantage points and visible on the Internet Intelligence Map. In this example, as is typical with cloud-based DDoS protection, a cloud-based DDoS protection provider hijacked the organization’s IP blocks so that all the attack traffic was redirected to specialized DDoS scrubbing centers. During the IP block hijack, our security team measured a number of interesting statistics about the route instability, latency jump, and other artifacts caused by the traffic reroute.
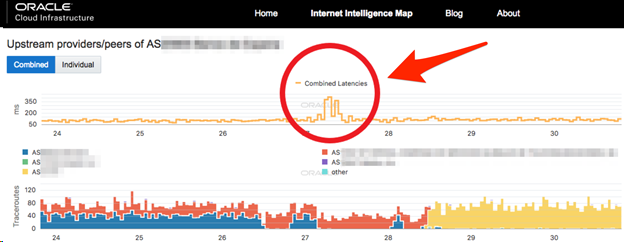
Observing the propagation duration and the completeness of the route change allows for some unique quality measurements. With this example, AS announces two prefixes.
As the following image shows, despite the announcement change, there are still unprotected routes via an ISP, allowing some of the attack traffic through. The DDoS protection provider intercepted the IP blocks under attack, at around 16:00 local time.
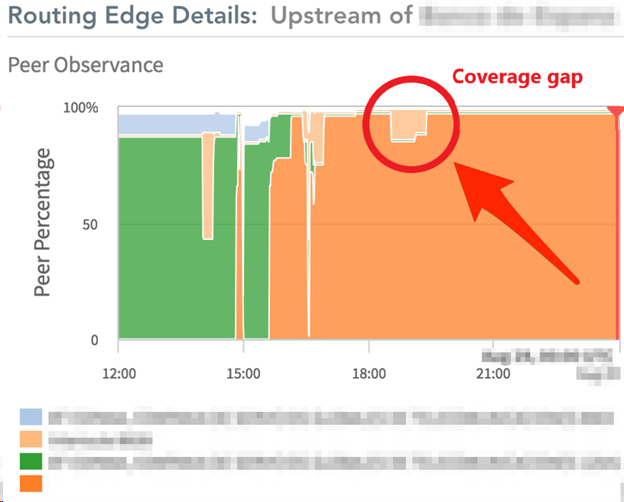
DDoS Attack Leakage
Although the organization’s DDoS protection provider was efficiently mitigating most of the DDoS attack, our tool shows that a small portion of the attack was still going to the organization, for approximately one hour. This is called a DDoS attack leakage.
Despite the fact that a very powerful cloud-based DDoS provider was mitigating the attack, the internet assets of the organization still went offline during this hour because a portion of the attack was still going to its data center.
Additional visibility from trace routes confirms that not all routes were going through the DDoS protection. Two traces from London and Frankfurt confirm that some traffic was still routing through an ISP (instead of going entirely through the cloud-based DDoS mitigation provider).

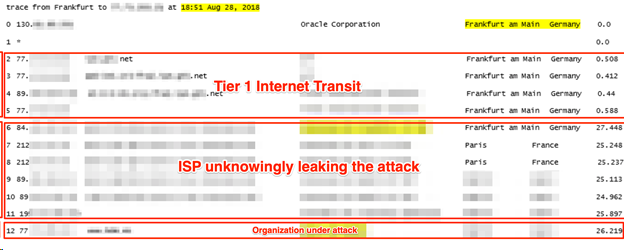
Note: This doesn’t mean that the ISP is knowingly responsible for the DDoS leakage. In fact, quite the contrary. The internet is largely a self-adjusting network, in which traffic is sometimes routed via unexpected core locations. Routing tables need frequent adjustments (made by tier 1 providers and ISPs), and these routing adjustments always take some time to propagate, as was the case here.
Similar to many of our colleagues in the DDoS industry, the Oracle Security team was able to measure and score the quality of the IP hijack and the consistency of the hijack over time. Our results also shows that, indeed, the attack leakage was captured by a low quality score:
| Prefix |
Prefix Owner (under attack) |
AS or prefix owner |
DDoS Provider |
AS of provider |
Handoff Coverage |
Consistent Coverage |
| xxx.xxx.xxx.0/24 |
[organization] |
xxxxx |
[DDoS provider]
|
yyyyy |
64.39 |
95.53
|
These statistical sensors are called the Handoff and Consistent Coverage. A Handoff Coverage of +97 percent typically shows an almost perfect coverage. Less than 90 percent might indicate a DDoS leakage.
The Handoff Coverage impact is shown in the following image:
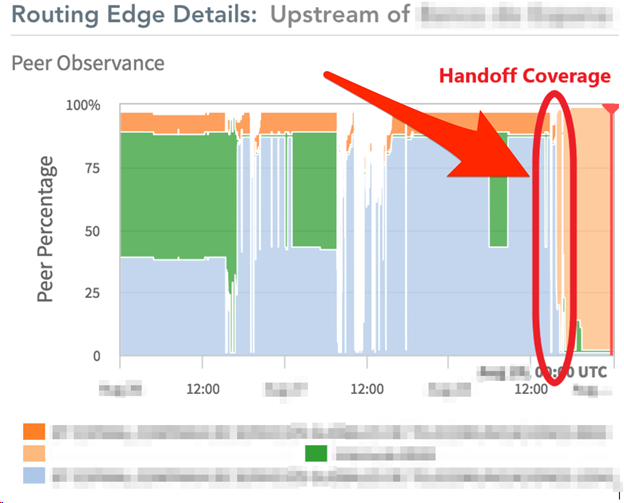
As demonstrated in this example, Handoff Coverage and Consistent Coverage are important parameters that analysts and security staff can use to quantify the effectiveness of a cloud-based DDoS mitigation solutions. In particular, these parameters can help detect the residual attack traffic still leaking back to the organization during the initial handoff, which causes downtime.
Conclusion
DDoS attacks continue to plague organizations across all industries. Mitigation is widely available but applied unevenly. Leakage during mitigation can still have an impact on infrastructure, leading to the loss of mission-critical functions.
When solutions are deployed, tracking their efficacy is critical to ensure that the organization’s security baseline is known and validated. Telemetry gathered from external monitoring, as Oracle provides for DDoS mitigations, in one such example of seeking evidence-based optimization.