Oracle Cloud Infrastructure [10] Audit [1] is included at no cost with each tenancy and records activity across the tenancy for all supported Oracle Cloud Infrastructure services. This information can be retrieved and processed by a tenancy owner for various use cases.
In this blog post I will show how to retrieve audit data for a given time period and several use cases around its consumption.
About Oracle Cloud Infrastructure Audit and use cases
Oracle Cloud Infrastructure Audit [1][2] automatically records calls to all supported Oracle Cloud Infrastructure public API endpoints as log events. This information can then be leveraged for the following purposes:
- Governance
- Industry and regulatory compliance
- Operational and/or security processes
- Risk auditing
Customers can collect logs centrally using log management, or security incident and event management (SIEM) solutions. The following are common use cases:
- Monitoring – for example, to decrease incident response times
- Security – for example, to identify suspicious activity across the tenancy [10], mitigating a variety of risks, breaches and/or any unauthorized events.
- Debugging in Test/Troubleshooting in Production – for example, root cause analysis purposes during incidents.
- Analytics – for example, analyzing and identifying patterns for various events occurring in a tenancy.
- Machine learning – for example, use as training data.
By default, Oracle Cloud Infrastructure Audit is in recording mode and cannot be turned off. The default retention period 90 days, but as a best practice, customers may change the policy to the maximum retention.
Retrieving Audit events
In order to make use of audit events, the first step is to retrieve and store audit events. Let’s take a look into the ways in which an Audit event can be retrieved:
- Oracle Cloud Infrastructure Web Console – With user credentials, customers can log in to the web console to access the Audit service. For example, when customers are trying the service for the first time; this helps with a first look into a handful of events.
- Oracle Cloud Infrastructure CLI [3] – With CLI customers can make use of the service to retrieve events for a defined compartment and for a region specified as per CLI’s config. The CLI command would look like:
#oci audit event list –start-time $start-time –end-time $end-time –compartment-id $compartment-id - Oracle Cloud Infrastructure SDKs [4][5] – With SDKs customers can choose a supported language and retrieve Audit events with the ListEvents API [6]. For production use cases, this would be the best suitable option.
For this blog post, I will use the Oracle Cloud Infrastructure Python SDK [5]; I will make use of retrieve_audit_events.py [9]
About the retrieve_audit_events.py demo script
As mentioned, let’s use the python script, which retrieves logs for a tenancy [10] for a given time period across:
- All regions, including the regions that may be added in future
- All compartments, including the root compartment
Pre-requisites
Before you make use of this demo script, it is important to understand its pre-requisites:
-
Installation of Oracle Cloud Infrastructure Python SDK [4]
-
IAM Permissions [7][8]- READ permissions for audit-events for a user used above to execute the demo script, The IAM policy would look like:
Allow group <GroupName> to READ audit-events in tenancy -
Configuration of Python SDK [5] – The following are the important parameters for the local configuration:
- User OCID
-
RSA private key in PEM format
-
Its fingerprint
-
Tenancy OCID
Recommendations when using the demo script retrieve_audit_events.py
The following are a few recommendations while using this demo script:
- This demo script works on a single tenancy [10] and it is not production-ready, so customers should take necessary steps to run the script across all their existing tenancies.
- The results should be stored, and may be processed for downstream SIEM tools before further consumption.
- The demo script may take a few minutes to complete execution. The time it takes to execute the script is directly dependent on the following:
- Number of compartments under the tenancy
-
Number of resources for each compartment for each region
-
Number of updates to the Oracle Cloud Infrastructure environment (e.g. start/stop/termination of instances) – Write events
-
The method in which you regularly query metadata (e.g. using console vs CLI) – Read events
-
The time span for which the Audit Events are queried (e.g. 20 minutes, 1 hr, 365days)
Example use case and analysis of events
Let’s focus on a use case where we want to find out how many changes were made to our tenancy across a month.
For this use case, we want to retrieve all the audit events and filter write operations such as Create/Modify/Delete operations on Oracle Cloud Infrastructure resources, which can be done by eliminating all the list/get operations required to retrieve the metadata.
For our test tenancy, consisting of 13 compartments, Audit entries were retrieved for a time span of one month. The following were the timestamps:
start_time=‘2017-11-05T00:00:00 GMT’ to end_time=‘2017-12-05T00:00:00GMT’
The demo script took about 6 minutes to execute fully on a VM.Standard1.8 with Ubuntu 16.04.
The following is a table that shows the number of write events vs all the events throughout the tenancy.
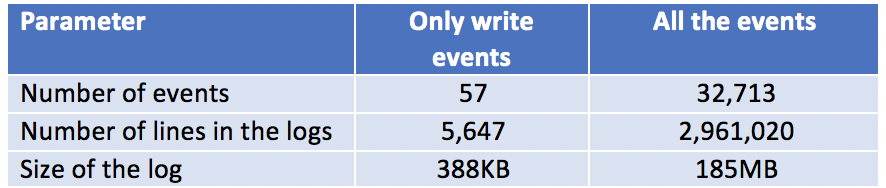
This analysis gives us an insight into the amount and the type of data being retrieved. Understanding this is important for processing data for respective use cases. For example, if we wish to track changes on specific cloud resources, such as an instance, then focusing only on write events will be required.
Conclusion
In this blog, we learned about Oracle Cloud Infrastructure Audit and how it can be leveraged to retrieve all activities that occurred across a tenancy. After each retrieval, the results can be indexed into a SIEM tool for further processing.
References
- OCI Audit Introduction – https://cloud.oracle.com/en_US/governance/audit/features
- OCI Audit Overview – https://docs.us-phoenix-1.oraclecloud.com/Content/Audit/Concepts/auditoverview.htm
- OCI CLI – https://docs.us-phoenix-1.oraclecloud.com/Content/API/SDKDocs/cliconfigure.htm
- OCI SDK Configuration – https://docs.us-phoenix-1.oraclecloud.com/Content/API/Concepts/sdkconfig.htm
- OCI Python SDK – https://oracle-cloud-infrastructure-python-sdk.readthedocs.io/en/latest/api/index.html
- ListEvents API – https://docs.us-phoenix-1.oraclecloud.com/api/#/en/audit/20160918/AuditEvent/ListEvents
- Introduction to OCI IAM – https://cloud.oracle.com/en_US/governance/identity/features
- IAM concepts – https://docs.us-phoenix-1.oraclecloud.com/Content/Identity/Concepts/overview.htm
- RetrieveAuditEvents.py – https://github.com/oracle/oci-python-sdk/blob/master/examples/retrieve_audit_events.py
- OCI Key Concepts – https://docs.us-phoenix-1.oraclecloud.com/Content/GSG/Concepts/concepts.htm