This post was written by a guest contributor, Henrik Rosendahl, Head of Business Development at NeuVector.
As part of our continuing commitment to open standards and supporting a broad and varied ecosystem, we’re pleased to announce that NeuVector has extended its Lifecycle Container Security Platform support to Oracle Cloud Container Engine for Kubernetes (OKE). NeuVector is a Kubernetes security platform that delivers end-to-end protection from DevOps vulnerability management to next-generation runtime security with the only Layer 7 container firewall. Customers can now protect sensitive data and defend against attacks when running containers on OKE.
The NeuVector solution extends the built-in security of Kubernetes and OKE to provide security integrated into the DevOps CI/CD pipeline. It also provides defense-in-depth during runtime for production container deployments.
Deploying NeuVector on OKE
NeuVector is a true cloud-native, container-based product and is deployed and managed using the same tools and processes as cloud-native applications. NeuVector is also tightly integrated into the Kubernetes and OKE environment, enabling security automation during all phases.
First, you need an OKE cluster running. Creating a new Kubernetes cluster is simple on Oracle Cloud.
Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE) provides a CLI and Console (browser-based interface) for creating and managing Kubernetes clusters. You can set up OKE to automatically provision and launch Kubernetes clusters based on a custom configuration or through a quick cluster option in the Console.
When OKE launches a cluster, it creates master and worker nodes in a node pool along with all of the network resources needed for that cluster, including a virtual cloud network (VCN).
Because OKE is a managed service, you can easily modify your cluster and download your cluster’s kubeconfig file to perform additional management tasks with kubectl.
Next, you deploy the NeuVector security containers by using either the NeuVector Helm chart on GitHub, or native kubectl commands. Full instructions are provided in the NeuVector documentation. For example:
Create the namespace:
$ kubectl create namespace neuvector
Add the role bindings:
$ kubectl create clusterrole neuvector-binding-app –verb=get,list,watch, \
update –resource=nodes,pods,services
$ kubectl create clusterrole neuvector-binding-rbac –verb=get,list,watch \
–resource=rolebindings.rbac.authorization.k8s.io,roles.rbac.authorization.k8s.io, \ clusterrolebindings.rbac.authorization.k8s.io,clusterroles.rbac.authorization.k8s.io
$ kubectl create clusterrolebinding neuvector-binding-app \
–clusterrole=neuvector-binding-app –serviceaccount=neuvector:default
$ kubectl create clusterrolebinding neuvector-binding-rbac \
–clusterrole=neuvector-binding-rbac –serviceaccount=neuvector:default
$ kubectl create clusterrole neuvector-binding-admission \
–verb=get,list,watch,create,update,delete \
–resource=validatingwebhookconfigurations,mutatingwebhookconfigurations
$ kubectl create clusterrolebinding neuvector-binding-admission \
–clusterrole=neuvector-binding-admission –serviceaccount=neuvector:default
Copy the sample yaml, change NodePort to LoadBalancer, then deploy:
$ kubectl create -f neuvector.yaml
That’s it! The required services and pods are deployed on your OKE cluster. You can see the NeuVector controllers, enforcers, and manager containers.
NAME READY STATUS RESTARTS AGE
neuvector-controller-pod-f98bfc954-4965x 1/1 Running 6 26d
neuvector-controller-pod-f98bfc954-9vjz8 1/1 Running 4 21d
neuvector-controller-pod-f98bfc954-rrtx4 1/1 Running 5 21d
neuvector-enforcer-pod-4dgkg 1/1 Running 4 26d
neuvector-enforcer-pod-f9l5b 1/1 Running 2 12d
neuvector-manager-pod-b45d7999c-dj55r 1/1 Running 6 21d
You can now access the NeuVector browser console on port 8443 using the public IP address of the load balancer. Find this for the webui service as follows:
$ kubectl get svc -n neuvector
After logging in, apply your license file. You will see that NeuVector has discovered all containers and hosts in the cluster, and is starting to learn the behavior of them to create network, process, and file access rules. In addition, NeuVector has already started monitoring containers and hosts for known suspicious network threats and unusual processes and file system activity.
Integrate NeuVector Vulnerability Scanning into the CI/CD Pipeline
To integrate NeuVector into the build process, use the Jenkins plug-in, REST API, CircleCI ORB, or other supported integrations to scan images during the build phase.
Registry scanning is also supported, so images in specific repositories can be scanned for vulnerabilities before deployment. After images are scanned, admission control rules should be created to prevent vulnerable or unauthorized images from being deployed. NeuVector integrates with the Kubernetes admission control webhook running on the OKE cluster to enforcer these rules.
Runtime Protection Without Compromise
NeuVector alerts on and, if necessary, blocks any unauthorized network connections, process starts, or file activity during runtime. It also scans running containers and hosts for vulnerabilities.
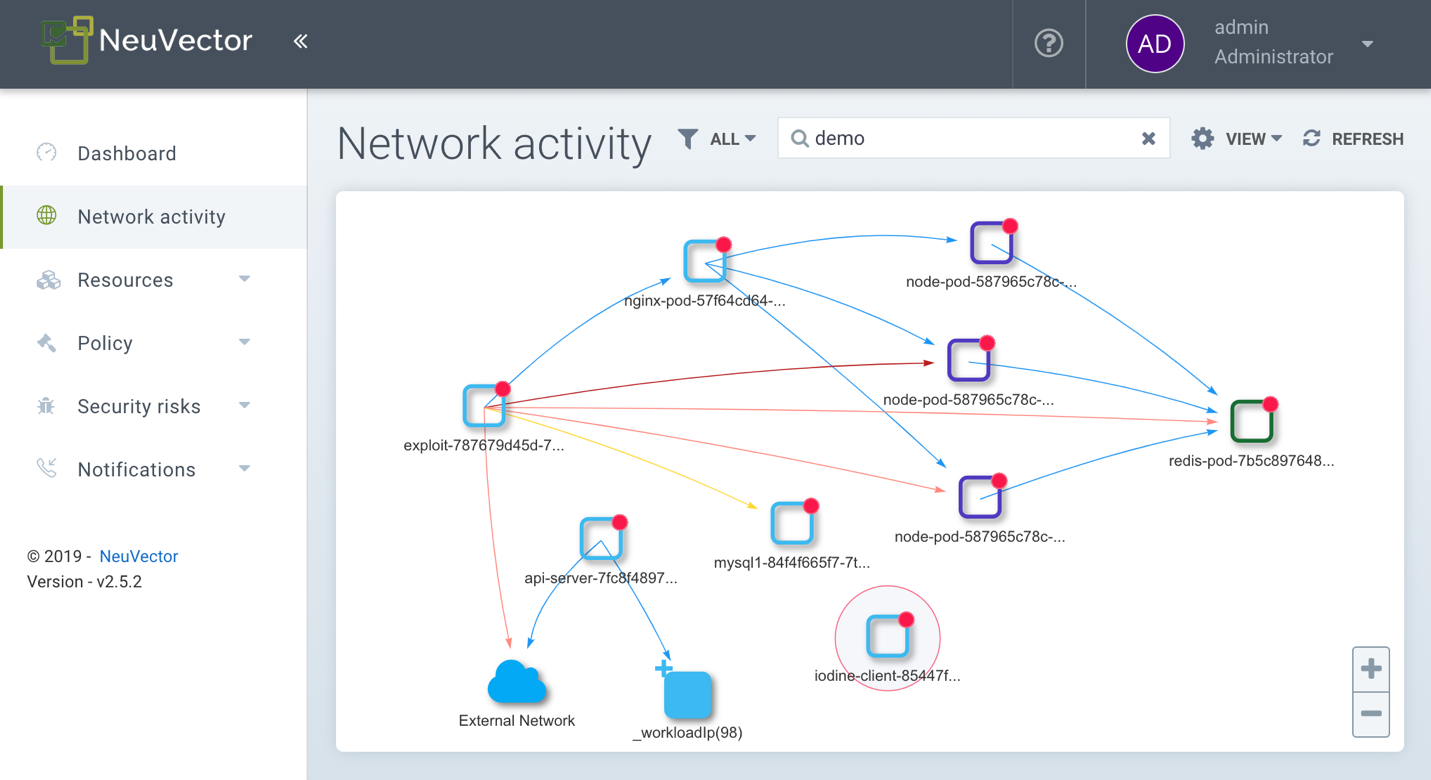
Ultimately, NeuVector helps prevent attacks on containers and data stealing exfiltration with its unique Layer 7 container firewall. This provides deep packet inspection (DPI) to verify proper application protocol usage and detect embedded network attacks, for all east-west (pod to pod) connections as well as north-south (ingress and egress) access. Attempts to exploit a vulnerability, perform a zero-day attack, or conduct insider attacks are detected by the combination of network inspection, process monitoring, and file-system monitoring. With Oracle Cloud OKE and NeuVector, enterprises can deploy Kubernetes with confidence.
Want to experience NeuVector on OKE for yourself? Sign up for an OCI trial account, and then contact info@neuvector.com to start a trial.
