We are pleased to announce the release of the Oracle Cloud Infrastructure Web Application Firewall (WAF) service for Oracle Cloud Infrastructure workloads and multicloud web applications. Oracle Cloud Infrastructure WAF is an enterprise-grade, cloud-based security solution designed to protect internet-facing web applications from malicious cyberattacks and bot scrapers. In the 2018 Oracle and KPMG Cloud Threat Report, 51 percent of respondents indicated that a web application firewall was a top priority in protecting malicious access to an organization’s sensitive and critical data.
Web applications are the heart of today’s digital businesses, and they are under constant threat from cyberattacks by bad actors who want to compromise your site. A bad actor who gains access to your web application server can steal data, use it as a platform to propagate malicious software to your customers, and damage the brand reputation of your business. It’s no wonder that security is a top concern for all businesses moving their workloads to the cloud, and a web application firewall is an absolute requirement for today’s digital business. Many businesses won’t even relocate critical applications, data, and services to the cloud without a web application firewall. Oracle Cloud Infrastructure WAF is here to provide the protection and peace of mind that you require for your Oracle Cloud Infrastructure, on-premises, and multicloud workloads.
The WAF service uses a layered approach to protect web applications against cyberattacks. This release includes over 250 predefined Open Web Access Security Project (OWASP), application, and compliance-specific rules. WAF also provides aggregated threat intelligence from multiple sources, including Webroot BrightCloud®. Administrators can add their own access controls based on geolocation, whitelisted and blacklisted IP addresses, and HTTP URL and Header characteristics. Bot management provides a more advanced set of challenges, including JavaScript acceptance, CAPTCHA, device fingerprinting, and human interaction algorithms. Onboarding your applications to the WAF service will protect against layer 7 distributed denial-of-service (DDoS) attacks.
How WAF Works
Oracle Cloud Infrastructure WAF acts as a reverse proxy that inspects all traffic flows or requests before they arrive at the origin web application. It also inspects any request going from the web application server to the end user.
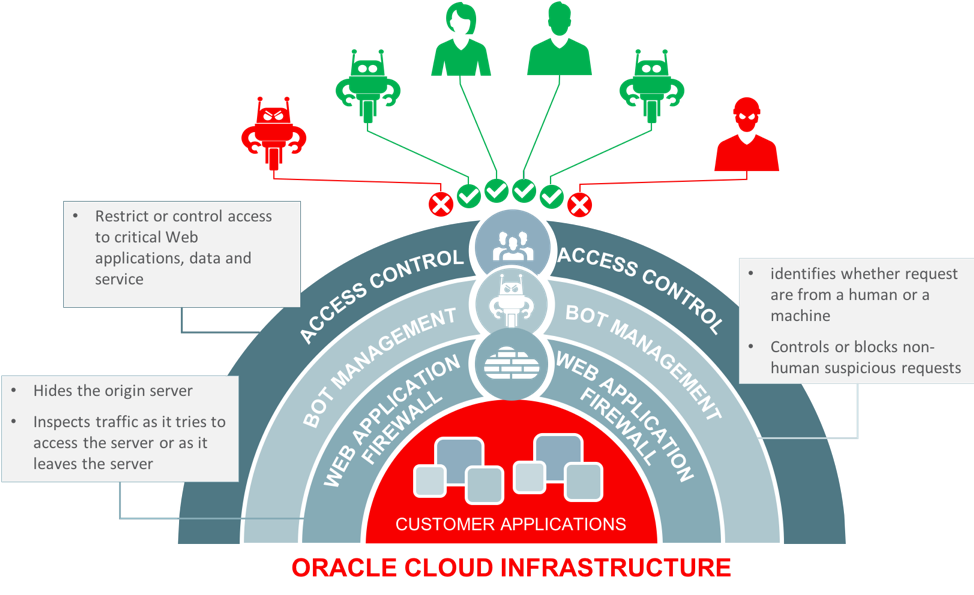
This powerful service enables you to control data leakage from your applications servers and to protect your servers from outside threats.
WAF Integration
Oracle Cloud Infrastructure WAF is tightly integrated in the Console with the other Oracle Cloud Infrastructure applications and services, making it easy to set up and control. For example:
- You can apply tagging to WAF policies for cost tracking.
- You can use Identity and Access Management (IAM) to control access to WAF management.
- WAF changes are recorded in the Audit service.
WAF is located under the Edge Services menu. You can enable predefined rules for passive detection, or WAF can block for each individual rule as a reverse proxy to the web application origin.
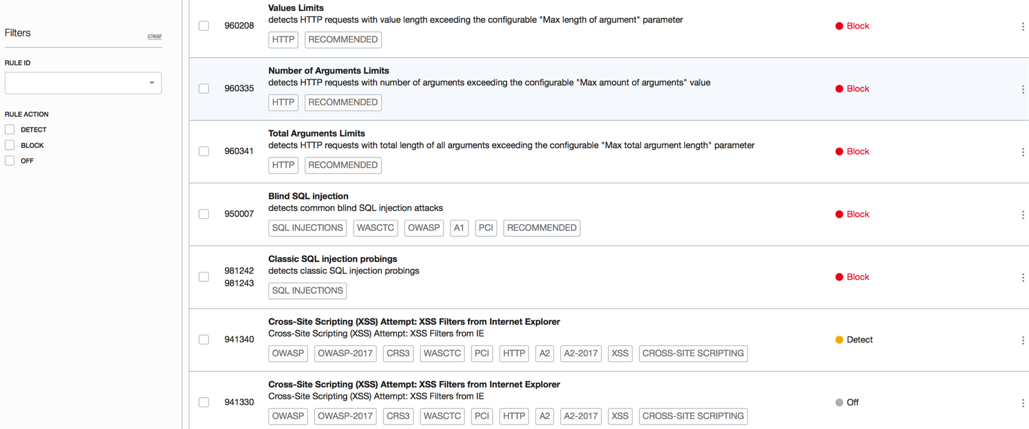
Hundreds of ready-to-use protection rules
Logging of traffic through the WAF can be analyzed from within the Console or pulled into an enterprise SIEM.
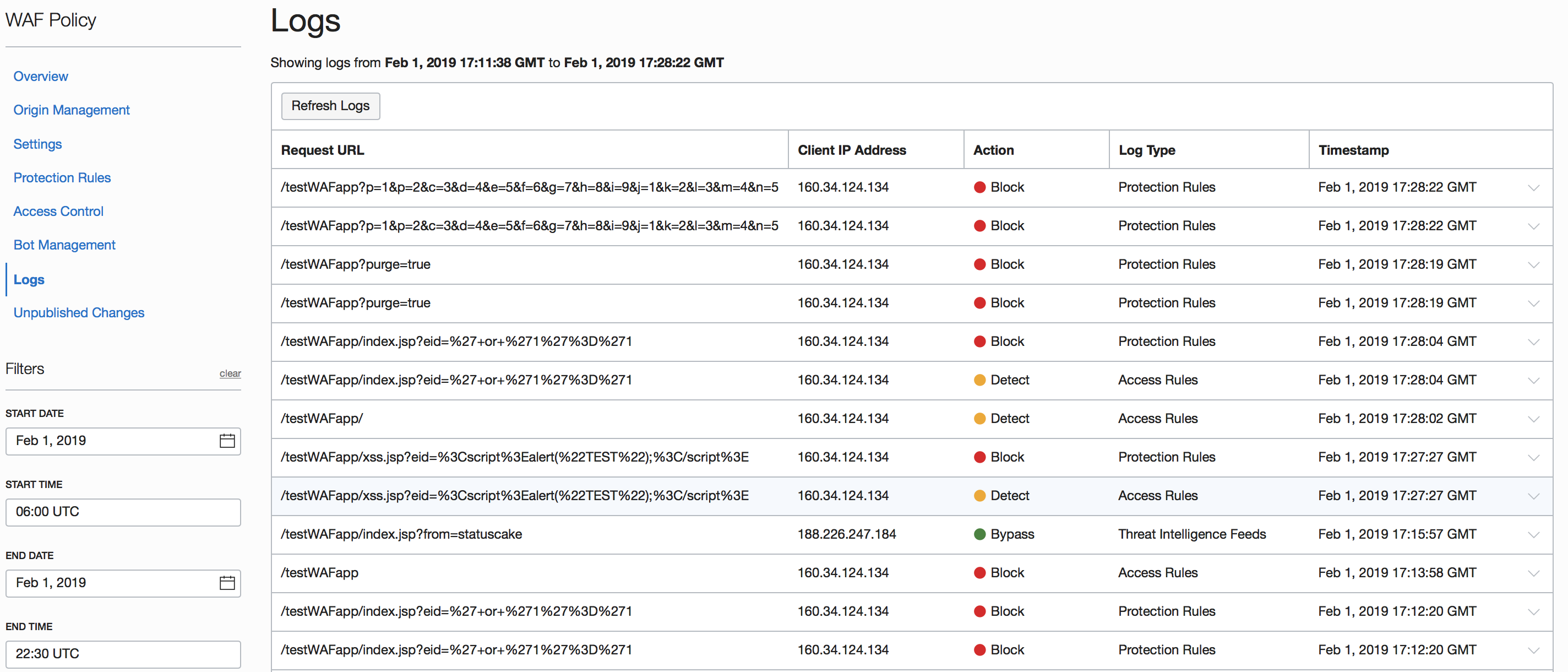 Detailed application logging and visibility
Detailed application logging and visibility
In addition to the Console integration, a robust RESTful API into the WAF platform is available. This includes multiple language SDKs, a CLI, and Terraform.
Key Use Cases
Following are just a few of the many use cases for a web application firewall:
- Protection against cyberattacks: Oracle Cloud Infrastructure WAF is cloud-based and supports 250 rule sets, as well as rule sets for OWASP. Use these rules to protect your critical web applications against malicious cyberattacks. These rules are compared against incoming requests to determine if the request contains an attack payload. If it determines that the request is an attack, WAF blocks or alerts you to that request. These attacks are many and varied, and include threats such as SQL injection, cross-site scripting, and HTML injection—all of which can be detected and blocked by the WAF rule sets.
- Access control for data-privacy standards: Use the access control to restrict or control access to your critical web applications, data, and services. As an example, regional-based access control is perfect for the EU General Data Protection Regulation (GDPR) compliance requirements. In some cases, an offering might need to stay within a specific region or country to comply with GDPR. Regional-based access control can be used to restrict users to a geography and prevent them from getting information from servers located in, for example, the United States. Another use could be to block countries from getting to your applications servers entirely. For example, if you don’t do business with countries located in Asia, you can completely block access from these countries.
- Integration with existing management systems: The RESTful API provides a complete machine-to-machine interface into WAF. This is ideal if you are an Oracle Cloud Infrastructure customer, partner, or managed service provider who already has backend management systems, doesn’t need the Console, and wants to integrate WAF directly into your existing management systems.
- Bot management: Bot traffic has surpassed human traffic on the internet. The majority of bots are good, however, so you can’t just block them all. You can use the additional JavaScript challenge, CAPTCHA challenge, and whitelisting capabilities in conjunction with the WAF rule sets to further detect and block bad bots while allowing good bots through.
- Hybrid and multicloud protection: Many cloud providers restrict their web application firewall protection to applications that reside within their own clouds. This is not the case with Oracle Cloud Infrastructure WAF. In addition to providing protection for Oracle Cloud Infrastructure workloads, WAF also protects on-premises and multicloud environments. Having a single web application firewall to protect your workloads in any environment is extremely important as you move to Oracle Cloud Infrastructure. WAF will protect your entire environment and each phase of your migration—cloud testing, migration, and ramp up.
Conclusion
Oracle Cloud Infrastructure WAF is a key component for enabling internet-facing web applications when you move away from requiring a VPN or build customer-facing applications. For more information about the Oracle Cloud Infrastructure WAF, visit our website.