This post was written in collaboration with guest contributor Jeff Engel, Cloud Alliance Architect, Check Point.
Oracle Cloud Infrastructure (OCI) continues to embrace open source technologies and the developer communities that support them. With the rapid adoption of cloud native technologies and DevOps methodologies, many organizations have said that they want an open cloud that avoids vendor lock-in and allows them to run what they want, whether the cloud provider builds it or not.
As part of Oracle’s continuing commitment to open standards and supporting a broad and varied ecosystem, we’re pleased to announce that Check Point has extended its most complete real-time threat prevention against Gen V cyber-attacks to OCI.
As application developers, our goal is to produce secure, robust code that meets business needs and is easy to maintain, extend, and support with the least effort. Within that framework, the challenge of securing our code can be a never-ending whack-a-mole exercise that robs us of precious development time. Evolving new exploits and obscure attack vectors have created the role of DevSecOps to protect vital corporate assets from application vulnerability exposure.
Best practices now require automated solutions integrated into robust continuous integration-continuous deployment (CI/CD) pipelines that provide threat prevention from known and unknown vulnerabilities.
Securing your cloud
What containers are running in my environment? How do I ensure that my environments meet industry security benchmarks? It looks like these questions open a set of challenging tasks to answer them.
However, with CloudGuard Security Posture Management (CSPM), you can easily manage the security and compliance of your Kubernetes clusters, whether they are on the public or private cloud.
The onboarding process is simple. Deploy Check Point helm chart in your cluster, and the agents start collecting cluster and workload information.
When the setup is complete, you can take advantage of CloudGuard platform capabilities. Out of the box, CloudGuard provides 87 rules defined for Kubernetes environments. These rules cover industry standards like the CIS benchmark and NIST.
You can also build your own policies using Governance Specification Language (GSL). This language specification is human readable and comes with an integrated editor that makes creating rules intuitive.
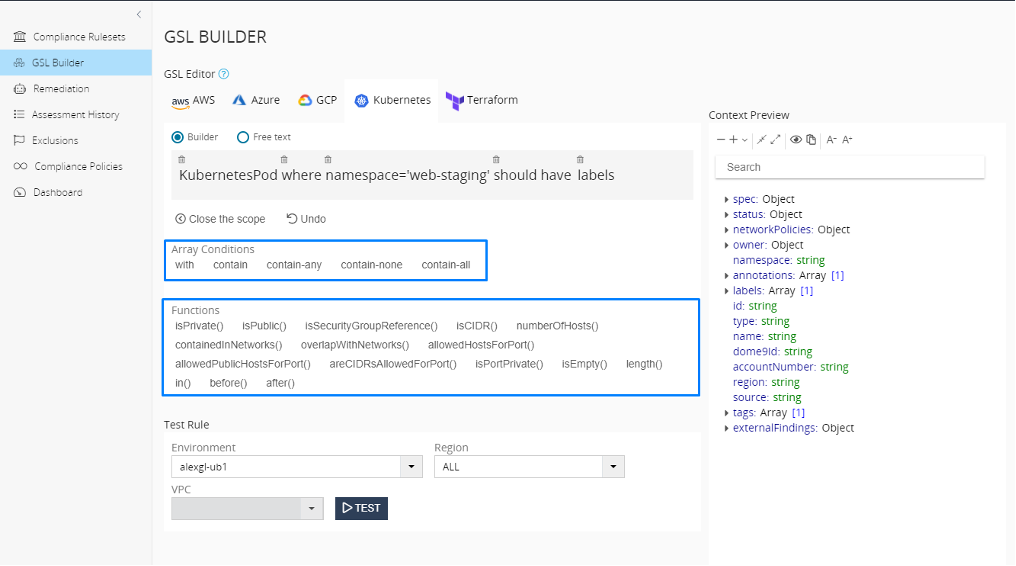
You can export the rules into JSON format. Using the CloudGuard API, you can update rules programmatically, enabling CloudGuard to fit in any automation process.
Containers running in the cluster are analyzed for vulnerabilities that could become a risk for the application. In the alerts panel, you can filter all the alerts for your environments.
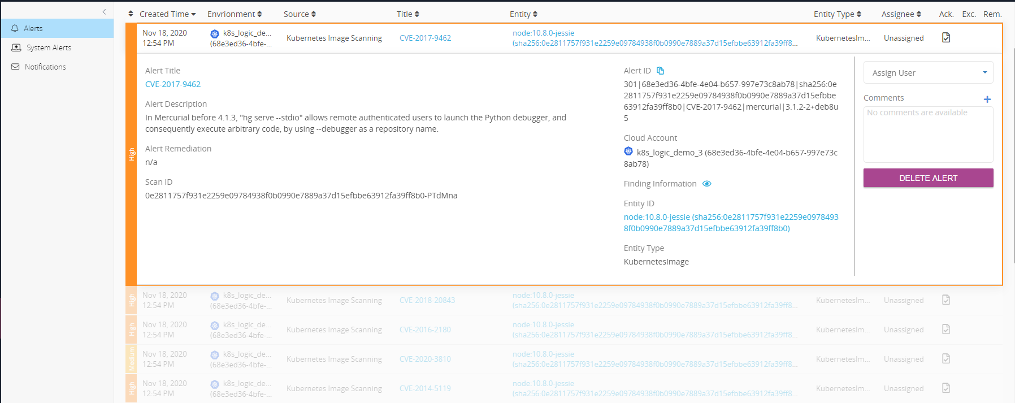
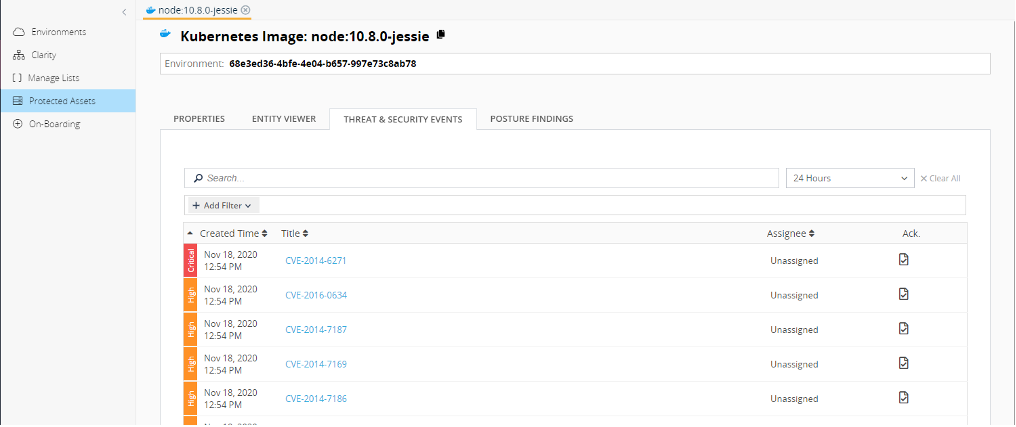
You can dig deeper into the specific container image to find all vulnerabilities associated with it.
CloudGuard Log.ic for Kubernetes consumes flow logs generated in the k8s cluster to analyze and visualize traffic flows. With this analysis, you can identify traffic from unwanted sources or gaps in network security settings, including the following examples:
-
Outbound traffic to malicious IP addresses
-
Port scanning of an internal asset from a Kubernetes pod
-
Outbound traffic to a Tor exit node from within a Kubernetes cluster
-
Inbound accepted traffic to a Kubernetes cluster from a malicious IP address
-
K8s DNS spoofing
K8s pod access to metadata
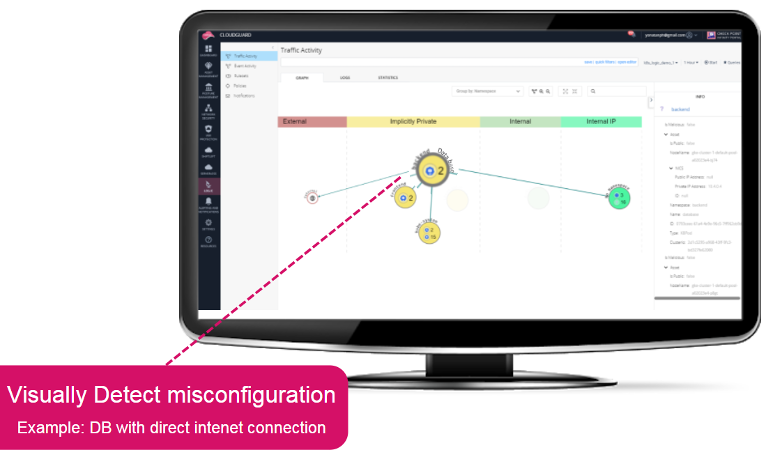
Although we covered only a few key features, with CloudGuard CSPM, cloud security operations teams can gain full visibility, compliance, and control of their security posture, allowing them to detect misconfigurations, protect against vulnerabilities, and respond to incidents and alerts in a faster and more effective way. The Check Point Infinity architecture provides the tools needed to protect both your Oracle Container Engine for Kubernetes (OKE) environment with continuous posture management evaluation and your container-based applications with Infinity Next web application and API protection (WAAP).
Next steps
If you want to experience Check Point with OKE for yourself, sign up for an Oracle Cloud Infrastructure trial account and start a free Check Point trial. With Oracle Cloud Container Engine for Kubernetes and Check Point, you can deploy Kubernetes with confidence.
