As part of our continuing commitment to open standards and supporting a broad and varied ecosystem, we’re pleased to announce that Trend Micro has extended its Cloud One Container Security support to Oracle Cloud Infrastructure Container Engine for Kubernetes (sometimes referred to as OKE).
This post was written by guest contributor Manish Patel, Sr. Director of Strategic Alliances at Trend Micro.
Containers add speed and agility to application deployment, and their ephemeral nature lets organizations benefit from the on-demand consumption of resources and abstract away from the underlying infrastructure. For organizations that require scalable, reliable, and fully managed service for deploying containerized applications to the cloud, Container Engine for Kubernetes allows deployment teams to reliably build, deploy, and manage cloud native applications.
The use of containers requires organizations to implement a holistic security model that detects vulnerabilities before a container is deployed and at run time, and also protects up and down the infrastructure stack. The implications of this new development model have prompted the need to “shift left.” Whether you deploy these new applications using containers on-premises or in the cloud, organizations must now consider security throughout the software development life cycle (SDLC).
But organizations typically have heterogeneous environments in which some applications are containerized, others are virtualized or run on physical infrastructure, and others run in multiple clouds—for example, using Oracle Cloud Infrastructure or using Linux Distribution in a virtualized data center. Having separate security solutions for such deployments is costly, requires additional skills and resources to manage, and leads to security inconsistency and exposure to threats if not configured and managed properly. And with modern development practices and technologies, like continuous integration/continuous delivery (CI/CD), containers, and serverless, you need security that provides earlier detection, immediate protection, and assurance that your cloud services meet security best practices, all while maintaining DevOps speed.
The Trend Micro Solution
Trend Micro Cloud One is a security services platform for organizations that are modernizing their software development practices. This single solution includes multiple integrated security components that provide consistent protection across your heterogeneous environment, including data center, cloud, containers.
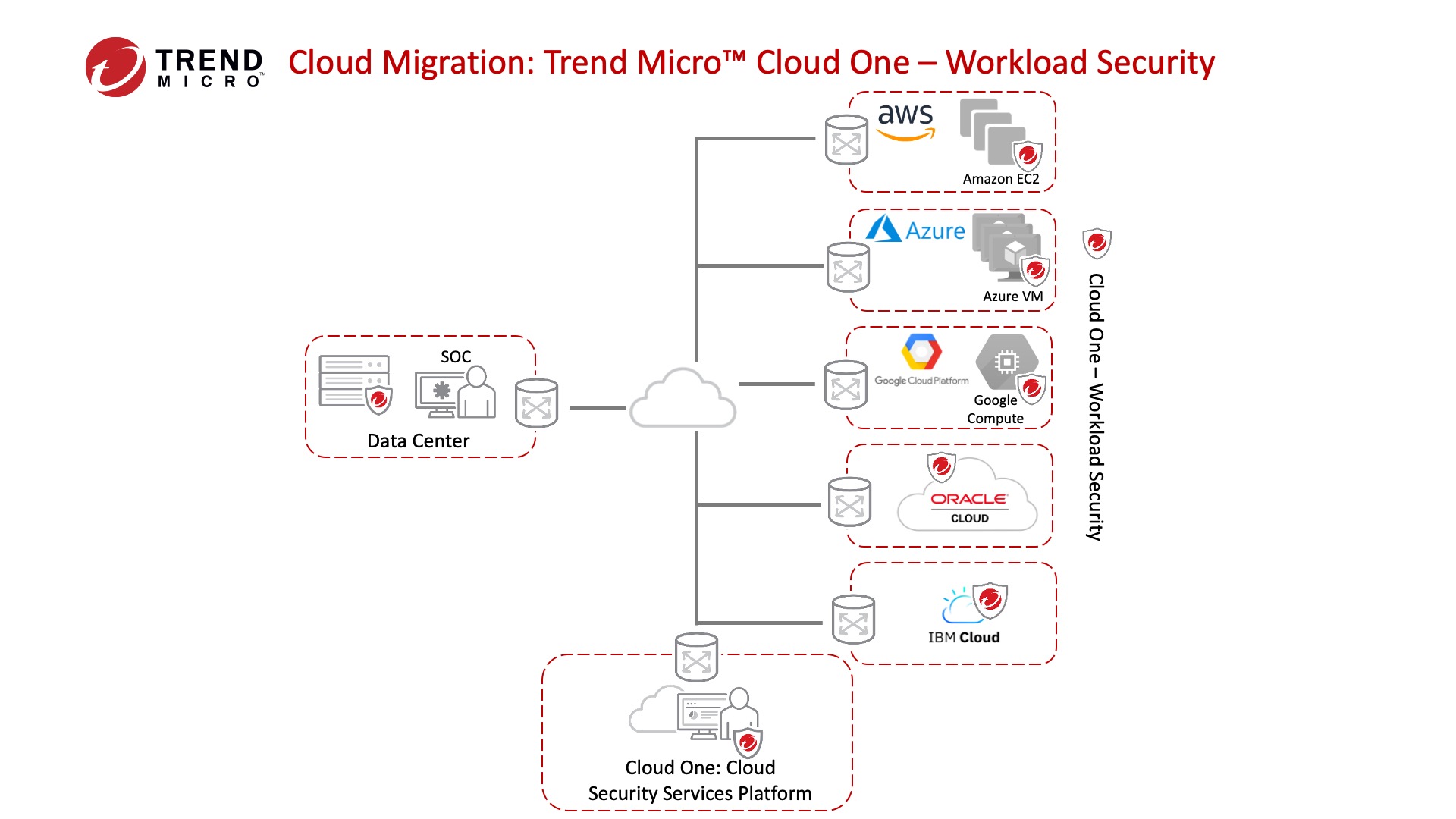
Figure 1: Cloud One Workload Security Across a Heterogeneous Environment
Trend Micro Container Security Architecture
The Container Security component of Cloud One works with Oracle Cloud Infrastructure Registry (OCIR) to deliver automated build pipeline container image and registry scanning. Designed for developers and operations teams, Container Security enables earlier and faster detection of malware, secrets and keys, compliance violations, and vulnerabilities, including those found in open source code dependencies.
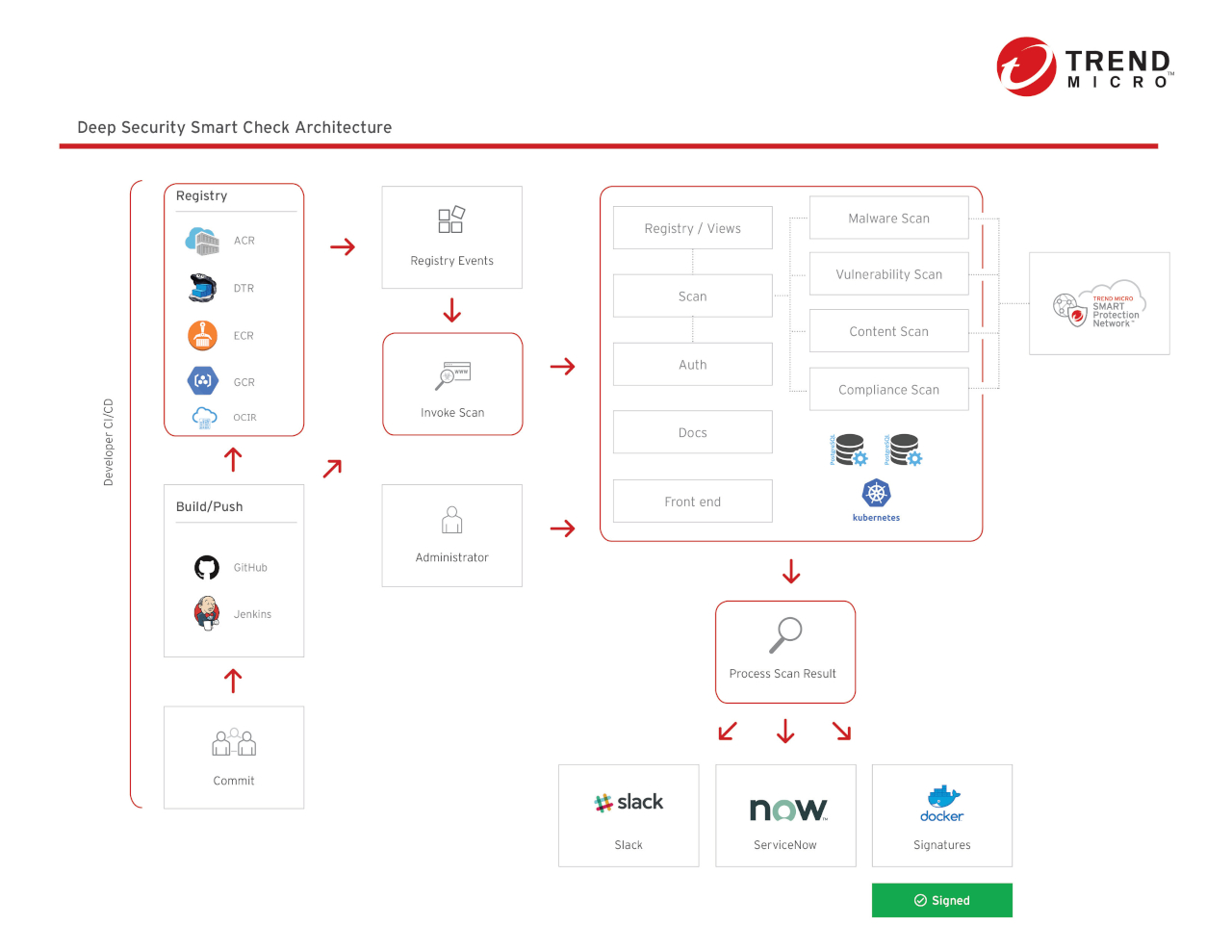
Figure 2: Code One Container Security Embeds Security Throughout the Development Process
Additionally, Container Security helps to detect threats in package-manager-installed apps and directly installed apps by using Trend Micro’s industry-leading rules feed. Container Security helps developers extend even further to the left with Snyk’s open source vulnerability database, which offers early detection and mitigation of vulnerabilities in open source code dependencies. With Container Security, DevOps teams are enabled to continuously deliver production-ready applications and meet the needs of the business—without impacting build cycles.
Advanced Image Scanning
When scanning, Trend Micro Container Security unpacks each layer of the image and performs detailed scans on the content. You can ensure that issues are fixed early and filter out false positives by correlating patch layers with packages that are vulnerable in the same image. Container Security scans images for malware detection, vulnerability assessment, secrets (such as private keys and passwords), policy compliance, and vulnerabilities in open source code, using Snyk detection.
Continuous Protection
Container Security scans can be invoked when images are first built and will continually scan in the registry for new malware and vulnerabilities in production-ready images. So, your images are secured from the first build and remain protected from future unknown threats. You can scan images across multiple cloud environments from a single Container Security deployment.
Automate Processes with APIs
Container Security provides complete automated product functionality by using a comprehensive catalog of APIs built to integrate into your CI/CD pipeline. Container Security allows application architects and developers to include security as code into their build pipeline for container image and registry scanning. Implementing effective security earlier in the software build pipeline helps to achieve consistent results faster in the development cycle and reduces manual security steps and application downtime.
Compliance-Ready Protection
Container Security lets security engineers meet compliance requirements without impacting productivity and interfering in the CI/CD pipeline. What’s more, it delivers policy compliance scanning, with customizable policies to meet compliance and governance needs. Container Security also offers detailed log history, which enables easy reporting and auditing.
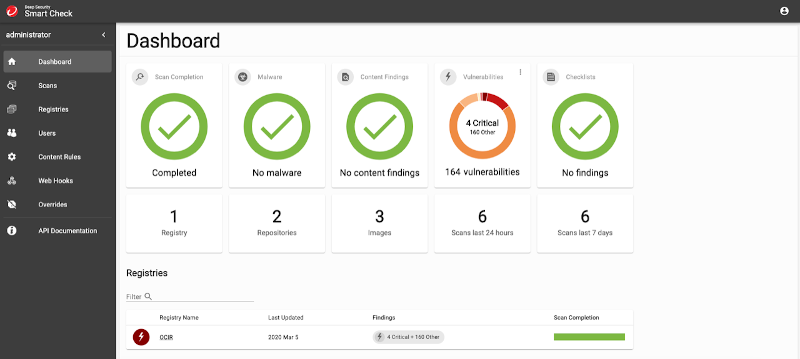
Figure 3: Clear Scan Results
World-Class Threat Feed
Container Security receives up-to-date threat feeds from private Trend Micro sources (the Trend Micro Smart Protection Network) and public sources, and implements automation and learning algorithms to detect zero-day threats.
The Complete Cloud One Platform
Container Security is just one component of Trend Micro’s Cloud One platform, which also consists of the following components:
- Workload Security: Runtime protection for workloads (virtual, physical, cloud, and containers)
- File Storage Security: Security for cloud file and object storage services
- Application Security: Security for serverless functions, APIs, and applications
- Network Security: Cloud network layer IPS security
- Conformity: Cloud security and compliance posture management
Learn More
For more information, see the Container Engine for Kubernetes and Trend Micro Container Security documentation. Trend Micro’s Cloud One website provides information about the full capabilities for hybrid cloud security. If you want to try Trend Micro’s Container Security with Container Engine for Kubernetes for yourself, sign up for an Oracle Cloud Infrastructure account and a Trend Micro Container Security free trial, and start testing today!
