A few months ago, the Oracle Cloud Infrastructure Web Application Firewall (WAF) identified and mitigated a malicious bot attack on a major e-commerce site.
This post explains how sophisticated behavioral analytics stopped the attack and why they are a critical component of a core-to-edge security strategy.
Inside the Attack
As is typical in the e-commerce industry, the website of this customer is separated into two components:
- Brochureware site: The home page that includes the selection of items for purchase
- Commerce engine: The backend where the actual transactions are performed, which includes user identity management and a payment gateway
Both the brochureware site and commerce engine are on the same domain, and the visitor cannot see the difference between the two components. In this case, both components are hosted in separate cloud environments, in different countries and time zones.
On the day of the attack, the brochureware site experienced a slight increase in traffic around midday, on what would otherwise be called a typical day. There had been a generic traffic pattern, with little traffic during the night and increased traffic during the day when customers are making purchases.
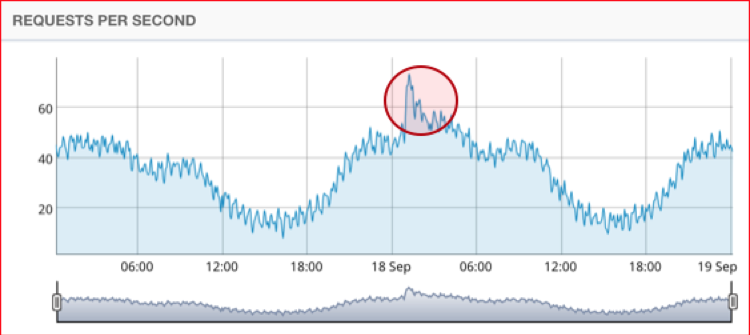
A spike in traffic is clearly visible for the brochureware component of the site over 48 hours of traffic.
The commerce site experienced a much stronger spike in suspicious traffic around the same time. Note the scale of requests per second: two orders of magnitude higher on the commerce site than the brochureware site.
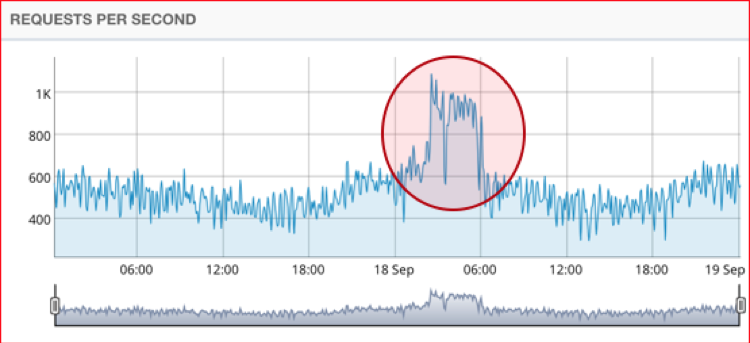
On a normal day, the customer’s applications receive about 80 million to 90 million requests. During this attack, almost 10 million additional requests were performed by a very sophisticated and well-distributed botnet. The botnet was automatically identified, classified as malicious, and blocked by the Oracle Cloud Infrastructure WAF. The botnet’s primary objective was to drive up prices artificially by temporarily holding inventory, thus driving paying customers to competitors’ sites.
Attack Detection
The Oracle Cloud Infrastructure WAF analyzes traffic in real time using Oracle’s high-capacity Edge Network, globally distributed points of presence that proxy traffic to clients’ web properties.
When suspicious activity is detected, the WAF’s bot management capabilities automatically classify and activate countermeasures that attempt to block the incoming nonhuman traffic. The application security engine automatically selects the countermeasure depending on the degree of sophistication of the botnet.
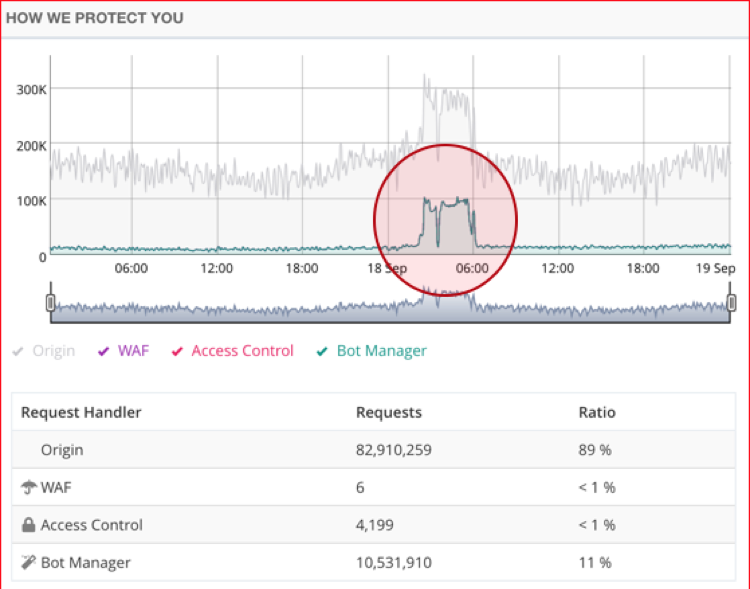
The Oracle Cloud Infrastructure WAF automatically identified and blocked the entirety of the bot traffic spike.
The sophistication of the attack and the countermeasures that the platform selected are notable. In many cases, large botnets are identified by a threat intelligence layer (when the botnet IP addresses are known and blacklisted by a consortium of organizations) or a JavaScript defense layer (which classifies users as bots when traffic requests lack a JavaScript engine typical of common internet browsers).
In this case, the Oracle Cloud Infrastructure WAF automatically activated, identified, and blocked the suspected malicious bots by using two advanced countermeasures: Device Fingerprinting and the Human Interaction Challenge. The following figure shows that the entirety of the malicious traffic was mitigated using these two countermeasures.
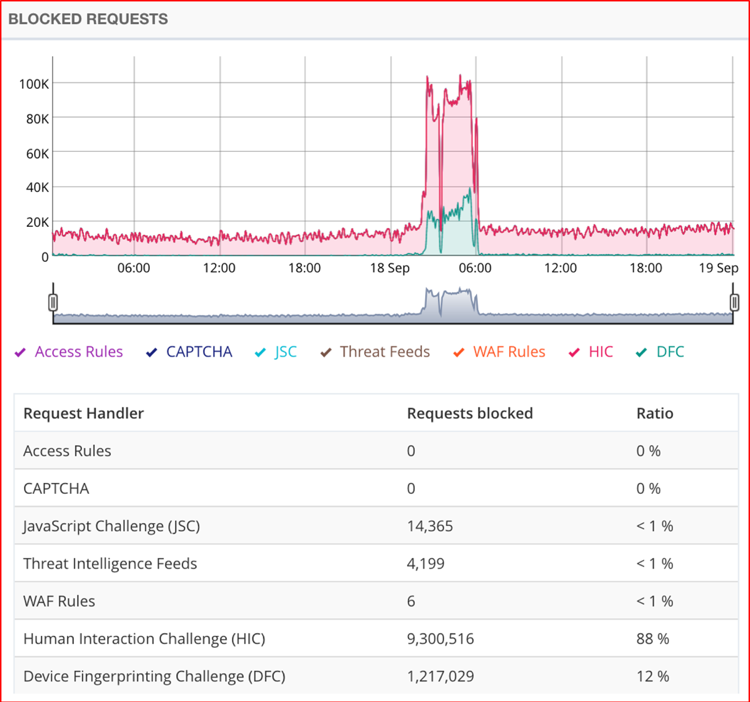
Traditional bot management techniques such as IP blacklisting, WAF rules, and the JavaScript challenge were not used to block the botnet in this instance.
Sophisticated, Automated Bot Management
The Human Interaction Challenge, which blocked the majority of bots in this attack, identifies normal usage patterns for each web application based on legitimate visitor behavior analysis and provides customizable security postures for bots that deviate from the standard usage behavior, activity, or frequency. This is where machine learning, a subset of artificial intelligence, comes into play.
For the Human Interaction Challenge to work to its fullest potential, a learning model must be incorporated. This model combines known signatures, request headers, common IP addresses, request language, and other factors to create a profile of legitimate user behavior. When traffic violates these known behavior patterns, the traffic is flagged and blocked by the challenge.
The Device Fingerprinting Challenge generates a hashed signature of both virtual and real browsers based on over 50 attributes. These proprietary signatures are then leveraged for real-time correlation to identify and block malicious bots.
What Was the Botnet Doing
We suspect that the bots were executing an attack known as cart stuffing. In this case, the bots were reserving items but not completing purchases. This caused the system to hold these items out of inventory pending payment, driving up the price of other items. Human users were leaving the site, as items appeared to be sold out or grossly overpriced because of limited availability.
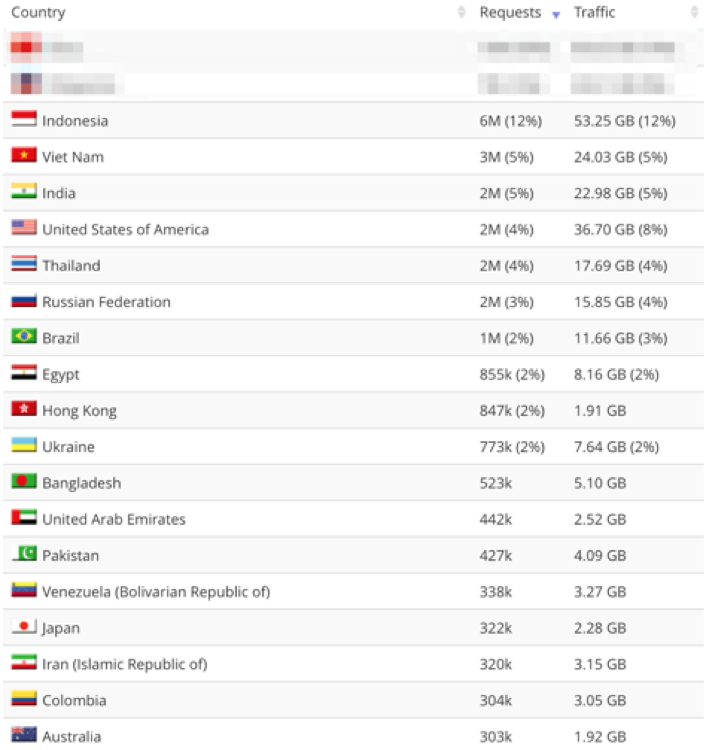
As illustrated in the following images, the botnet used a variety of IP addresses and countries of origin. The images show the top countries per traffic. Note that a botnet is usually well distributed in many different locations, which just means that the compromised machines that ran this attack were spread out. This is never an indicator of the geolocation of the hacking team itself.
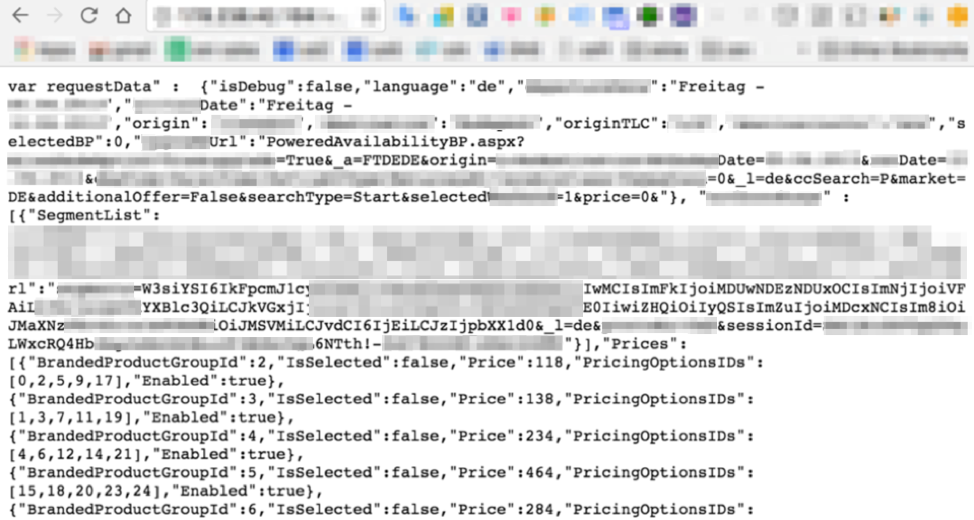
In some cases, we can find traces of the bots’ activity post-mortem. Following is an example of a file that we found on one of the compromised botnet hosts, which appears to show how dynamic pricing can be manipulated by false traffic.
In Conclusion
As bot technology becomes increasingly sophisticated, the techniques used to stop it must become just as advanced. Although basic bot protections are still necessary, the future of cybersecurity must incorporate automation for complete protection against emerging threats. The key, as always, is for security teams to select and use systems and processes that are smart enough to activate defenses when the earliest signs of suspicious activity are detected.
Oracle Cloud Infrastructure’s core-to-edge security strategy protects you and your organization from a variety of external and internal threats and incorporates common management of events, alerts, and orchestration of mitigations. Often, as is the case here, attacks can include millions of bot requests. High capacity must be mobilized instantaneously, so that an attack can be quickly identified and dealt with. Oracle’s edge compute and infrastructure capacity is highly scalable and almost limitless.
In this case study, the customer applications are hosted by two different cloud providers, in countries 4,500 miles apart. Increasingly, enterprises are using more than one cloud provider, often in combination with on-premises legacy systems and their private clouds. Hence, the Oracle Cloud Infrastructure WAF is natively designed to work independently from where applications are hosted (Oracle Cloud, as well as Amazon Web Services, Microsoft Azure, Google Cloud Platform, and on premises) and their delivery mechanisms (such as a content delivery network).
This design is especially important for security and performance, because one platform provides a global view of all events and monitoring, and serves as the unique protection layer for all applications.