VCN is a customizable private network in Oracle’s Bare Metal Cloud Service (BMCS). Just like a traditional data center network, a VCN provides you with control over your network environment. This includes assigning your own private IP address space, creating subnets, creating route tables and configuring stateful firewalls. A single tenant can have multiple VCNs, thereby providing grouping and isolation of related resources.
In this post, I will walk you through a scenario in which you configure your VCN as an extension to your on-premises network. The instances you subsequently launch into this VCN will only be accessible from your private, on-premises network, and not to the public Internet. This enables you to use the Oracle Bare Metal Cloud Service just like you would your own datacenter, providing you with the flexibility to use compute, storage and database resources when you want and for however long you need them, without the complexity and the overhead of operating a traditional data center environment.
Key Components
Here is an overview of the key components configured in this scenario.
- 1 Virtual Cloud Network (VCN), with address space 172.16.0.0/16. This spans an entire Region across all its three Availability Domains (ADs).
Note: Every Region has at least 3 Availability Domains (ADs) which are connected by a low-latency network and each one is isolated from failures in other ADs. You can launch your resources in separate ADs to protect your application from failure of a single AD, build redundancy and high-availability. - 3 Subnetworks (Subnets) in the VCN (172.16.0.0/24, 172.16.1.0/24, 172.16.2.0/24) in separate Availability Domains (ADs).
- 1 Route Table for instances in the subnets to communicate with on-premises network.
- 1 Security List to allow traffic in/out of the instances.
- 1 Dynamic Routing Gateway (DRG) to establish a site-to-site VPN between the VCN and your on-premises network.
- 1 (or more) routers in your on-premises network, which you can configured to establish a site-to-site VPN connection.
Pre-requisites
- You need to have an Oracle Bare Metal Cloud Services account. If you don’t already have one, you can get one at the Oracle Store.
- You need to get the following information from your network administrator. You will use this information to configure IPSec tunnels on Oracle Bare Metal Cloud end. You will then need to use the IPSec tunnel information to configure the VPN on your end.
- IP address of the router in your on-premises network to configure the VPN
- Static routes for your on-premises network
Configuration
Note: You can use the Oracle Bare Metal Cloud Services (BMCS) Console to perform all of the steps required for this scenario. If you havent already done so, please go through Using the Console.
You can create all your resources under the “Sandbox” compartment for the sake of simplicity. This can be different based on your identity and access management model.
- Create VCN

Choose ‘Create Virtual Cloud Network Only’ so you can explicitly create the subnetworks and their configuration.
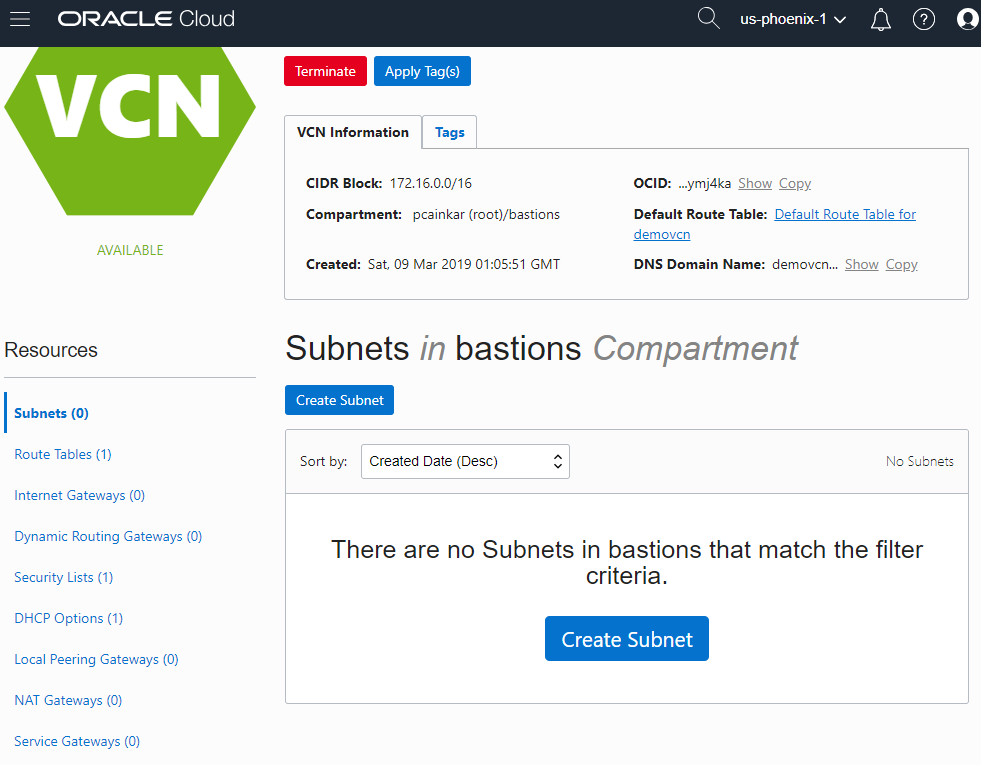
You now have a Virtual Cloud Network (VCN) with address space 17.16.0.0/16, which spans an entire region.
Notice the number in parenthesis that indicates the number of resources of each type in the VCN. There is 1 item in “Route Tables”, “Security Lists” and “DHCP Options” which are the default components created with the VCN.
- Create subnetworks
You can now create three subnets, in separate Availability Domains. This will allow distributing your instances across the subnets for high-availability.
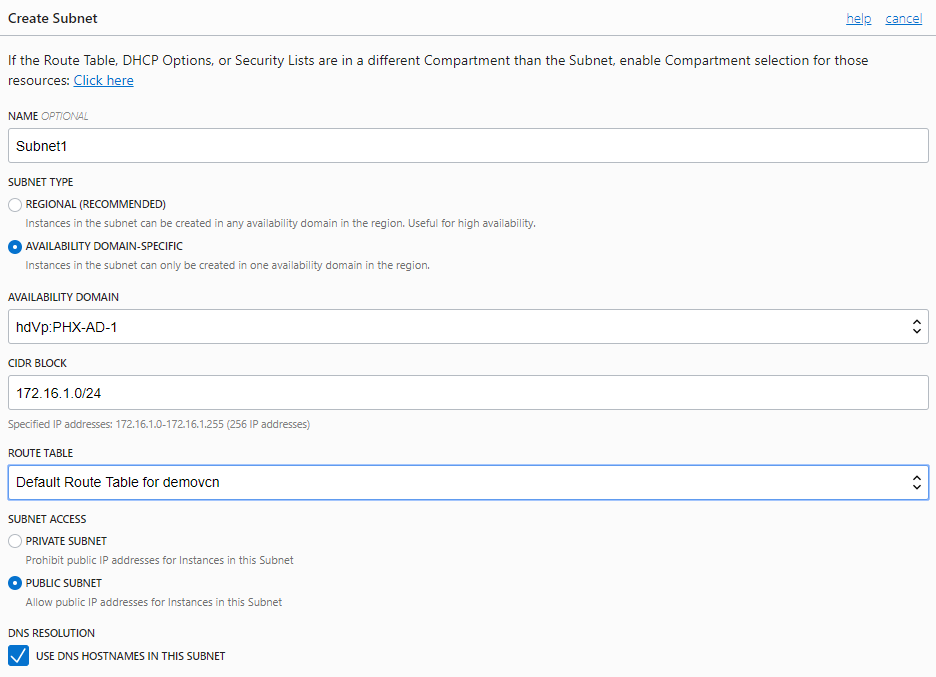
The snapshot above shows the options provided for one subnet. You will have to change the Availability Domain and the CIDR block when creating the remaining two subnets. - You can use the default route table, security lists and dhcp options for all subnets.

Note: In this scenario, all subnets have a similar function and it is okay to configure them with the same route table and security list. However, it is recommended to use separate resources for subnets with different functions (webservers vs database).
- Create a Dynamic Routing Gateway (DRG)
There are no DRGs to begin with in your compartment. You can create a ‘demodrg’ which will function as the VPN head on OBMCS end.

The provisioning of a DRG can take a few seconds.
Once the DRG is available, you can attach it to your VCN.

Once the DRG is successfully attached to your VCN, you are ready to create IPSec tunnels which will be required to configure the VPN head at on-premises end.
- Create a Customer Premises Equipment (CPE)
Before you can create the IPSec tunnels, you need to create a customer-premises equipment (CPE) to logically represent the on-premises VPN device within BMCS Networking configuration.
At this time, you only need to know the public (external) IP address of the VPN device that will be used to establish IPSec VPN.

- Create IPSec Connection
You can now go to my DRG configuration page and create an IPSec connection to the CPE added above.
Now, you need to know the CIDR block of your on-premises network, which will be the encryption domain configured on the on-premises VPN device.
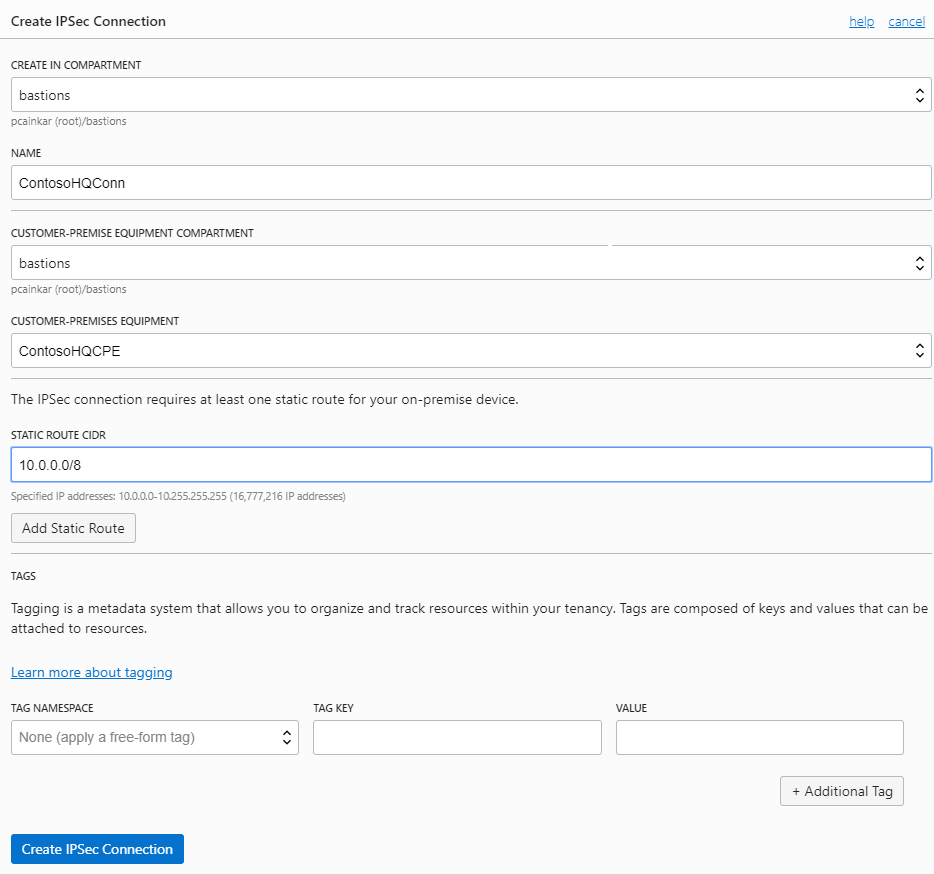
Once the IPSec connection provisioning is complete, BMCS creates 3 IPSec tunnel endpoints, one in each AD. You can use the tunnel information to configure the VPN device on-premises.
- Get IPSec tunnel information
Once the IPSec connection is available, you can get the information of IPSec tunnels setup on OBMCS end by clicking on “Tunnel Information” on the “IPSec Connection” item.

The tunnel information will contain the IP addresses of the tunnel endpoints and the shared secret to be used to initiate the IPSec connection.

It also shows the status of the IPSec connection, which is currently ‘DOWN’ as the on-premises end is not configured yet.
- Configure IPSec connection on remote end.
This step generally needs a network administrator who can configure your on-premises VPN device(s) to initiate an IPSec connection to the tunnels created on OBMCS.
Once this this step is complete, the status changes to ‘UP’. Now the VCN on OBMCS has connectivity to your on-premises network through IPSec tunnel(s) established between DRG (OBMCS end) and the VPN devices at your on-premises.
Note: It is recommended to establish at least two IPSec tunnels, from the VPN device at on-premises. The best practice is to use redundant VPN devices at on-premises, and do a full-mesh with the three IPSec tunnel endpoints at OBMCS end.
- Configure routing for subnets to go through DRG for on-premises traffic
The default routing table created for a VCN has no rules by default. All instances in VCN have a route to other instances in the VCN only.
You can modify the default route table to add a default route and set the DRG as the route target. This will route any non-VCN traffic through the DRG into on-premises network (which can subsequently be inspected/forwarded as required).

Since this route table is attached to both subnets, you only need to do it once.
- Configure security rules to allow valid traffic in/out of my subnets
The default security list has only 3 ingress rules to allow (ssh from any source, ICMP fragmentation needed but DF bit set from any source, ICMP destination not reachable from sources within VCN address space), and 1 egress rule to allow all outgoing traffic.
In this case, you need to allow SSH only from within the VCN address space and on-premises network. So you can modify the rules to allow SSH only from these two sources. You can also open up specific ports for the application running on your compute instances within these subnets, again from the same two sources.

With these steps, you now have a VCN that is only accessible from your on-premises network. You will be able to launch compute instances, storage, and several other resources offered by Oracle Bare Metal Cloud Services (BMCS) into your VCN. For a complete list of resources you can launch, please visit our product page here.
Thank you for going through this post. Your feedback and recommendations for future posts is most welcome.
I hope you will enjoy using Oracle Bare Metal Cloud Services. Keep watching the Oracle Bare Metal Cloud Community space for updates as we add more exciting capabilities.
