This post was written by guest contributors, Dr. Swarup Kumar Sahoo, Co-founder and Chief Scientist, and Shyam Krishnaswamy, Co-founder & VP of Engineering, at Deepfence Inc
We’re excited to announce that Deepfence has extended its cloud native workload protection platform support to Oracle Cloud Container Engine for Kubernetes. Deepfence is a security platform that provides security starting from CI/CD stage to deployment stage against both known and unknown attacks targeting cloud native workloads.
Container Engine for Kubernetes and Oracle Cloud Infrastructure provide rich security functionality at the infrastructure level. Deepfence can complement this built-in security mechanism by understanding the application behavior deeply in cloud deployments to protect applications during CI/CD and at runtime using their patent-pending semantic patching technology.
Deepfence provides a rich set of security functionalities without proxies, kernel modules, code changes, or intrusive agents. Customers can now use it to strengthen their security in their containerized cloud native deployments. Deepfence community edition is a free version that provides visualization and vulnerability scanning of their cloud native workloads. Deepfence enterprise edition provides compliance management, deep packet inspection including encrypted traffic, file, process, system integrity monitoring, and runtime protection. Overall, Deepfence monitors 65+ different types of signals, 50+ vulnerabilities sources, thousands of compliance policies, and provides runtime protection using a powerful combination of rules and machine learning.
Deploying Deepfence on Oracle Kubernetes Engine
Deepfence installation consists of two components: Deepfence Management Console, which is installed outside of a cluster being threat mapped, and super lightweight Deepfence agents, which are deployed as daemon service on the Oracle Kubernetes Engine cluster.
Installing Deepfence Management Console
The following steps show the installation of the management console:
-
Create an Oracle Kubernetes Engine cluster for running management console, and install kubectl and helm. Creating a Kubernetes cluster on Oracle Cloud is straightforward. You can use either CLI or Console for creating and managing Kubernetes clusters on Oracle Cloud Infrastructure Container Engine for Kubernetes (OKE). You can either create a quick OKE cluster with default configurations using the quick cluster option in the Console, or create a custom OKE cluster based on a custom configuration using the custom cluster option.
After installing kubectl, you can also easily upgrade, scale, and perform other tasks on your OKE cluster using kubectl.
-
Create a three-node Kubernetes cluster with at least four cores, 16 GB RAM, and 120 GB disk space. For larger workloads, you can scale the Console accordingly.
-
Install the Deepfence management console using the helm package manager. For quick installation, you can use the following helm command, after adding the provided username and password. We send a customized helm chart with detailed instructions to install console for enterprise version.
# helm v2
helm install deepfence-console-0.2.1.tgz \
--name=deepfence-console \
--set registry.username=<> \
--set registry.password=<>
# helm v3
helm install deepfence-console deepfence-console-0.2.1.tgz \
--set registry.username=<> \
--set registry.password=<>Give it a few minutes, and you’re ready to register your product installation using your license key.
Installing Deepfence Agent on Oracle Kubernetes Engine
-
Similar to the console installation, you need an OKE cluster running, which Deepfence protects, and to install kubectl and helm.
-
You can quickly deploy Deepfence agents on your cluster using the helm package manager. Run this command with the provided username, password and console IP address to start deepfence agent in all nodes in the cluster. Deepfence sends a customized helm chart with detailed instructions to install Deepfence agents for enterprise version.
# helm v2 helm install deepfence-agent-0.2.1.tgz \ --name=deepfence-agent \ --set registry.username="<>" \ --set registry.password="<>" \ --set managementConsoleIp=40.40.40.40 # helm v3 helm install deepfence-agent deepfence-agent-0.2.1.tgz \ --set registry.username="<>" \ --set registry.password="<>" \ --set managementConsoleIp=40.40.40.40 -
It may take a few minutes for deepfence agents to get installed and show up on the console UI. You can check the status of agent installation using the following command:
kubectl get ds -n deepfence --watchOnce the agents are installed, you can visualize the nodes, containers and pods from the Topology tab in the Console UI.
You can click individual nodes in the topology view to initiate various tasks, such as packet capture, vulnerability scanning, compliance checks, and setting up protection policies.
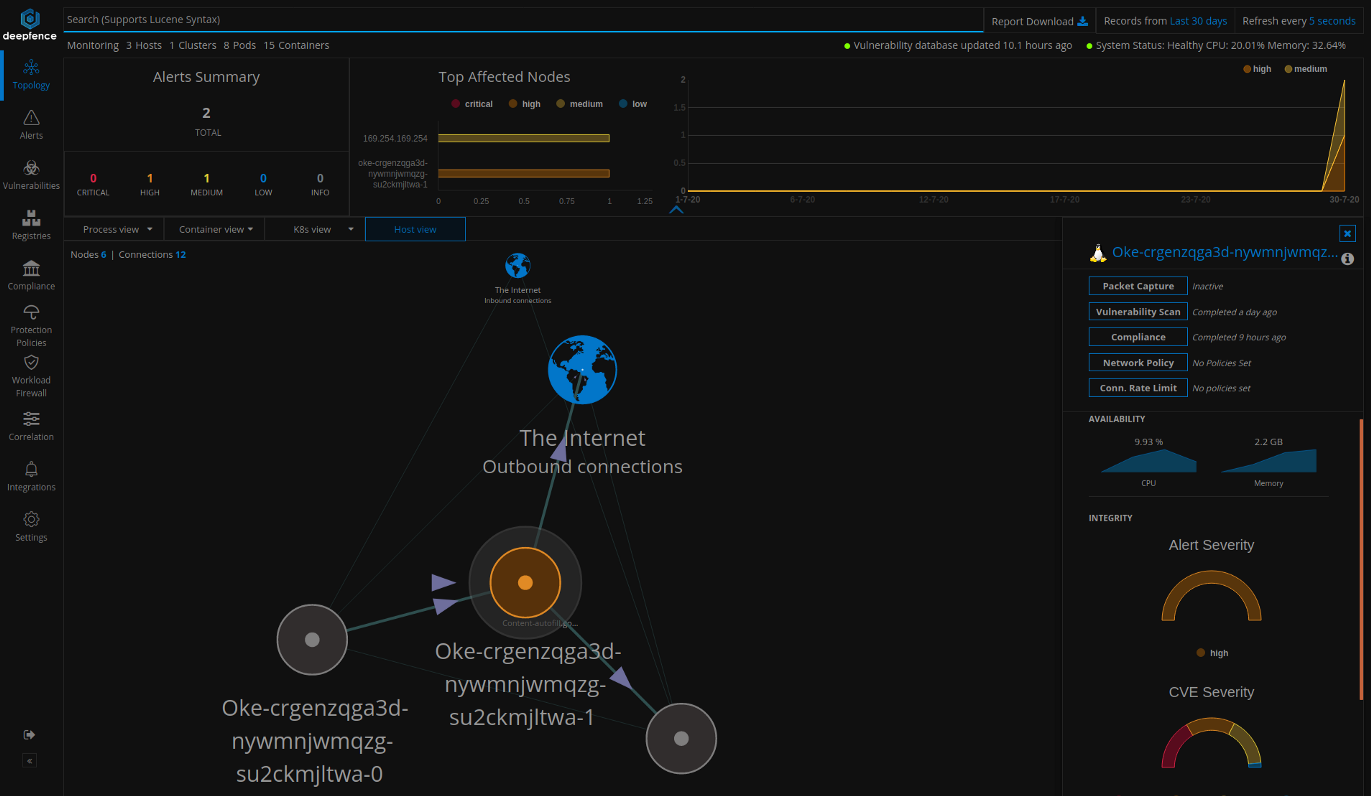
Now, we briefly describe some important functionality of Deepfence security platform.
Vulnerability Scanning
After the vulnerability database populates, you can scan the nodes, containers, and pods for vulnerabilities. It takes up to 30–60 minutes for vulnerability database to download. You can check the download status of the vulnerability database on the notification panel.
You can also initiate vulnerability scanning of any number of nodes by using Deepfence APIs. You can visualize the vulnerabilities found on each node and a ranked list of the most exploitable vulnerabilities across images by navigating to Vulnerabilities tab. You can tag and scan a subset of nodes by using user-defined tags.
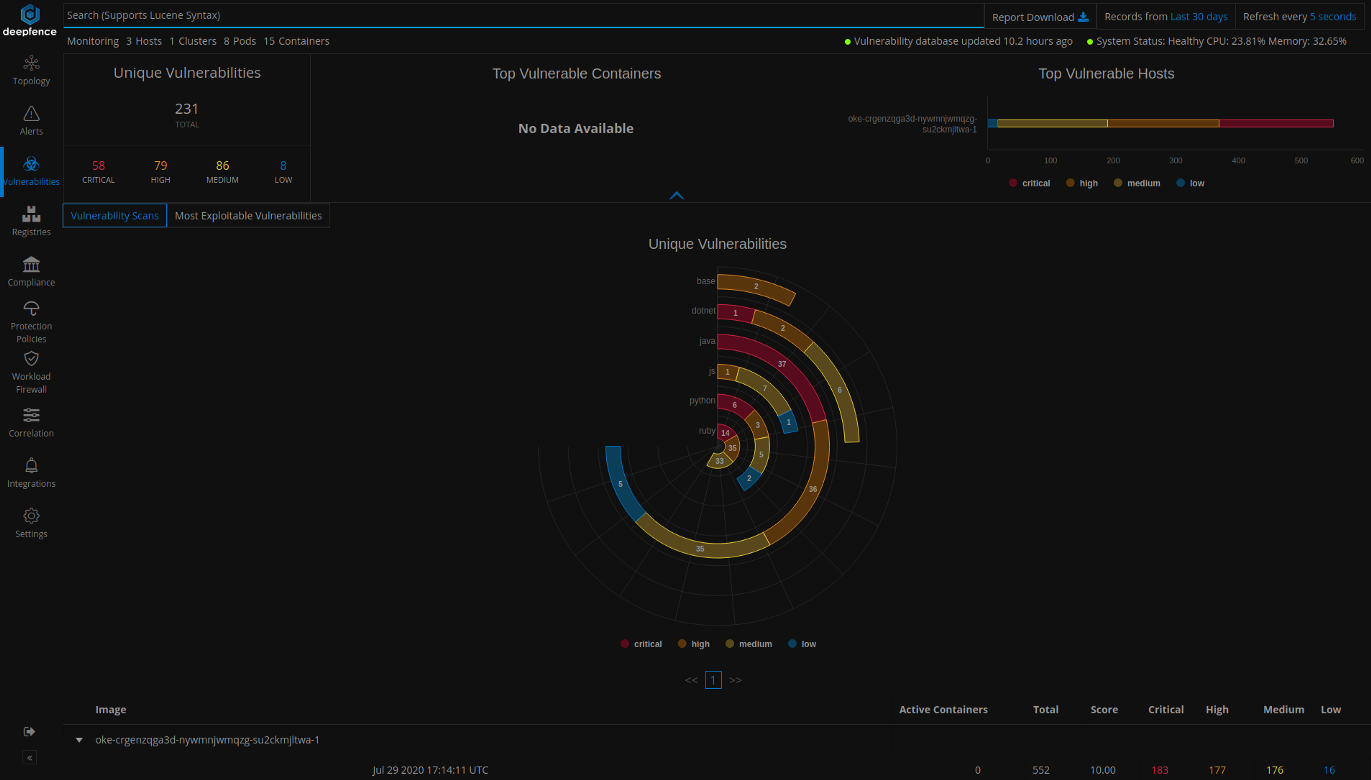
You can also scan for vulnerabilities in images stored in various container registries from the registry scanning dashboard.
Compliance Checking
Similar to vulnerability scanning, you can start standard compliance checks from the topology tab or using Deepfence APIs. You can visualize the results of compliance checks by navigating to the Compliance tab. You can also tag and check a subset of nodes by using user-defined tags. Deepfence provides standard compliance checks, such as System Harding, CIS, NIST master, NIST agent, PCIDSS, HIPAA, and mission critical.
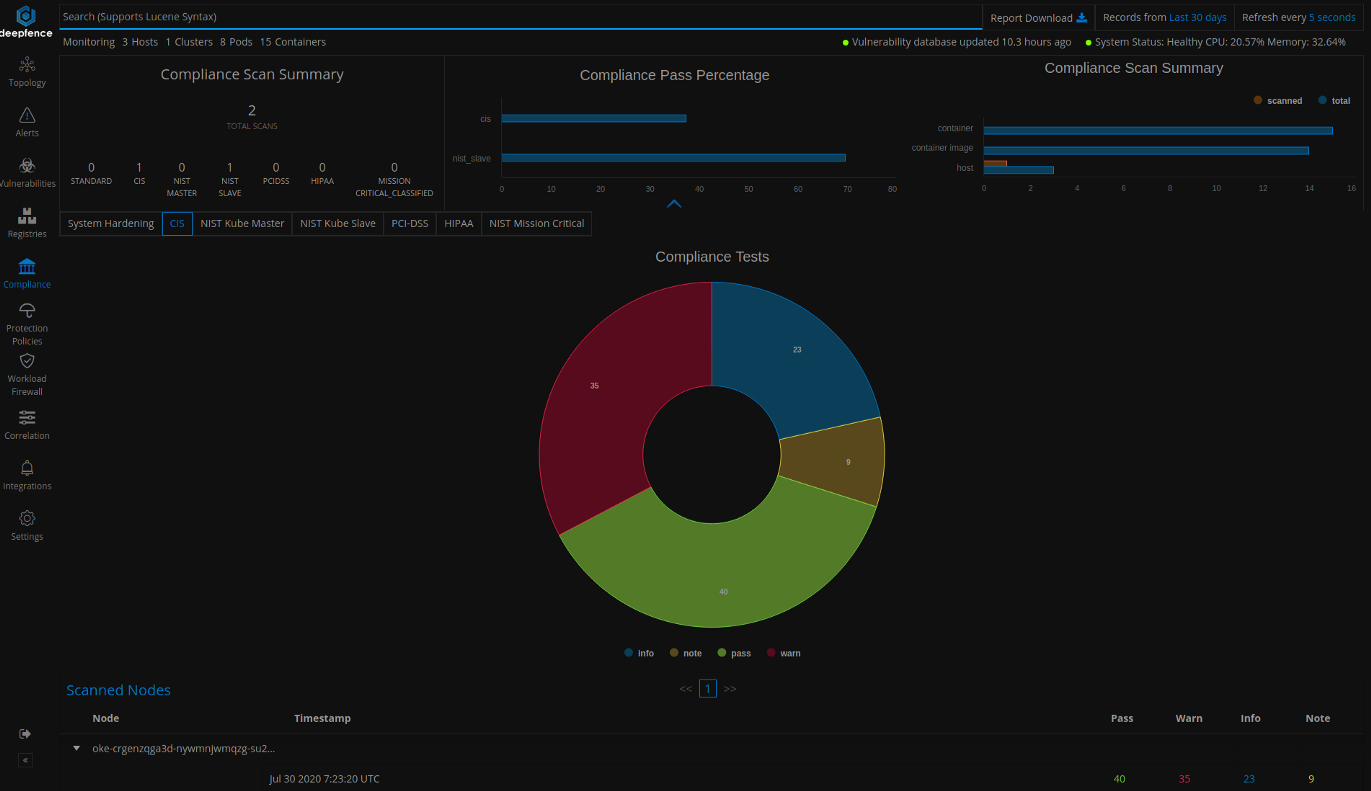
Runtime Integrity Monitoring
You can measure the attack surface using vulnerability and compliance scans. Also, Deepfence monitors runtime application behavior to detect attacks because of those security vulnerabilities and weaknesses. Deepfence observes network, file, and system level activities to detect any suspicious events and attacks. You can enable deep packet inspection of normal and encrypted network traffic on the topology tab by clicking the nodes and then on the packet capture button.
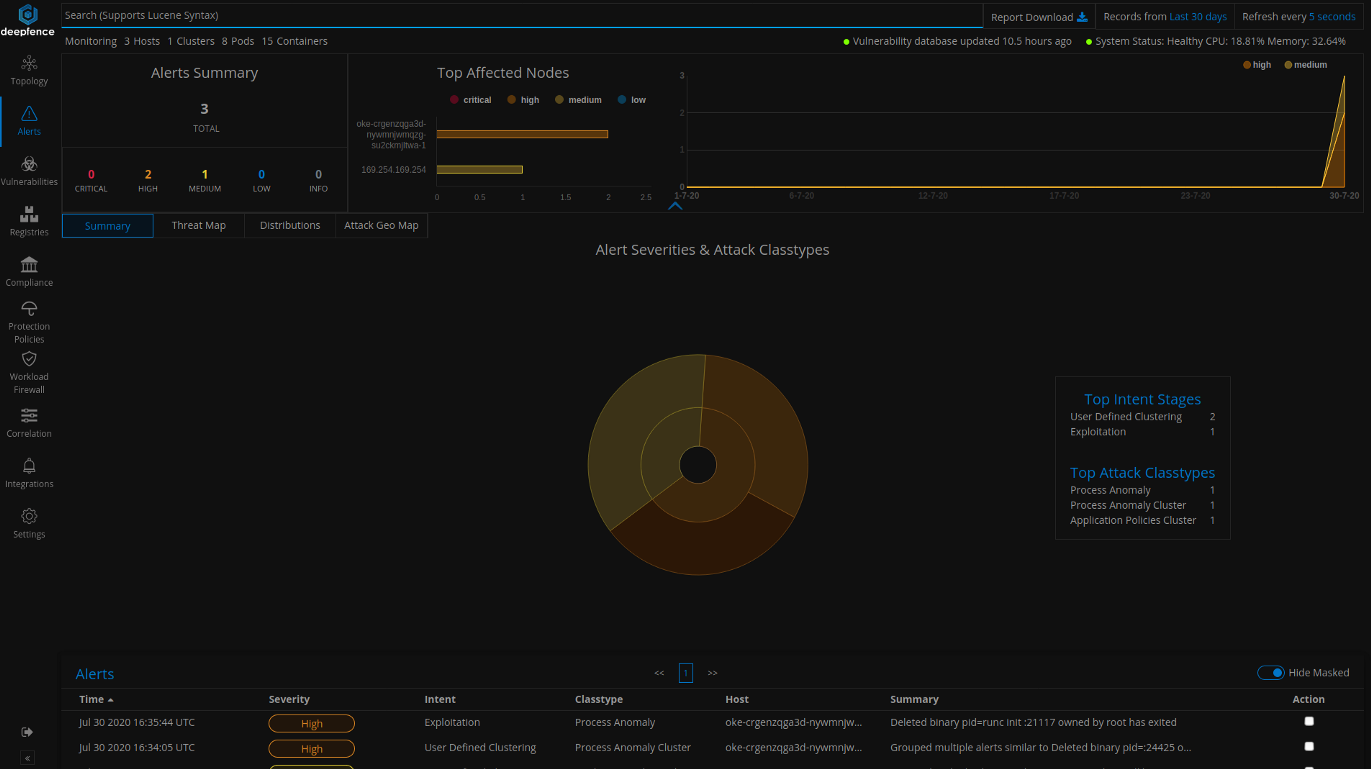
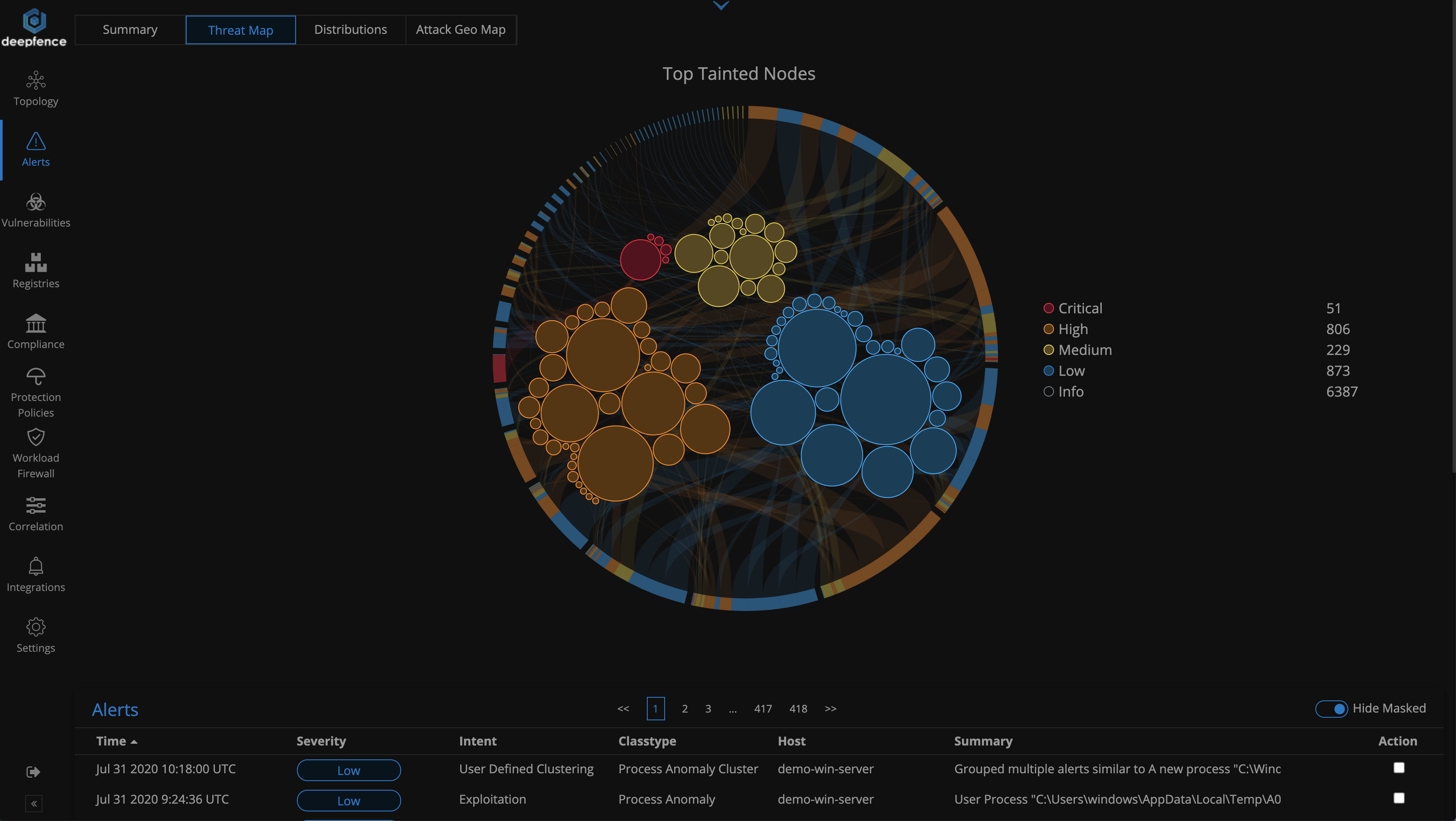
Deepfence can also correlate detected vulnerabilities with various runtime alerts to reduce false positives and alert users about multistage attack plans.
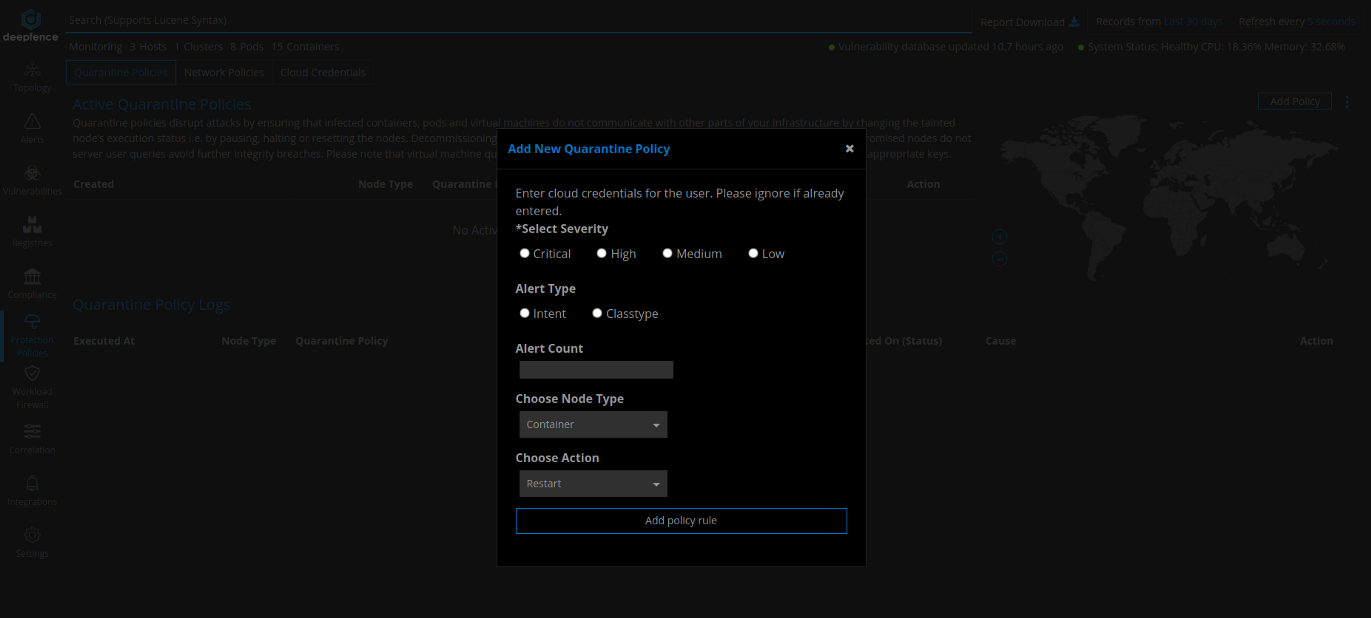
Protection Policies
Deepfence also allows you to set infrastructure and workload level quarantine and network protection to quarantine infected nodes and stop further attacks. Quarantine policies disrupt attacks by ensuring that infected containers, pods, and virtual machines don’t compromise the integrity of other parts of your infrastructure by pausing, halting, or restarting the nodes. Network policies disrupt attacks by ensuring that infected containers, pods, and virtual machines do not communicate with other parts of your infrastructure or external entities. Decommissioning nodes in this manner ensures that attacks don’t spread laterally and compromised nodes don’t serve user queries to avoid further integrity breaches.
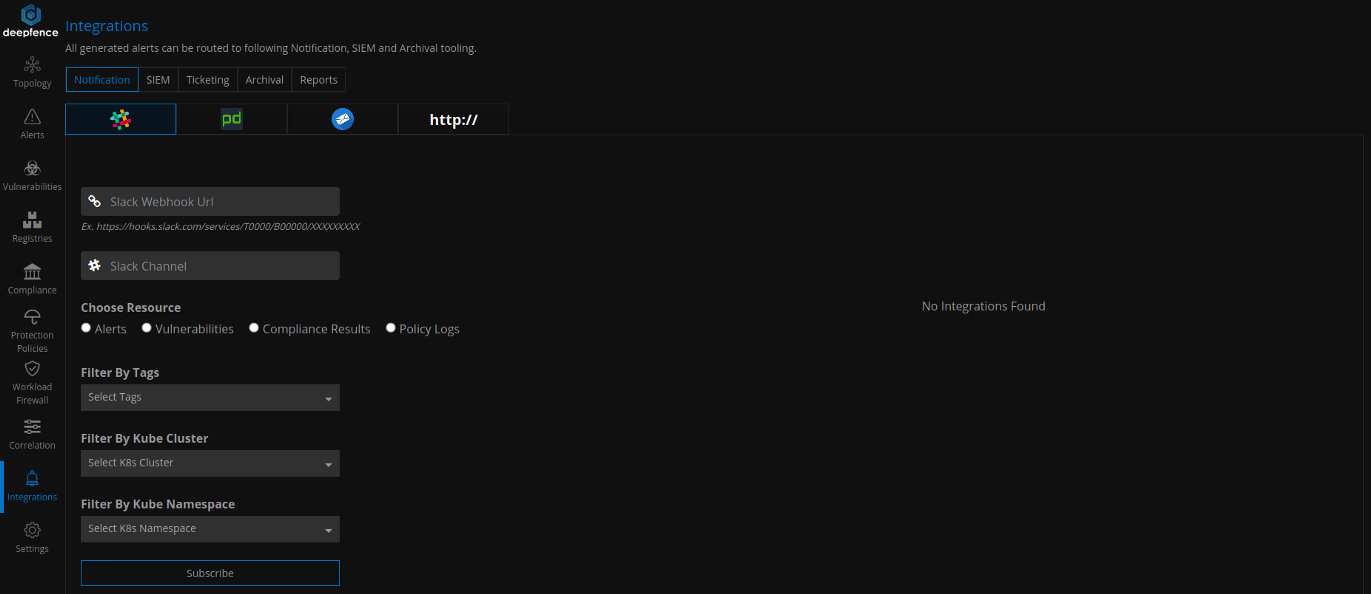
Integrations
Finally, you can send vulnerability and compliance scanning reports, runtime alerts, and policy violation logs to various popular SIEM and notification channels like Slack, PagerDuty, Splunk, ElasticSearch, SumoLogic, and Jira by navigating to the Integrations tab.
With Oracle Cloud Container Engine for Kubernetes and Deepfence, enterprises can deploy Kubernetes with confidence. If you want to use Deepfence to protect your Oracle Kubernetes Engine workloads, sign up for an Oracle Cloud Infrastructure trial account and request a Deepfence demo.
