Companies have increasingly mobile workforces and therefore need to be able to provide their employees with convenient and secure access to their networks. A VPN allows users to connect securely to their networks over the public internet which is a convenient way to support mobility.
IPSec VPN can be used to provide a dedicated connection to remote locations. IPSec is used with Network Access Control to make sure that only approved users can connect to the enterprise.
The other type of VPN is an SSL VPN which uses Secure Socket Layer protocols. SSL VPN provides more granular access control than IPSec. It allows companies to control the types of resources a user can access through the VPN.
This blog post explains how to create a secure SSL VPN connection between Oracle Cloud Infrastructure and remote users using OpenVPN.
At a high level, these are the steps required to create an SSL Tunnel between Oracle Cloud Infrastructure and the OpenVPN client.
- Configure Oracle Cloud Infrastructure for OpenVPN
- Install and configure the OpenVPN server
- Install the OpenVPN client
Configuration Diagram
The following diagram shows the high-level architecture of the proposed setup:
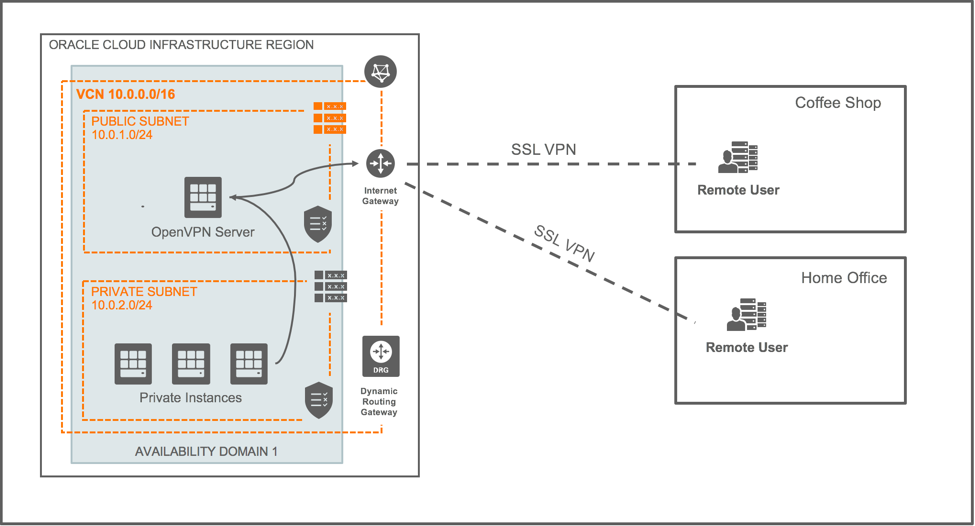
The diagram shows a VCN with two subnets:
- Public (10.0.1.0/24) – a public subnet with access to the internet through an internet gateway.
- Private (10.0.2.0/24) – a private subnet with no access to the internet.
1. Configure Oracle Cloud Infrastructure for OpenVPN
The following steps outline how to create and prepare an Oracle Cloud Infrastructure VCN for OpenVPN.
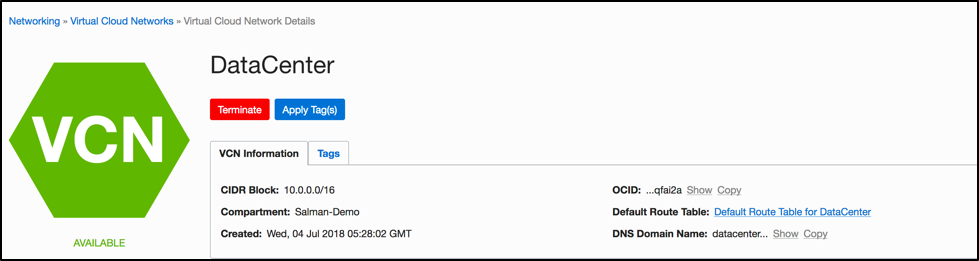
Create a VCN
Create a VCN with two subnets in an availability domain to house OpenVPN server and a Linux host. For more information on how to create a VCN and associated best practices, see VCN Overview and Deployment Guide.
Public Subnet Configuration
Public subnet route table Default route table for datacenter has a route rule, where the internet gateway is configured as the route target for all traffic (0.0.0.0/0).
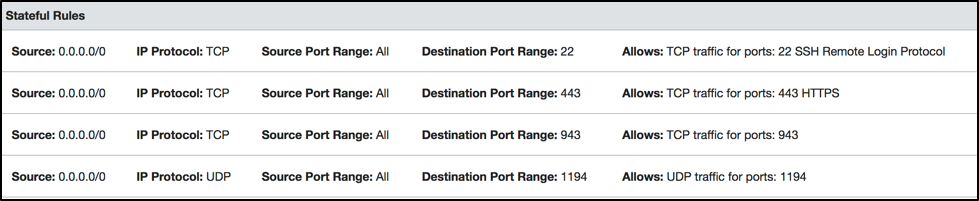
For the subnet’s security list Default Security List, create an egress rule to allow traffic to all destinations. Create ingress rules that allow access on:
- TCP Port 22 for SSH
- TCP Port 443 for OpenVPN TCP connection
- TCP Port 943 for OpenVPN Web-UI
- UDP Port 1194 for OpenVPN UDP Port
For details about how to create subnets, see VCNs and Subnets.
Launch an Instance
Launch an instance in the newly created public subnet. In this case, we are using a VMStandard2.1 shape running Centos 7. Use this instance to install OpenVPN server.
For details, see Launching an Instance.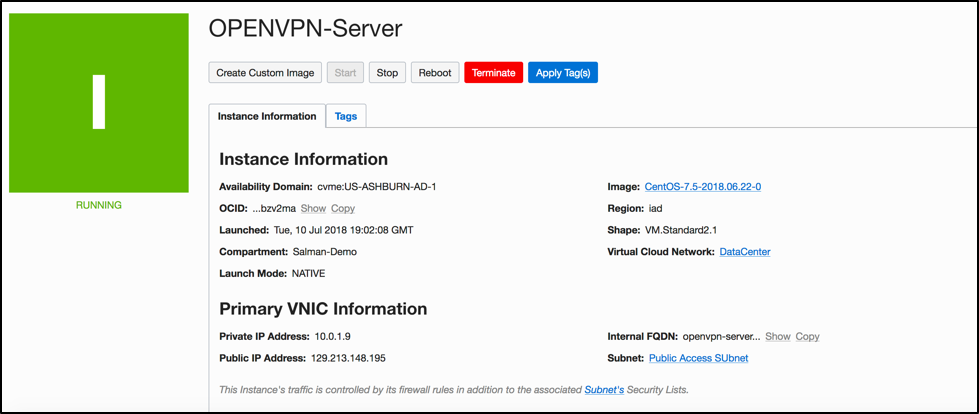
Private Subnet Configuration
The private subnet’s route table Private RT has a routing rule, where OpenVPN (10.0.1.9) is configured as the route target for all traffic 0.0.0.0/0.
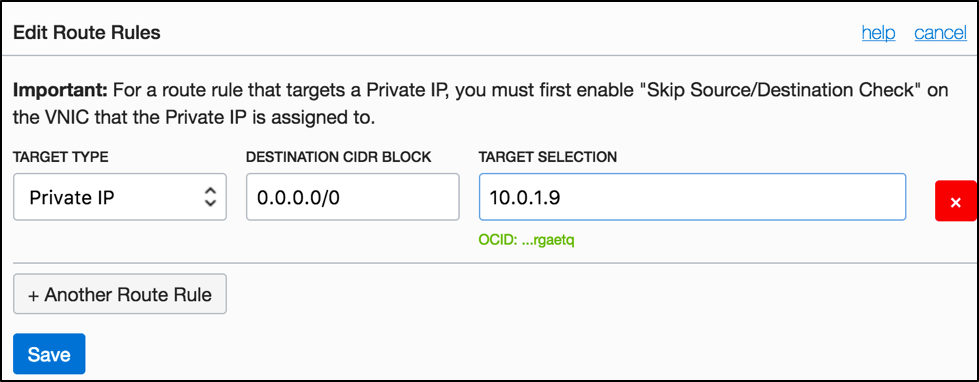
The security list has an egress rule to allow traffic to all destinations. Ingress rules allow only specific address ranges (like on-premises network or any other private subnets in the VCN).
2. Install and Configure the OpenVPN Server
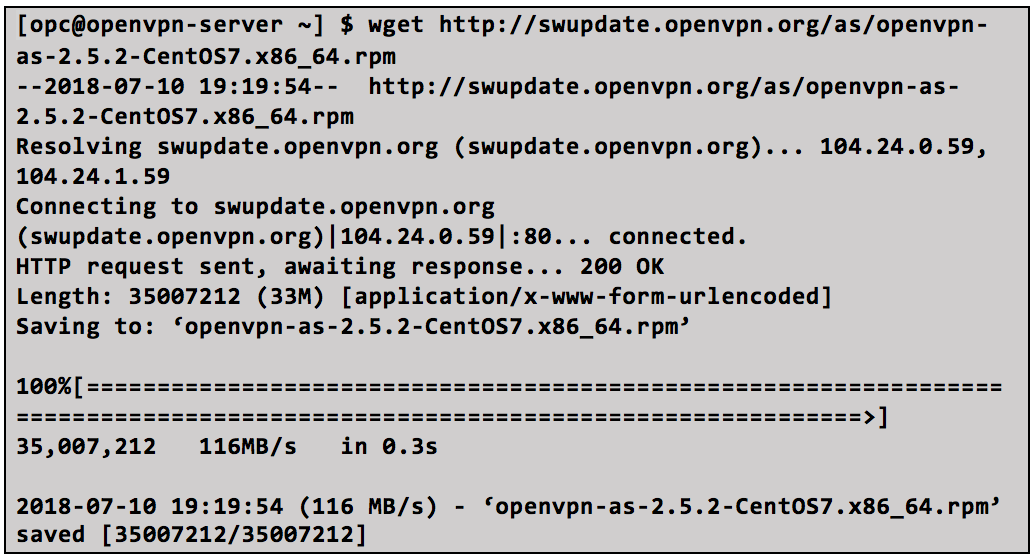
After the new instance starts, connect to it through SSH and install the OpenVPN package. You can download the software package for your OS platform from the OpenVPN website.
Use the RPM command to install the package.
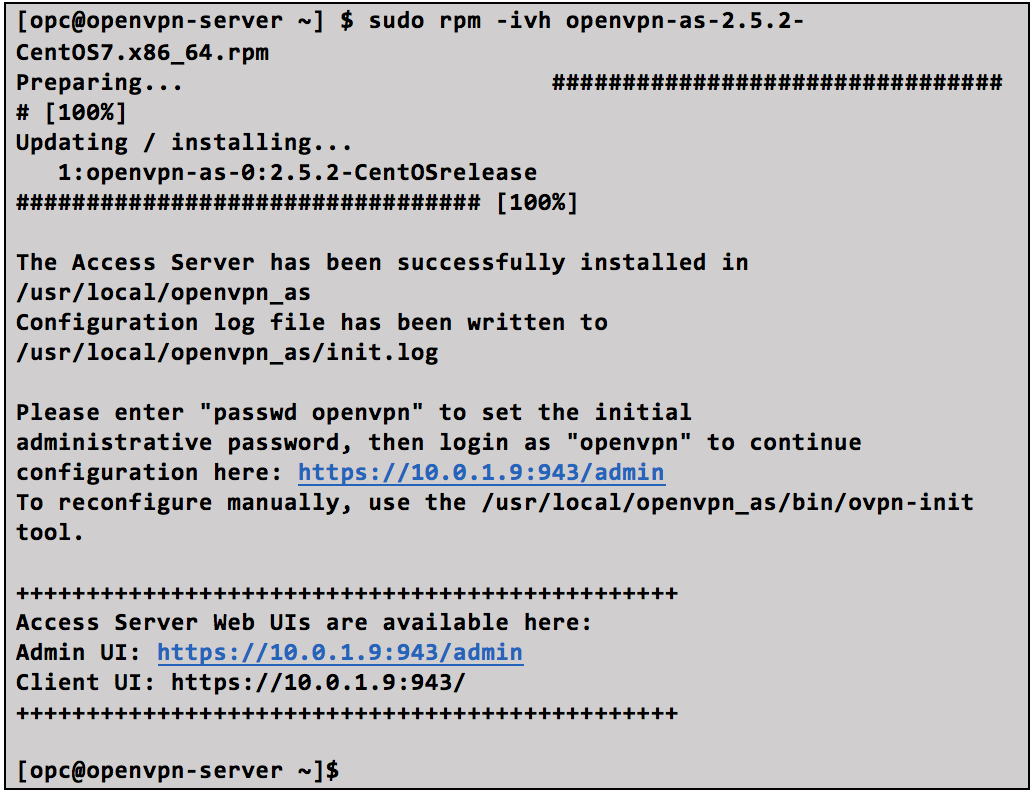
Note: Make sure that you change the password using the “passwd openvpn” command.
Connect to the Admin UI address (https://public-ip:943 /admin), using the password for OpenVPN User.
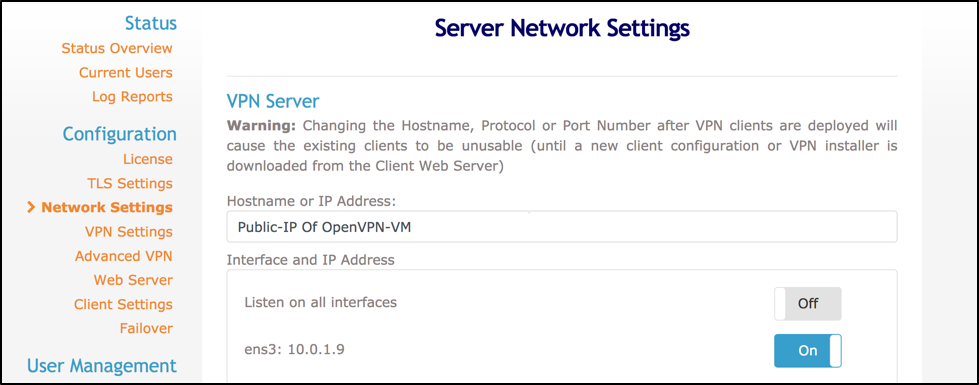
Once you are logged in, click Network Settings and replace the Hostname or IP address with the public IP of the OpenVPN server instance.
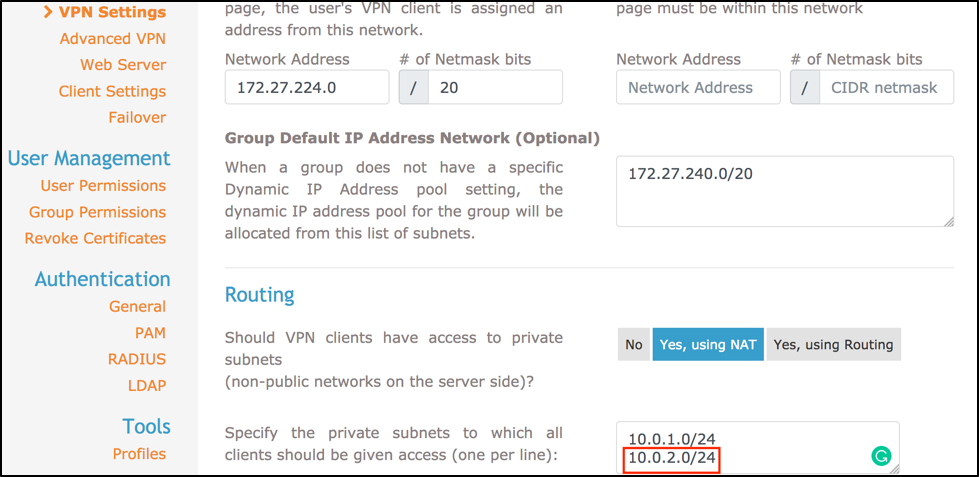
Next, click VPN settings and add the private subnet address range in the routing section.
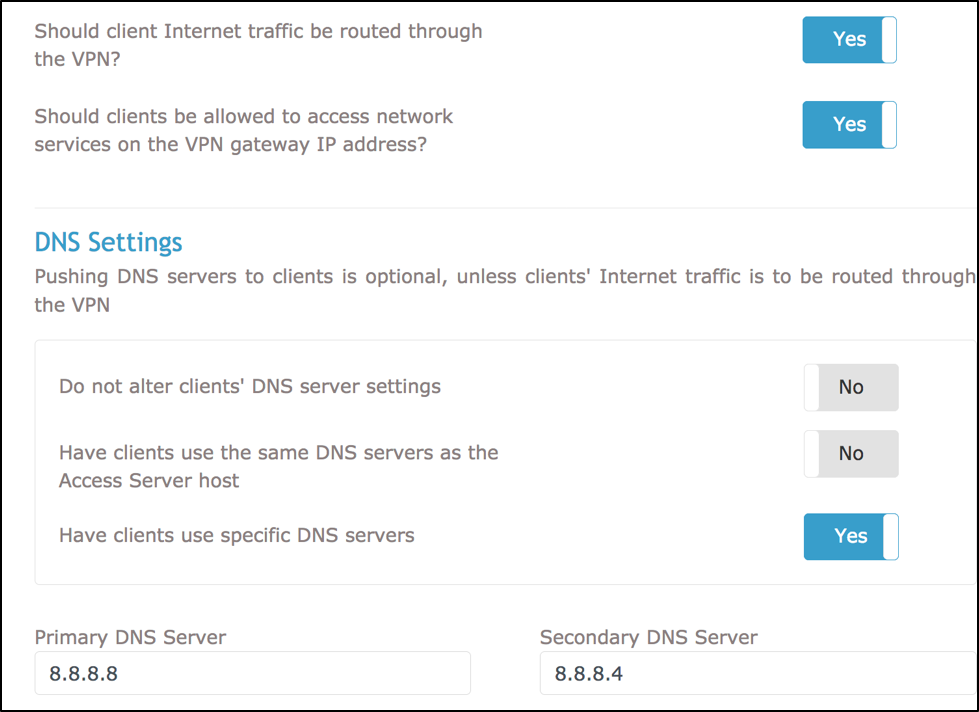
In the Routing section, ensure that the option Should client Internet traffic be routed through the VPN? is set to Yes.
Under Have clients use these DNS servers, manually set the DNS resolvers that will be used by your VPN client machines.
Inter-Client Communication
In the Advanced VPN section, ensure that the option Should clients be able to communicate with each other on the VPN IP Network? is set to Yes.
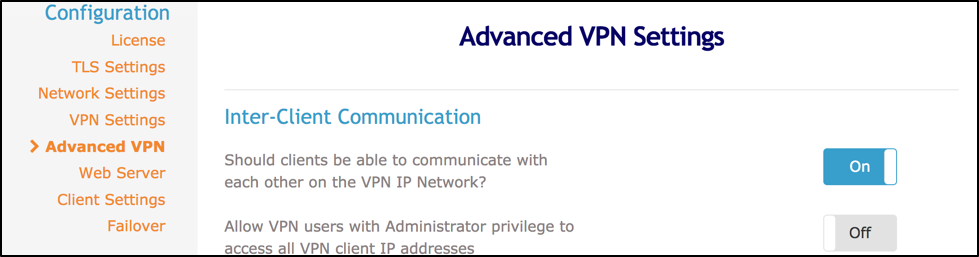
Once you’ve applied your changes, press Save Settings. You are prompted to Update Running Server to push your new configuration to the OpenVPN server.
3. Install OpenVPN Client
Connect to the OpenVPN Access Server Client UI https://Public-IP-OpenVPN-VM:943
Download the OpenVPN client for your platforms.
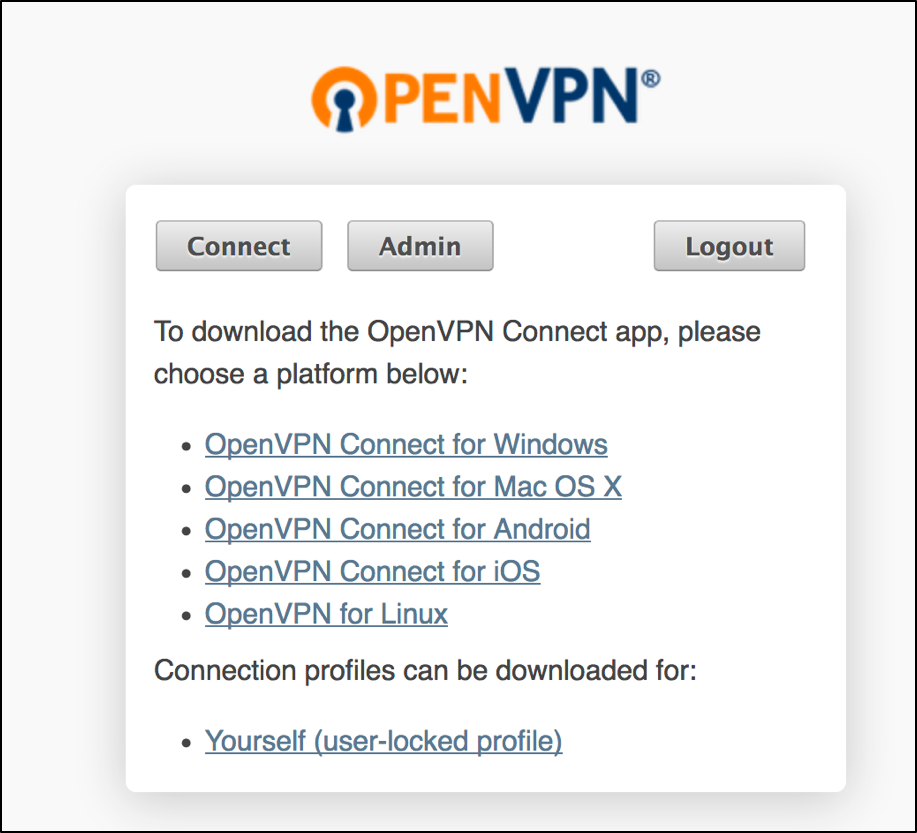
Once the installation process has completed, you see an OpenVPN icon in your OS taskbar. Right-click this icon to bring up the context menu to starting your OpenVPN connection.
![]()
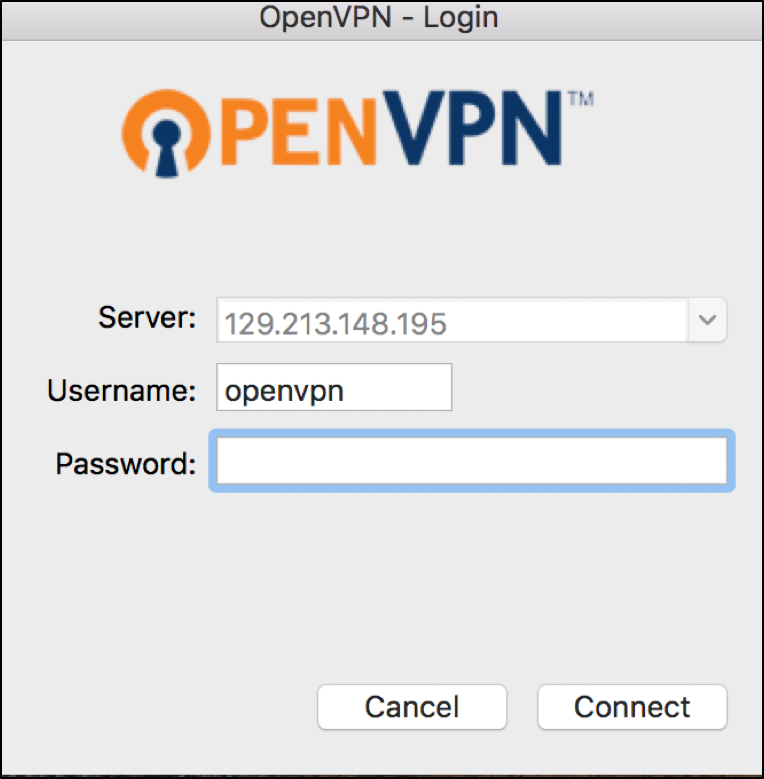
Clicking Connect brings up a window asking for the OpenVPN username and password. Enter the credentials for your OpenVPN user and click Connect to establish a VPN tunnel.
Verification
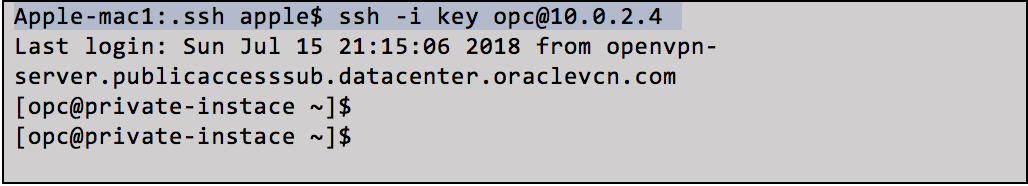
Launch a host instance by using any operating system in the private subnet. Open a terminal window on your laptop and connect to the host using the private IP.
Conclusion
This blog discusses how to create a secure and encrypted SSL VPN tunnel between Oracle and a remote user, allowing the user to be able to access the resources in a private subnet of Oracle Cloud Infrastructure.
